LockBit 3.0 'Black' targets large corps. Operator demands $9M for decryption
LockBit 3.0, also known as LockBit Black, is a ransomware family that operates under the Ransomware-as-a-Service (RaaS) model, where the creators collaborate with affiliates who may not have the resources to create and deploy attacks. The LockBit ransomware family is known for its public presence, as it announced its services in July 2022 and even offered a bug bounty program and money to individuals who got the LockBit logo tattooed on their bodies. Despite the public attention, LockBit continues to be one of the most prevalent strains of ransomware and in September 2022, the builder for the ransomware was leaked and made available for download on GitHub. During our analysis, we were able to engage in a direct conversation with the attacker who reveals a staggering $9M for file decryption.
Infection Cycle:
Upon infection, files on the system are encrypted. Each encrypted file is given a “.NegNiNNop” file extension. File names are also obfuscated. eg. 4sk2dwe.NegNiNNoP. After encryption, the following message is displayed on the desktop background:

The following files are added to the system:
- C:\ProgramData\NegNiNNoP.bmp [seen above]
- C:\ProgramData\NegNiNNoP.ico
- C:\Users\NegNiNNoP.README.txt
- C:\Users\All Users\NegNiNNoP.bmp
- C:\Users\All Users\NegNiNNoP.ico
- C:\Users\{user}\NegNiNNoP.README.txt
The following registry key is added:
- HKEY_CLASSES_ROOT\NegNiNNoP\DefaultIcon @ “C:\ProgramData\NegNiNNoP.ico”
NegNiNNoP.ico contains the following image:

A file called NegNiNNop.README.txt is written to the desktop and to all folders where files were encrypted. It contains the following message:
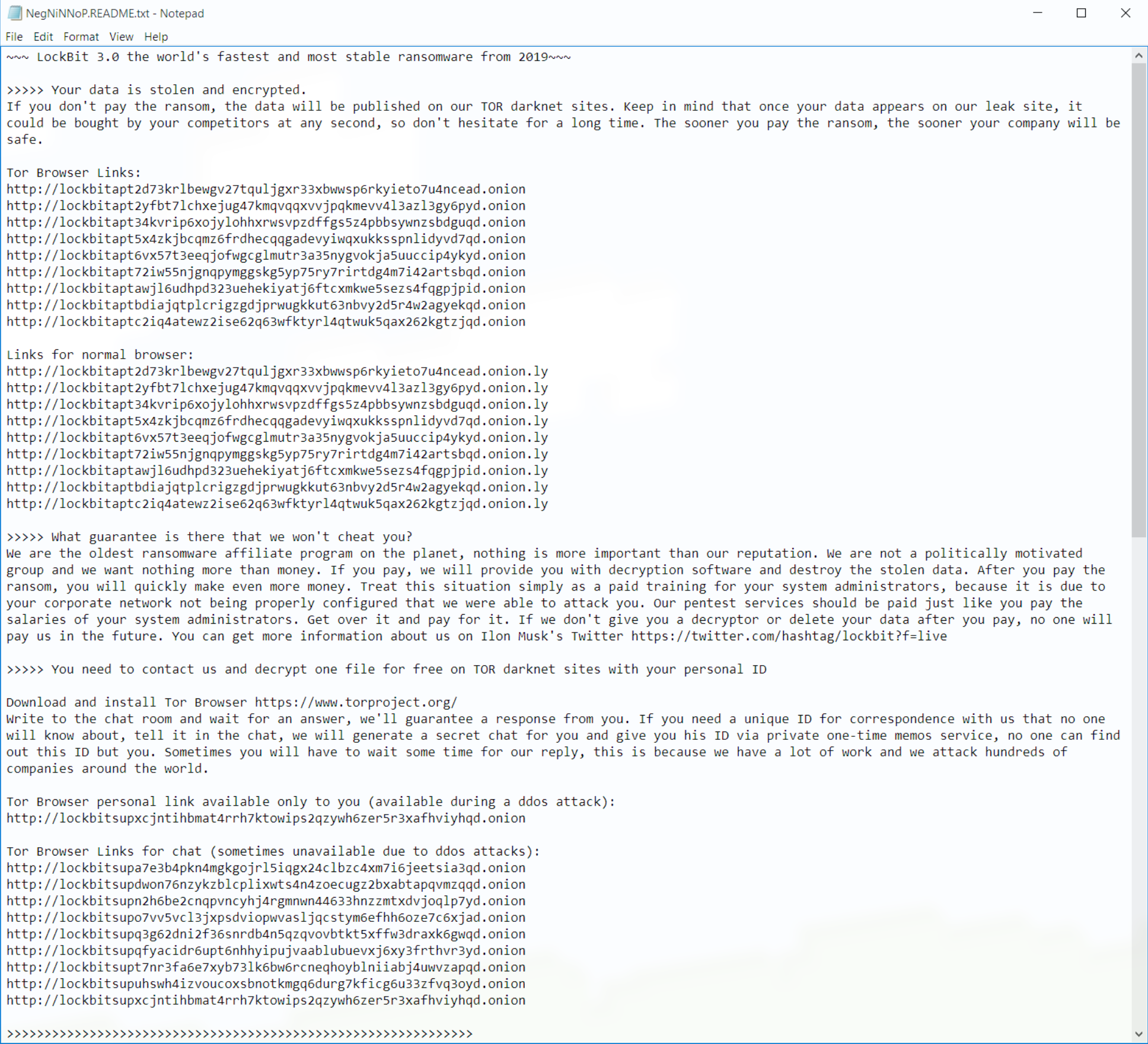
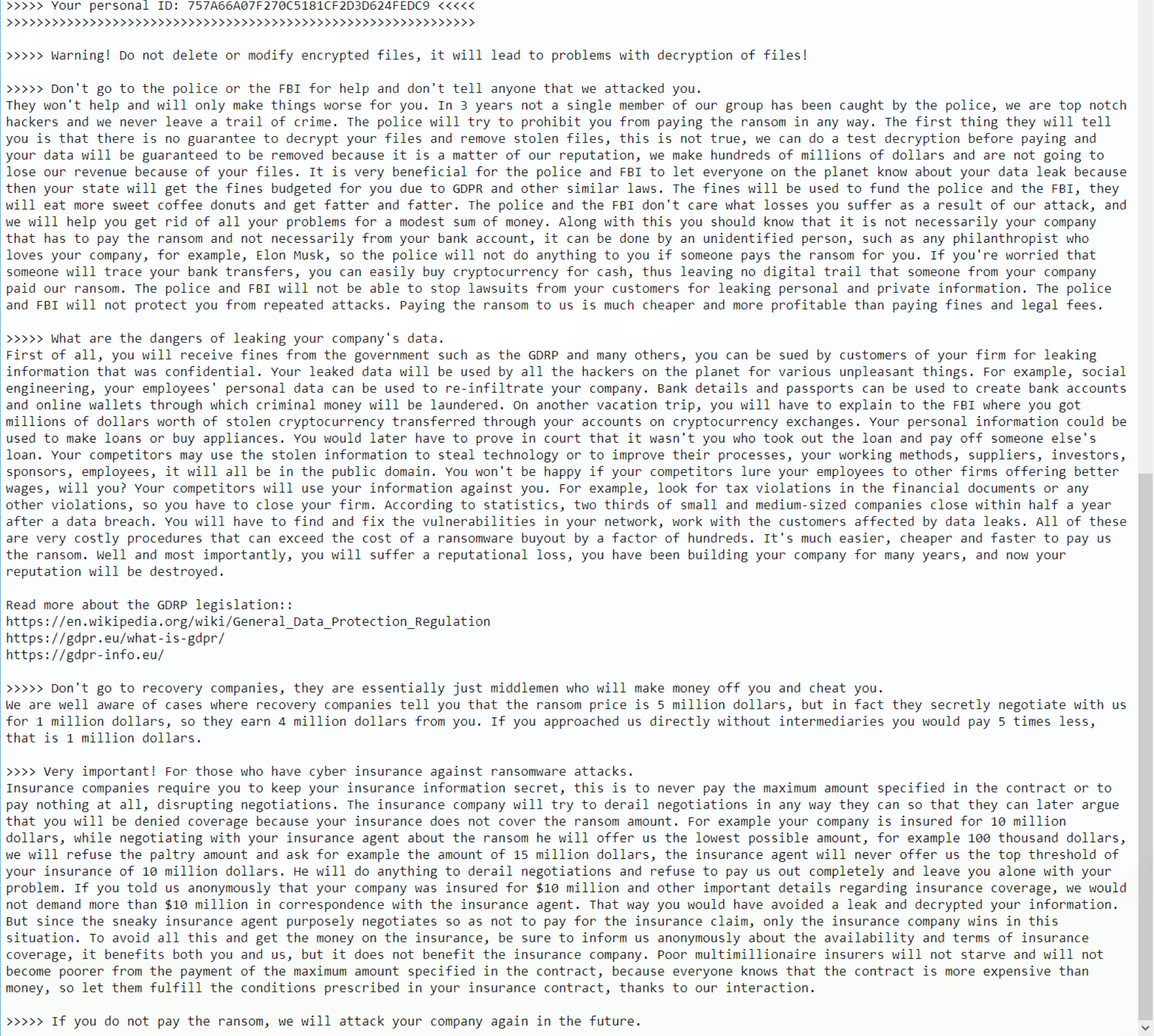
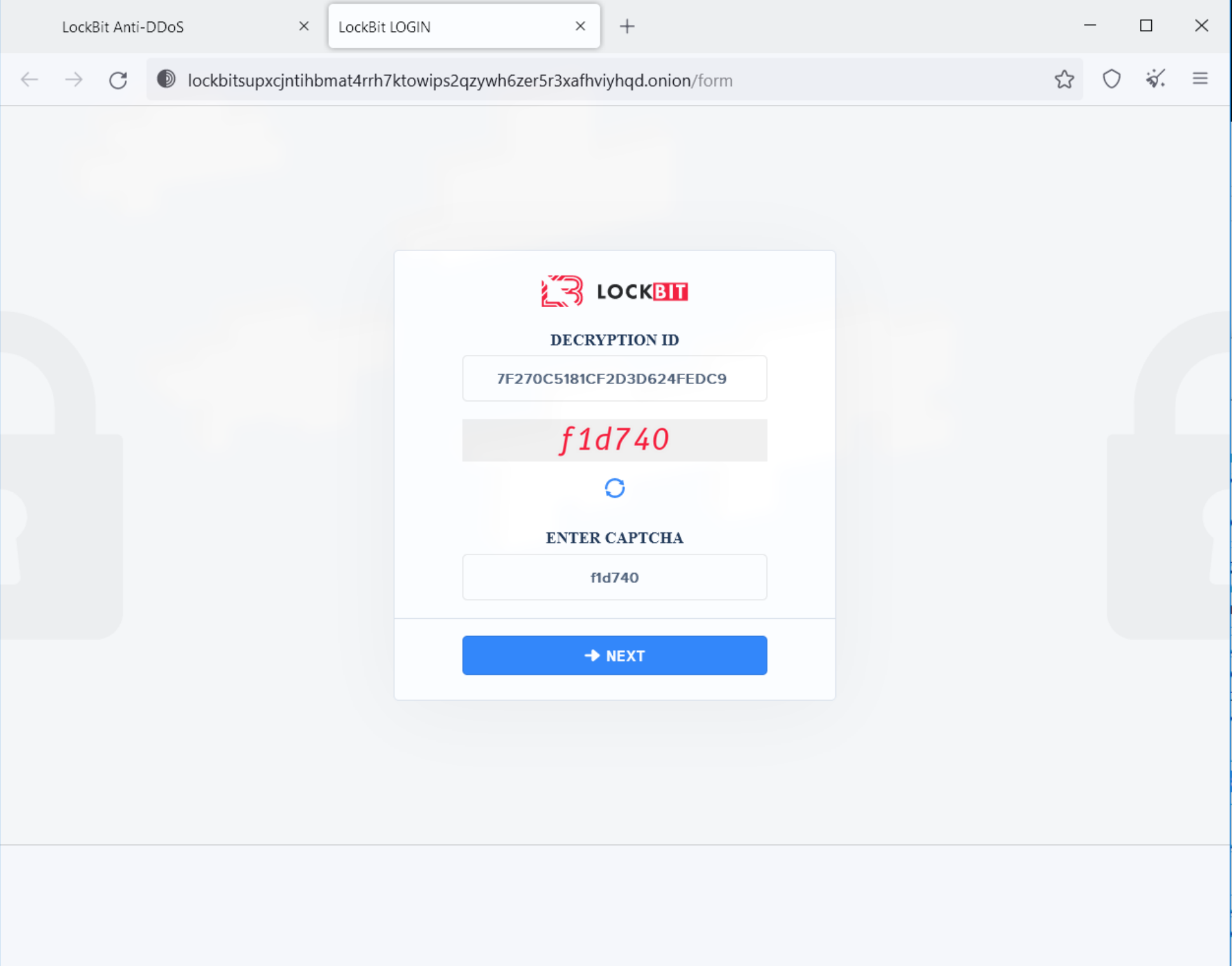
A tOr address is provided in the message and brings the victim to the following pages:
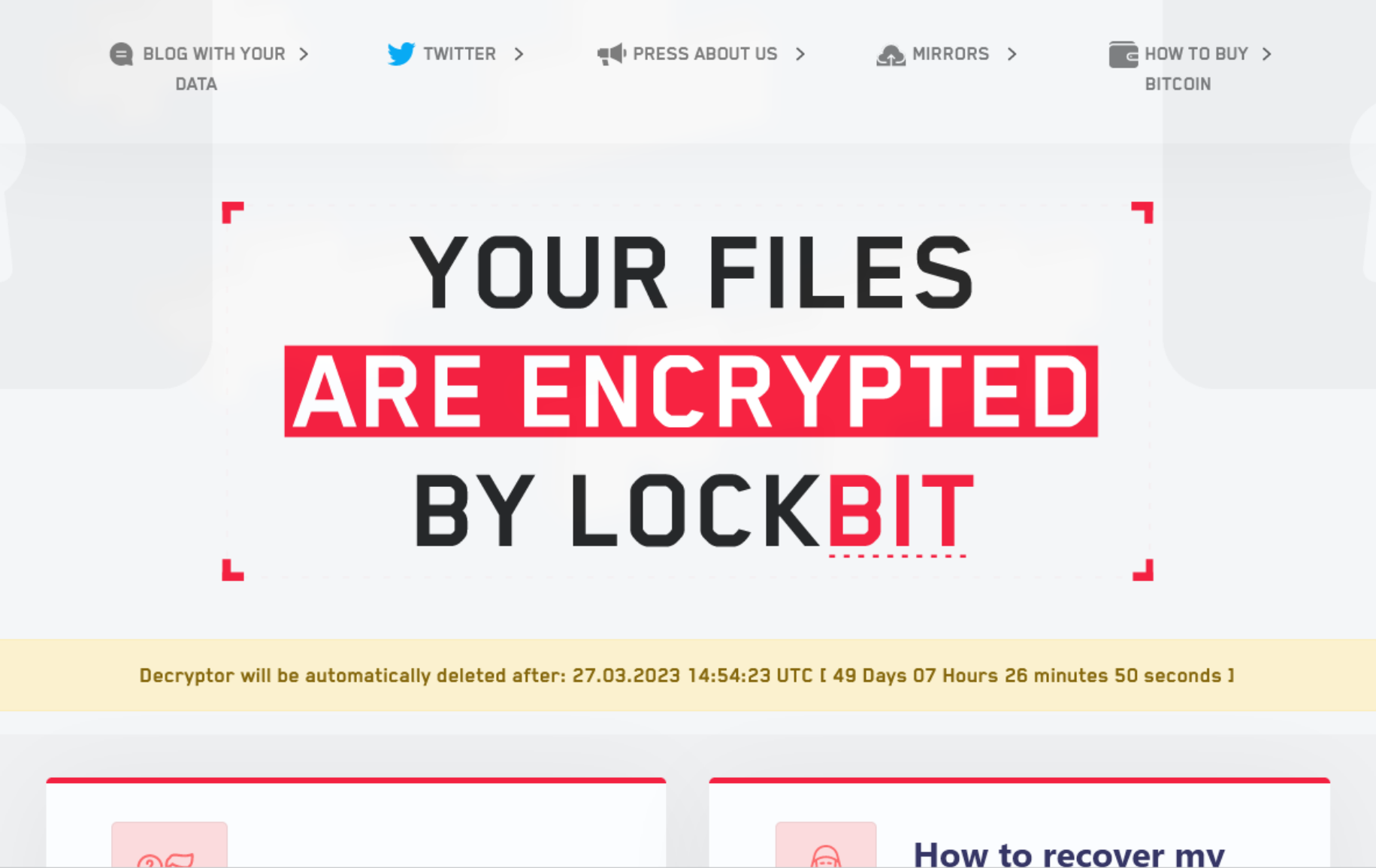
The operators take pride in their work and display a list of victims on their site. This list is filled with various organizations from around the world:
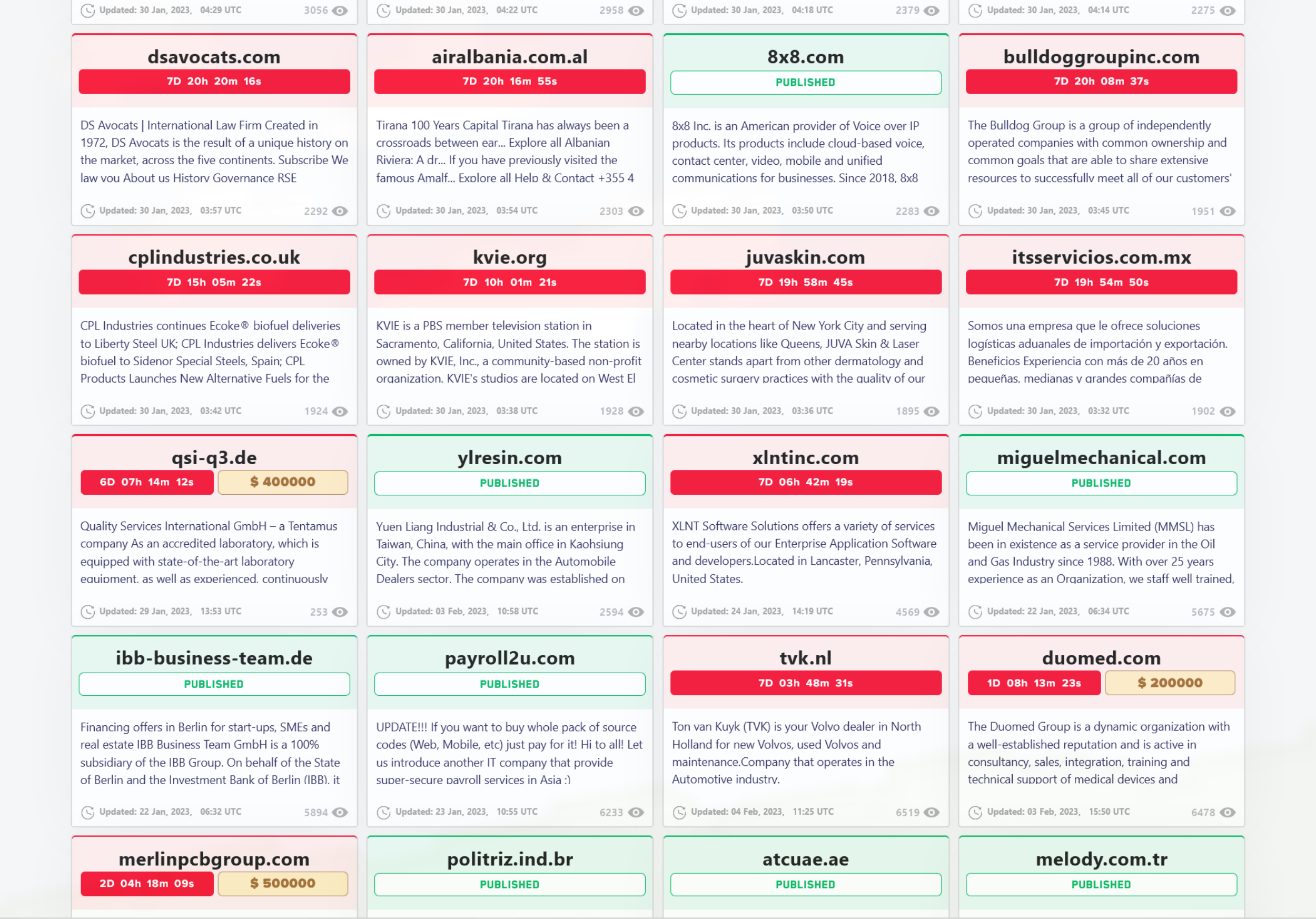
In addition to requiring payment for data retrieval, the operators double down and threaten to leak sensitive data to the public if the ransom is not paid in time. This double extortion method adds additional pressure to the victim in an effort to force them to pay the ransom. Leaked sensitive data is publically available on the site for all to see:
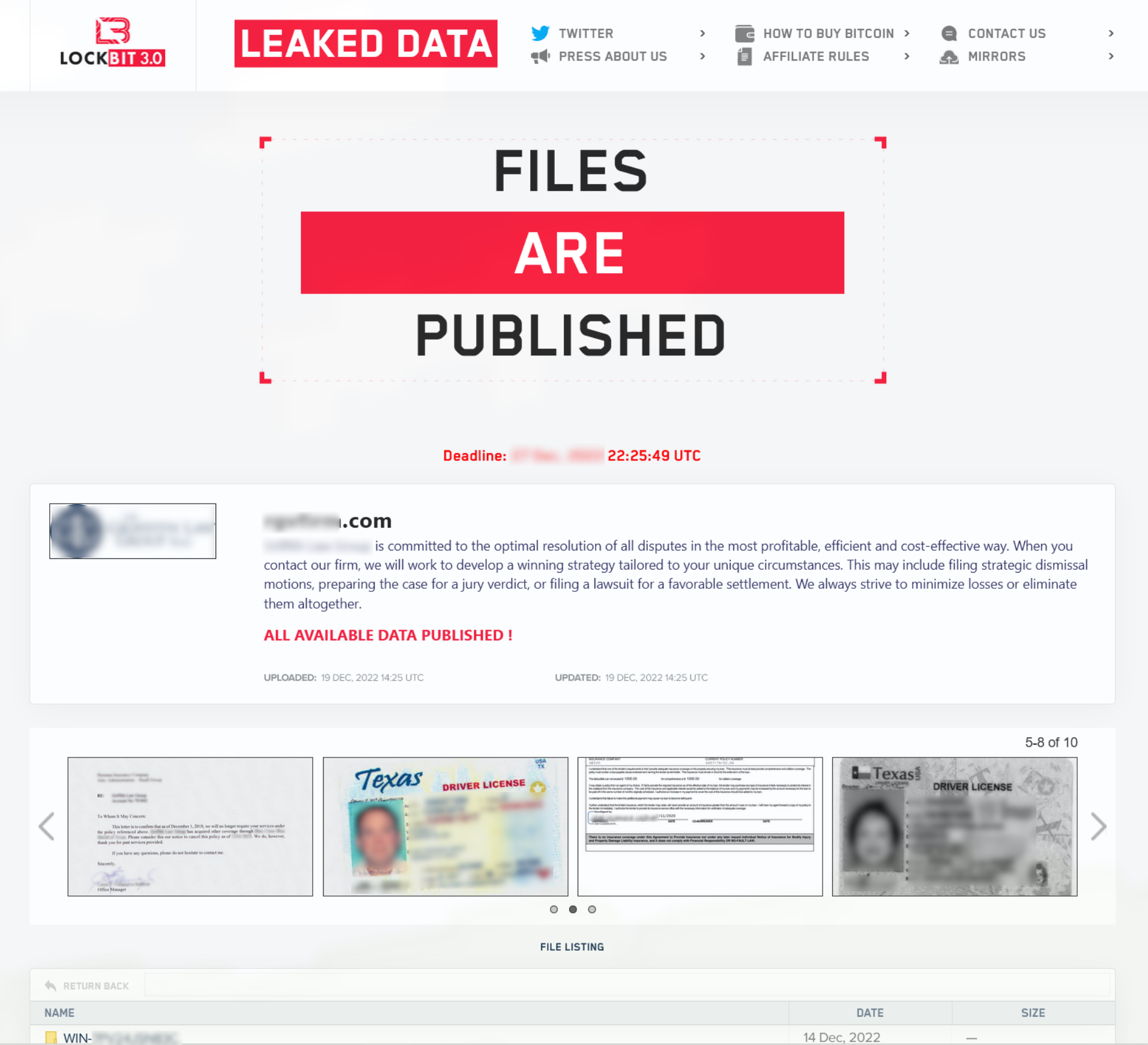
During our analysis, no data was exfiltrated from the system.
On the victim page, a “support” chat box is presented. This enables direct communication with the attackers. Ransomware operators usually use this for negotiation with their victims and to provide additional pressure:
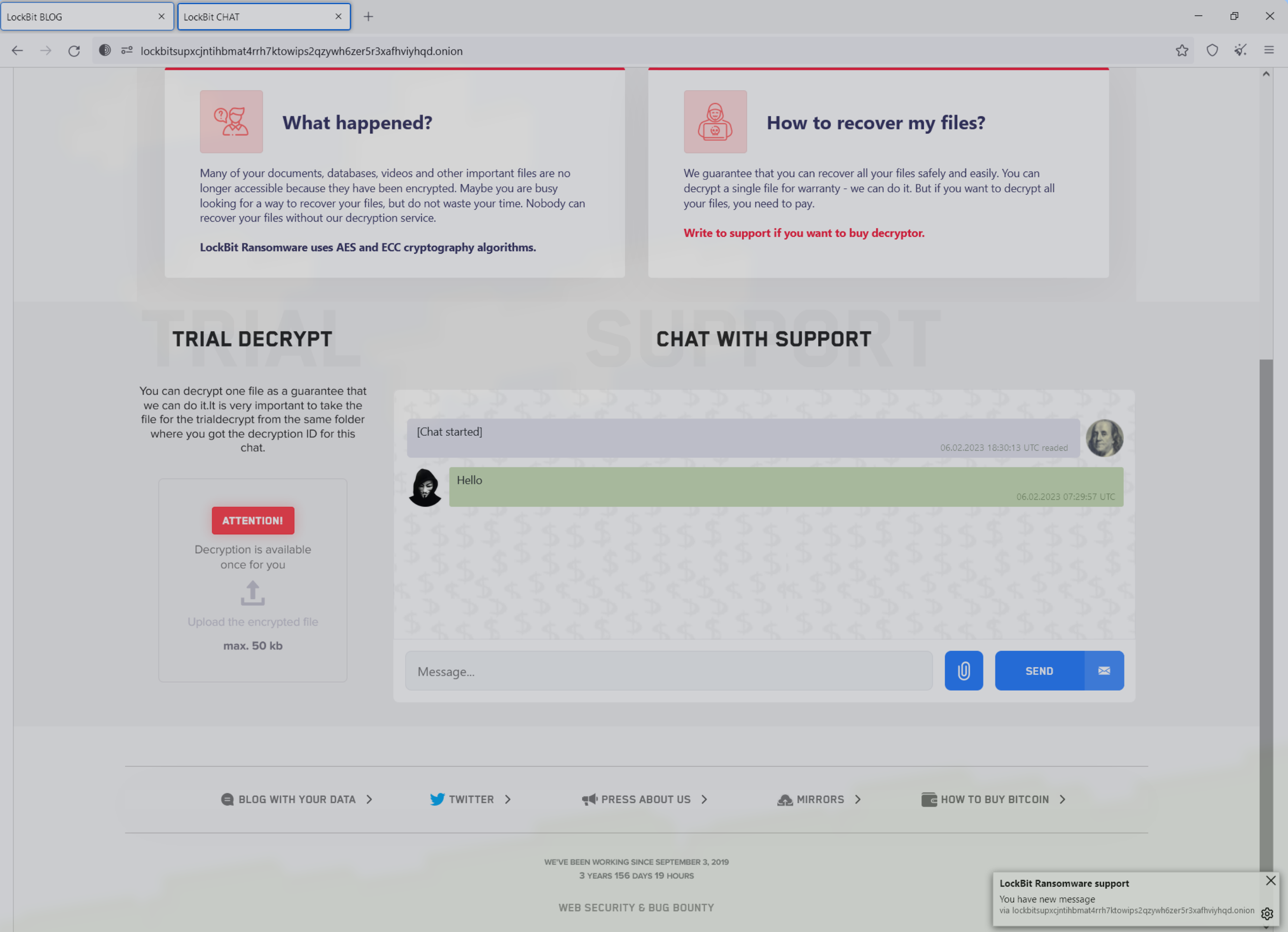
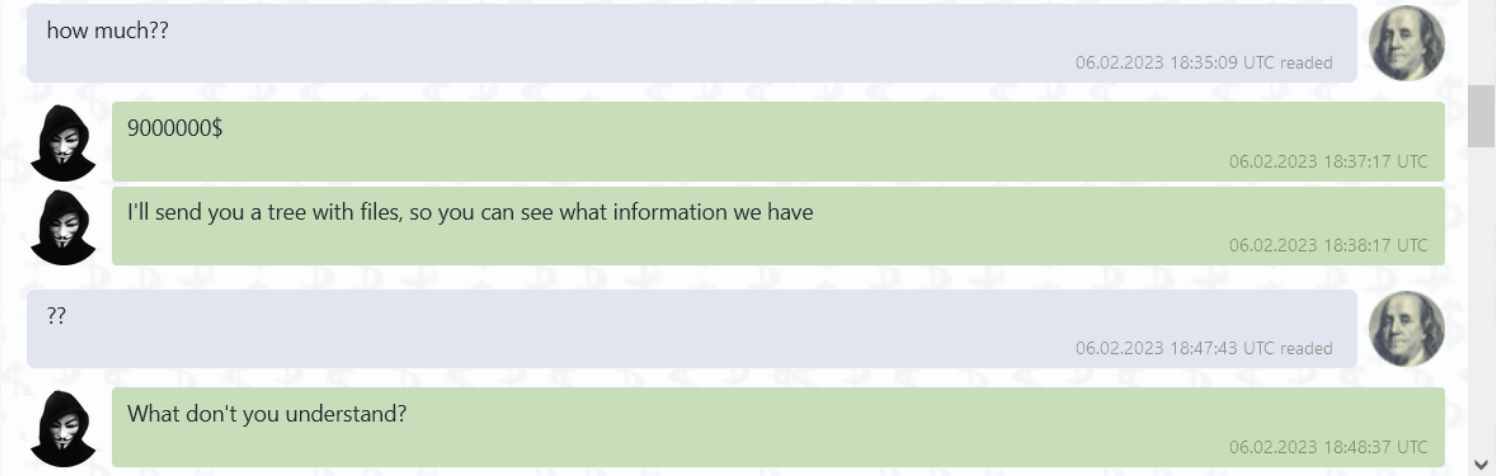
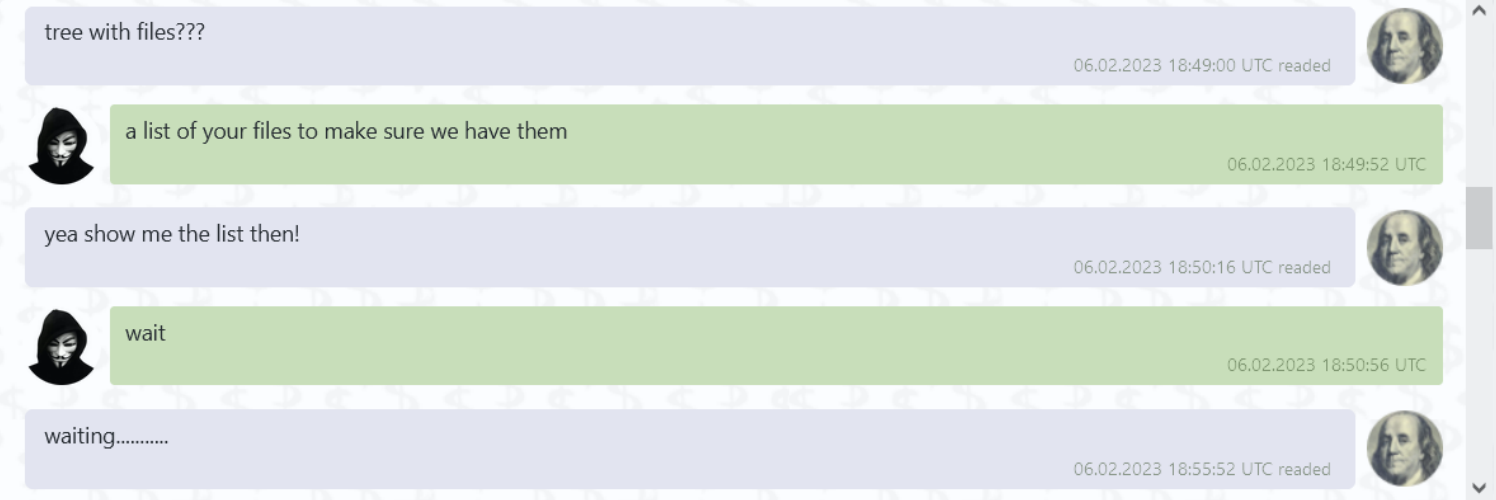
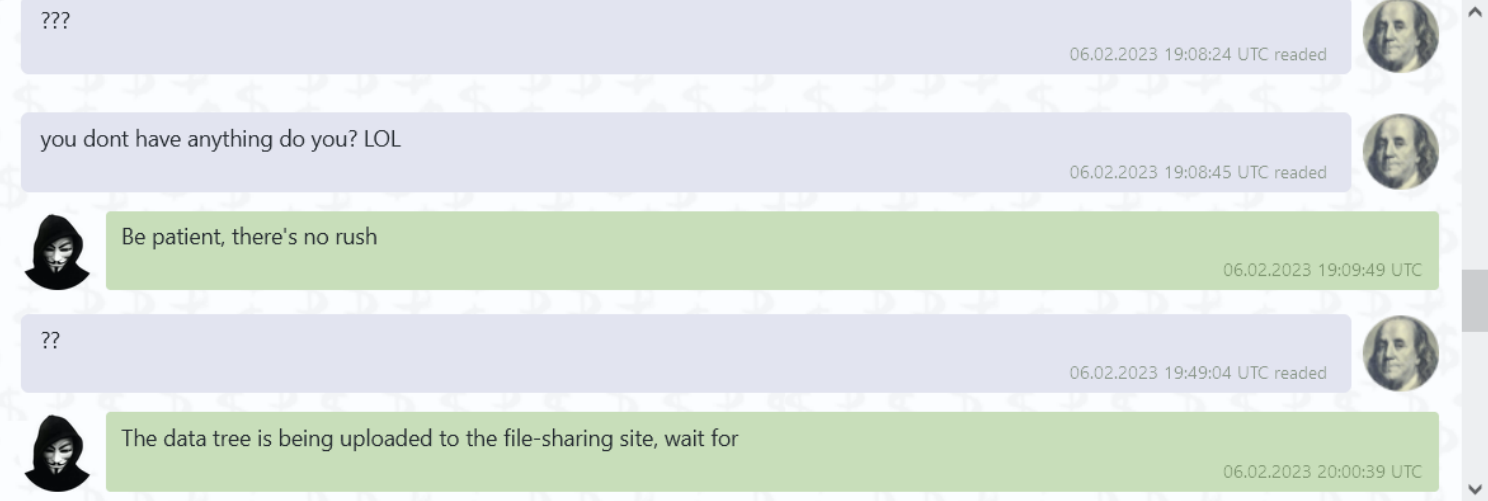
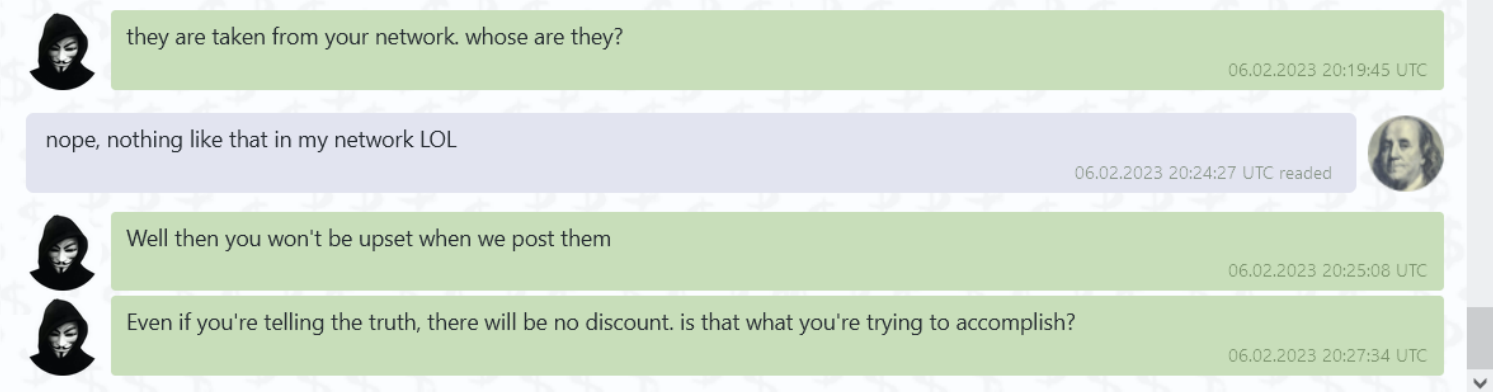
We had the following live conversation with an operator revealing a $9M decryption fee:
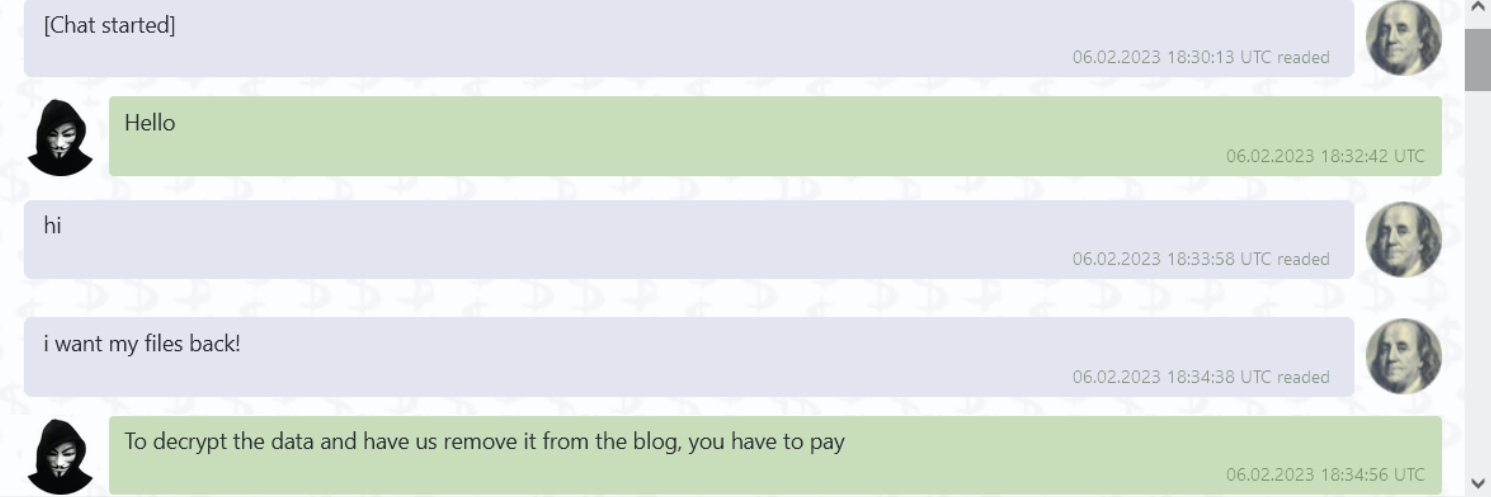
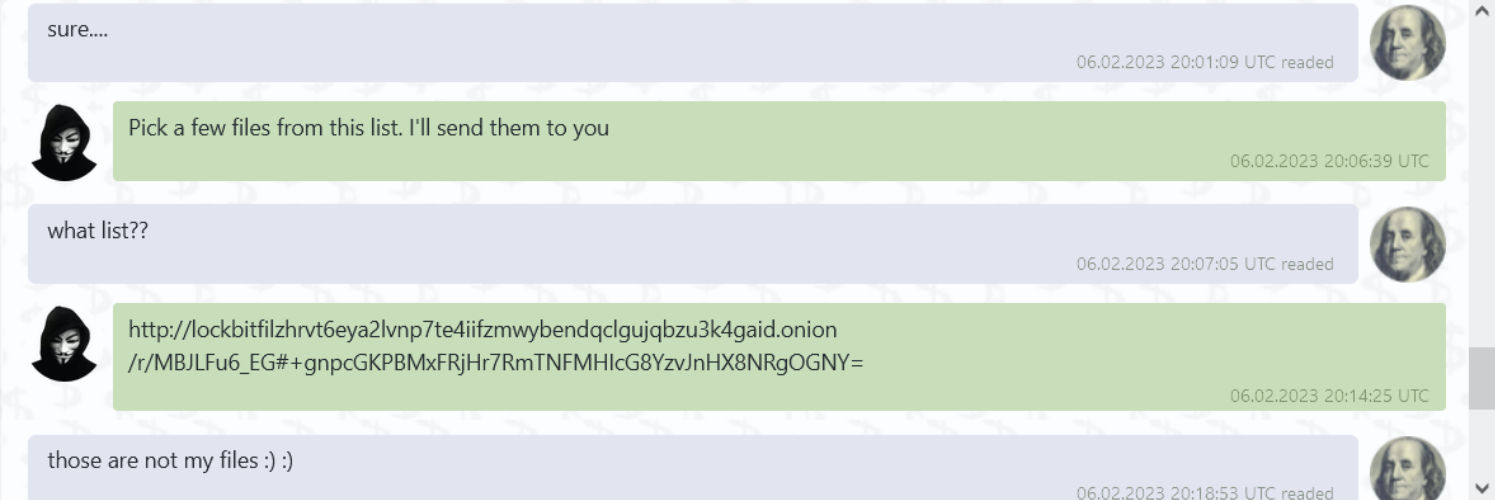
The link took us to the following pages. However, the files referenced were not from our network:

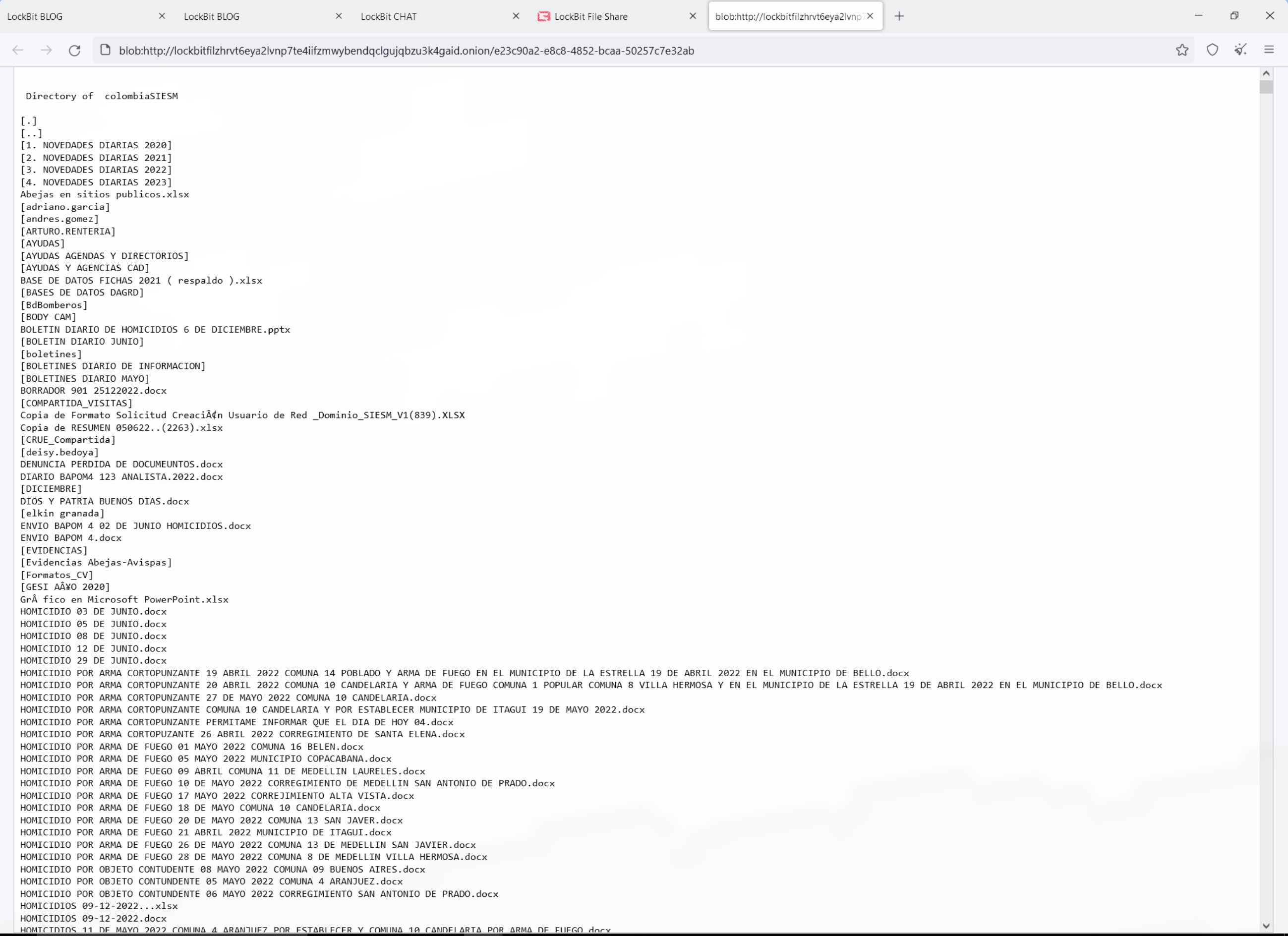
This appears to be a bug on their end:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: LockBit3.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.



