Chinese Remote Access Trojan Taidoor
Overview:
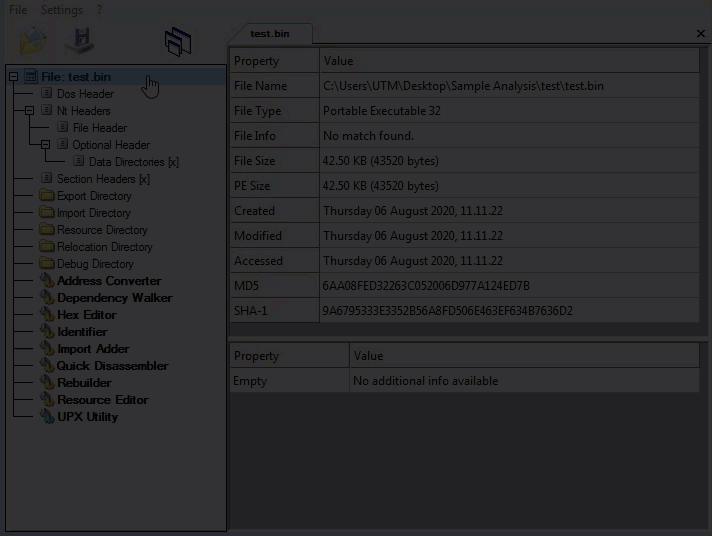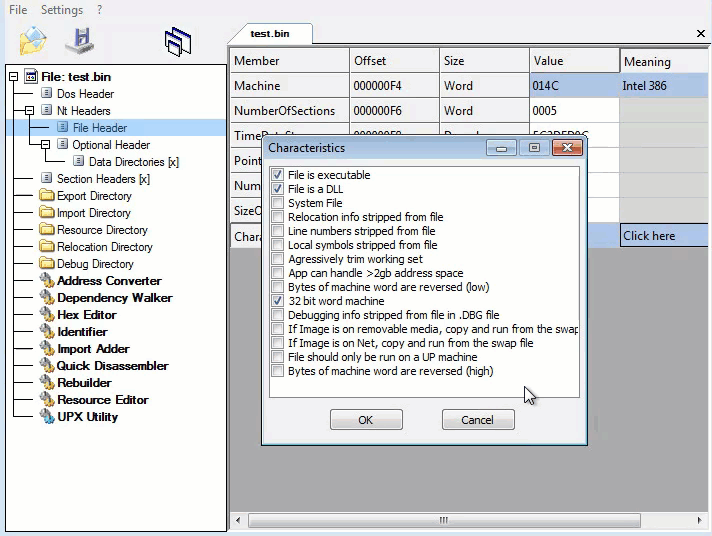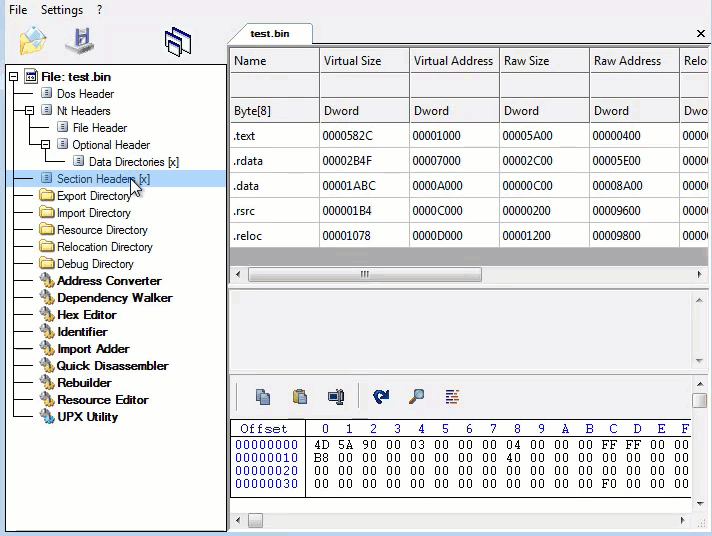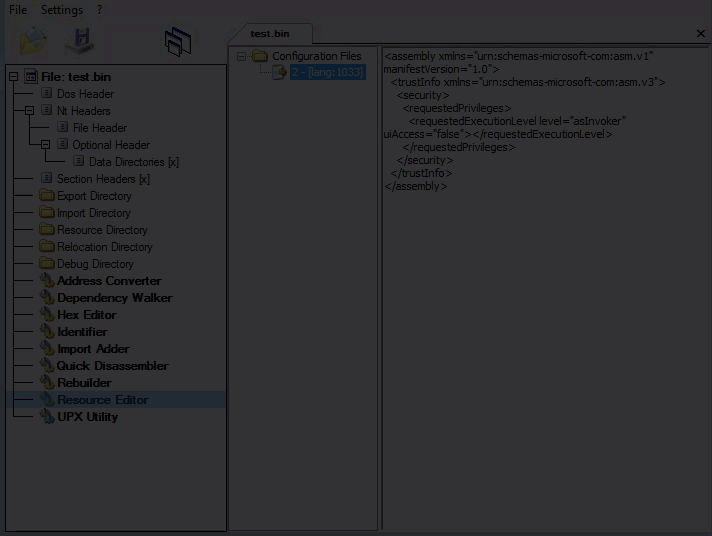
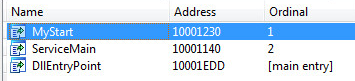
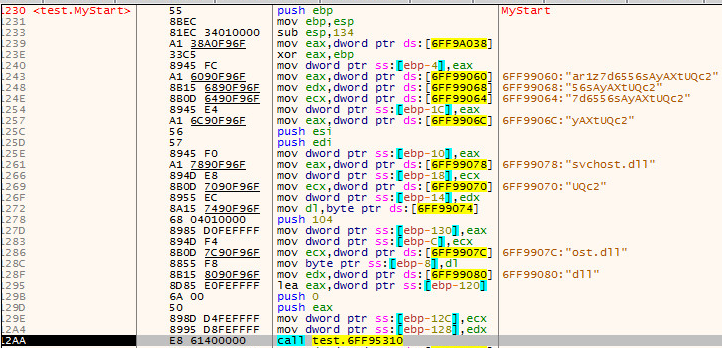
SonicWall Capture Labs Threat Research Team recently observed activity for the Chinese Remote Access Trojan Taidoor. Taidoor is composed of two stages, the loader and RAT module. The loader starts the service and decrypts the second file. The loader uses its export function “MyStart” for the initial infection. The function will allocate memory space for a new file called “svchost.dll”.
Before the new file is called it will have to go through a series of routines to decrypt the contents of the file. The DLL uses RC4 encryption, the key is actually rebuilt using the following sting: “ar1zyAXt7d6556sAsvchUQc2”. Once filtered, the RC4 key will be: “ar1z7d6556sAyAXtUQc2”.
The RC4 algorithm is also used to decrypt the import names and other related strings.
DLL Loader Layer, Static Information:
Dynamic Information:
Looking inside “MyStart” Export Routine:
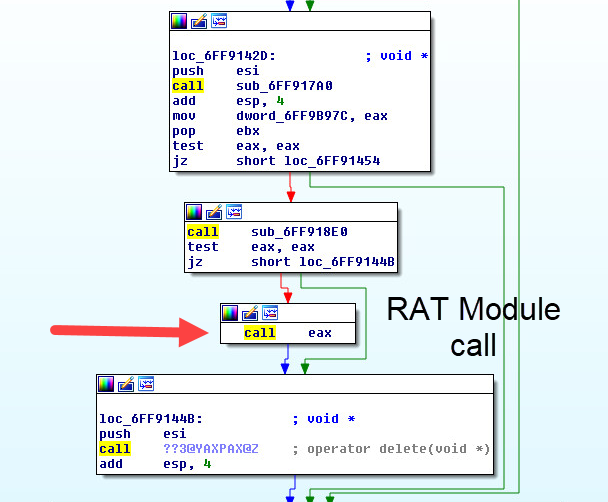
Creating the RAT module:
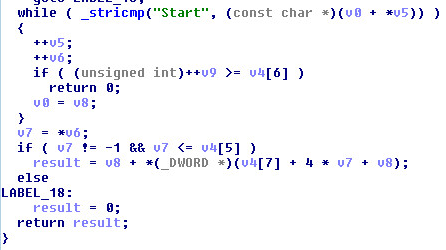
Once the svchost dll is allocated in memory it will cycle the exports and located the “Start” export routine in the new dll.
Calling the call routine to start the Remote Access Trojan module:
Network Artifacts:
Command and Control Information:
- cnaweb.mrslove.com
- 210.68.69.82
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Taidoor.LD
Appendix:
Sample SHA256 Hash: 4a0688baf9661d3737ee82f8992a0a665732c91704f28688f643115648c107d4