BAT file based Ransomware targeting people in China
The SonicWall Capture Labs Threat Research Team has observed a BAT file related to CXK-NMSL V3.2 Ransomware targeting people in China.
The batch file uses ‘FOR’ looping command for listing the files in the directory. The listed files are renamed with “.cxkdata” suffix.
The renamed files are then base64 encoded using the “certutil –encode” command and saved into new file having .cxk_nmsl as extension, the original files are later deleted.
The Ransomware encodes files found in the following locations:
• %SystemDrive%\
• %UserProFile%\
• %UserProFile%\Desktop\
• %UserProFile%\Downloads\
• %UserProFile%\Favorites\
• %UserProFile%\Searches\
• %UserProFile%\Saved Games\
• %UserProFile%\Contacts\
• %UserProFile%\Links\
• %UserProFile%\Videos\
• %UserProFile%\Pictures\
• %UserProFile%\Documents\
• %UserProFile%\Music\
The batch file contains base64 encoded PE file which is saved into the disk as “X”.
The file “X” is later decoded and saved into the disk using Certutil command as show below:
![]()
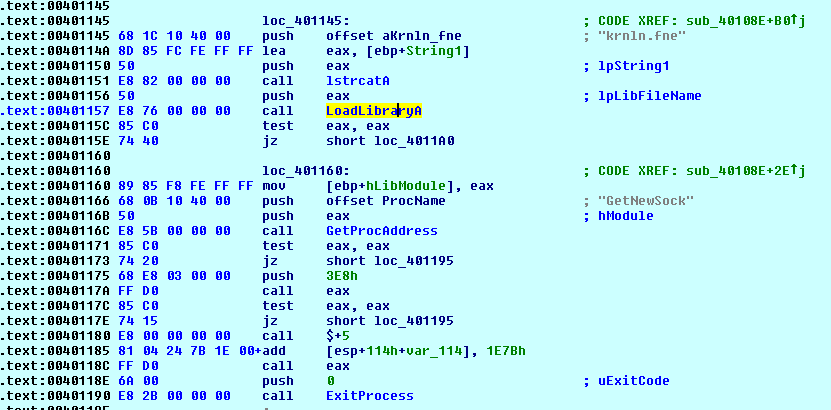
The PE file tries to load Krnln.fnr Dll and execute the “GetNewSock” API. This API provides capabilities for remote administration.
It also has base64 encoded zip file containing the wallpaper.jpg
Wallpaper.jpg

It creates the .JS file which is used to decode the base64 encoded file (wallpaper.jpg)
It also creates a VBS file which is used to display the message box in Chinese language.
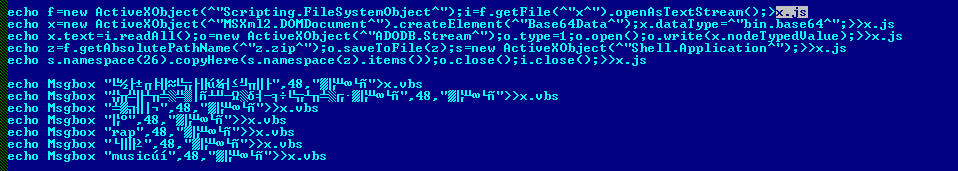
It modifies the registry and sets the values of wallpaper to its own wallpaper.jpg.
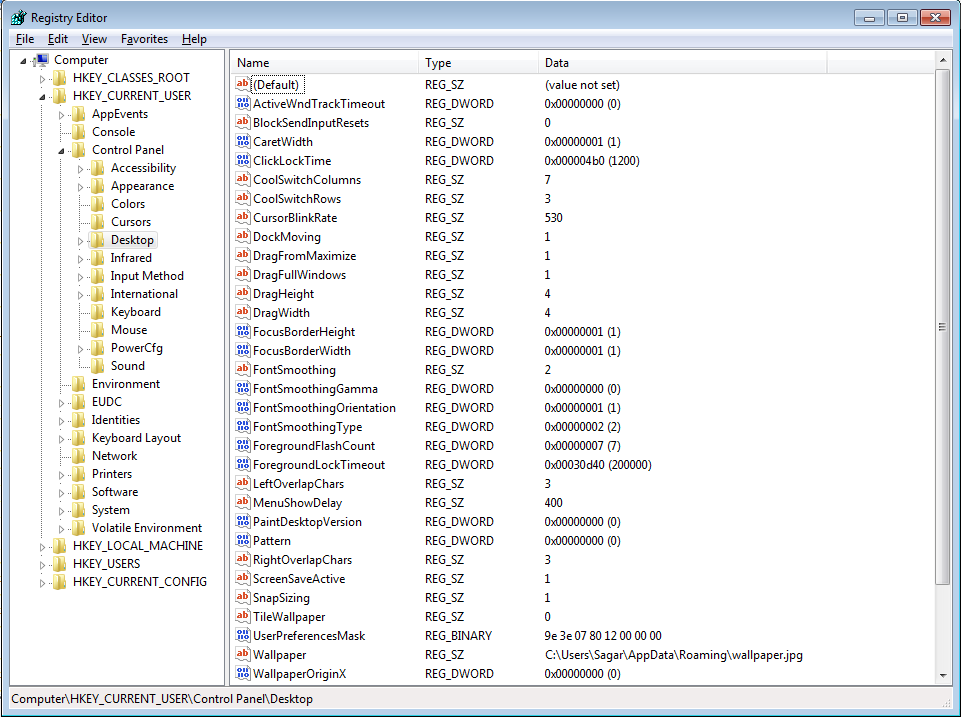
And executes the below command which is a preferred method for refreshing the wallpaper without the user being logging off and back on.
![]()
The Ransomware note is in Chinese language; which asks the victim to pay 100 B coins as ransom and for more information regarding the B coins it directs user to below site.
https://www.bilibili.com/blackboard/help.htmlprice.
Ransomware note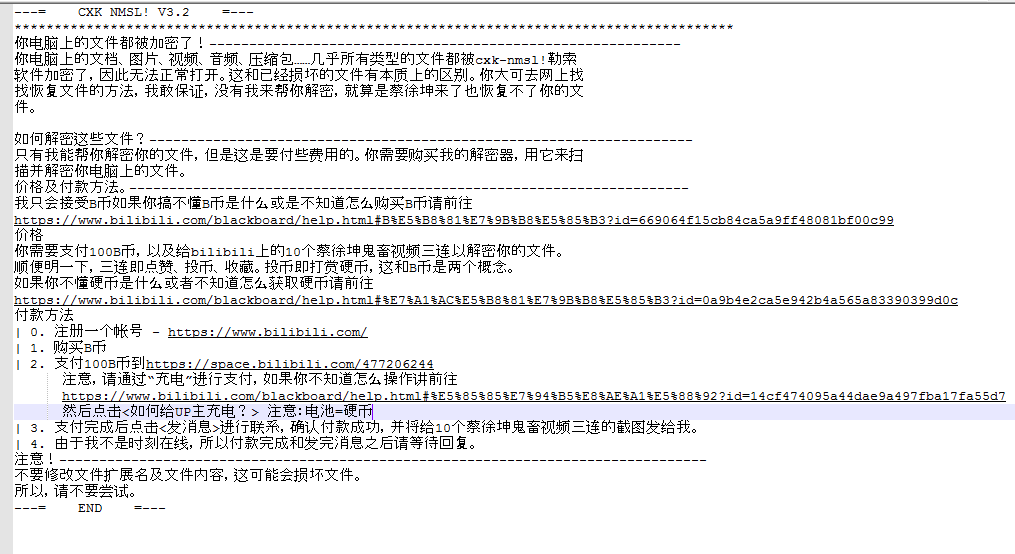
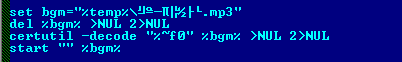
And at the end it drops the MP3 file and plays the song.
Sonicwall Capture Labs provides protection against this threat with the following signature:
- GAV: Ransom.BatCXK_NMSL (Trojan)
Indicators of Compromise:
- 01b575a1012b97988655980a48430dbb




