CrypRAT Infostealer actively spreading in the wild.
The SonicWall Capture Labs Threat Research Team observed reports of a new variant family of CrypRAT Infostealer [CrypRAT.A] actively spreading in the wild.
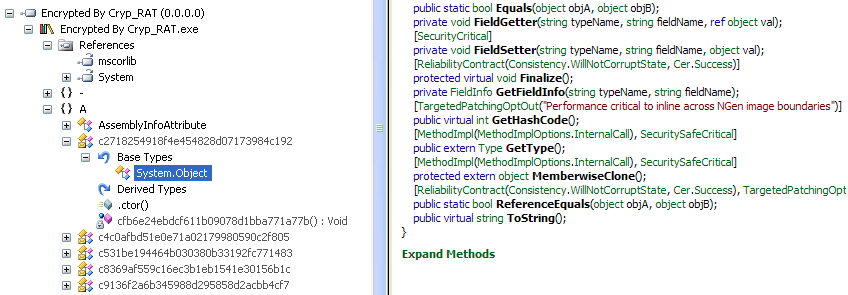
Memory Snapshot of the CrypRAT Infostealer ( Raw and Encrypted Data )
Infection Cycle:
The Malware adds the following file to the system:
- Malware.exe
- %APPDATA%\roaming\system.exe
The Malware adds the following keys to the Windows registry:
- HKEY_CURRENT_USER\Environment\SEE_MASK_NOZONECHECKS
- 1
- [HKEY_CURRENT_USER\Software\061c2e9167603fb87dafebfaad0bb29a]
- Keylogger data
Once the computer is compromised, the Malware installs following components to record the activity of the user via key logging and clipboard:

The Malware terminates the Self-Extractor process and installs the System.exe [Key logger module] on the target system.
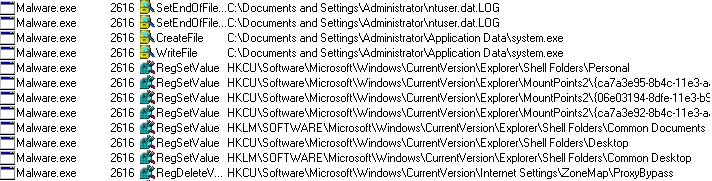
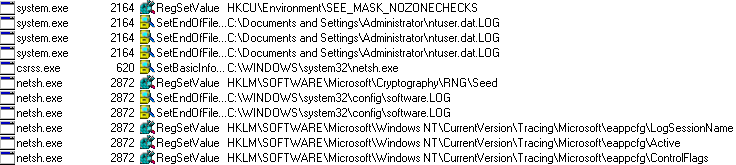
The Malware saves raw data in the following registry:
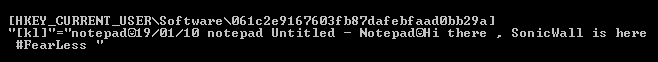
The Malware checks if data is available for transfer to the command and control (C&C) server every 10 seconds.
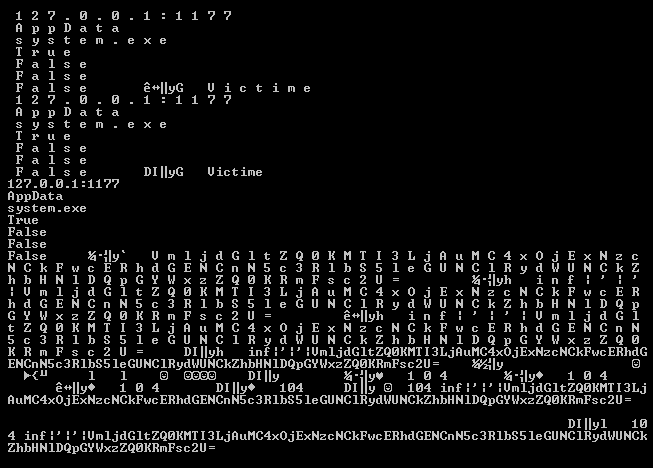
The Malware uses base64 to encrypt its strings as well as its network communication, here an example:
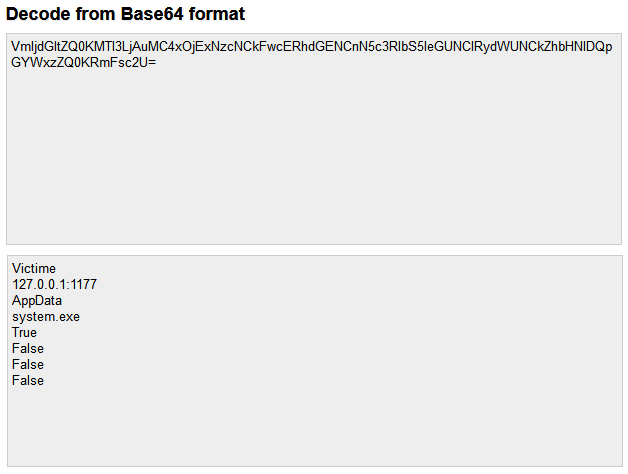
Command and Control (C&C) Traffic
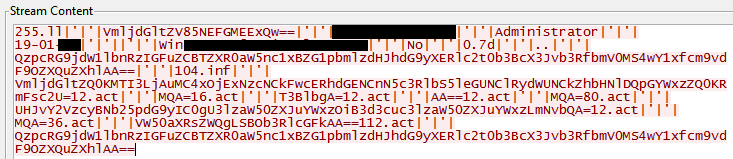
CrypRAT.A performs C&C communication over port 1177. The Malware transfers stolen data in Base64 format, here are some examples:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: CrypRAT.A (Trojan)




