GigaCLR Trojan – Quad Layer GigaRun Custom Loader
Overview:
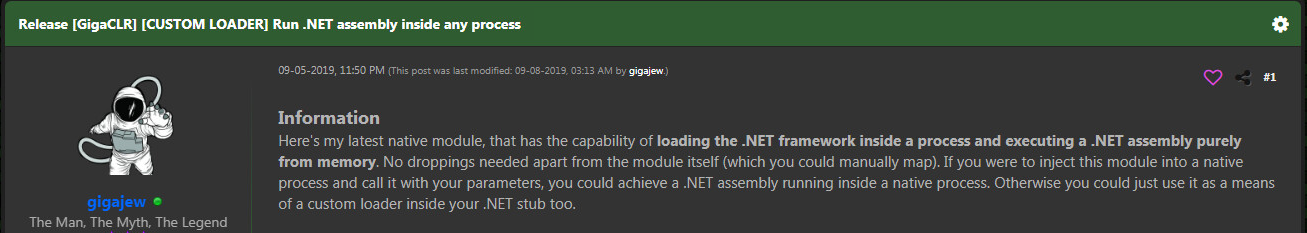
SonicWall Capture Labs Threat Research Team recently found a new sample and activity in March for the GigaCLR Trojan binary. It starts out as a self-extracting native executable, drops two binaries. One a .NET sample, and the other a native Win32 .dll library binary. The .NET binary is called DEO, this will call an exported function within the library called “GigaRun”. GigaRun is apart of the “GigaCLR” Custom loader. Which allows injection of .NET binaries into any native process. Once the payload is injected into the process it will decrypt a picture resource and run the malware on the operating system. This sample has four layers until you reach the core of the malware.
Samples: 1st Layer, Static Information:
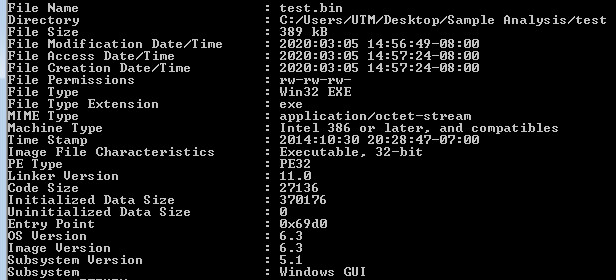
Looking at the first layer in CFF Explorer, checking for corruption. The first layer is a Native Win32 binary.
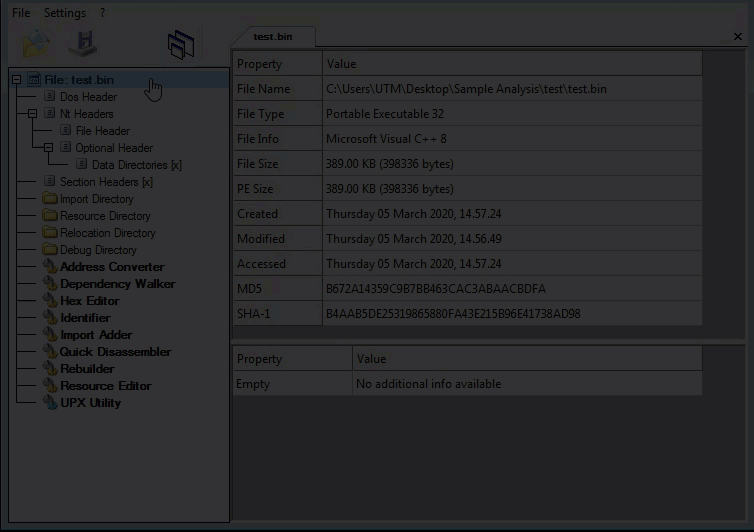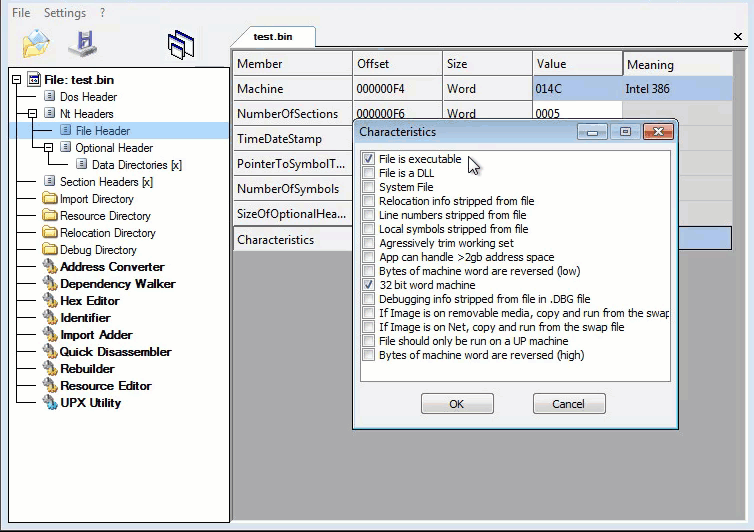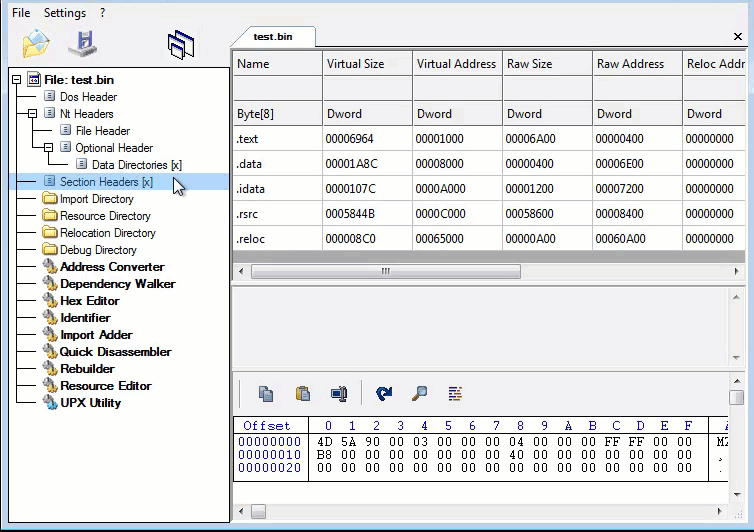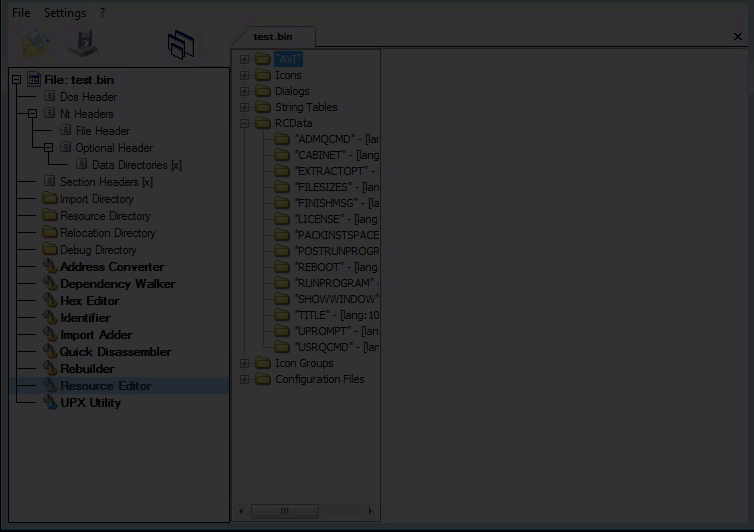
Command line static information:
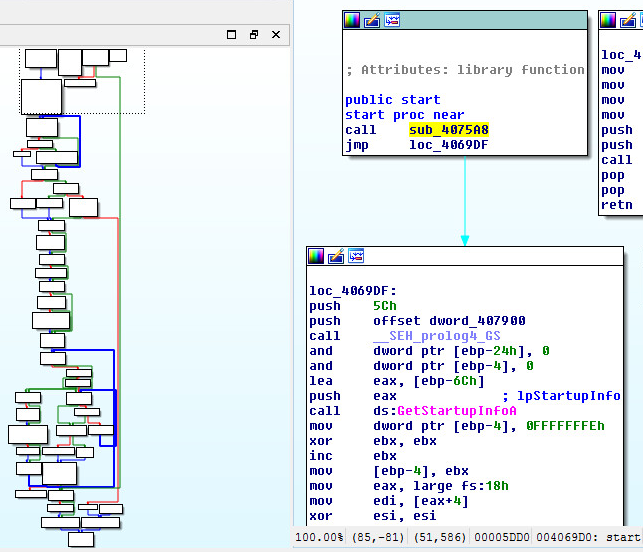
Main starting routine:
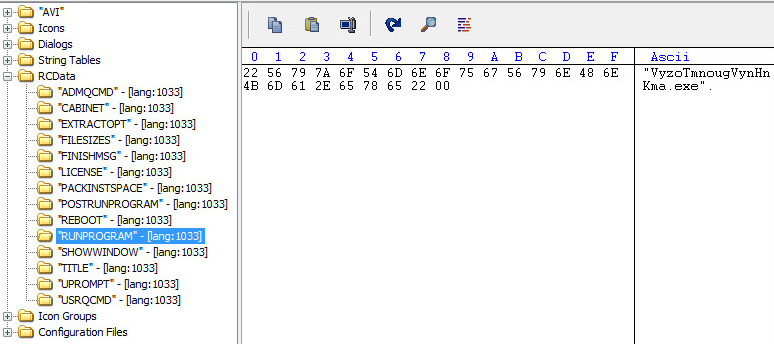
Resources
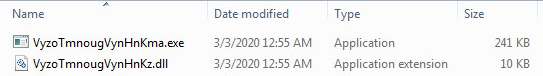
At this point, we can tell from the resources that this is a self-extracting installation binary. So, we can go forward with our research by unzipping the sample. Once decompression is complete you will see the following files:
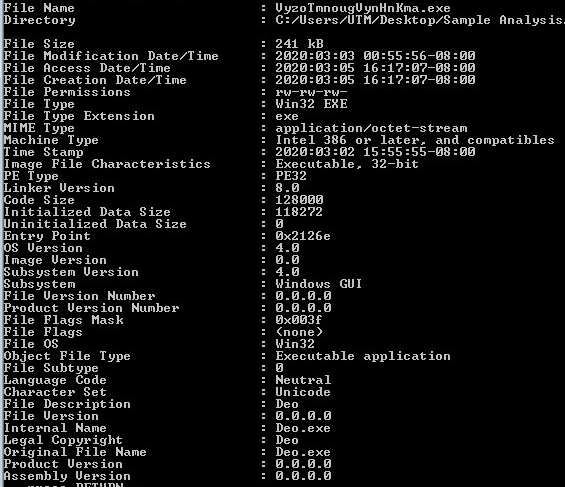
Samples: 2nd Layer, Static Information:
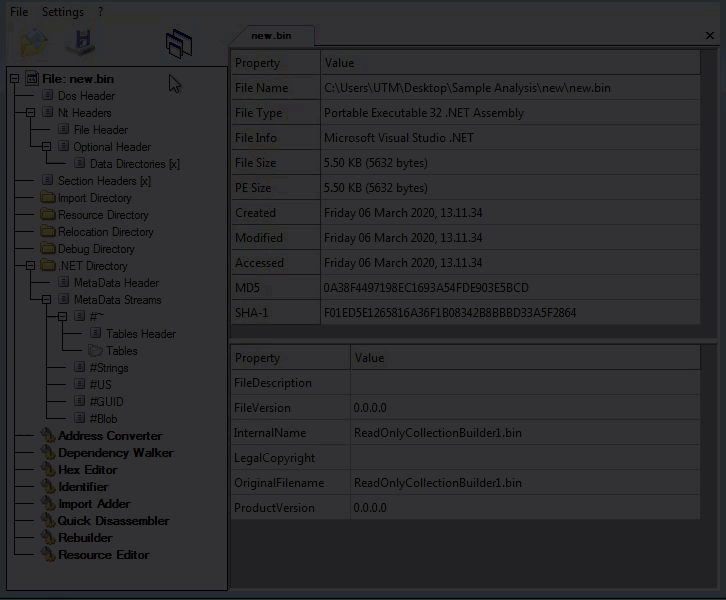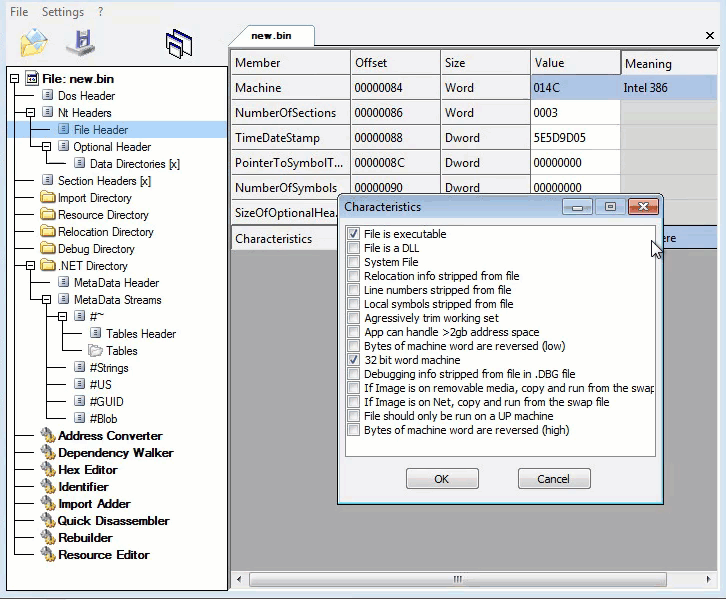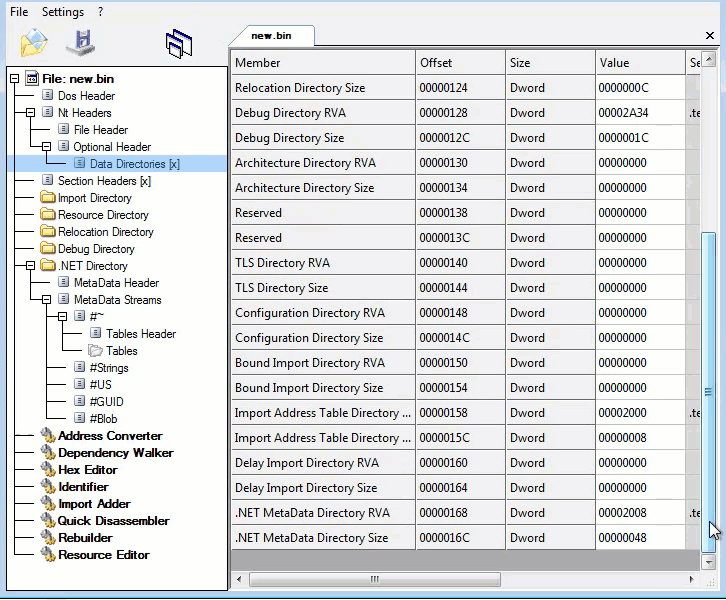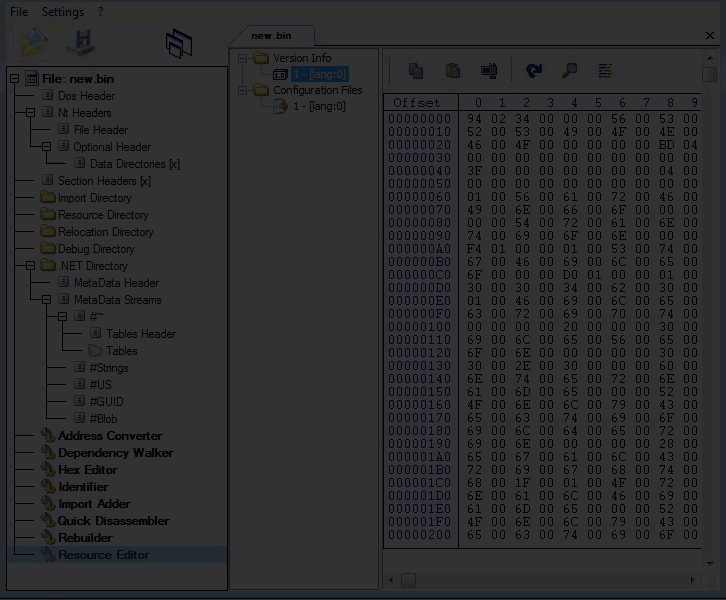
Looking at the second layer in CFF Explorer, checking for corruption. The second layer is a .NET binary.

Command line static information:
Main starting routine inside Ida Pro:
Main starting routine inside .NET Reflector:
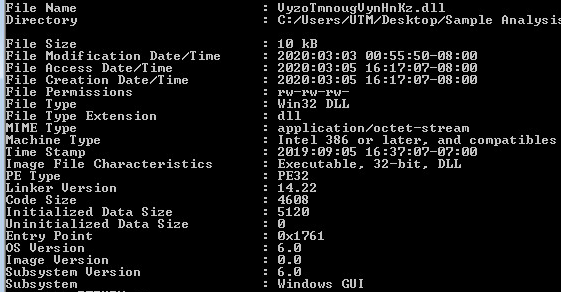
Samples: 3rd Layer, Injection Static Information:
Looking at the third layer in CFF Explorer, once again checking for corruption. The third layer is a .dll native Win32 binary.
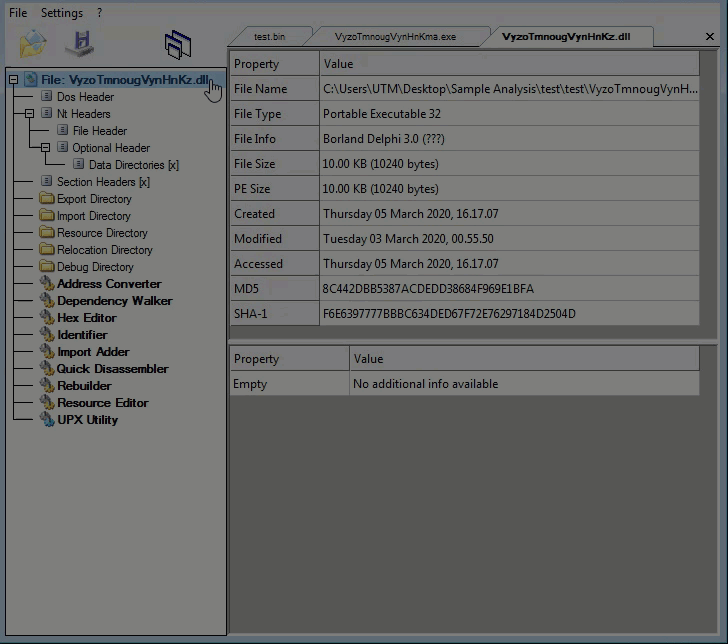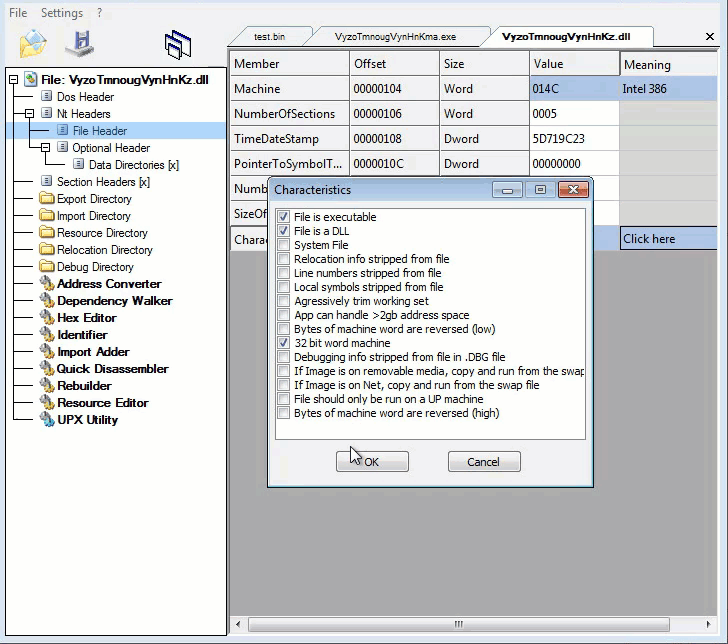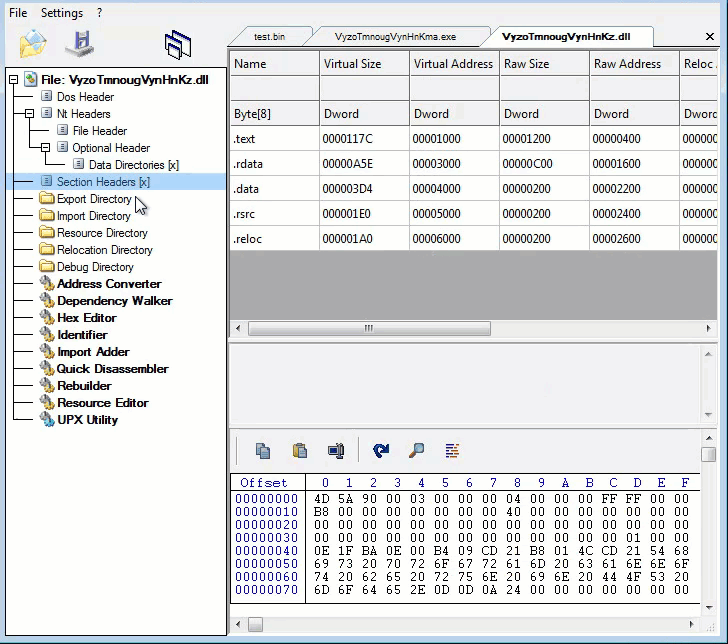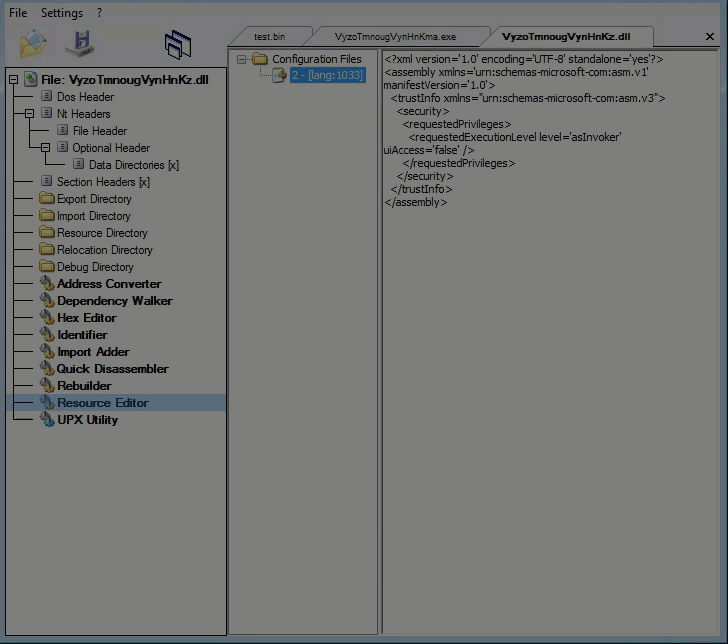
Command line static information:
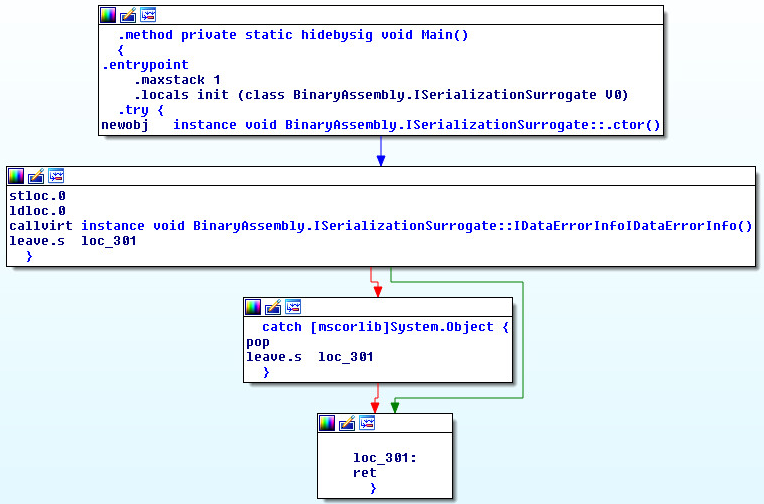
Main starting routine inside the .dll library:
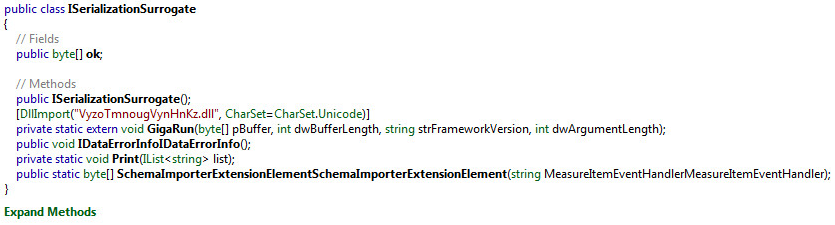
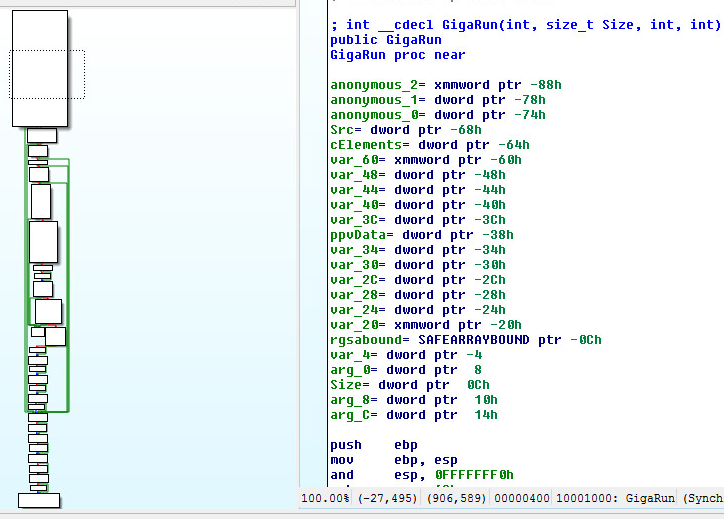
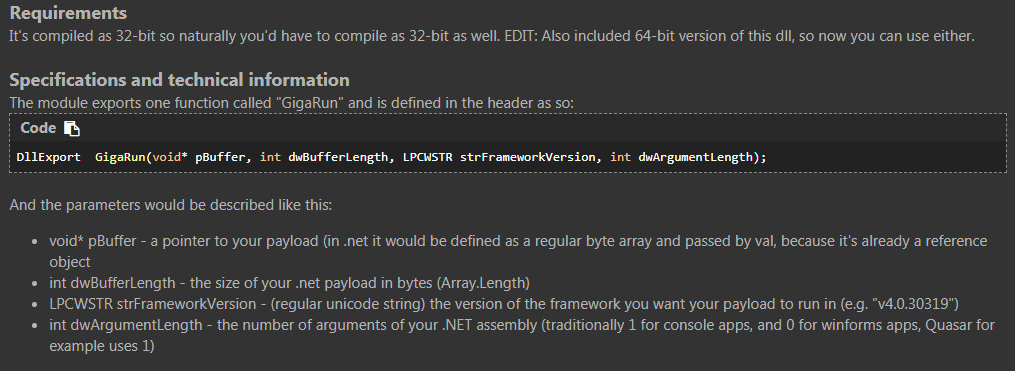
GigaCLR Custom Loader:
GigaRun Library Call Disassembled:
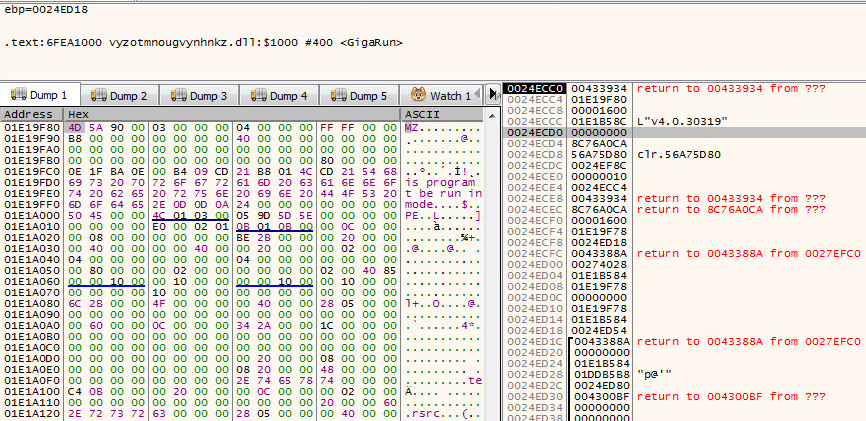
We can trap the call and look at the parameters of this special function:
Here we see the buffer with a newly created file. The 4th file, and it’s size are on the stack. Now we can dump the payload. It’s 1600 hex in size.
Samples: 4th Binary, The Payload:
Here we can see the payload used in parameter 1 of the GigaRun routine:
Payload Main inside .NET Reflector:
As you can see the 4th Binary will lead into the another decryption of the resource picture to finally reach the main malware.
Supported Systems:
- All Windows Operating Systems…
Summary:
The GigaCLR Trojan allows injection into any process. There are pieces of forensic data, such as looking at the .dll exports for the GigaRun function. This function allows the injection to take place. The first parameter holds the payload of the malware. Using this technique, the malware author can inject any payload into any process. SonicWall has captured the following forensic artifacts within the signature below.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: GigaCLR.NT
Appendix
Sample Hash: f87bcda31a5e53ebac41f3c994883bcdf3f92f2579c82a33100d11d696160b34