Critical remote code execution flaw in VMware is being actively exploited
A critical remote code execution vulnerability has been reported in VMware’s vSphere/vCenter. The vulnerability is due to improper validation of paths in an uploaded tarball. A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation can result in code execution in the context of the target process.
CVE-2021-21972:
vCenter Server is the centralized management utility for VMware and is used to manage virtual machines. The vulnerability is reported in the vRealize Operations (vrop) plugin that comes with the default installation of vCenter. This plugin allows unauthorized file upload and fails to validate the paths provided in the uploaded tarball. An unauthenticated, remote attacker could exploit this vulnerability by uploading a specially crafted file to a vulnerable vCenter Server endpoint that is publicly accessible over port 443. Successful exploitation of this vulnerability would result in an attacker gaining unrestricted RCE privileges on the underlying operating system that hosts vCenter Server.
In most cases, vCenter is available only to users having access to the internal networks. According to Shodan, however, more than 6000 Center servers are exposed online and vulnerable to an attack.
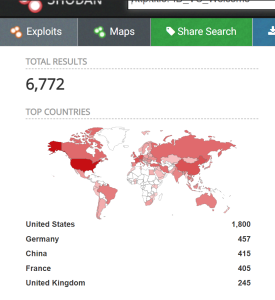
Bad Packets observed mass scanning activity for CVE-2021-21972, searching for vulnerable vCenter servers.

According to Sans Internet Storm Center, attack activity for port 443 has significantly increased over the last few days. Attackers are likely to be scanning for vulnerable vCenter servers.

Fix:
The affected vCenter Server plugin for vROPs is available in all default installations.
Impacted product versions:
- 7.0 prior to 7.0 U1c
- 6.7 prior to 6.7 U3l
- 6.5 prior to 6.5 U3n
Upgrade to one of the patched versions 7.0 U1c or 6.7 U3l or 6.5 U3n. If upgrading is not feasible, follow the KB workarounds KB82374 to disable the vulnerable plugin.
Find VMware security advisory here
SonicWall Capture Labs Threat Research team provides protection against this vulnerability with the following signatures.
IPS: 15403 VMware vCenter Server VMSA-2021-0002 Remote Code Execution (Linux)
IPS: 15404 VMware vCenter Server VMSA-2021-0002 Remote Code Execution (Windows)
IPS: 15406 VMware vCenter Server vropspluginui Access
IPS: 15408 VMware vCenter Server VMSA-2021-0002 Remote Code Execution 3
IPS: 15409 VMware vCenter Server VMSA-2021-0002 Remote Code Execution 4
IPS: 15410 VMware vCenter Server VMSA-2021-0002 Remote Code Execution 5
IPS: 15411 VMware vCenter Server VMSA-2021-0002 Remote Code Execution 6
IPS: 15412 VMware vCenter Server VMSA-2021-0002 Remote Code Execution 7




