Conti operator demands $20M from victim. Faces litigation backlash instead
The SonicWall Capture Labs threat research team have recently been tracking Conti ransomware. It has been reported that Conti has been connected with over 400 cyberattacks against organizations around the world. In addition to encrypting files and holding them hostage for ransom, attackers attempt to increase chances of payout by threatening to publish sensitive data that is stolen from company networks. Such double-extortion schemes are a growing trend with ransomware.
Infection Cycle:
Conti ransomware is aimed at large company networks. The initial infection is handled manually by the attackers and would usually start with phishing attempts or firewall exploits. Once inside a network, a Cobalt Strike beacon is introduced onto the system to communicate with the attacker’s C2 server. Once the backdoors are established, the attackers propogate malware further within the network and begin to exfiltrate sensitive data that will be used later on for extortion. After this, Conti malware is deployed.
Conti malware uses the following icon:

Upon infection, files on the system are encrypted. Each encrypted file is given a .FEEDC extension. A file named readme.txt is dropped into directories containing encrypted files. It contains the following message:
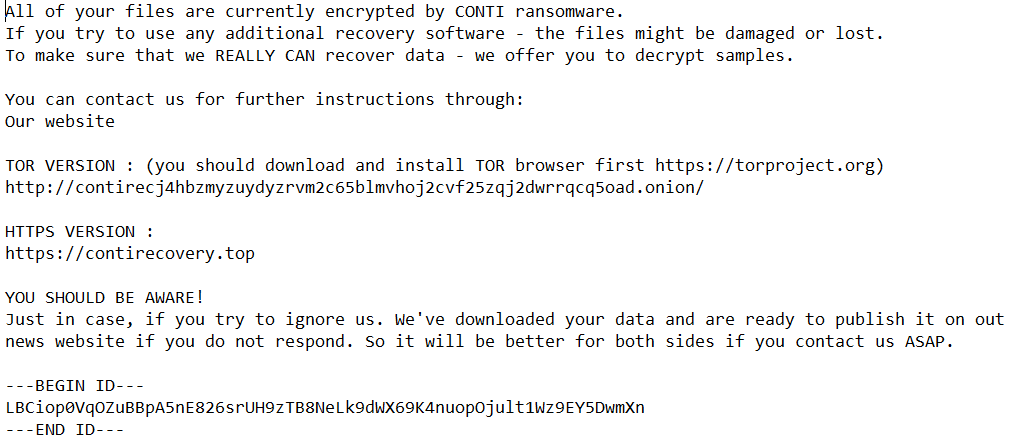
https://contirecovery.top is down but the tOr link leads to the following page:

After uploading readme.txt to the tOr website, the following conversation can be seen between a prior victim and the operator.
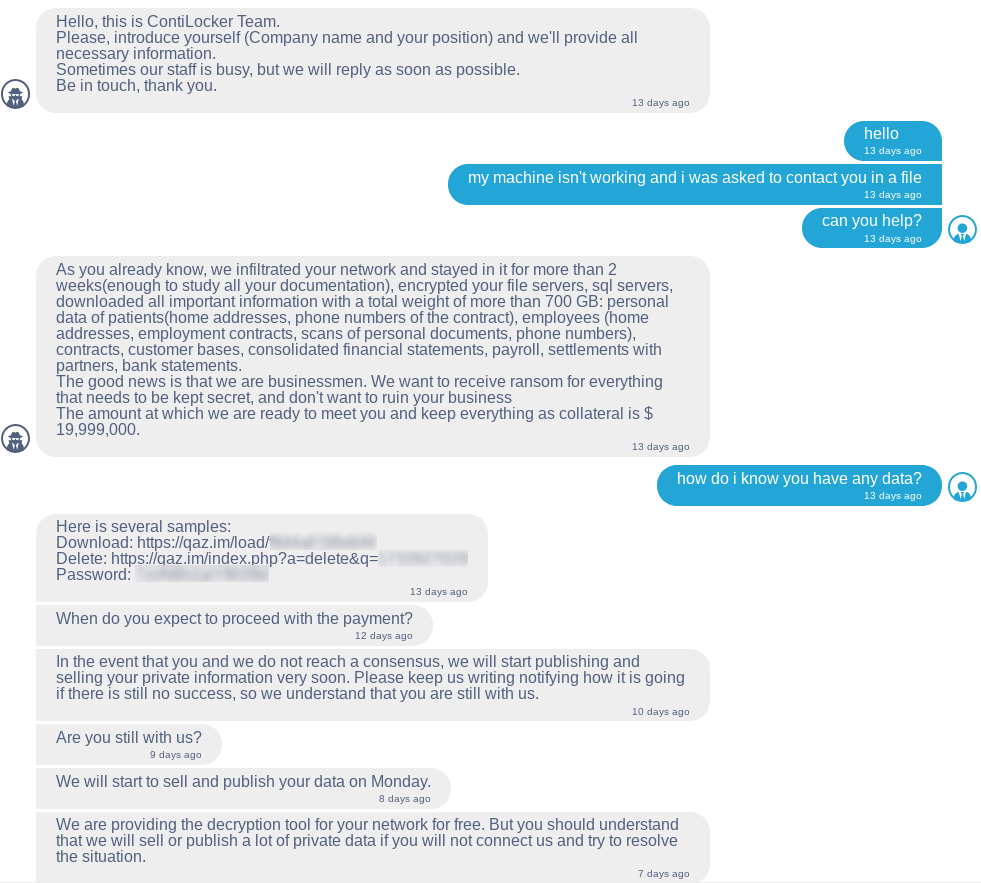
As seen in the message above, the operator demands a staggering $20M for file decryption.
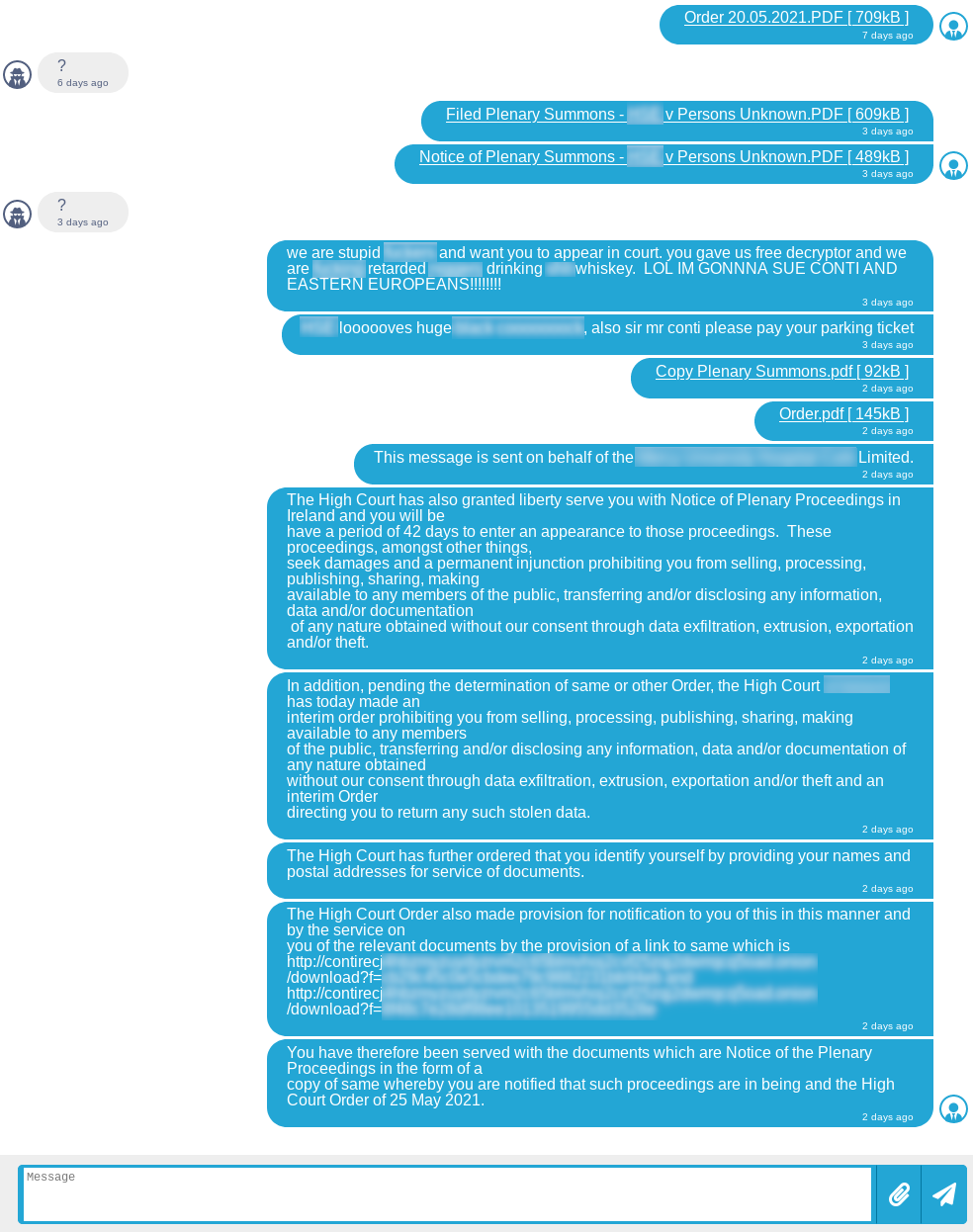
After a few days, the victim fights back with litigation:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Conti.RSM (Trojan)
- GAV: Conti.RSM_2 (Trojan)
- GAV: Conti.RSM_3 (Trojan)
- GAV: Conti.RSM_4 (Trojan)
- GAV: Cobaltstrike.A_1 (Trojan)
- GAV: Cobaltstrike.A_2 (Trojan)
- GAV: Cobaltstrike.A_3 (Trojan)
- GAV: Cobaltstrike.A_4 (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.




