Darkside ransomware targets large corporations. Charges up to $2M.
The SonicWall Capture Labs threat research team have observed a new family of ransomware called Darkside. The operators of this ransomware primarily target large corporations. Recently, a Canadian land developer and home builder, Brookfield Residential has been hit with Darkside ransomware. In this case, the operators have not just encrypted data, but have stolen it and threatened to publish the company’s data online if it does not pay up. Darkside has been around since early August and its operators have been launching multiple customized attacks towards known high revenue companies. The operators charge between $200,000 and $2M for file decryption. It has been reported that the operators have already obtained over $1M since the start of their campaign.
Infection Cycle:
When running the malware the following User Account Control dialog is shown:
Files on the system are encrypted and given a “ehre.eb2e8d90″ extension. A file named README.eb2e8d90.TXT is copied into all directories containing encrypted files.
README.eb2e8d90.TXT contains the following message:
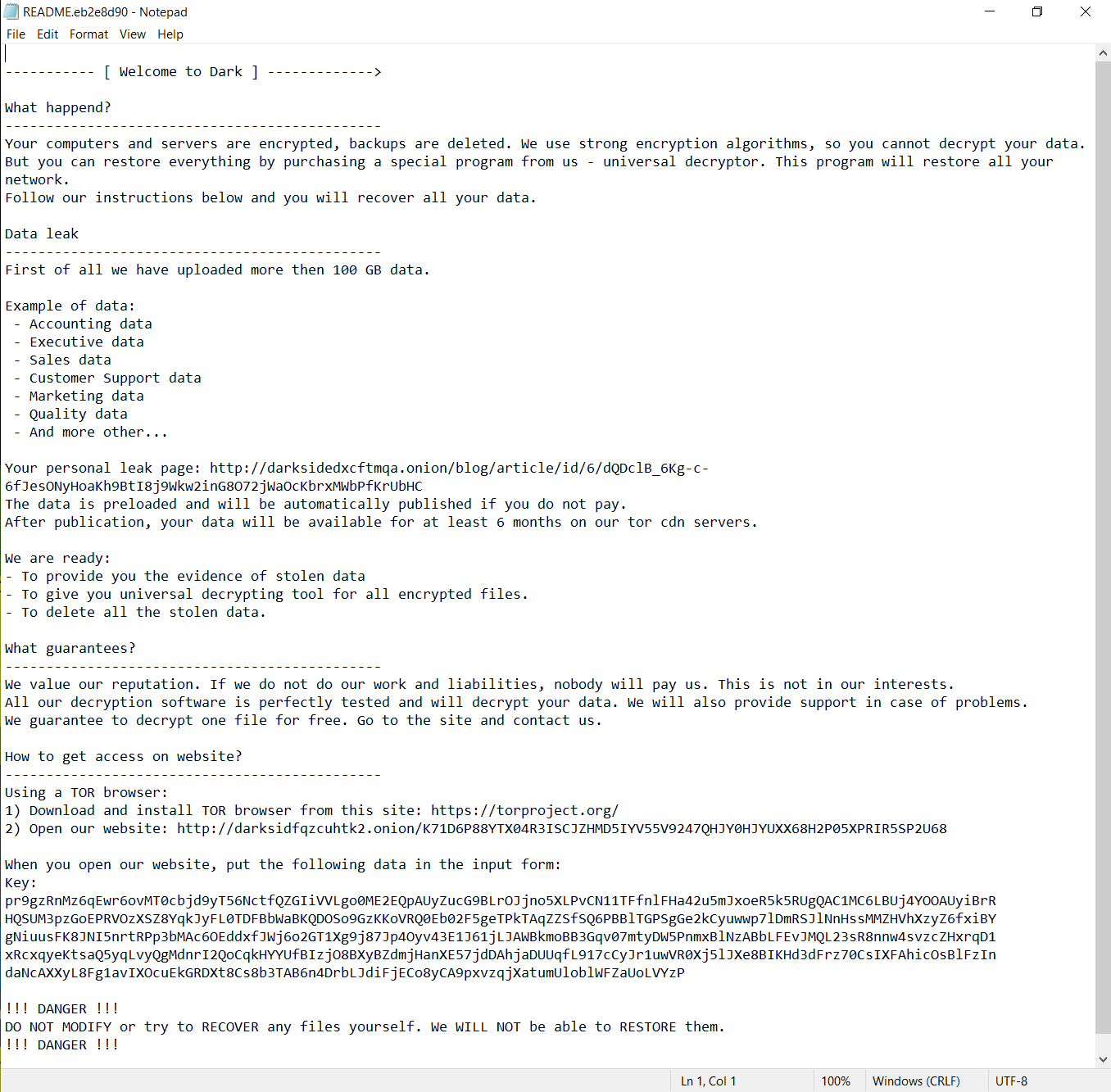
As the malware is aimed at large corporations, the message states that over 100GB of data has been uploaded to the operators. However, we did not observe any data being uploaded during our analysis.
The link provided in the ransom message leads to the following page hosted on a server on tOr:
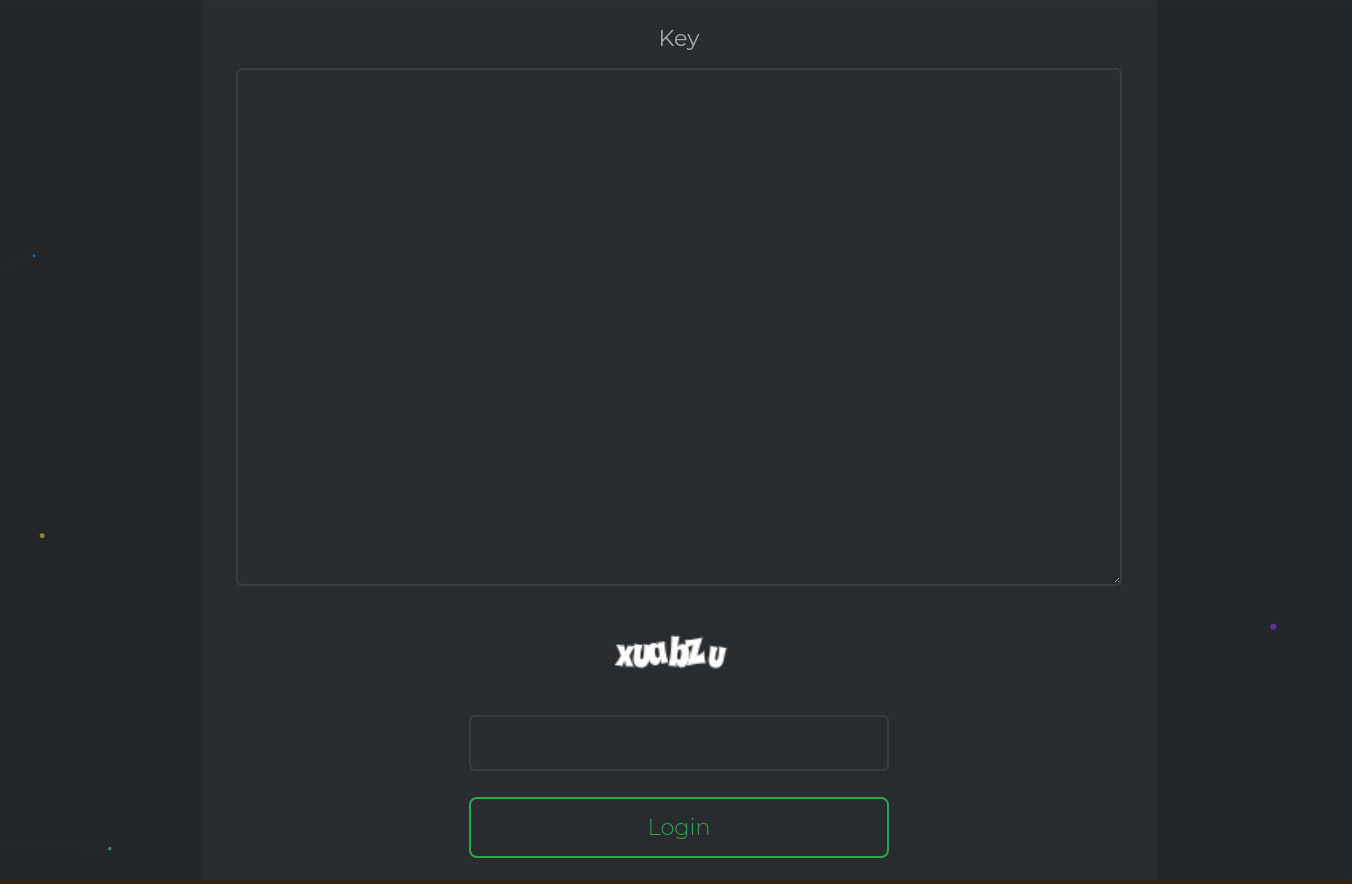
Upon entering the key provided in the message, the following page is displayed:
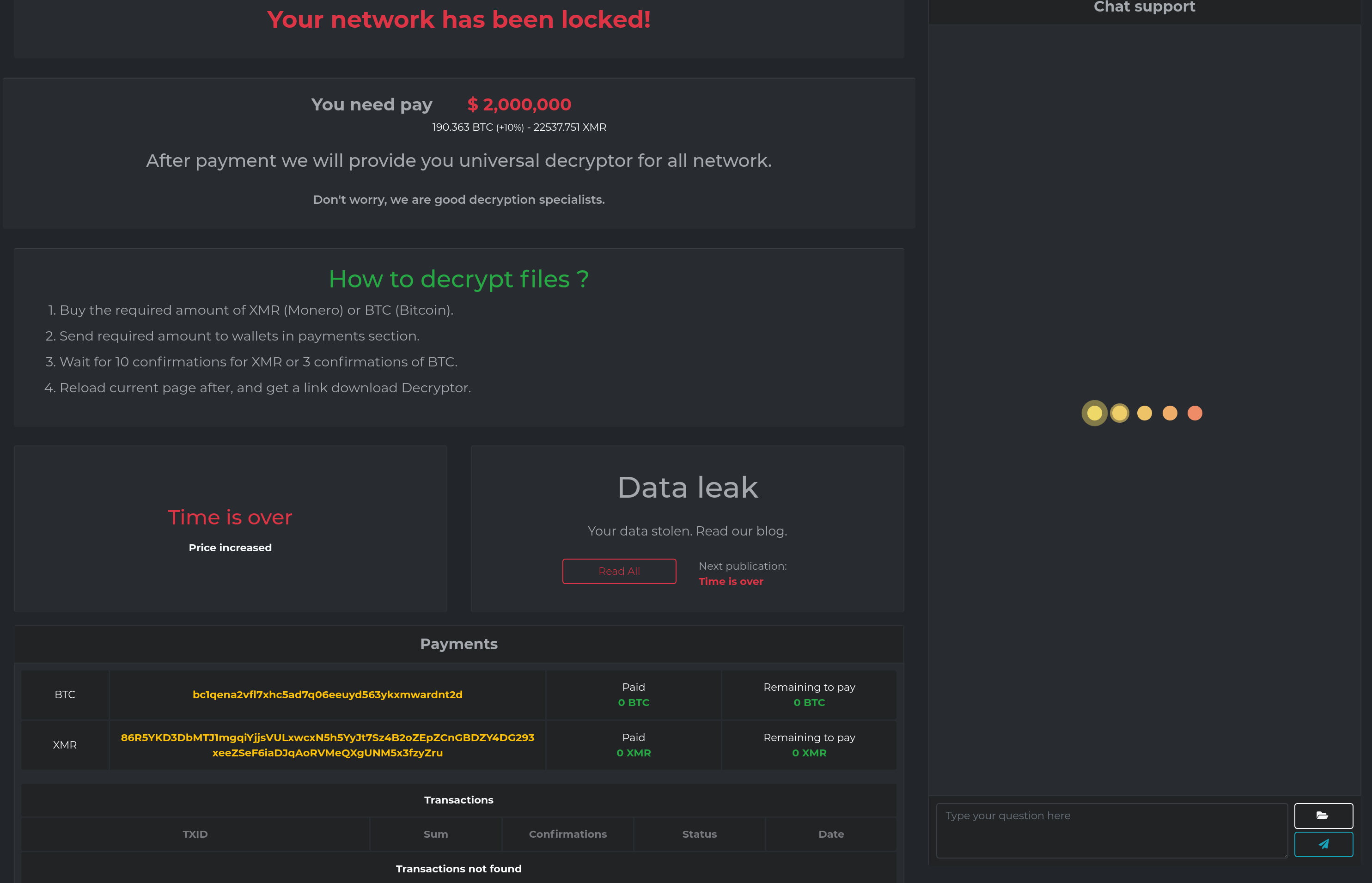
$2 Million in crypto is demanded for file decryption. It is interesting to note that in addition to Bitcoin, Monero is offered as a valid paymenet method. Compared to Bitcoin, Monero is used significantly less by ransomware operators. However, one of Monero’s key features is its untraceability. We expect to see an increase in malware operators using cryptocurrency of this nature.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Darkside.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




