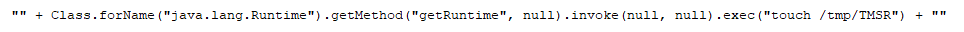Atlassian Confluence and Data Center OGNL Injection Vulnerability
Overview:
Atlassian Confluence is a collaboration platform written in Java. Users can create content using spaces, pages, and blogs which other users can comment on and edit. It is written primarily in Java and runs on a bundled Apache Tomcat application server.
An OGNL injection has been reported in the Webwork module of Atlassian Confluence Server and Data Center. The vulnerability is due to insufficient input validation leading to OGNL evaluation of user-supplied input.
A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation can result in arbitrary code execution under the security context of the affected server.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-26084.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.3 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:F/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.3 (E:F/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is functional.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
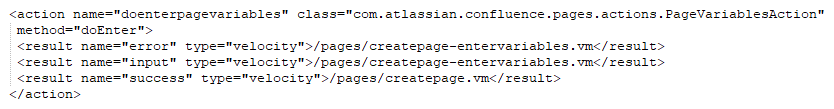
Confluence uses the Webwork web application framework to map URLs to Java classes, creating what is known as an “action”. Action URLs end with the “.action” suffix and are defined in the xwork.xml file inside confluence “version”.jar (where “version” is the confluence version number) and in the atlassian-plugin.xml file within the JAR files of the included plugins. Each action entry contains at least a name attribute, defining the action name, a class attribute, defining the Java class implementing the action, and at least one result element which decides the Velocity template to render after the action is invoked based on the result of the action. Common return values from actions are “error”, “input”, and “success”, but any value may be used as long as there is a matching result element in the associated XWork XML. Action entries can contain a method attribute, which allows invocation of a specific method of the specified Java class. When no command is specified, the doDefault() method of the action class is called. The following is a sample action entry for the doenterpagevariables action:
In the above example, the doEnter() method of the “com.atlassian.confluence.pages.actions.PageVariablesAction” class handles requests to “doenterpagevariables.action” and will return values such as “success”, “input”, or “error”, resulting in the appropriate velocity template being rendered.
Confluence supports the use of Object Graph Navigational Language (OGNL) expressions to dynamically generate web page content from Velocity templates using the Webwork library. OGNL is a dynamic Expression Language (EL) with terse syntax for getting and setting properties of Java objects, list projections, and expressions. OGNL expressions contain strings combined together to form a navigation chain. The strings can be property names, method calls, array indices and so on. OGNL expressions are evaluated against the initial, or root context object supplied to the evaluator in the form of OGNL Context.
The container object “com.opensymphony.webwork.views.jsp.ui.template.TemplateRenderingContext” is used to store objects needed to execute an Action. These objects include session identifiers, request parameters, spaceKey etc. TemplateRenderingContext also contains a com.opensymphony.xwork.util.OgnlValueStack object used to push and store objects against which dynamic Expression Languages (EL) are evaluated. When the EL compiler needs to resolve an expression, it searches down the stack starting with the latest object pushed into it. OGNL is the EL used by the Webwork library to render Velocity templates defined in Confluence, allowing access to Confluence objects exposed via the current context. For example, the $action variable returns the current Webwork action object.
OGNL expressions in Velocity templates are parsed using the ognl.OgnlParser.expression() method. The expression is parsed into a series of tokens based on the input string. The ognl.JavaCharStream.readChar() method, called by the OGNL parser, evaluates Unicode escape characters in the form of “\uXXXX” where “XXXX” is the hexadecimal code of the Unicode character represented. Therefore, if an expression includes the character “\u0027”, the character is evaluated as a closing quote character (‘), escaping the context of evaluation as a string literal, allowing to append an arbitrary OGNL expression. If an OGNL expression is parsed in a Velocity template within single quotes and the expression’s value is obtained from user input without any sanitization, an arbitrary OGNL expression can be injected.
An OGNL injection vulnerability exists in Atlassian Confluence. The vulnerability is due to insufficient validation of user input used to set variables evaluated in Velocity templates within single quotes. By including the “\u0027” character in user input, an attacker can escape the string literal and append an arbitrary OGNL expression.
Before OGNL expressions are evaluated by Webwork, they are compared against a list of unsafe node types, and variables names in the “com.opensymphony.webwork.util.SafeExpressionUtil.containsUnsafeExpression()” method. However, arbitrary Java objects can be instantiated without using any of the unsafe elements listed. For example, the following expression, executing an OS command, would be accepted as a safe expression by this method:
A remote attacker can exploit this vulnerability by sending a crafted HTTP request containing a malicious parameter to a vulnerable server. Successful exploitation can result in the execution of arbitrary code with the privileges of the server.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
Triggering Conditions:
An attacker connects to a target server and submits an HTTP request containing a malicious parameter to a vulnerable XWork action. The vulnerability is triggered when the target server processes the XWork action, resulting in the processing of the malicious request parameter.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 8090/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15673 Atlassian Confluence Server Webwork OGNL injection 1
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Upgrading the product to a non-vulnerable version.
• Filtering attack traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory