Cryptonite Ransomware leaves files unrecoverable
This week, the Sonicwall Capture Labs Research team analyzed a ransomware called Cryptonite. It is an open-sourced ransomware that was once available on GitHub but has now been taken down. It exhibited behavior consistent of most ransomware but later versions were found to malfunction and leaving encrypted data unrecoverable.
Infection Cycle:
The ransomware installer arrives as a fake windows update and can use the following filename:
- WindowsUpdate.exe
This ransomware is written in Python thus a Python interpreter needs to be present in the victim’s machine for it to successfully run. Therefore upon execution, all the necessary files and modules are dropped in the temp directory under a randomly named folder.
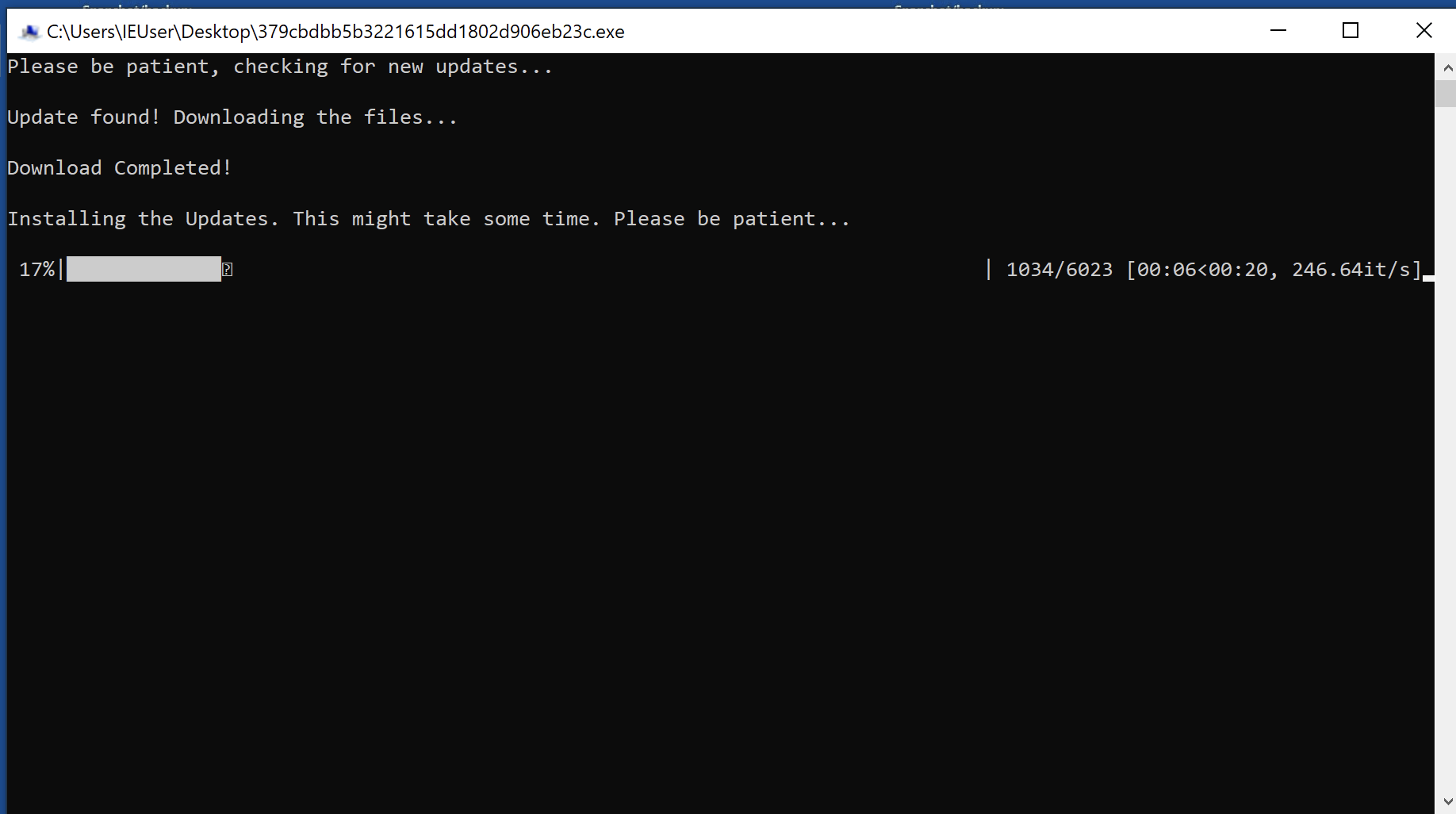
A window then pops up showing the status of the supposed download of a software update, complete with the progress bar.
Meanwhile, encryption of the files are happening in the background. Encrypted files have the file extension “.cryptn8” appended to them.
This ransomware uses the Python cryptography module and more specifically uses an implementation of Fernet to perform encryption.
In our static analysis, we found that this unique key generated using this Fernet implementation appears to be sent out to a remote server hosted on this domain – hxxps://e4c0660414bf.eu.ngrok.io
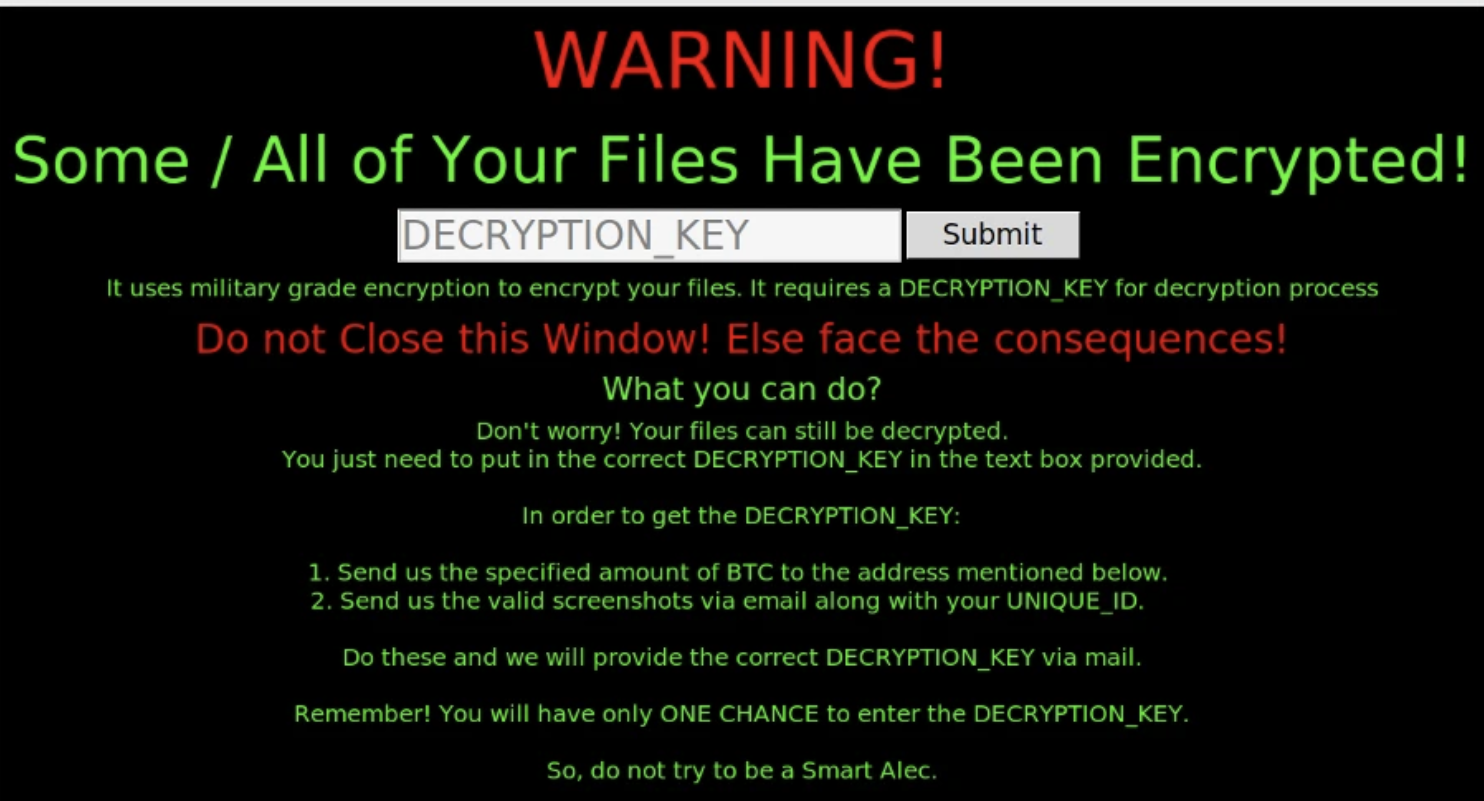
Upon successful encryption a standard warning message is then presented to the victim which allows the victim to enter a decryption key if they decide to contact the ransomware operator.
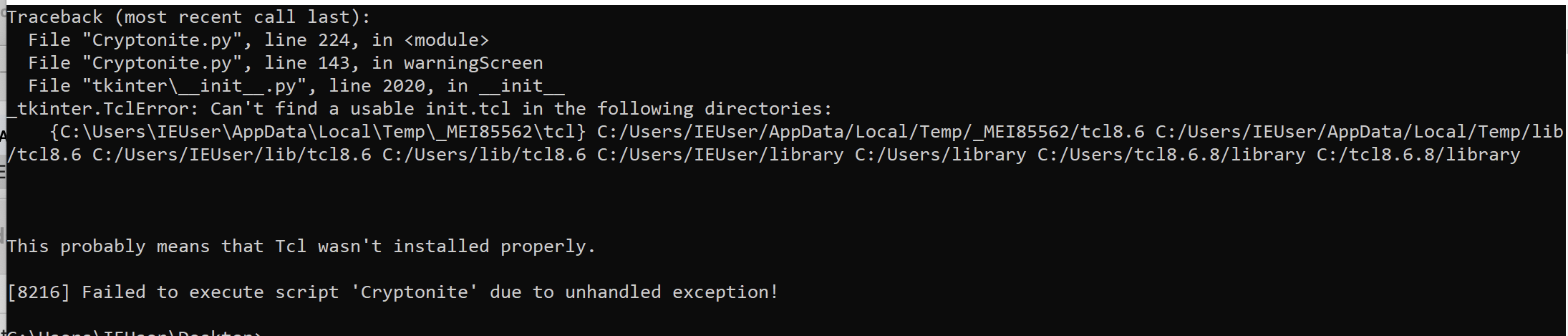
However, later samples have been found to not complete the entire infection cycle. During encryption the ransomware application abruptly crashes with an error. Encryption completes but that key never gets sent to the remote server leaving the files unrecoverable. Subsequent execution of the ransomware just encrypts the already encrypted files and thus ransomware essentially just wiped out the data in the victim’s machine.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Cryptonite.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.