Dew18 banker for Android targets Korean financial institutions
Bankers are one of the most widespread threats seen in the Android malware landscape. Most of these threats target specific banks and steal login credentials, credit card numbers and other sensitive data from the infected device.
SonicWall Threats Research Team observed a campaign that has been spreading since the last few months and targeting Korean banks, we have named this campaign as the Dew18 campaign since samples belonging to this campaign have Dew18 in their package name.
Few functionalities of the malware present in this campaign include stealing sensitive data like call logs and SMS messages from the device, blocking the user from contacting customer care of certain banks and killing a particular spam detector app thereby preventing the user from spam detection when receiving a potential spam call.
Infection Cycle: Application Installation & Execution
The malware requests for the following permissions during installation:
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.INTERNET
- android.permission.READ_SMS
- android.permission.READ_CONTACTS
- android.permission.READ_CALL_LOG
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.READ_PHONE_STATE
- android.permission.CALL_PHONE
- android.permission.PROCESS_OUTGOING_CALLS
- android.permission.WRITE_CALL_LOG
- android.permission.READ_CONTACTS
- android.permission.MODIFY_PHONE_STATE
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.BOOT_COMPLETED
- android.permission.ACCESS_BACKGROUND_SERVICE
- android.hardware.telephony
Majority of the malware belonging to from this campaign use an icon closely resembling other banking apps. One of the sample we analyzed uses the icon of the official Citibank finance app as visible once it gets installed:
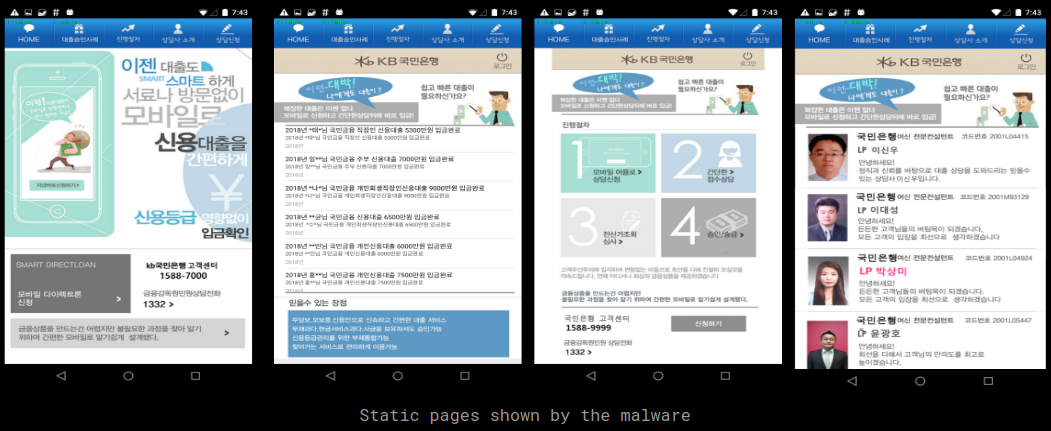
Once installed and executed we are shown the main screen in the app which accepts user inputs to apply for a loan and few other screens to choose from the options in the top menu. None of the links or buttons in any page except the loan application page work, they are just static pages displayed in the app:
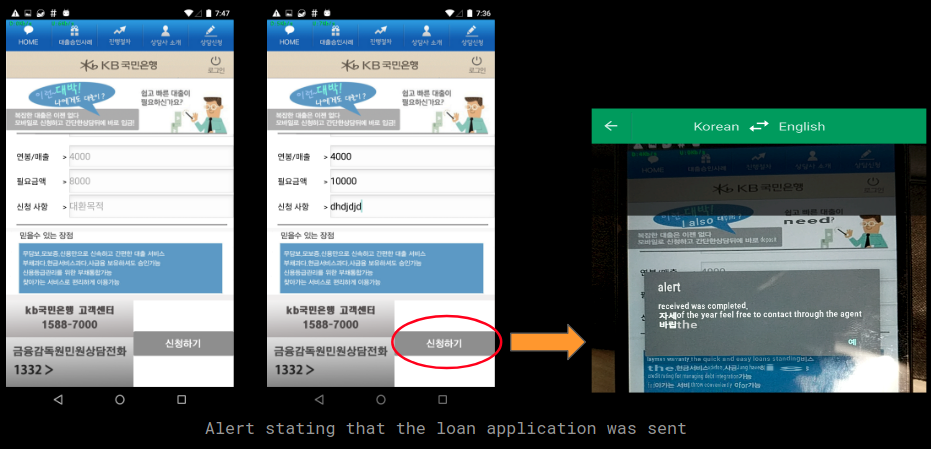
The loan application page accepts details from the user and once the Apply button is clicked the user is informed that his application has been submitted. There is no activity from the app that would indicate that any loan related data is sent, this is just shown to the user to make him feel that the app is actually doing something:
Infection Cycle: Device related data
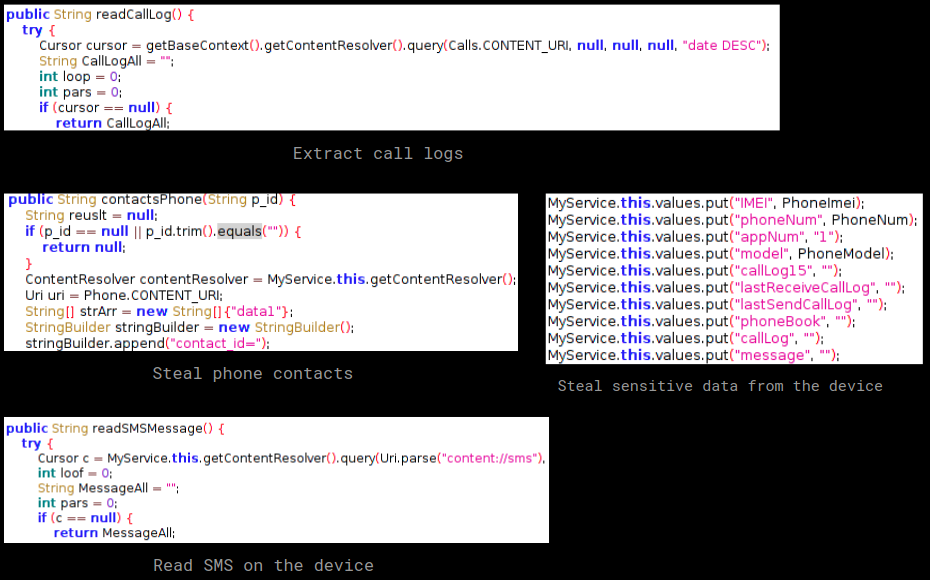
Once the execution begins, the malware starts sending personal information from the infected device:
As visible above, the malware is more interested in the calls made and received from the device. Below images show different areas in the code where sensitive data from the device is accessed:
Infection Cycle: Outgoing calls and Phone numbers
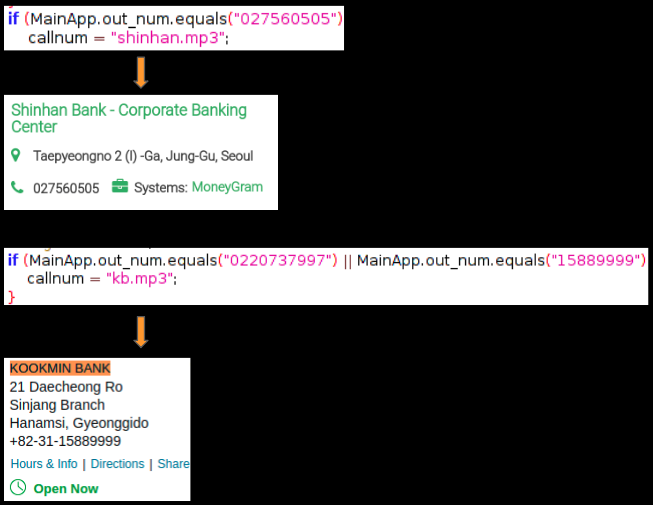
The malware contains interesting code related to outgoing calls. It contains a list of numbers belonging to customer care of certain Korean banks, if a number from this list is called it loads a specific audio file from its assets folder and plays it effectively blocking the user from contacting the bank. For the user, it would feel as if this voice came from the banking representative he made the call to but in reality the call never went through.
Figure below shows a snippet of phone numbers that the malware monitors when an outgoing call is made and few audio files from the assets folder:
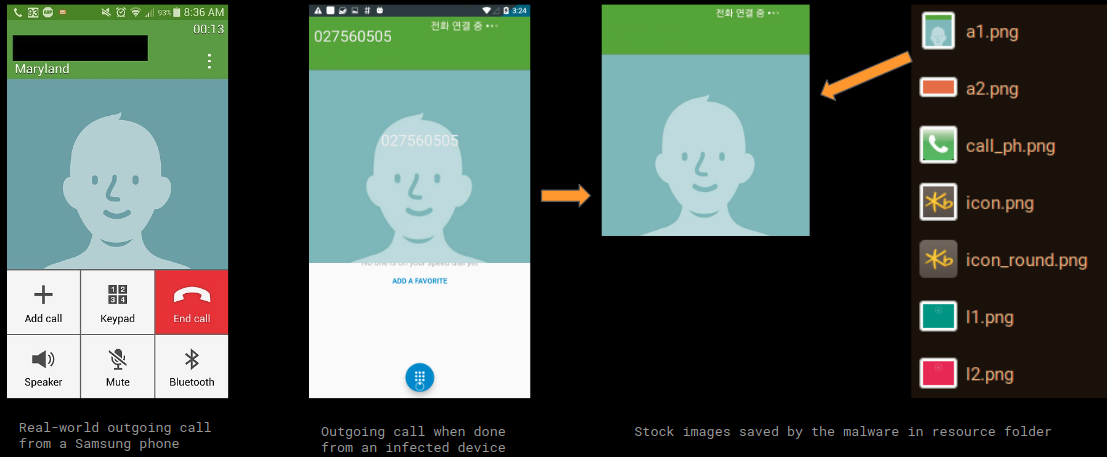
Based on the phone number dialed an appropriate audio file is played to mimic a person answering the phone. The malware also displays a stock background image for incoming/outgoing calls to make things look authentic and believable (more on this later in the blog):
A quick search based on the hard-coded phone numbers and file name of the audio files confirmed that they belong to the customer service of certain banks:
A rough translation of the audio from one of the audio files is as follows:
- “Welcome to (name) corporation. Through our safe and convenient loan service we will take care of you.”
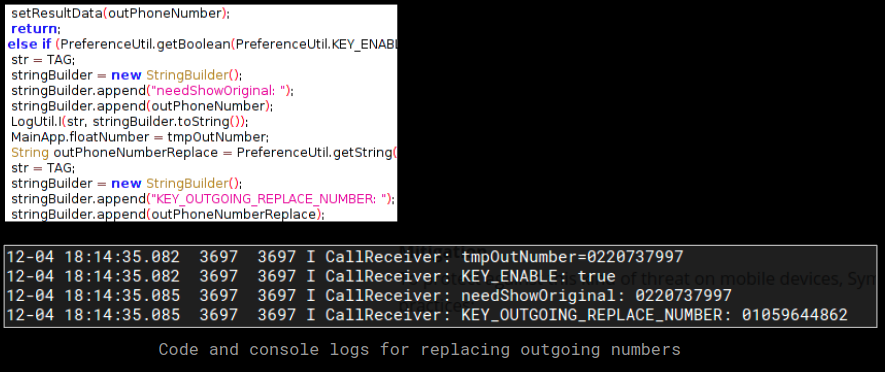
We observed code that mentions replacing the outgoing phone number, during our analysis we did see console logs indicating this but it did not reflect on the device being used for the call. Considering how this malware plays a default audio recording if a number belonging to a bank/financial institution is dialed, it is possible that the malware replaces the number and makes a call to one of the attackers. The attackers can then pose as a real banker and request for sensitive user information like bank account numbers, credit card numbers and other details making this a clever scam.
Infection Cycle: Kill the spam detector
These days there are a number of useful apps that check the incoming number and notify the user if it is a potential spam call before the user receives the call. Such apps are extremely useful, so much so that Google took notice of this feature and incorporated it into their OS.
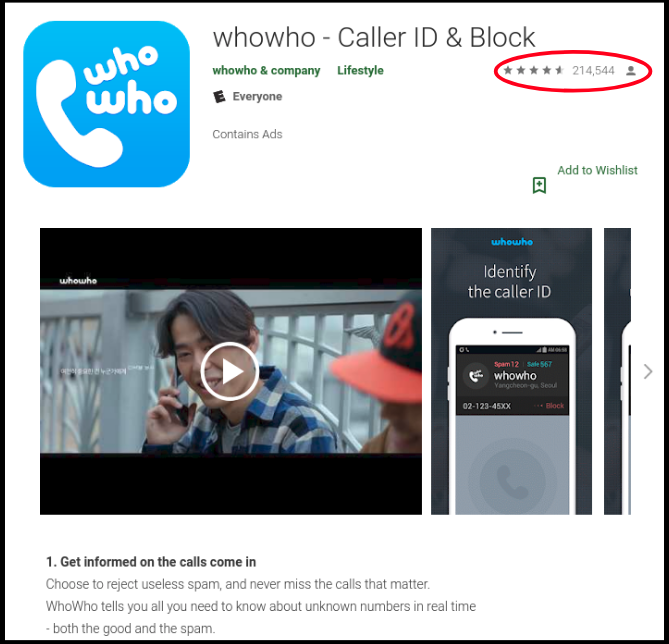
One such spam detecting Korean app is WhoWho, this app enjoys a good user base as visible from its high ratings:
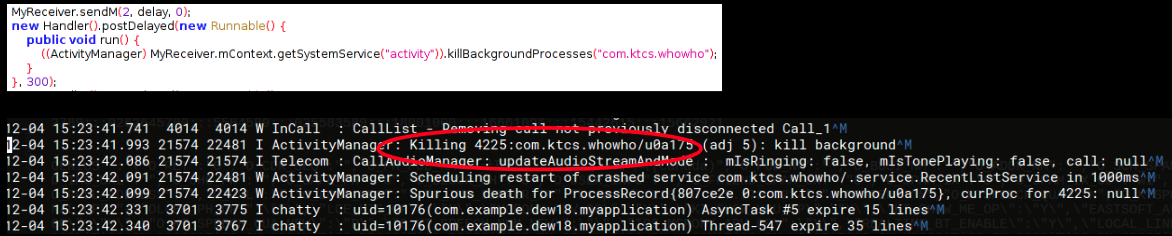
When a call is received on the infected device this malware quietly kills the spam detector app WhoWho if it is installed on the device thereby helping the spammers:
Floating call windows
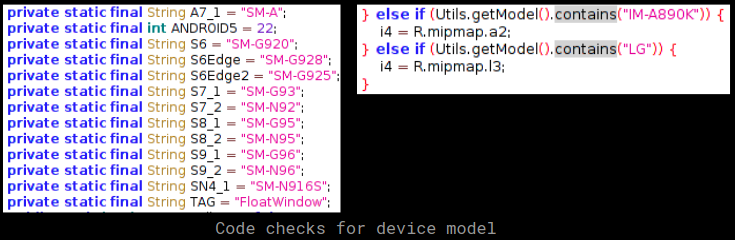
As mentioned earlier, when a call to a particular number is made from the infected device this malware simulates a call by playing an audio file. To make things more convincing based on the make of the phone the malware displays an appropriate stock background for outgoing calls used for certain popular phones, we observed code for the following phone manufacturers in the samples:
- Samsung
- LG
- Pantech
All the above manufactures are based out of South Korea and phones from these manufacturers are a popular choice among Korean users.
Below is a comparison of a the real-world outgoing call background from a Samsung device, what happened when we made an outgoing call from an infected device and stock images saved by the malware in the resources folder:
The outgoing call background effect is achieved in Android using Floating Windows which is essentially a small overlay on top of the current view/activity.
The Dew18 campaign
The earliest sample belonging to this campaign can be traced back to October 22, 2018 whereas the latest one dates to today – December 5, 2018. This indicates that this is a fairly new campaign.
Based on our observations, samples belonging to this campaign have one of the following package names:
- com.example.dew18.myapplication
- com.example.dew18.a
Most of the application names and icons are that belonging to Korean financial institutions, few are mentioned below:
- KB Kookmin Bank
- NH Capital
- Hana financial group
Following are few domains that were contacted by different samples from this campaign during our analysis:
- 45.120.69.4
- 45.120.69.57
- 112.219.131.74
- 182.162.104.210
- 182.162.104.245
- 211.169.248.219
- 211.169.248.246
We observed links for the following hardcoded php pages in every sample belonging to this campaign:
- [server_ip]/InfoFromAPP.php – Information from the infected device is sent to this page
- [server_ip]/upload_ok.php – We did not see network activity for this page during our analysis
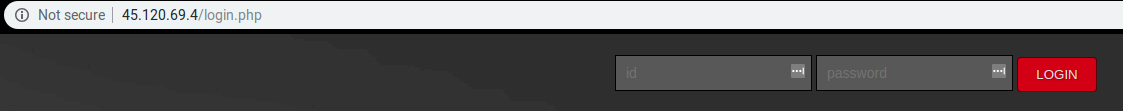
Investigation using VirusTotal for this campaign and IP addresses revealed an interesting page:
- [server_ip]/login.php
This page contains additional redirects:
- If an ‘admin’ logs in – /adminpage.php
- If a ‘user’ logs in – /sample1.php
At the time of writing this blog, one of the pages is still serving a malicious apk belonging to this campaign at the link:
- [server ip]/aaa.apk
There is a possibility that this campaign operates using a Malware-as-a-Service (MaaS) model as this campaign has a fairly good implementation to carry out financial frauds, this makes it extremely attractive to scammers.
SonicWall Capture Labs provides protection against this threat with the following signatures:
- AndroidOS.Dew.BNK
- AndroidOS.Dew.BNK_2