Atlassian Confluence OGNL Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Atlassian Confluence is a collaboration platform that allows you to build a knowledge base for documentation, product requirements, create, collaborate, comment on pages, project plans, share information between teams, and the entire company. It is written primarily in Java and runs on a bundled Apache Tomcat application server.
An OGNL injection has been reported in the Atlassian Confluence Server and Data Center. The vulnerability is due to insufficient input validation leading to OGNL evaluation of user-supplied input.
A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation can result in remote code execution under the security context of the affected server.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-26134.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.3 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:F/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.3 (E:F/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is functional.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
Confluence uses the Webwork web application framework to map URLs to Java classes, creating what is known as an “action”. Action URLs end with the “.action” suffix and are defined in the xwork.xml file in confluence-
Each action entry contains at least a name attribute, defining the action name, a class attribute, defining the Java class implementing the action, and at least one result element which decides the Velocity template to render after the action is invoked based on the result of the action. Common return values from actions are “error”, “input”, and “success”, but any value may be used as long as there is a matching result element in the associated XWork XML.
Action entries can contain a method attribute, which allows invocation of a specific method of the specified Java class. When no command is specified, the doDefault() method of the action class is called.
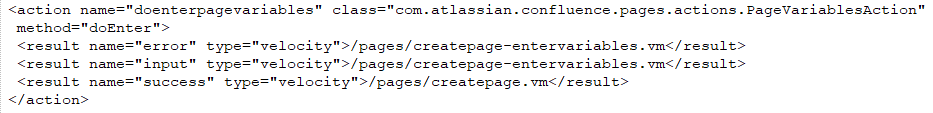
The following is a sample action entry for the doenterpagevariables action:
In the above example, the doEnter() method of the com.atlassian.confluence.pages.actions.PageVariablesAction class handles requests to “doenterpagevariables.action” and will return values such as “success”, “input”, or “error”, resulting in the appropriate velocity template being rendered. Request-URI paths that end in a slash are set to use “index.action”.
The vulnerability is due to insufficient validation of user input that is evaluated during Result calculation. As part of action processing, the action namespace is parsed from the Request-URI path from the start until the last slash. When processing the result of a request in the result class ActionChainResult, the namespace is checked for OGNL expressions and evaluated if found. A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request with an OGNL expression in the Request-URI to the target server.
Triggering the Problem:
• The target must have the vulnerable software installed and running.
• The attacker must have network connectivity to the target service.
Triggering Conditions:
The attacker sends a malicious HTTP request to the target server with a malicious Request-URI path. The vulnerability is triggered while processing the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2801 Confluence Server and Data Center OGNL Injection RCE 1
• IPS: 2804 Confluence Server and Data Center OGNL Injection RCE 2
• IPS: 2806 Confluence Server and Data Center OGNL Injection RCE 3
• IPS: 2809 Confluence Server and Data Center OGNL Injection RCE 4
• IPS: 2813 Confluence Server and Data Center OGNL Injection RCE 5
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Upgrading the product to a non-vulnerable version.
• Detect and filter malicious traffic using the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory