Fake Ransomware just overwrites MBR but demands payment
The SonicWall Capture Labs Threat Research Team have recently come across a fake ransomware trojan that pretends to hold a victim’s files hostage. Although its ransom message is intimidating and a Monero address is provided for $200 payment there is no encryption functionality present in the malware.
Infection Cycle:
The attacker has made no effort to hide the functionality of the malware. It was written in Delphi and is so straigtforward that even a simple listing of strings in the binary instantly reveal its purpose:
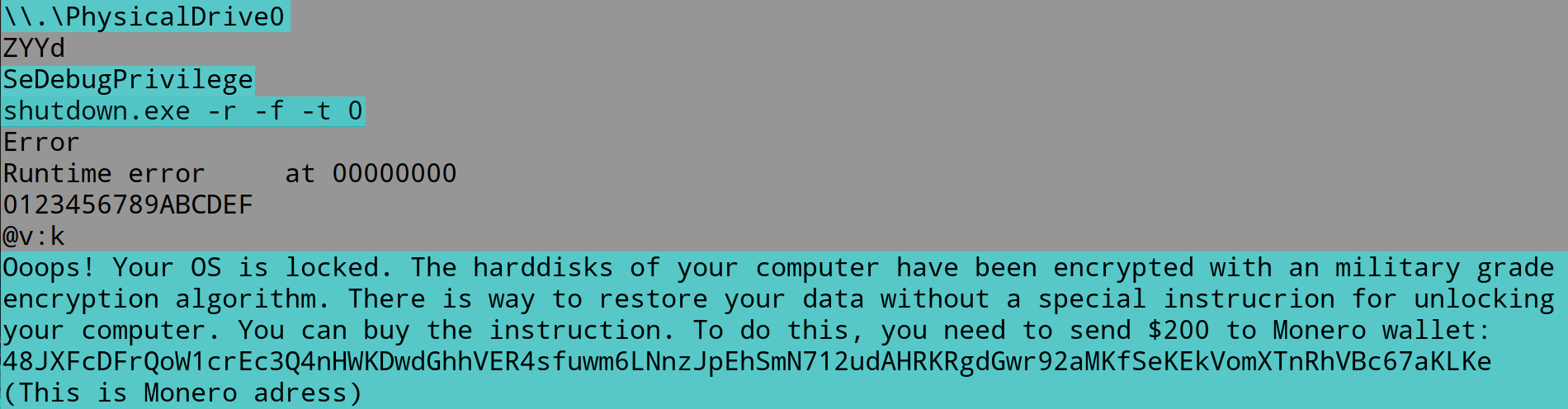
Running the executable through a debugger reveals its runtime functionality. The first step is to verify whether physical access to the system drive is possible using the CreateFileA and ReadFile API calls:
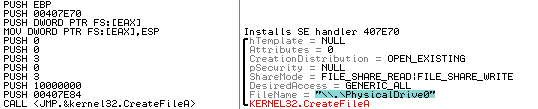
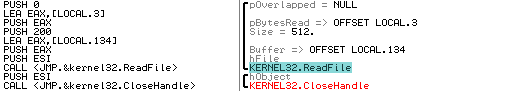
If the above test passes, it proceeds to open a handle to the physical drive again and overwrite the MBR using the WriteFile API call:
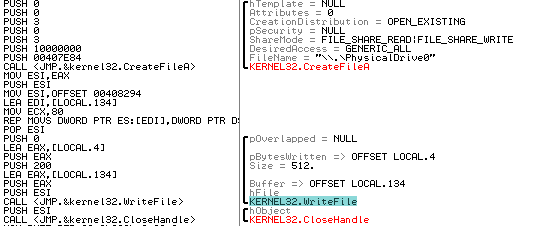
Arguments on the stack point to the ransom text to be displayed after reboot:
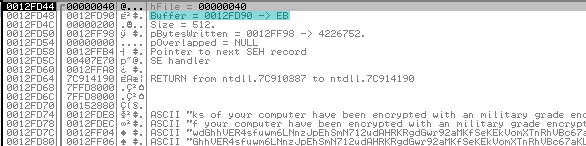
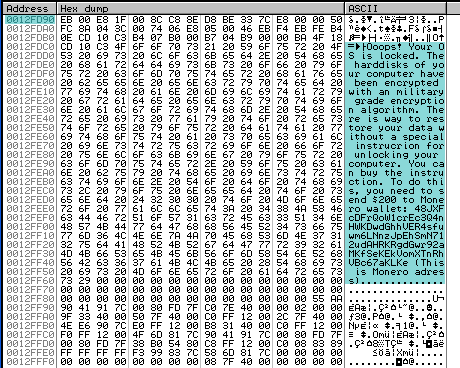
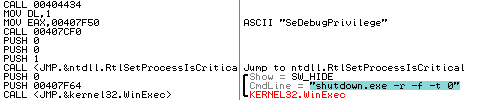
After succesfully overwriting the MBR with the ransom text, the trojan executes “shutdown -r -f -t 0” using WinExec to immediately reboot the system:
Upon reboot, the following ransom text is displayed and the machine is unable to boot as normal:
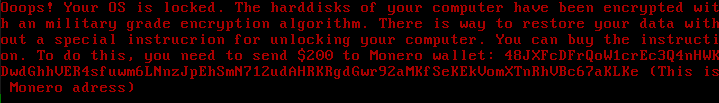
The only modification to the filesystem is the overwritten MBR. No files have actually been encrypted and there is no encryption functionality present in the malware. Although files can easily be restored by mounting the filesystem using a live OS booted via a memory stick, most users will likely consider their files gone and perform a full reinstall. There is no contact information provided to “restore” files and no way of verifying if paying the $200 in Monero will suffice.
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- GAV: KillMBR.RSM (Trojan)




