Fake Coronavirus site delivers Metamorfo banking Trojan
SonicWall Capture Labs Threat Research team has come across another variant of Metamorfo banking trojan that tries to take advantage of the global crisis due to COVID-19 pandemic.
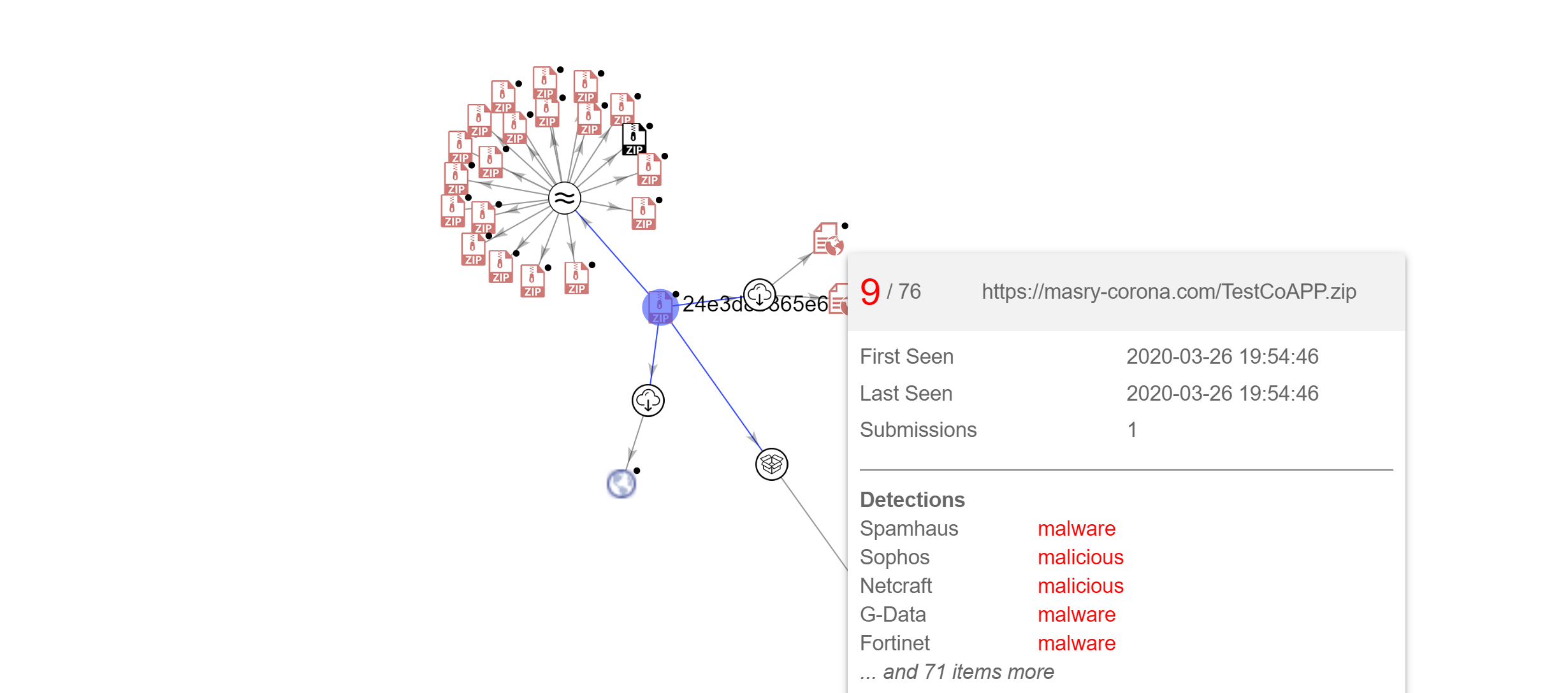
This malware was first seen 2 days ago and the domain “masry-corona” that hosts this malware was also created recently with “corona” in the domain name to attract people looking for information regarding coronavirus.
Infection Cycle:
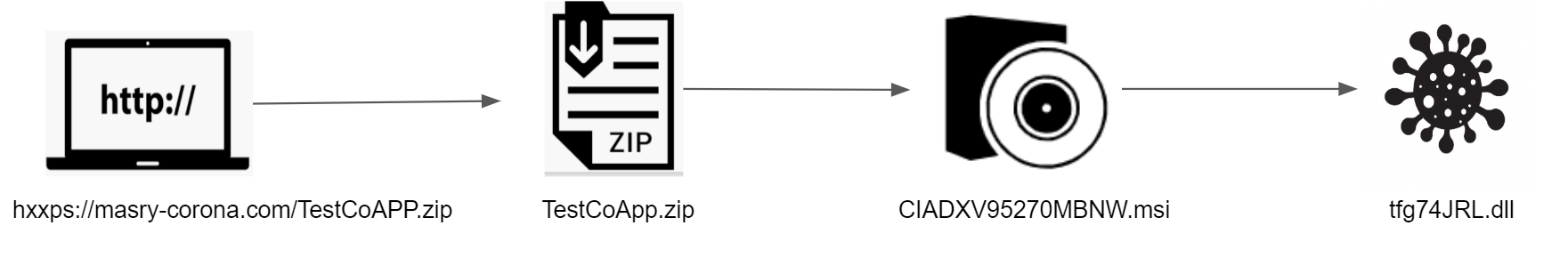
When the malicious web page “hxxps://masry-corona.com/TestCoAPP.zip” is visited, the Zip archive “TestCoApp.zip” gets downloaded onto the victim’s device, it is an archive of an MSI file named “CIADXV95270MBNW.msi”. Once clicked, it gets installed with the help of MsiExec.exe, a built-in Windows Installer.
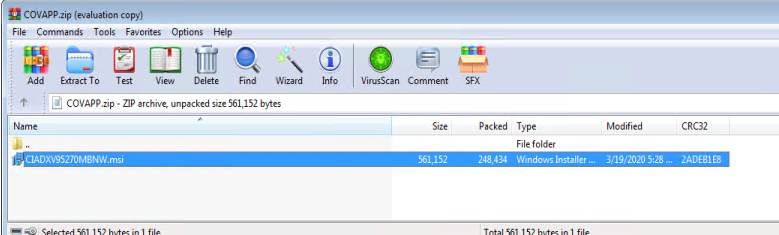
This MSI file has 48 streams in it and the stream “!_StringData” has the downloader JavaScript code obscured with huge garbage strings.
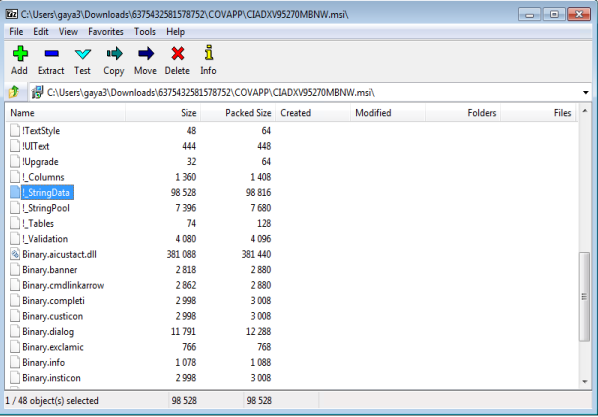
After extracting and de-obfuscating the !_StringData, we see the below JavaScript code, that downloads the malicious payload.

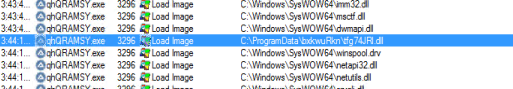
When the javascript code within the MSI file gets executed, it downloads a ZIP file from the URL “hxxp://la42.website/pro2/comprobante_771124.zip” using WinHttpRequest. ZIP file contains three files, it then gets decompressed into a 8-letter random string folder “bxkwuRkn” under “C:\ProgramData”. Also, the three files are renamed with 8-letter random strings, which were “qhQRAMSY.exe”, “8SkHjLCy” and “tfg74JRL.dll”.
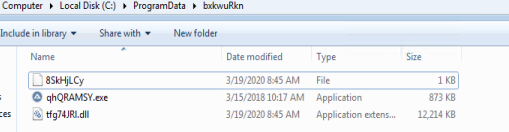
qhQRAMSY.exe is a legitimate AutoIt script execution program, whose original name was “AutoIt3.exe”.
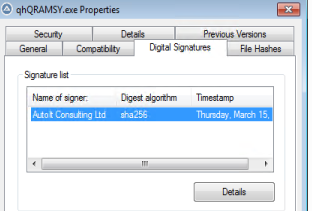
The actual malicious payload “tfg74JRL.dll” is a variant of Metamormfo. Metamorfo is a malware family that was observed targeting the customers of online financial institutions
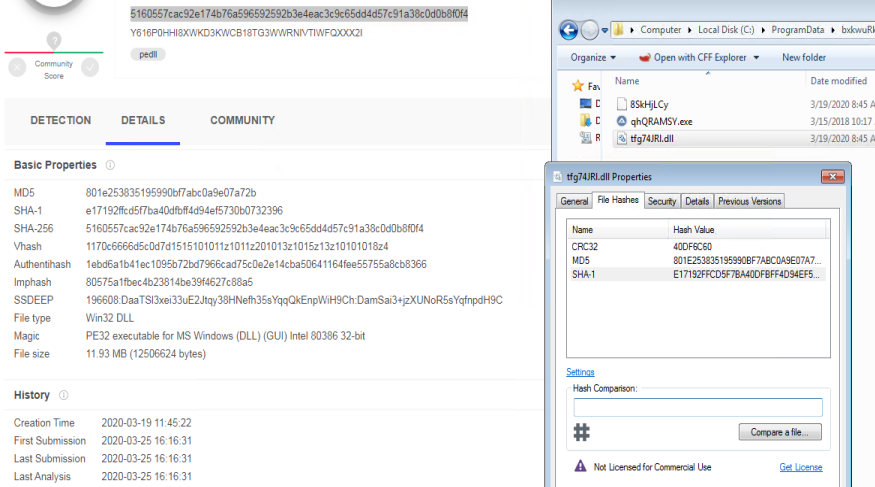
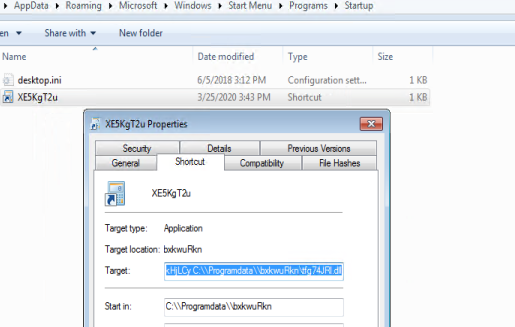
It gets executed with the command: “C:\\programData\\qhQRAMSY.exe C:\\Programdata\\bxkwuRkn\8SkHjLCy C:\\Programdata\\bxkwuRkn\tfg74JRl.dll“. AutoIt, a whitelisted process was being used to load the malicious dll to evade from antivirus detection.
Later, a shortcut file (LNK) was created with the above command in the Windows Start Menu folder to persist after system reboots.
It then modifies several registry key values to disable “AutoComplete”, “Use FormSuggest”, “FormSuggest Passwords”, “FormSuggest PW Ask” under the “HKCU\Software\Microsoft\Internet Explorer\Main”, and “AutoSuggest” under the “HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\AutoComplete”. This allows the malware keylogger function to record the victim’s input.

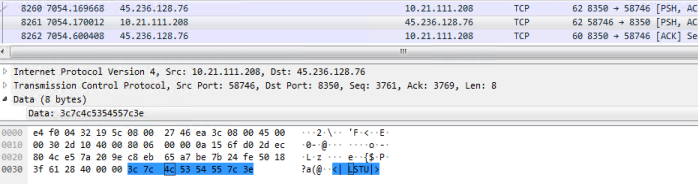
It connects with the command-and-control (C&C) server informing that it’s been has been infected. The below command “<|LSTU|>” is sent to the server, functioning like a heartbeat.
This variant also starts the Volume Shadow Copy Service (VSS) to create a shadow copy (system restore point) with malicious files in it. Volume Shadow Copy Service is a technology included in Microsoft Windows that can create backup copies or snapshots of computer files or volumes, even when they are in use.
Most antivirus software do not scan volume shadow copies for malware or other security threats. That could be why this malware tries to persist through system restore points and as well to evade from antivirus detections.

With VSS Service, a shadow copy gets created after the victim’s machine gets infected.

As we are responding to combat the coronavirus (COVID-19) outbreak in the real world, we must also focus on cyber hygiene.
SonicWall Capture Labs Threat Research team provides protection against this threat with the following signatures:
GAV: 8676 Metamorfo.DN
This threat is also detected by SonicWALL Capture ATP w/RTDMI.
IOCs:
URLs:
hxxps://masry-corona.com/TestCoAPP.zip
hxxp://masry-corona.com/TestCoAPP.zip
hxxp://la42.website/pro2/comprobante_771124.zip
hxxp://la42.website/pro2/comprobante_771124.zip
SHA-256:
24e3d85865e6046e747f993dfc3b732d3922e7a1f9a382198cf699a06d83a51f (Zip)
5d413bf1c985529c38399323a7c2698371319332241b4e9bf55a47b51857aca8 (MSI)
237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d (exe)
5160557cac92e174b76a596592592b3e4eac3c9c65dd4d57c91a38c0d0b8f0f4 (dll)
5e07234588a7af03453c082a23f03e41418a1f42fea9c5884f19d8df16ad0fa2 (script)
Domain:
masry-corona.com
la42.website
IP Address:
192.3.157.116
134.0.10.213





