CVE-2015-8446 Exploits in the Wild (Jan 8, 2016)
Multiple flash exploits of CVE-2015-8446 have been seen in the wild and some of them were used by Angler Exploit Kit. A list of them is below:

The Heap-based buffer overflow vulnerability CVE-2015-8446 exits in Adobe Flash Player. It allows attackers to execute arbitrary code via an MP3 file with COMM tags that are mishandled during memory allocation. The vulnerability was patched by Adobe on December 8, 2015.
After decompiling the flash exploits, we found the exploits share the similar structure as below, and the second structure is believed to be the extracted flash files from the first ones:

Or

The action scripts in all of the exploits were highly obfuscated. We have observed the following obfuscation methods have been used:
1. The action script directory or file (package) names were obfuscated/randomized, which can be seen from the above figure.
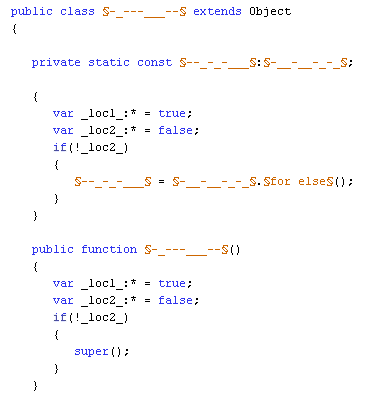
2. The variable names and function names were obfuscated/randomized:
3. The system function names had to be concatenated on the fly, for example, the variable “ertyth” is the string “flash.utils.ByteArray” concatenated by multiple small strings in the following function:

4. The program control flow has been obfuscated as below:

5. Multiple layers of encryption were applied through binary files. Some of them may use commercial flash packer such as DoSWF. For example, the following binary file:

will be decrypted on the fly when the flash file was opened and the following newly decrypted flash file will be loaded afterwards:

The obfuscation methods listed above make it almost impossible for an anti-virus/intrusion prevention engine to parse through the crafted flash files.
Dell SonicWALL Threat team has researched the exploits and added the following GAV signatures to protect their customers:
- Angler.Z (Exploit)
- Angler.Z_2 (Exploit)
- Angler.Z_3 (Exploit)
- Angler.Z_4 (Exploit)
- Angler.Z_5 (Exploit)
- Angler.Z_6 (Exploit)
- Angler.Z_7 (Exploit)
- Angler.Z_8 (Exploit)
- CVE-2015-8446.C291 (Exploit)
- CVE-2015-8446.A (Exploit)




