Fake Zoom App installs a Cryptominer
With stay-at-home orders implemented in several states and cities in the country in an effort to slow the spread of the novel coronavirus, internet data usage has spiked with more people being online and confined to their homes. More people have been shopping for groceries online, making virtual doctor’s office visits, kids connecting to their online education portals, people working remotely and having virtual meetings or connecting with friends and relatives via online chat. The Sonicwall Capture Labs threat research team has analyzed several different coronavirus-related malicious online schemes since more people are connecting online from home with typically more relaxed security measures and cybercriminals are certainly taking advantage.
One videoconferencing software has gained so much popularity lately that cybercriminals have seen that as a perfect vector for their malicious activity. Zoom has become so popular that it is one of the most downloaded software applications. A malicious installer bundled with a crypto currency miner has been making the rounds online preying on unsuspecting users wanting to install this videoconferencing program.
Infection Cycle:
The Trojan uses the Zoom icon and comes as an Autoit compiled installer.
![]()
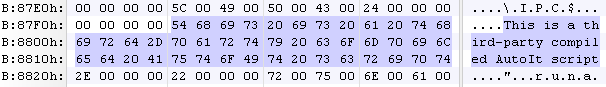
Upon execution it drops a legitimate Zoom installer and a cryptominer in the following directories:
- %Temp%\Zoominstaller.exe (legitimate installer)
- %Appdata%\Roaming\Microsot\Windows\helper.exe (cryptominer)
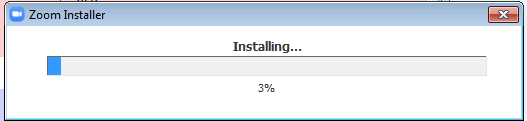
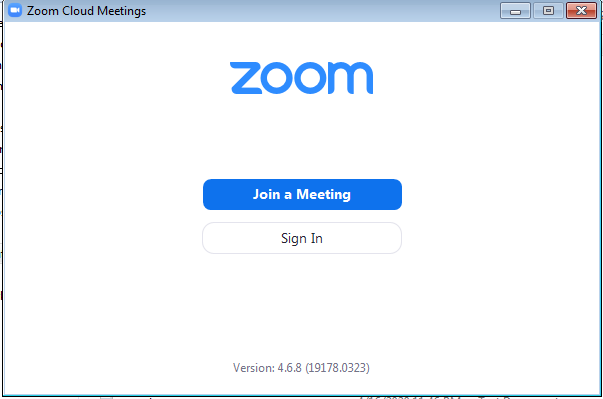
It will then execute the legitimate Zoom installer and a window will pop up to prompt the user of the program installation.
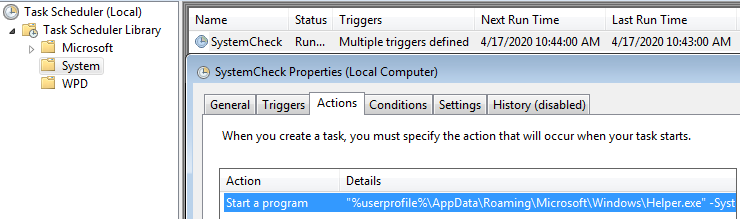
Meanwhile it adds the helper.exe as a ‘System Check’ scheduled task and then executes it.
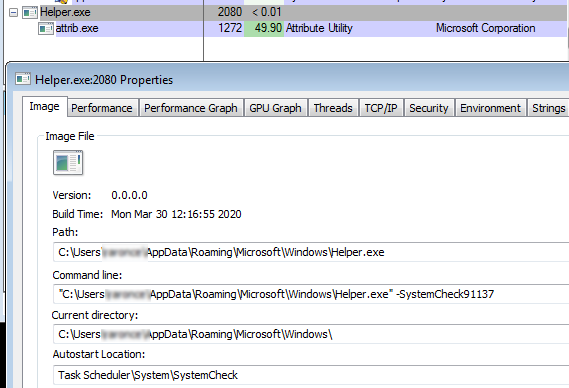
Upon execution of helper.exe, it creates a ‘Tor’ directory within %Appdata%\Roaming\Microsot\Windows\ folder and drops components of a Tor client.
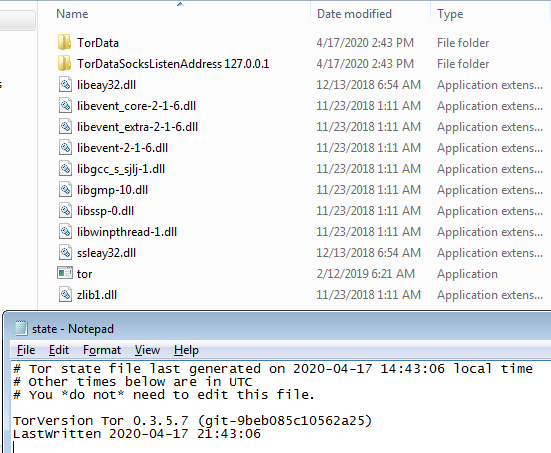
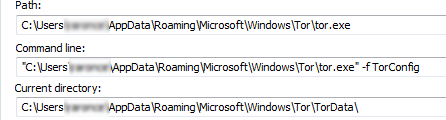
It executes the Tor client by running “tor.exe” to setup the proxy environment using its own config.
![]()
It then spawns attrib.exe (a legitimate windows system file) and uses it as a mining client and begin mining through the local Tor proxy using the following command:
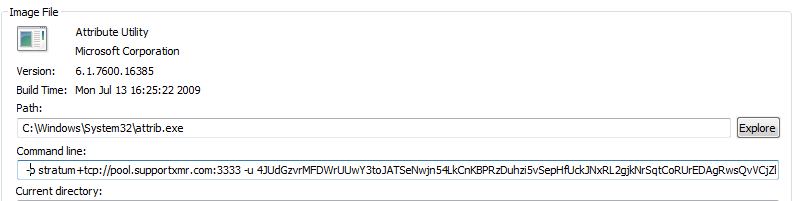
Once a mining session has ended, the Tor directory gets deleted and will just be recreated on the subsequent run, thus leaving very little evidence of infection.
We urge our users to only use official and reputable websites as their source of software installer. Always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Autoit.OLS_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions




