GitLab CE and EE Kroki Diagram Stored XSS Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
GitLab is a web-based platform for software development and collaboration, offering a comprehensive suite of tools for version control, continuous integration, and continuous deployment. It comes in two editions: Community Edition (CE) and Enterprise Edition (EE).
The Community Edition is an open-source, self-hosted solution that provides core features for project management, code repositories, and collaborative development. It’s suitable for smaller teams, individual developers, and organizations that require basic functionality. The Enterprise Edition, on the other hand, is a commercial offering that includes all the features of the Community Edition, along with advanced features tailored to the needs of larger organizations and enterprises. EE offers enhanced security, compliance, and performance, as well as premium support options. This edition is available in different tiers, such as Premium and Ultimate, to cater to varying business requirements and budgets.
A cross site scripting vulnerability has been reported in GitLab Community and Enterprise Editions. The vulnerability is due to improper validation of user input of kroki diagrams.
A remote, authenticated attacker could exploit these vulnerabilities by sending crafted requests to the target server. Successful exploitation could result in arbitrary script execution under the security context of the target user’s browser.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-0050.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.4 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:L/E:U/RL:O/RC:C).
Base score is 7.4 (AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is low.
• Impact of this vulnerability on data integrity is low.
• Impact of this vulnerability on data availability is low.
Temporal score is 6.4 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
GitLab’s kroki diagram generation process enables users to create and embed various types of diagrams within their documentation using GitLab Flavored Markdown (GFM) or CommonMark formatting. Kroki supports a wide range of diagramming languages, such as PlantUML, Graphviz, Mermaid, and more, making it a versatile and valuable tool for developers to visually represent complex ideas and workflows. While this feature enhances GitLab’s capabilities, it also introduces potential security risks, as demonstrated by the stored XSS vulnerability discussed below.
A stored cross-site scripting (XSS) vulnerability is a type of security flaw that allows an attacker to inject malicious scripts into a web application. These scripts are then executed in the context of the user’s browser. In the case of GitLab, this vulnerability is reported to stem from improper input sanitization during the kroki diagram generation process. Input sanitization is a critical security measure involving the removal or modification of user inputs to prevent malicious code execution within the application.
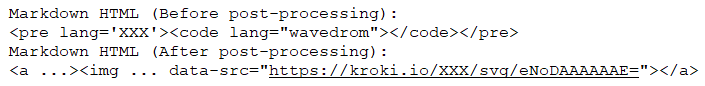
The vulnerability in GitLab occurs when code is processed and the “pre (lang)” attribute is copied to the “img (data-src)” attribute without proper escaping. Attackers can exploit this by using a “(pre)(code)” HTML block instead of the standard code block syntax and providing a malicious “lang” attribute. The example below illustrates how Markdown HTML changes before and after post-processing, resulting in an altered data-src attribute that can be used to execute malicious code.
To exploit this vulnerability, a remote, authenticated attacker would need to create a node with a malicious description within GitLab. If successful, this could result in arbitrary script execution in the target user’s browser, potentially leading to the compromise of sensitive information, unauthorized access, or other malicious activities.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
• The attacker must have authorized access to a user with the ability to submit GitLab markdown to a page.
• The target system must have kroki diagrams enabled.
Triggering Conditions:
The attacker authenticates to the target system as a user with the ability to submit GitLab markdown to a page. The authenticated attacker submits malicious markdown.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 3676 GitLab Kroki Diagram XSS 1
• IPS: 3677 GitLab Kroki Diagram XSS 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating to a non-vulnerable version of the product.
• Filtering attack traffic using the signature above.
• Disabling kroki diagrams.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory