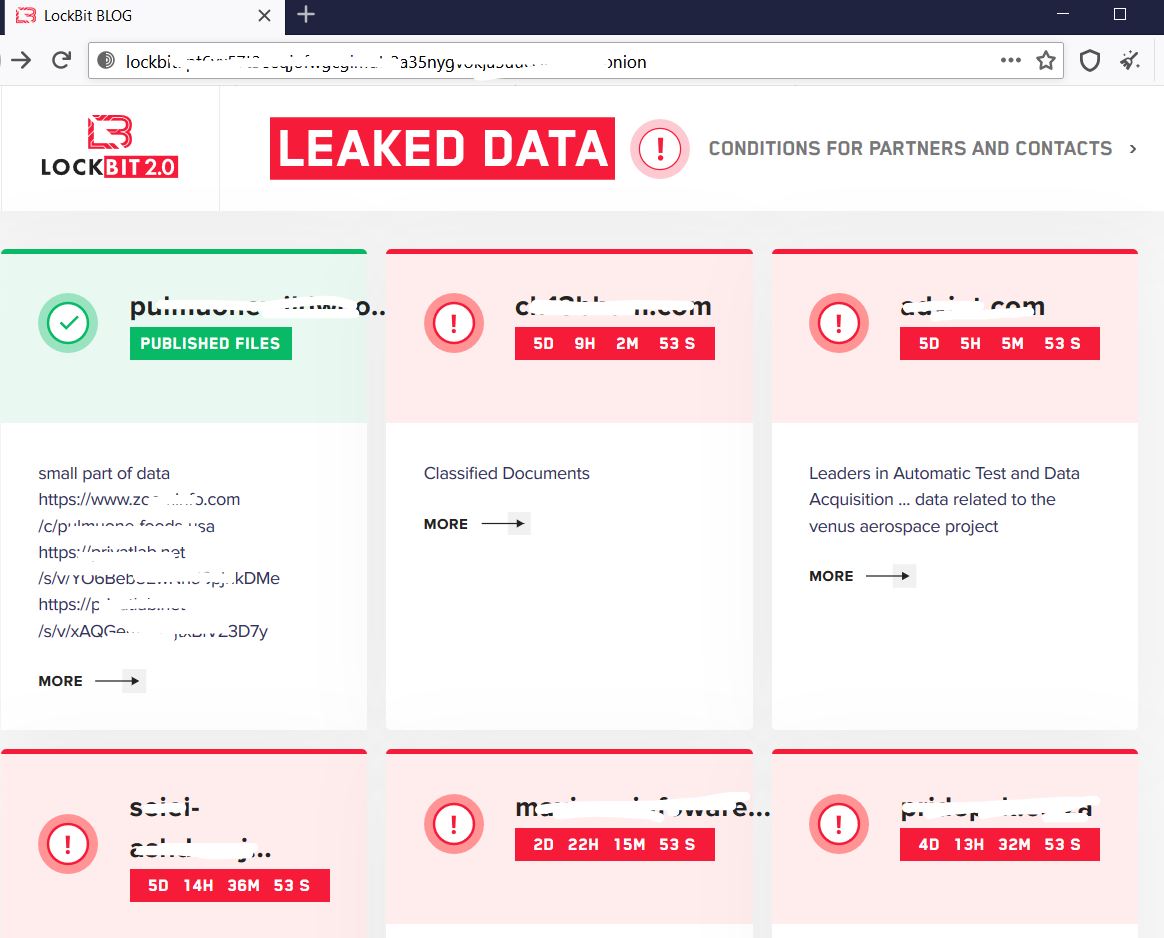
Lockbit 2.0, the ransomware behind the Accenture breach
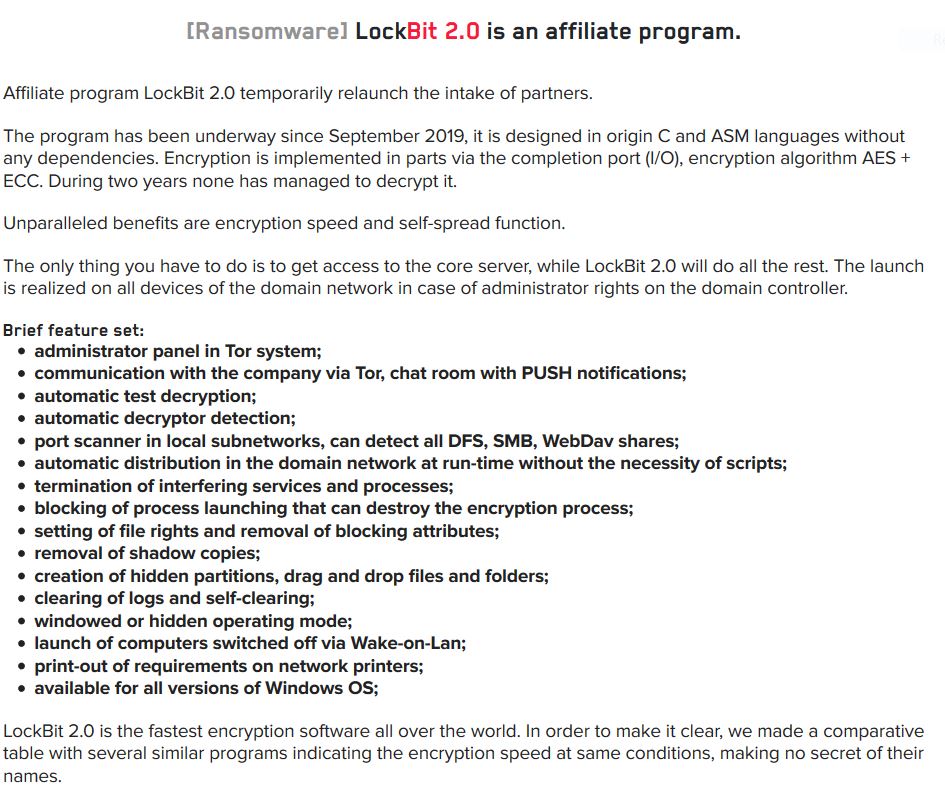
Lockbit ransomware has been around since 2019 but recently released an updated version called Lockbit 2.0. It is another ransomware-as-a-service (RaaS) which is a subscription based model allowing partners to use a full-featured already developed ransomware app ready to carry an attack. On their website, they boast their 2.0 version as being the fastest encryption software as well as the fastest upload of stolen data amongst myriads of many other popular ransomwares, all while highlighting the many features of this ransomware.
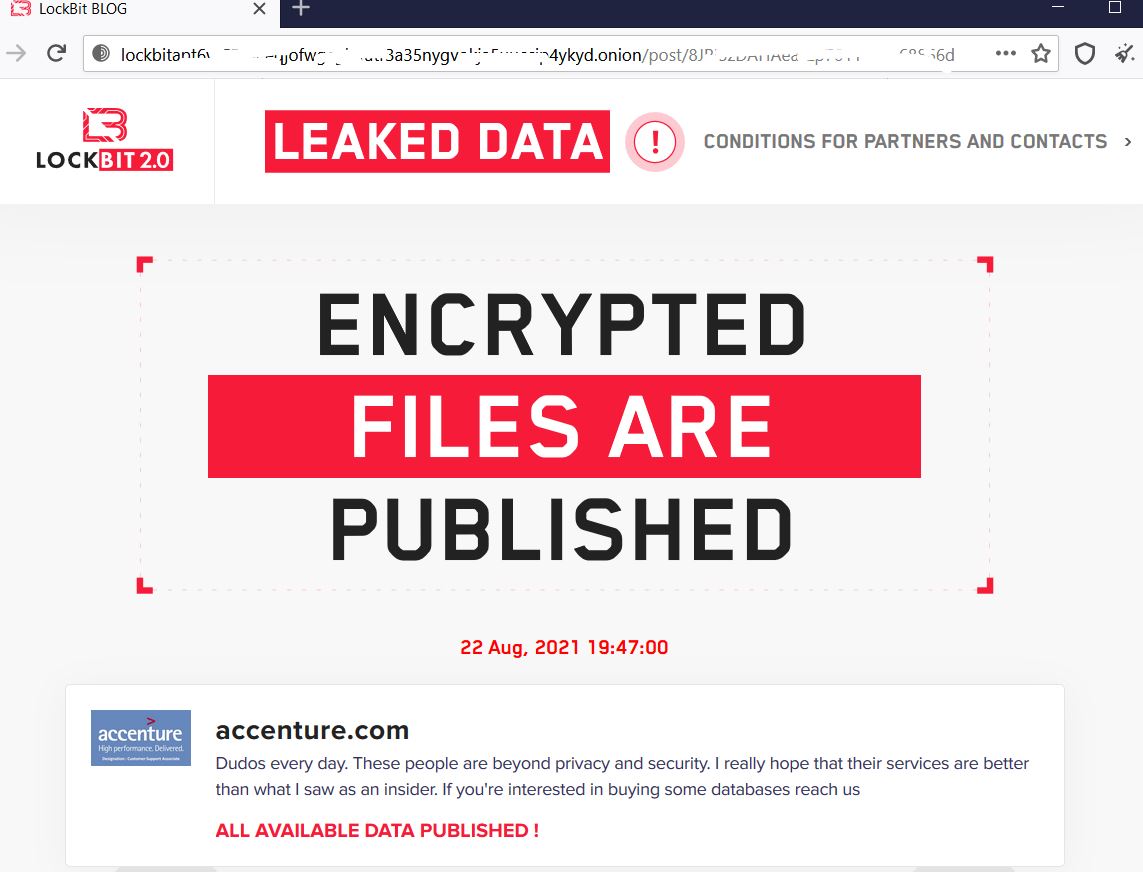
Recently, there were reports of targeted attacks with Accenture being the latest prominent victim of this ransomware. For non-payment, Lockbit has started leaking their data on their website to the public.
Infection cycle:
Upon execution of the ransomware, it disables all running security programs and any other means that could permit system recovery. It spawns a cmd exe to run the following commands:

- vssadmin delete shadows /all /quiet
- wmic SHADOWCOPY /nointeractive
- wmic shadowcopy delete
- wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
- wbadmin DELETE SYSTEMSTATEBACKUP
- wbadmin delete catalog -quiet
- wevtutil cl system
- wevtutil cl security
- wevtutil cl application
- bcdedit /set {default} recoveryenabled No
It then proceeds to encrypt the victim’s files. All encrypted files bear the lockbit icon and a .lockbit file extension.
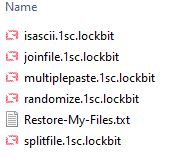
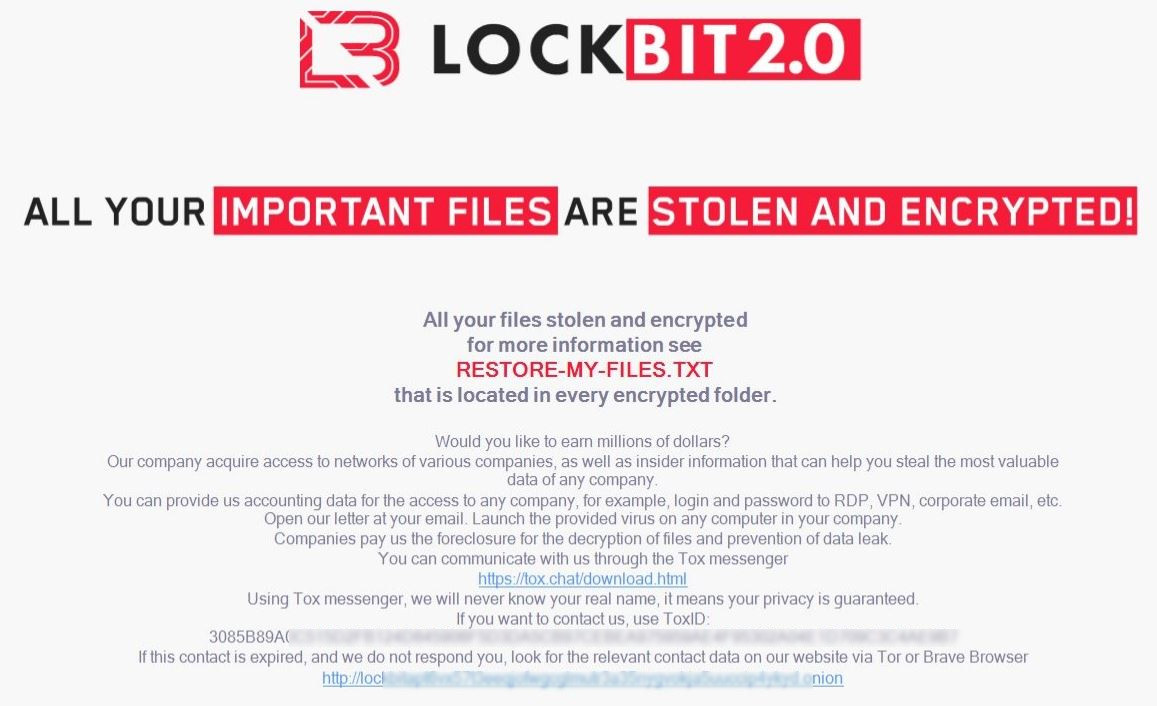
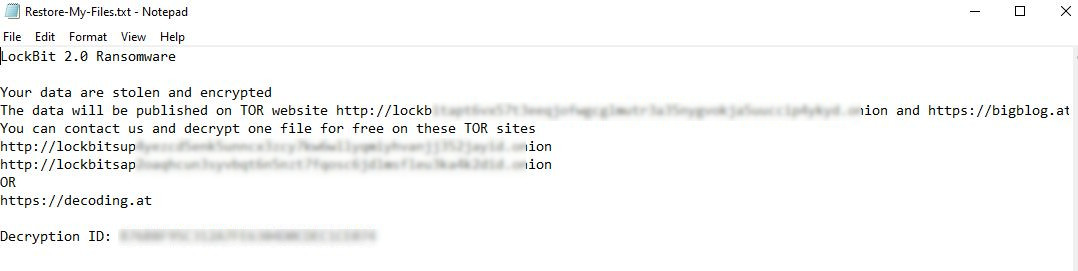
It changes the wallpaper with instructions on how to recover the files as well as adding a text file in every directory where files have been encrypted.
On reboot, the victim can’t miss the ransom note because it also adds a run key in the registry which loads an hta file that has the same instructions on how to get the victim’s files back.
- Key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Name: {2C5F9FCC-F266-43F6-BFD7-838DAE269E11}
- Data: %Desktop%\Lockbit_Ransomware.hta
It then proceeds to delete itself and no copy of the ransomware nor its components is left in the victim machine.
On Lockbit’s website, there are quite a few victims whose data have already been leaked to the public while others still have some days left to submit payment before facing the same consequence.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Lockbit.RSM_2 (Trojan)
- GAV: Lockbit.RSM_3 (Trojan)
- GAV: Lockbit.RSM_4 (Trojan)
This threat is also detected by SonicWall Capture ATP with Real-Time Deep Memory Inspection (RTDMI) and the Capture Client endpoint solutions.