Github hosted Android ransomware being misused in the wild
Github is a platform which is commonly used to host open-source projects, many such projects are security focused. SonicWall Threats Research team recently identified an Android ransomware that was found to be hosted on Github as an educational project.
Initial Discovery
We identified an Android apk (MD5: 6dc068db642247295e96437d8aca60a0) as malicious and upon inspecting its code found some interesting breadcrumbs which led us to the Github repository which was the origin for this treat. A simple search for the package name for this threat – com.termuxhackers.id – led us to the following Github repository:
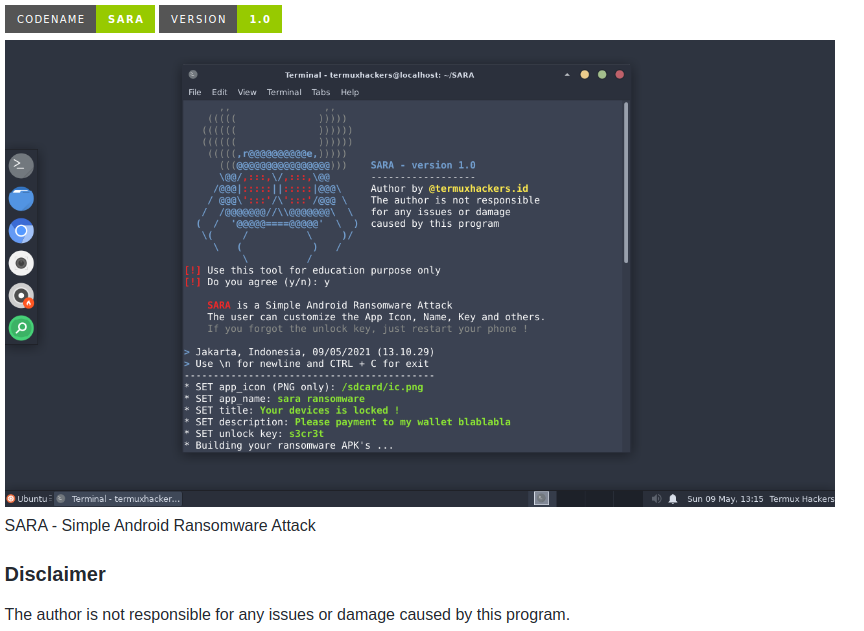
One of the repositories hosted here is SARA – Simple Android Ransomware Attack:
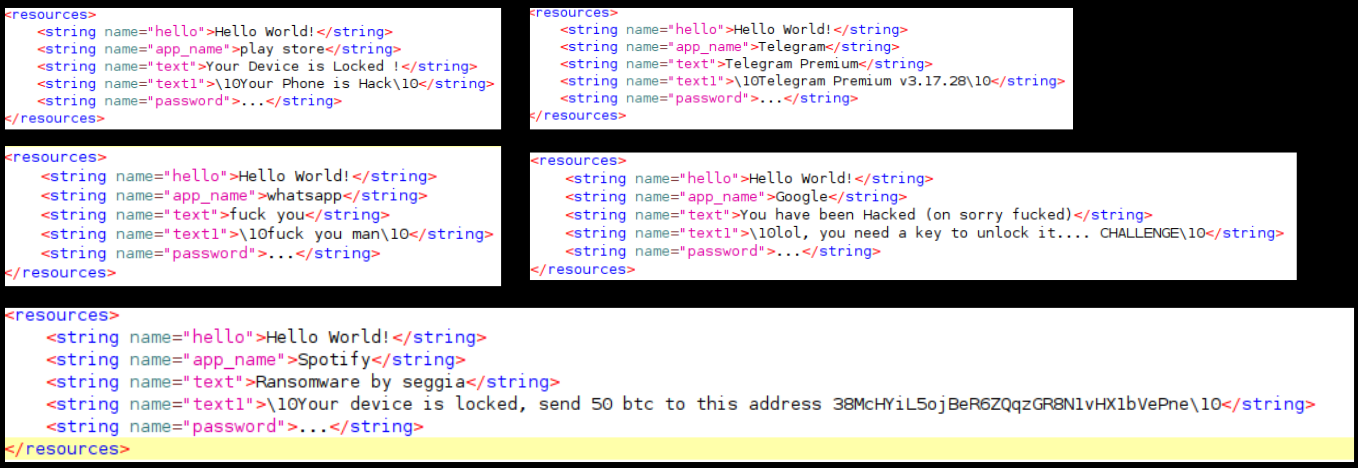
We identified a number of malicious apps on a number of platforms that were spawned using this codebase. A number of these apps are masquerading as popular legitimate applications, few are listed below:
We identified more than 200 apps that have been created using this codebase.
Creating the ransomware
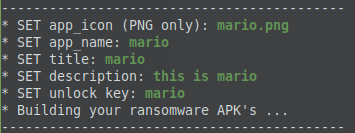
While building the apk, this kit asks the user to enter an unlock code:
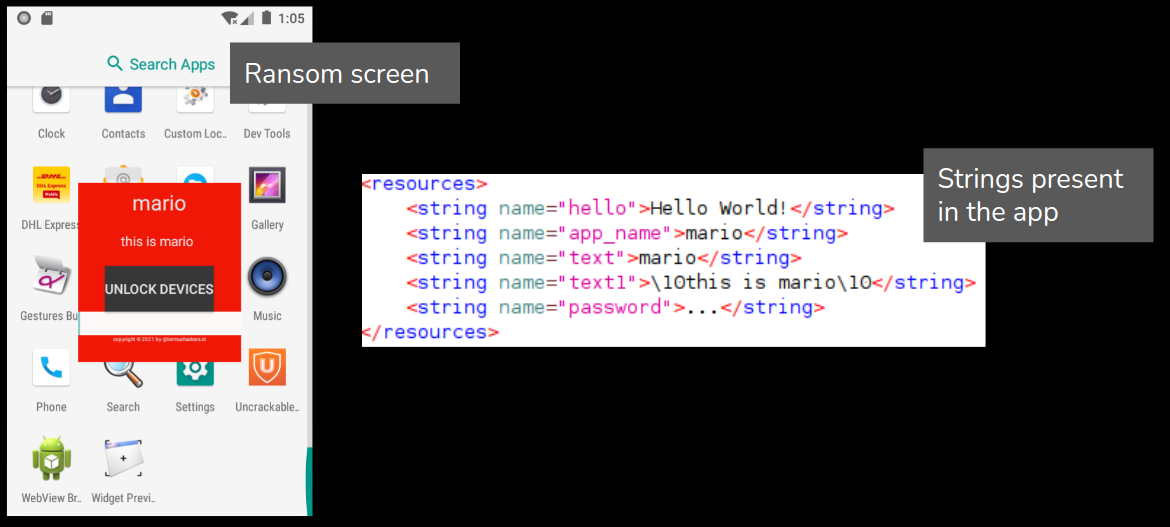
Once executed, a screen with user entered text is overlayed on the screen and the victim cannot use the phone. Strings present in the strings.xml in the app resource folders are used on the ransom screen.
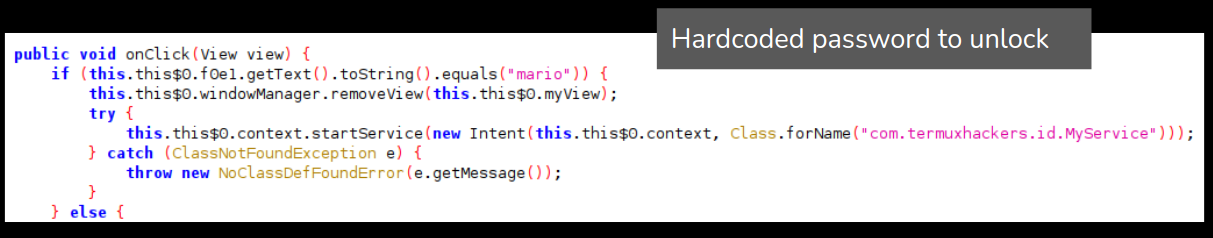
The unlock key is hardcoded in plaintext within the apk. The unlock key is added by the user during the app creation:
We analyzed a bunch of malicious apks, one instance in particular stood out where the ransom demand was 50BTC:
Overall this repository was created and distributed on Github for what appears to be educational purposes. However we identified a high number of apps created using this repository with legitimate app icons and application names. Whether this was created as a prank, with malicious intentions or to legitimately learn how ransomware works is yet to be determined.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Termux.RSM
Indicators of Compromise:
- 00dc92f14326c7b0e87e877bfd12a7df
- 6b9157e059da44f13843e682ac3bcba7
- 6dc068db642247295e96437d8aca60a0