Breach of FireEye Offensive Tools
On December 8, 2020, Cyber Security Firm FireEye disclosed an incident that resulted in theft of their offensive security tools (OSTs) used by their Red-Team to test the security posture of their customers.
Some of these tools look like the well-known offensive framework Cobalt Strike. This is evident in the naming convention used by FireEye,
In response to the breach, FireEye has provided Red Team tools countermeasures which are available on Github. These countermeasures include rules in multiple languages such as Snort, Yara, ClamAV, and HXIOC. Since none of these tools leverage 0-day vulnerability, FireEye also provided a listing of CVEs used by these tools.
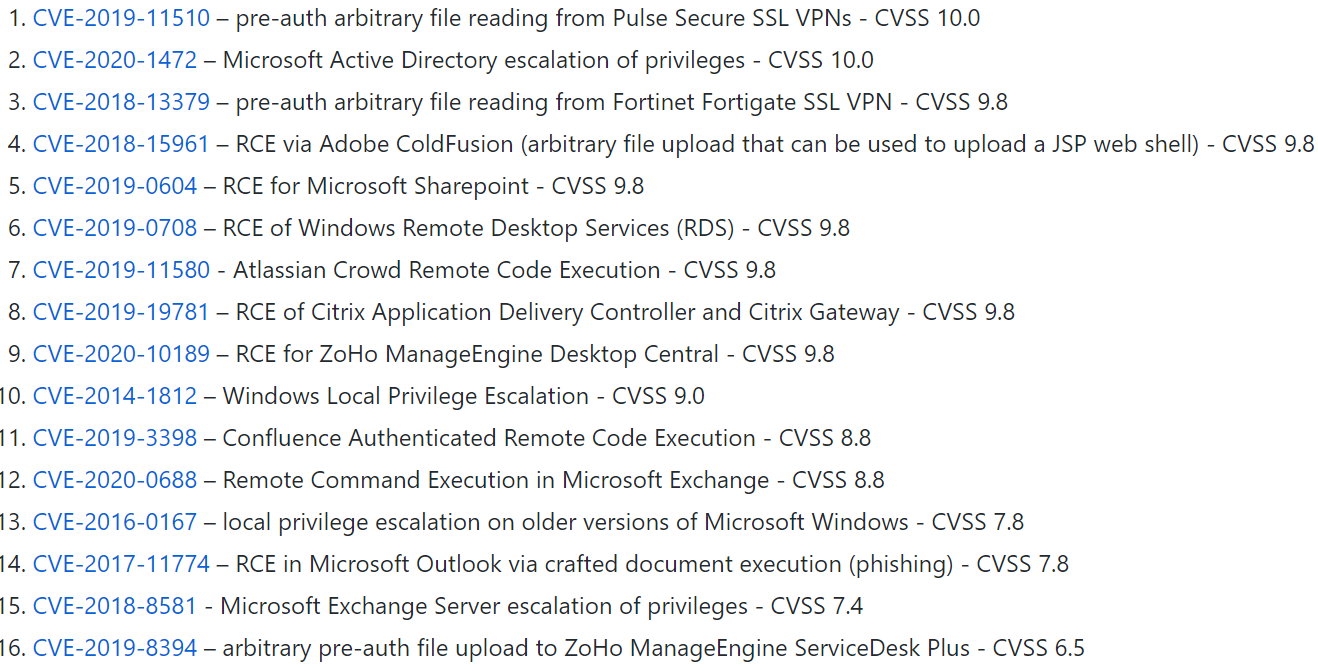
An important aspect for preventing the usage of these red teaming tools in your environment is to address the vulnerabilities which are known to exploit.
SonicWall Capture Labs Threat Research team provides protection against the list of CVEs shown above as well as the Beacon tool used by FireEye Red-Team with the following signatures
IPS:14422 Pulse Connect Secure Information Disclosure
IPS:15143 Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 1
IPS:15156 Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 2
IPS:15158 Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 3
IPS:15185 Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 4
IPS:15081 Fortinet SSL VPN Web Portal Directory Traversal
IPS:13910 Adobe ColdFusion Arbitrary File Upload 1
IPS:14689 Microsoft SharePoint Remote Code Execution (FEB 19)
IPS:14225 Remote Desktop Services Remote Code Execution (MAY 19)
IPS:14725 Citrix NetScaler ADC/Gateway Directory Traversal 2
IPS:14886 ManageEngine Desktop Central Insecure Deserialization
IPS:14826 Microsoft Exchange Server Remote Code Execution (CVE-2020-0688)
IPS:14888 Microsoft Exchange Server Remote Code Execution (CVE-2020-0688) 2
IPS:14889 Microsoft Exchange Server Remote Code Execution (CVE-2020-0688) 3
IPS:14890 Microsoft Exchange Server Remote Code Execution (CVE-2020-0688) 4
IPS:11556 Win32k Elevation of Privilege (MS16-039) 2
IPS:2007 FireEye RUBEUS nonce 2 TCP
IPS:2009 FireEye RUBEUS nonce 2 UDP
IPS:15285 FireEye BEACON CSBundle USAToday Server
IPS:15286 FireEye RUBEUS Process
IPS:15287 FireEye GORAT Build ID
IPS:15288 FireEye BEACON CSBundle Original Stager




