Argus Ransomware actively spreading in the wild.
The SonicWall Capture Labs Threat Research Team observed reports of a new variant family of Argus Ransomware [Argus.RSM] actively spreading in the wild.
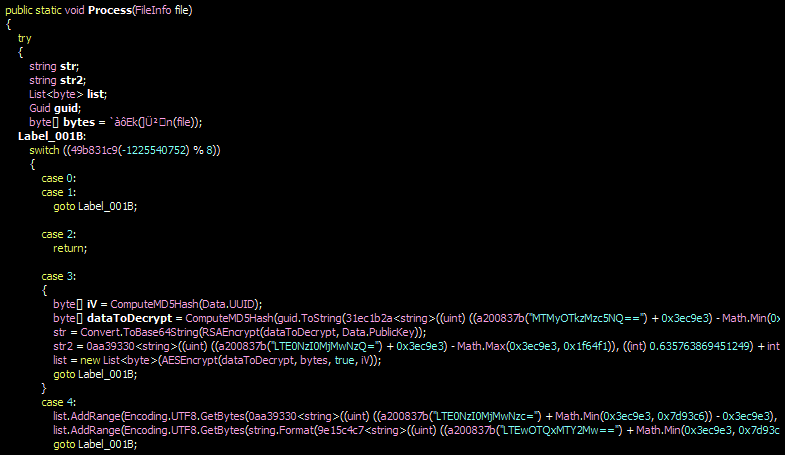
Argus encrypts the victims files with a strong encryption algorithm until the victim pays a fee to get them back.

Contents of the Argus Ransomware.
Infection Cycle:
The Ransomware adds the following files to the system:
- Malware.exe
- %Userprofile \audiodg.exe [Executable Dropper ]
- %App.path%\ [File Name]. ARGUS
- %Userprofile\Desktop %\ ARGUS-DECRYPT.html
- Instruction for recovery
Once the computer is compromised, the Ransomware runs the following commands:
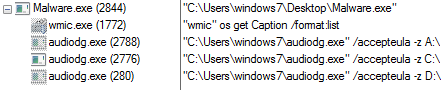
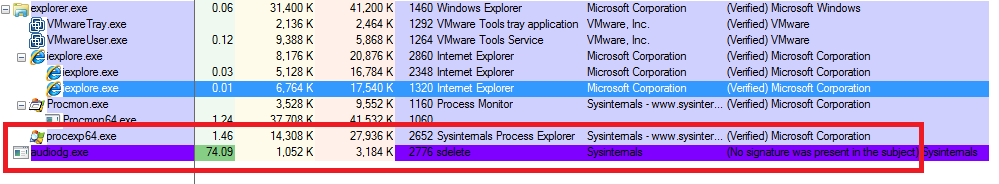
The Ransomware performs process injection techniques into Csrss.exe process to hide its own codes into a legitimate process.
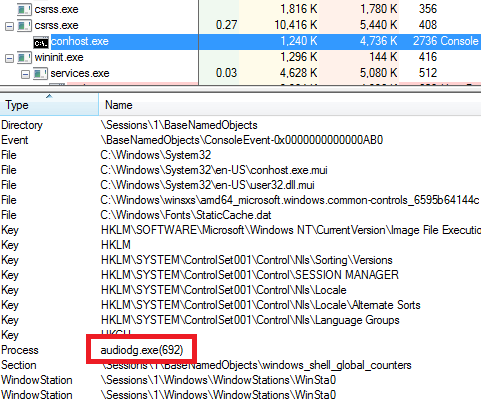
The Ransomware encrypts all the files and appends . Argus extension onto each encrypted file’s filename.
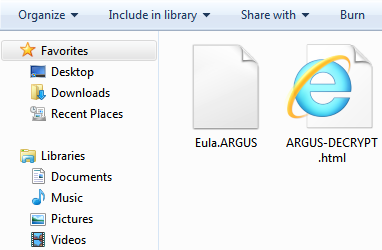
After encrypting all personal documents the Ransomware shows the following webpage containing a message reporting that the computer has been encrypted and to contact its developer for unlock instructions.

SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Argus.RSM (Trojan)




