CVE-2018-1111 Network Manager command injection vulnerability
SonicWall Threat Research Lab is seeing attempts to exploit the CVE-2018-1111 vulnerability – An OS command injection flaw in the Red Hat NetworkManager integration script included in its DHCP package. This is due to improper validation of DHCP responses by the Network Manager. Red Hat NetworkManager that’s shipped by default with Red Hat Enterprise Linux 6 and 7, Fedora 28, and earlier are vulnerable to this flaw. A remote attacker could exploit this vulnerability by sending a malicious DHCP response to a vulnerable target.
The Dynamic Host Configuration Protocol (DHCP) is a network management protocol that issues DHCP requests to fetch network configurations such as IP address, Gateway, DNS servers and more. DHCP is implemented with two UDP port numbers (67 & 68). Port 67 is the destination port of a server and 68 is used by the client. A single DHCP transaction consists of several DHCP messages exchanged between the DHCP client and DHCP server.
When a Network Manager receives a DHCP response with option records, DHCP client package provided by Red Hat for the NetworkManager component tries to read DHCP Option data for each of the record using the script and evaluates it to set the necessary environment variables. As the Option data is not properly sanitized, supplied arguments such as shell commands result in arbitrary command execution. Hence an attacker with a malicious DHCP server can spoof DHCP responses to vulnerable DHCP clients to execute arbitrary shell commands with root privileges.
Trend Graph:
The trend line below shows how this vulnerability is being exploited today
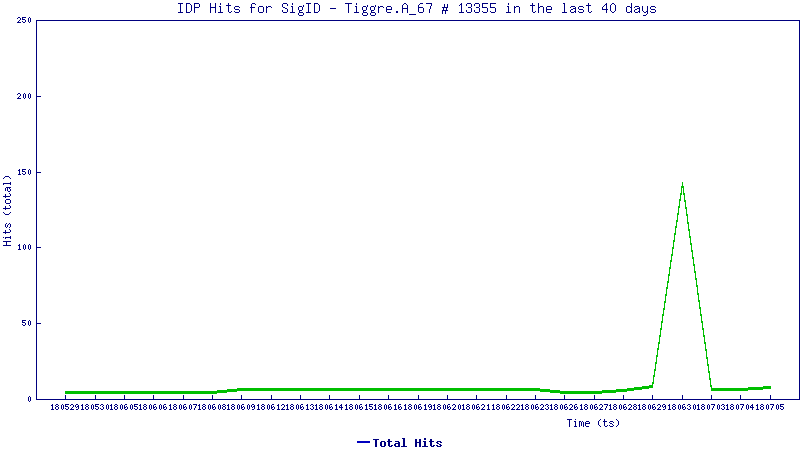
SonicWALL Threat Research Lab provides protection against this exploit via the following signatures
IPS 13354: Suspicious DHCP Traffic 6
IPS 13355: UDP Application Shellcode Exploit 5




