DCN DCBI-Netlog-LAB Remote Command Execution
DCN(Digital China Networks) focuses on the data communication field with full product lines, including switch, wireless router, security firewall and gateway, storage, CPE and Cloud services. DCBI-Netlog-LAB is an online behavior log system.
DCBI-Netlog-LAB Remote Command Execution | CVE-2023-26802
An issue in the component /network_config/nsg_masq.cgi of DCN (Digital China Networks) DCBI-Netlog-LAB v1.0 allows attackers to bypass authentication and execute arbitrary commands via a crafted request.
This vulnerability affects seven fields, namely proto, ip, pport, p_dip, pdport, odev, and tport, allowing the attacker to inject arbitrary malicious commands.
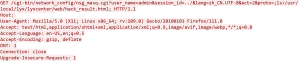
As seen in the exploit, the parameters are set to exploit the vulnerability by sending a GET request to the “/cgi-bin/network_config/nsg_masq.cgi” endpoint. Lets analyze the parameters of the request.
- user_name=admin: This parameter is specifying the username as “admin”.
- session_id=../: This parameter is setting the session ID to “../”. The use of “../” suggests a directory traversal attempt, where the attacker tries to navigate to a parent directory.
- lang=zh_CN.UTF-8: This parameter sets the language to “zh_CN.UTF-8”, indicating Chinese language with UTF-8 encoding.
- act=2: This parameter sets the action to “2”, potentially indicating a specific operation or task.
- proto=;ls>/usr/local/lyx/lyxcenter/web/hack_result.html: This is the most critical part of the code. It sets the “proto” parameter to execute a command. In this case, the command being executed is “ls” which lists the contents of a directory. The output of this command is then redirected (using “>”) to a file called “hack_result.html” located at “/usr/local/lyx/lyxcenter/web/” directory. This suggests an attempt to create a file containing the result of the “ls” command, possibly for further analysis or exploitation.
So overall this vulnerability allows unauthorized individuals to bypass authentication and inject harmful commands. By sending carefully crafted requests that exploit directory traversal, an attacker can bypass authentication and gain unauthorized access. If successfully exploited, this vulnerability enables the attacker to remotely execute any commands they choose on affected systems.
The CVSS (Common Vulnerability Scoring System) score is 9.8 with CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
SonicWall Capture Labs provides protection against this threat via following signature:
- IPS 15852:DCN DCBI-Netlog-LAB Remote Command Execution
Threat Graph