GandCrab Ransomware Windows PE
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity in May for GandCrab Ransomware. GandCrab is well known across 2018 and 2019 as ransomware-as-a-service (RaaS). The RaaS model allows affiliates to attack victims with minimal effort. GandCrab encrypts critical data files, demands ransom payments and escalates if the victim delays payment. Once the victim provides payment, their data will be decrypted with a secret key that is provided once the payment is completed. The kill chain for this sample is a 32 bit PE file with resource files that are encrypted. The resource will be decrypted and placed on your system then executed through ShellExecuteExW. Once executed the infection will spread across well known files and network shares encrypting everything it can get access too.
Distribution Methods:
GandCrab has seen many distribution methods in the past such as Javascript and Document downloaders attached to e-mails. Along with Drive-By downloads using exploit kits such as Grandsoft, RIG, and Magnitude. It’s much easier for an attacker to use an exploit kit. Exploit kits usually require a browser and trivial passing of an address link to the victim. The victim just needs to click on the address link to get infected. Exploit kits are usually developed for each Operating System version. So, the Operating System would have to be vulnerable in order to use such an easy method. This is also why the current GandCrab is using e-mail Javascript, and Document downloaders. More recent GandCrab campaigns have been seen using Encrypted Documents containing a password to open the document.
Sample Static Information:
Sample Overview:
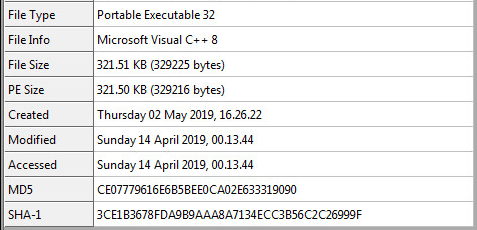
SHA-256 Hash: bbbb28aaa1050337356d9931a03533a522cd911e17aac2ac5003915419b126d7
Packer Information:
This sample has aPLib Compression and an Entropy of 7.31:
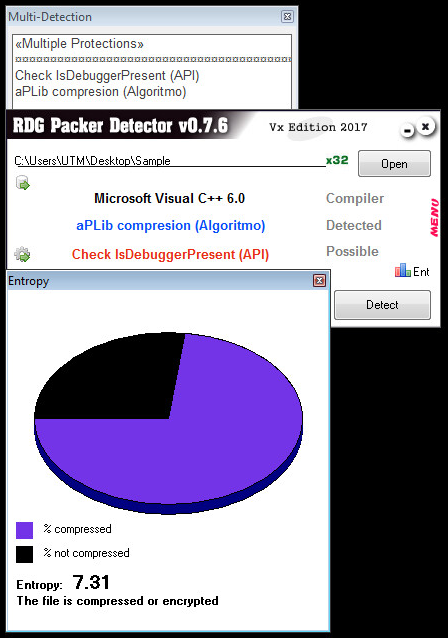
Unpacking The Sample:
The sample is not packed, only compressed with aPLIb, so this makes the sample easier to research inside Ida Pro:
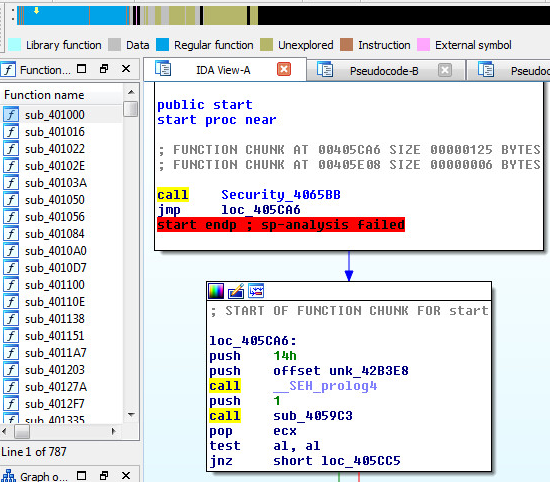
We can also see that the malware has about 787 functions available to research.
HTTP Network Objects:
The domain the sample connects to is “carder.bit” and another ip associated is “4.7.93.154”.
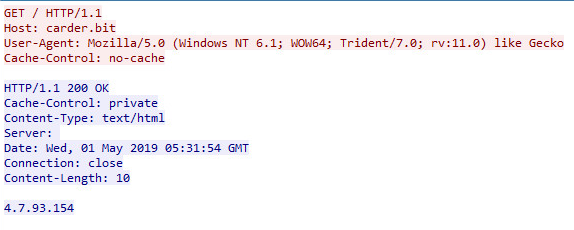
The ransom id is also sent through the network.

Closing Processes:
The sample contains a list of hardcoded process names which are closed and terminated before the encryption starts. This solves a handle issue that might arise when trying to encrypt the following list of processes.
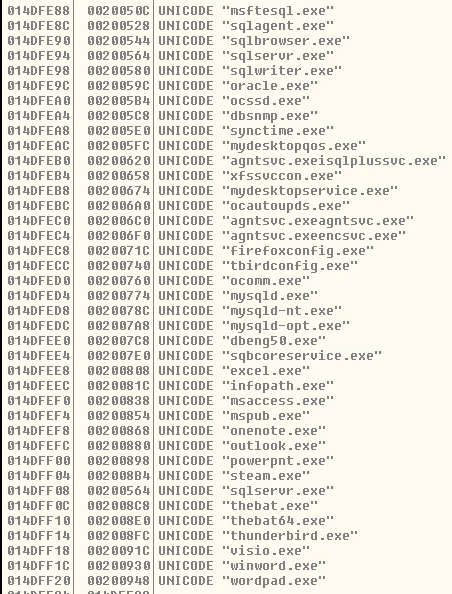
List of User-Mode Anti-Virus Detections:
Compares running processes with hardcoded Anti-Virus executable process names.
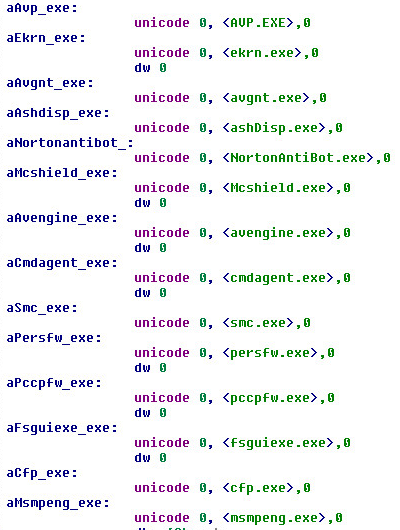
List of Kernel-Mode Anti-Virus Detections:
Kaspersky:
F-Secure:
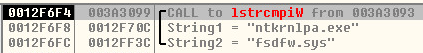
Symantec:
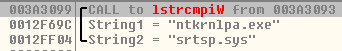
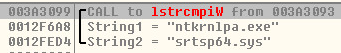
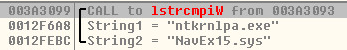
Ransom Strings:
This sample has pretty complex encryption and decryption techniques mostly for Anti-Analysis. This is what was found after a few rounds of decryption.

Debugging System:
The sample was tested and debugged on (x86) – 32 Bit, Windows 7 Professional.
Summary:
GandCrab ransomware is a well-known malware that is distributed with multiple exploit kits, email spam and the Dark Web. GandCrab is Russian in origin, and targets many different countries in 2019 such as the US, Australia, Sweden and Canada. GandCrab currently has many active affiliates over the web and thousands of samples scattered across the wild in 2019. It’s estimated that ransom payouts in 2018 reached millions of dollars.

Hit Graph & Statistics:
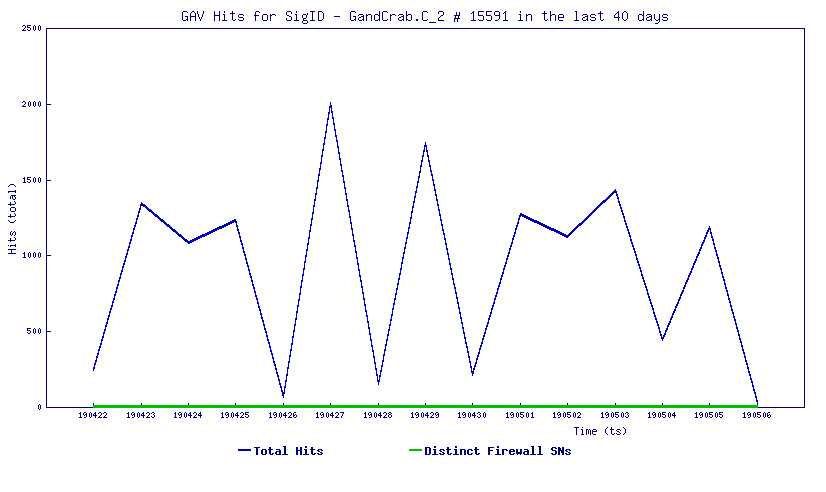
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: GandCrab.C_2




