Cisco ASA Cross Site Scripting Vulnerability
Cisco Adaptive Security Appliance XSS is being exploited in the wild.
The Cisco ASA Family of security devices protects corporate networks and data centers of all sizes. Cisco Adaptive Security Appliance (ASA) Software is the core operating system for the Cisco ASA Family. It delivers enterprise-class firewall capabilities for ASA devices in an array of form factors – standalone appliances, blades, and virtual appliances – for any distributed network environment. ASA Software also integrates with other critical security technologies to deliver comprehensive solutions that meet continuously evolving security needs.
Vulnerability in the web services interface of Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to conduct cross-site scripting (XSS) attacks against a user of the web services interface of an affected device.
The vulnerability is due to insufficient validation of user-supplied input by the web services interface of an affected device. An attacker could exploit these vulnerabilities by persuading a user of the interface to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the interface or allow the attacker to access sensitive, browser-based information.
Cross site scripting XSS
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
XSS attacks abuse the dynamic way websites interact with the browsers. It makes possible, for an attacker, to control the victim’s browser and his/her interaction with a given vulnerable website. To display back content provided or controlled by a user, like an URL parameter or an input field, a flawed application opens the door to manipulation of this content.
Cisco Adaptive Security Appliance XSS | CVE-2020-3580
When the website or application just reflects back content maliciously manipulated by user it is called a reflected XSS attack. This reflection, affects the way browsers displays the page and how they process things and behave.
For exploiting the Cisco ASA vulnerability the attacker abuses the svg tag’s onload event . Since the event handler code does not properly sanitize the input whatever is written in the alert is reflected back to the user.
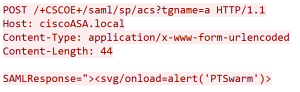
Authentication is not needed to exploit this vulnerability. A successful exploit could allow the attacker to execute arbitrary script code in the context of the interface or allow the attacker to access sensitive, browser-based information such as user’s session cookie, allowing an attacker to hijack the user’s session and take over the account. A successful exploit could also lead to the disclosure of end user files, installation of Trojan horse programs, redirect the user to some other page or site, or modify presentation of content.
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 15614: Cisco Adaptive Security Appliance XSS
Following versions are vulnerable
- Earlier than 9.61
- 9.61
- 9.71
- 9.8
- 9.9
- 9.101
- 9.12
- 9.13
- 9.14
- 9.15
Cisco had patched this vulnerability.
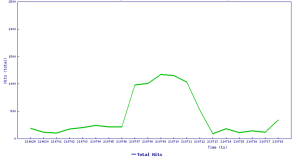
Threat Graph