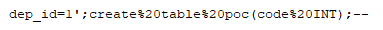Centreon hostGroupDependency.php SQL Injection Vulnerability
Overview:
Centreon is an open source IT monitoring solution. Centreon open source solution is the foundation for the Centreon EMS software suite which offers additional licensed modules. Centreon open source solution includes integration tools for IT Operations Management production environment.
An SQL Injection vulnerability has been reported in the Centreon Web Application. The vulnerability is due to incorrect input validation in hostGroupDependency.php.
A remote, authenticated attacker could exploit this vulnerability by sending a maliciously crafted request to the server. A successful attack may result in arbitrary SQL command execution against the database on the target server.
CVE Reference:
This vulnerability has not been assigned a Common Vulnerabilities and Exposures (CVE) identifier.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.1 (AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is high.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.2 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
A user with admin privileges can manage the notification settings for a host group on the “Configuration”->”Notification”->”Host Groups” page in the Centreon web interface. When clicking a host group on the web page, a request will be submitted to the “/centreon/main.get.php” endpoint as shown in an example below:
In the request above, the parameter “p” contains a topology_page number (e.g. 60408 in the above example) which is used by Centreon application to locate the correspondent PHP file to handle this request. The mappings of a topology_page number and its correspondent PHP file is defined in the insertTopology.sql. For the topology_page number 60408 in the “p” request parameter, the corresponding PHP file to handle this request is:
The hostGroupDependency.php is relevant to the vulnerability in this report.
An SQL injection vulnerability exists in the Centreon web application. The vulnerability is due to a lack of input validation on the dep_id request parameter in the hostGroupDependency.php. When receiving a request submitted to “main.get.php” endpoint, the main.get.php will check the “p” request parameter value. If the value is 60408, it will route the request to hostGroupDependency.php. The hostGroupDependency.php will read the dep_id request parameter value and then check the “o” request parameter value. If “o” parameter value is the character “c”, “w” or “a”, it will call formHostGroupDependency.php to process this request. In formHostGroupDependency.php, it will first check if the “o” parameter is “c” or “w” and if yes, it will construct a SQL statement by appending the dep_id parameter value. Then, it will execute the SQL statement to query the “dependency” table in the database.
However, the formHostGroupDependency.php does not sanitize the dep_id parameter before appending it to the SQL statement. A malicious user is therefore able to directly manipulate the Centreon database by embedding arbitrary SQL commands within the dep_id parameter in the HTTP requests. For example, an attacker may utilize the “;” character (or its URL-encoded equivalent) in a HTTP request to terminate a SQL statement with a malicious create table command, as shown below:
A remote, authenticated attacker could exploit this vulnerability by sending a maliciously crafted request to the server. A successful attack may result in arbitrary SQL command execution at the database on the target server, potentially leading to the execution of arbitrary code in the security context as root.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
• The attacker must authenticate to the target system.
Triggering Conditions:
The attacker authenticates and then sends an HTTP request containing maliciously crafted parameters to the target server. The vulnerability is triggered when the request is processed by the target server.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 80/TCP
• HTTPS, over port 443/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15666 Centreon main.get.php SQL Injection
• IPS: 15674 Centreon main.get.php SQL Injection 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Blocking the affected ports from external network access if they are not required.
• Filtering traffic based on the signature above.
• Upgrading the product to a non-vulnerable version.
The vendor has released an advisory regarding this vulnerability:
Vendor Advisory