LockCrypt ransomware spotted in the wild
Description
The SonicWall Capture Labs Threat Research Team receives reports of new strains and versions of ransomwares daily. This week we analyzed this ransomware called Lockcrypt.
Infection Cycle:
Upon execution, it opens a window titled “crypt” showing its progress so far.

It sends some data over to a remote server, which then responds with more encrypted communication.

It creates and executes a batch file which kills all running processes not in the whitelist.

In turn it disables running AVs and throws off the windows security center.

Encrypted files get an encrypted file name along with a “.lock” file extension.
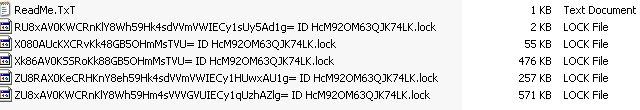
It also adds the ransom note text file in every directory where files were encrypted.
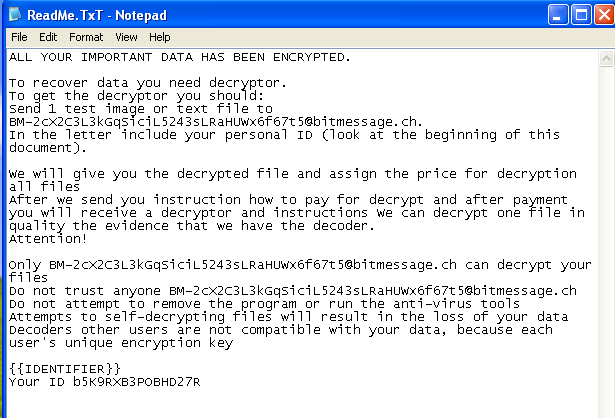
It adds the following in the registry to ensure that notepad opens this text file upon reboot:
- HKLM/Software/Microsoft/Windows/CurrentVersion\Run unlock “c:\Windows
otepad.exe” c:\ReadMe.TxT
A message box also appears with a warning before the user can log on to Windows. The user must click OK in the message box to continue logging on.

This was done by adding LegalNoticeCaption and LegalNoticeText data in the registry.
![]()
But forget about rebooting and logging on to Windows; an infected computer will render useless upon reboot, since some system files were also encrypted by LockCrypt.

Because of the prevalence of these types of malware attacks, we urge our users to back up their files regularly.
SonicWALL Capture Labs provide protection against this threat with the following signature:
- GAV: LockCrypt.RSM (Trojan)




