Free game download links spread via Facebook come with free Infostealer
Even back in the day, cybercriminals have been masking malware within pictures, screensavers or games that can be downloaded for free. But now, since the Internet has grown immensely into a huge form of entertainment for everyone especially with the popularity of social media, the threat from free downloads has greatly multiplied. This week we have come across free game download being distributed on Facebook which installs malware.
Infection cycle:
The sample we observed purportedly installs a free Nintendo Super Mario game. The main installer uses the following icon:
![]()
Upon execution it displays a fake splash screen that appears to install the game.
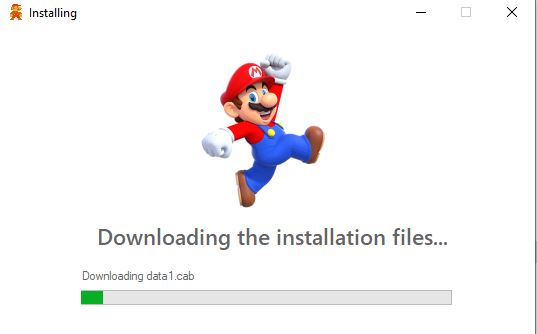
But instead it drops a Trojan along with a few legitimate libraries and python packages which it uses for a robust set of functionalities including data gathering and reconnaissance, downloading additional software, messaging functionality, receive commands from a remote server and more.
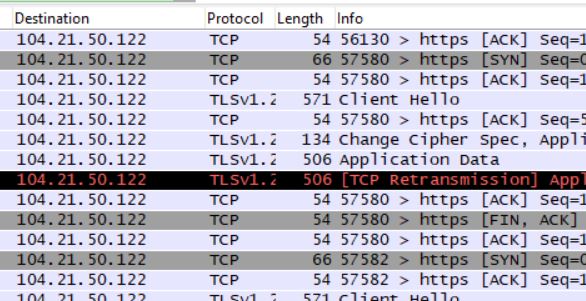
No game is installed but upon successful installation, the Trojan, janma.exe, runs in the background and begins gathering information about the victim machine like querying system security settings, browser settings, etc.
It intermittently sends and receives data from a remote server.
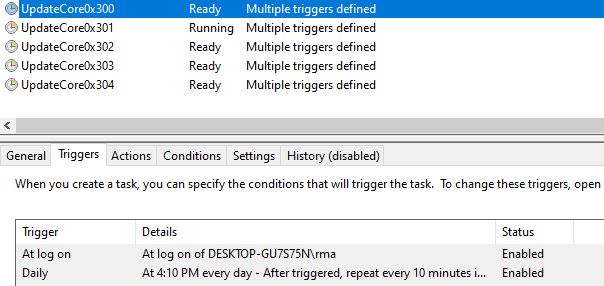
To maintain persistence it adds 5 scheduled jobs named “UpdateCore0x” to run a copy of the Trojan upon logon and every 10 minutes.
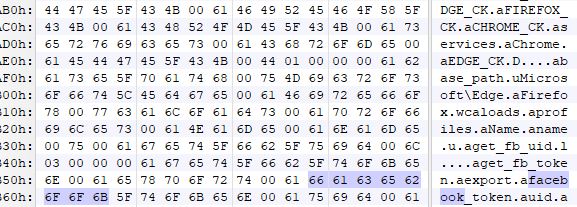
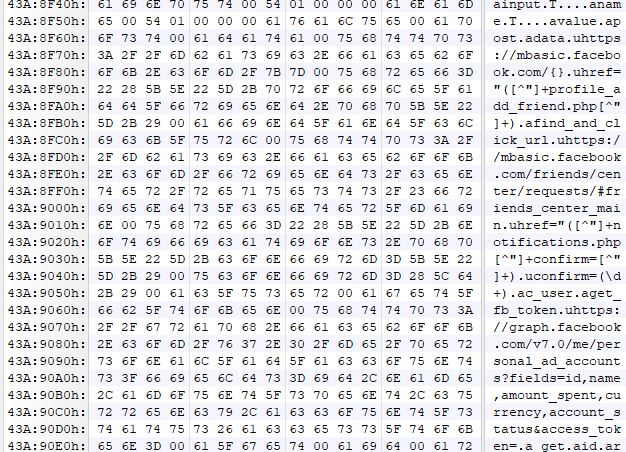
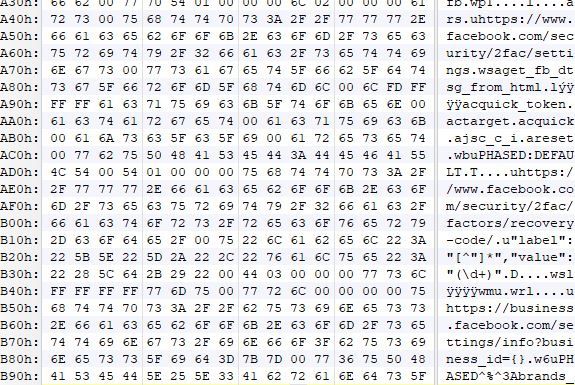
During further analysis, we observed that this Trojan gathers a lot of Facebook account information that might be available on the victim’s machine.
It gathers login information that might have been saved in the internet browsers.
It has the ability to add friends and confirm pending requests. In case the victim uses Facebook ad account, it has the ability to look at ad spent, retrieve ad ids, ad status and disable notifications, and therefore the victim will not be notified if there are any changes made on their ad account.
It also has the functionality to change Facebook security settings, check if the user uses two-factor authentication and to retrieve recovery codes.
This extensive amount of account information gathered can presumably be used to further this malicious campaign and spread via Facebook.
As always we urge our users to be vigilant and to be cautious of any free software download specially if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: FBSpam.FB (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.