CHIYU Technology Devices CRLF injection vulnerability
CHIYU Technology is a leading access control manufacturer and marketer of multi door access control system for enterprise, small business, and residential applications. BF-430 is a universal serial device server that enables industrial serial devices, such as, PLC, flow meters, gas meters, CNC machines, and biometric identification card readers to be monitored from the network.
Similarly BF-450M is a universal serial device server that can enable industrial serial devices, such as, access control, time attendance, PLC, CNC machines, and flow meters to be monitored from the network. Moreover, it includes built-in I/O control which could let users easily integrate with other systems via this special design.
CRLF injection vulnerability
A CRLF injection vulnerability exists if an attacker can inject the CRLF characters into a web application. A CRLF injection attack can be used to escalate to more malicious attacks such as Cross-site Scripting (XSS), page injection, web cache poisoning etc. The term CRLF refers to Carriage Return (ASCII 13, HEX 0d) Line Feed (ASCII 10, HEX 0a).CR and LF are special characters that are used to signify the End of Line (EOL) in Windows operating system. A CRLF injection attack occurs when a user manages to submit a CRLF into an application. This is most commonly done by modifying an HTTP parameter or URL.
CVE-2021-31249
A CRLF injection vulnerability exists in BF-430, BF-431, and BF-450M TCP IP Converter devices. This is due to a lack of validation on the parameter redirect= available on multiple CGI components.
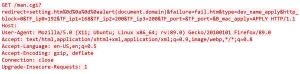
As can br seen in this example ![]() i.e. CRLF is used to split and
i.e. CRLF is used to split and ![]() is used to carry out a cross-site scripting attack. In this case the CRLF injection vulnerability leads to XSS attack.
is used to carry out a cross-site scripting attack. In this case the CRLF injection vulnerability leads to XSS attack.
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 15592:CHIYU Technology Devices CRLF injection
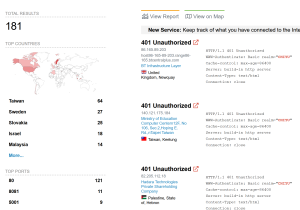
A quick check on Shodan shows vulnerable devices.