LockBkdr ransomware spotted in the wild.
The SonicWall Capture Labs Threat Research Team observed reports of a new variant family of LockBkdr [LockCrypt.BKR] actively spreading in the wild.
LockBkdr encrypts the victims files with a strong encryption algorithm until the victim pays a fee to get them back.
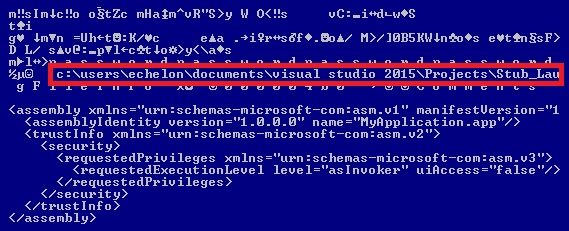
Contents of the LockBkdr ransomware
Infection Cycle:
The Ransomware adds the following files to the system:
- Malware.exe
- %App.path%\ [File Name] .BDKR
- C:\Windows\searchfiles.exe [ Copy of malware ]
- %Userprofile\Desktop %\ How To Restore Files.txt
- Instruction for recovery
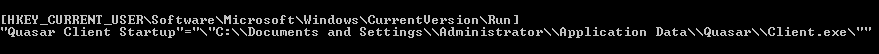
The Ransomware adds the following keys to the Windows registry to ensure persistence upon reboot:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Searchfiles
- C:\Windows\searchfiles.exe
Once the computer is compromised, the Ransomware copies its own executable into %Systemroot% folder and runs the following commands:

LockBkdr retrieves list of running processes and terminates every process other than certain system processes such as the following list:
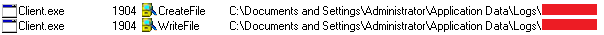
The Ransomware encrypts all the files and appends the .BDKR extension onto each encrypted file’s filename.
After encrypting all personal documents the Ransomware shows the following webpage containing a message reporting that the computer has been encrypted and to contact its developer for unlock instructions.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: LockCrypt.BKR (Trojan)




